Tips for Passwordless Authentication Success
Employees and customers want access to applications from anywhere, on any device, at any time. We have become so conditioned to using passwords to get that access, even the suggestion of moving away from them can make people nervous, despite all of the problems with passwords.
Passwords as we know them date back to 1961. The original password structure was four numeric characters (think PIN), which was assigned the core function in mainframe systems and still exists in some enterprises. We're now at a tipping point for passwords due to the sheer number of breaches caused by compromised passwords and overall user frustration with creation, usage and reset requests. If you've ever needed an urgent password reset and been on indefinite hold waiting for assistance, you know what I mean. Things have gotten so bad, some people use their social media accounts as the primary pathway to other accounts to avoid creating new passwords. Unfortunately, risk doesn't go down because users transfer the responsibility of securing their data to social media companies.
What is Passwordless Authentication?
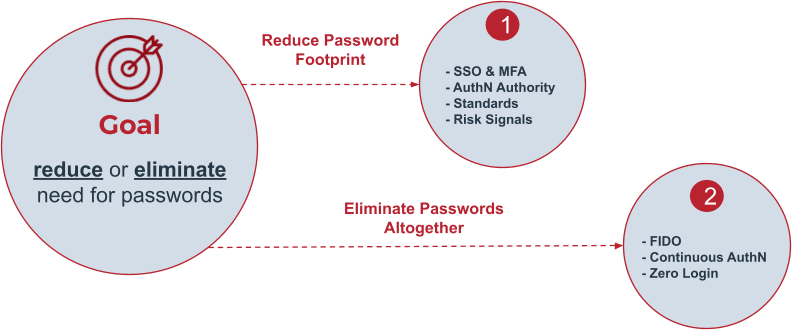
Passwordless authentication is a shift away from using passwords during the authentication process. While the eventual goal is the elimination of passwords, reducing the need for passwords is more realistic for the time being. There are numerous authentication methods available that are more secure than passwords and the transition has already begun. For example, you may already be using a fingerprint scan to authenticate yourself when you unlock your smartphone or access apps. Alternatives are discussed in more detail below.
Passwordless Authentication Improves Security
Verizon’s 2021 Data Breach Investigations Report found that 61% of breaches in 2020 were executed using unauthorized credentials. Password fatigue leads people to reuse the same passwords on multiple accounts rather than coming up with new ones and those passwords are often shared with others. When passwords are created using the names of family pets or other things shared freely on social media pages, they are easy for bad actors to figure out. Once that password has been compromised, it can impact multiple accounts, which has led some organizations to require more frequent password changes and increase password complexity.
61% of data breaches involve the use of unauthorized credentials.
2021 Data Breach Investigations Report, Verizon
When we think of compromised passwords, we often think of stolen data and identity theft, which is costly and damaging to the brand, but we have also seen password-based compromise create business disruptions that impact services, including essential infrastructure.
Stolen credentials also fuel the rise in ransomware. The Digital Shadows Research Team found that 15 billion stolen credentials allowing account takeover were available on the dark web. Phishing and social engineering schemes, password cracking tools, and other methods are also used by bad actors to obtain passwords in order to steal resources, including other passwords, data and money, or hold them ransom for big payouts. By moving away from the use of passwords, we can devalue them on the dark web and as part of the attack chain.
Passwordless Authentication Improves Productivity and the User Experience
The use of passwords has led to lower productivity for workers in multiple ways. Unless single sign-on (SSO) and multi-factor authentication (MFA) are in place, workers may be required to create multiple accounts and log into multiple apps each day in order to do their jobs. For IT help desk workers, frequent password reset requests from employees and customers take them away from other responsibilities.
Customers also experience friction and frustration with passwords. As with employees, SSO and MFA solutions improve the user experience, so users aren't forced to login to different company applications with different credentials, like separate logins for an eCommerce account and its corresponding rewards points account. Even with those improvements, the customer is still required to input their account password—one of many passwords that they probably have to use every day—and that password is still subject to the same vulnerabilities.
Why the Resistance to Passwordless?
Passwords have been embedded in apps and services for so long, moving away from passwords will take time. The average person has almost 200 services that require them to enter passwords or other credentials. No matter how complex password creation has become (e.g., at least 8 characters long, including 1 uppercase letter, 1 lowercase letter, 1 number and 1 special character), passwords still provide many people with a sense of security. This misplaced sense of security is often based on conditioning after years of being asked to create a password every time a new account is opened.
The password habit isn't just for users. Enterprises have long used passwords for security. Requiring just a username-password combination has transitioned to requiring additional verification methods, so progress is being made for increased security. In the short term, the goal is password-less, not password-free. The first step is reducing each user's password footprint, so users aren't creating additional passwords.
Tips for Success: The Passwordless Journey
The journey to passwordless success has four steps:
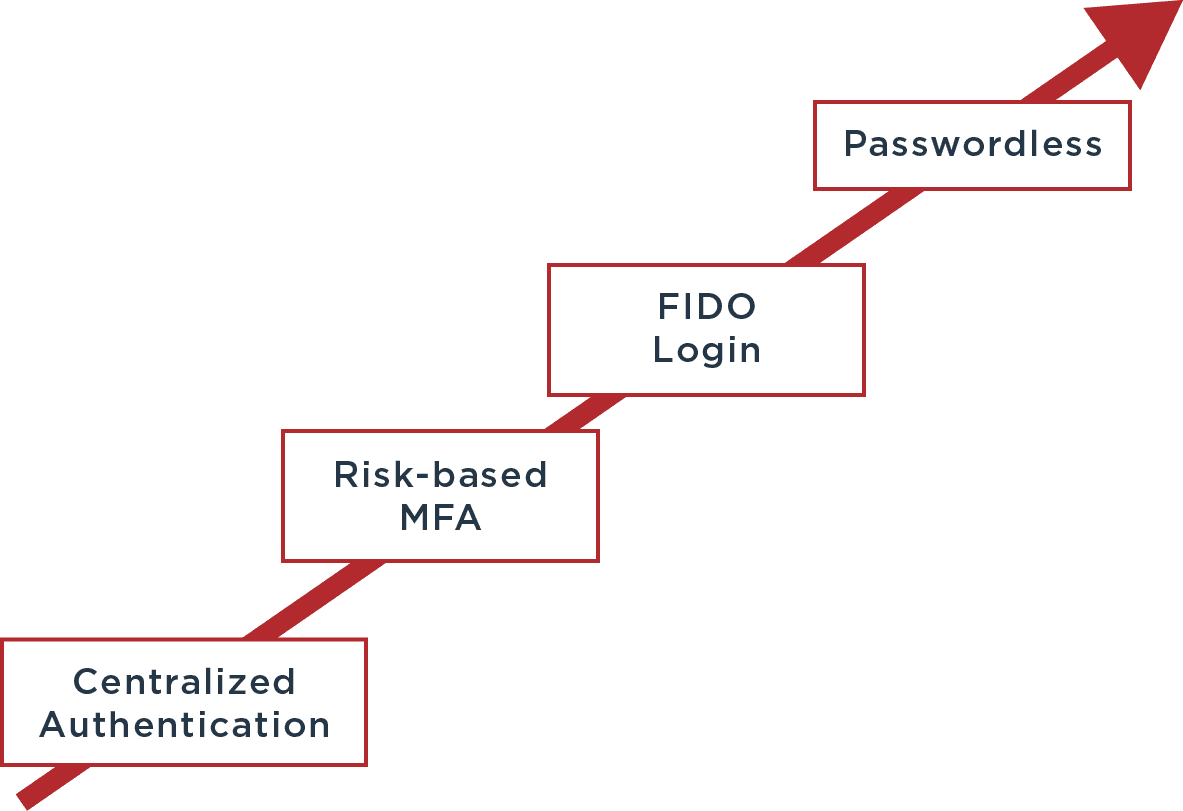
Start by Centralizing Your Authentication
Centralizing authentication with single sign-on and adaptive multi-factor authentication (MFA) provides the framework needed for passwordless authentication. Multi-factor authentication requires users to verify their identities using two or more authentication factors, while two-factor authentication (2FA) requires just two factors. Passwords are often used as the first authentication factor, but that is not a requirement for MFA or 2FA. Microsoft found that MFA can "prevent 99.9 percent of attacks on your accounts."
Authentication factors include:
- Knowledge = Something You Know (password, PIN, etc.)
- Possession = Something You Have (smartphone, key fob, etc.)
- Inheritance = Something You Are (fingerprints, retinal scans, etc.)
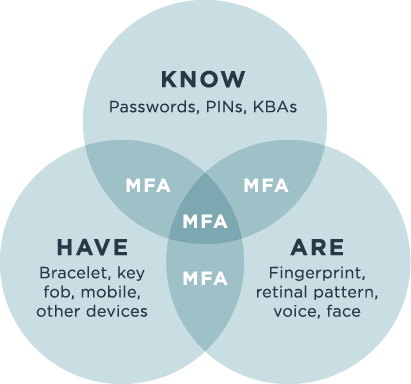
A subset of Possession can be considered a fourth authentication factor by incorporating device-based behavioral and contextual information as "Something You Do." This new factor may look at the time of day a user typically logs in, usual location or behavior during sessions (keystrokes, speed, cut & paste frequency, etc.).
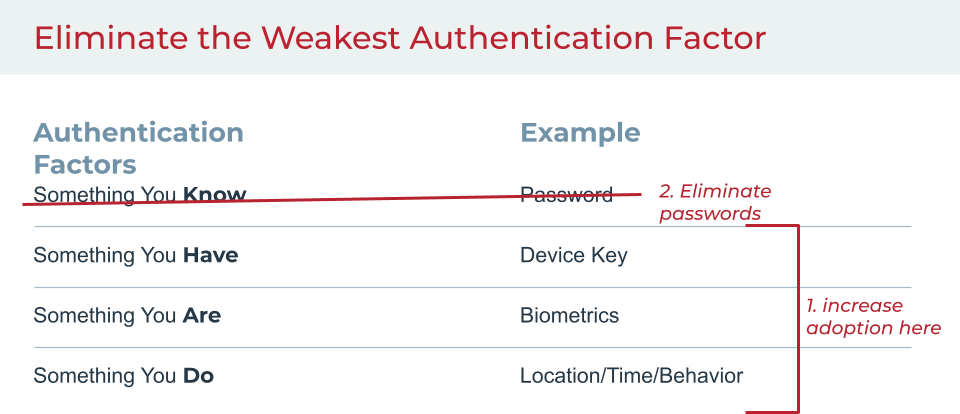
As we phase out the password, three stronger authentication factors remain for MFA and 2FA. Minimizing reliance on passwords not only makes your network more secure, but it reduces calls to your IT help center for password resets.
Adopt Risk-based Multi-Factor Authentication (MFA)
Risk-based MFA, also known as adaptive MFA, dynamically assesses the risk of a given interaction based on a variety of factors and adjusts the authentication process accordingly. By looking at the context and behavior of the login attempt, bad actors using compromised credentials can be stopped before they enter your system. For example, if a user is logging in from a suspicious IP address and trying to gain access to sensitive information, additional authentication methods can be required before access is granted. Failure to provide the additional proof will cause access to be denied.
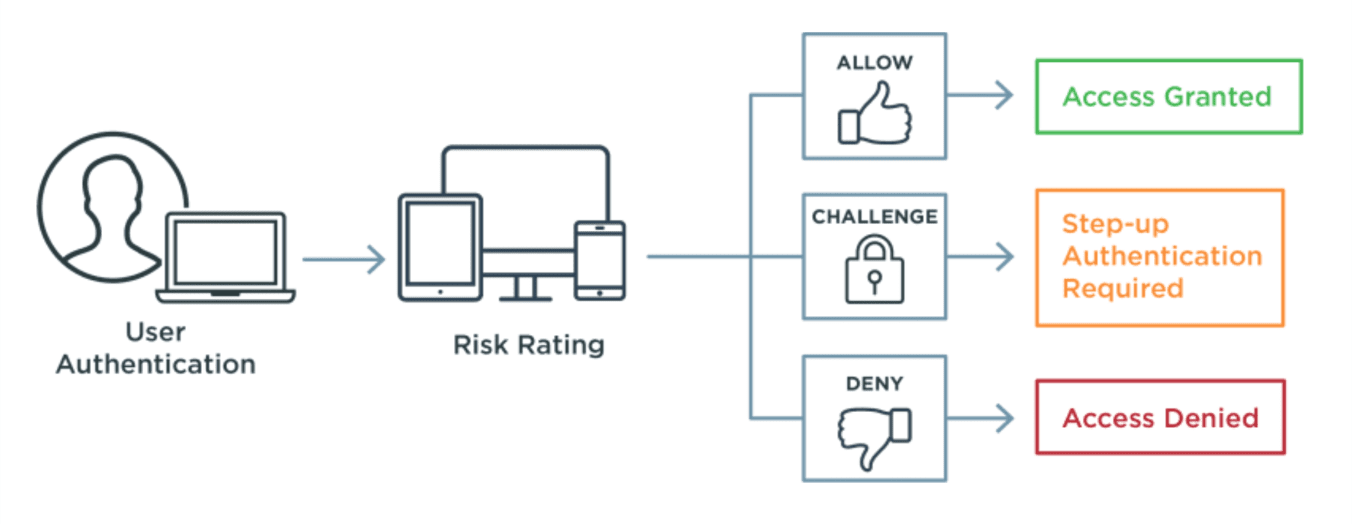
By evaluating whether adequate security requirements have been met for each individual transaction and stepping up authentication when they haven't, an additional layer of security protects data without introducing unnecessary friction into the process.
Choose the Right Alternative Authentication Mechanism
There are numerous authentication methods that can be used instead of passwords. By providing a variety of authentication options, we can meet users how and where they prefer to work with brands and/or support different workforce scenarios.
The pros and cons of several of these methods are listed below.
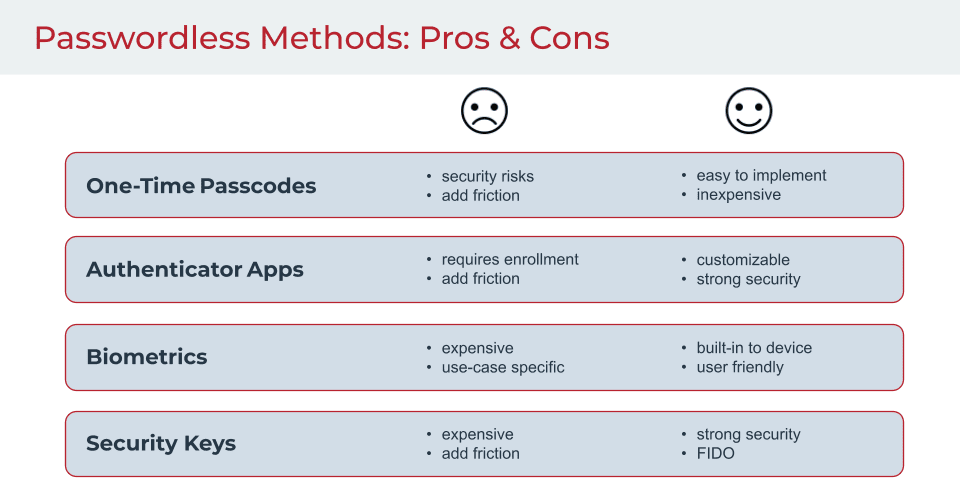
One-time passcodes (OTPs) fall into the Possession category, since OTPs are sent to a smartphone or generated by a device, such as a key fob, in the user's possession.
Authentication apps, such as Google authenticator or Microsoft authenticator, can be used to generate a one-time passcode for authentication.
Biometrics relate to unique physical traits. While many people are familiar with facial and fingerprint recognition, other forms of biometric authentication, such as retinal scans, voiceprints, brainwave and heart signatures, have been gaining prominence.
Security keys are hardware-based devices inserted into a computer or mobile device to grant the user instant access to services using a button or keypad.
Adopt Standards-based Authentication with FIDO and Public Key Cryptography
Numerous organizations have joined together to develop alternatives to passwords. Founded in 2013, the FIDO Alliance focuses on creating authentication standards to help reduce the world's reliance on passwords.
FIDO (Fast Identity Online) is a set of open, standardized authentication protocols that use standard public key cryptography techniques to secure user authentication. The fact that FIDO is an open standard means it is intended for widespread use, publicly available and free to adopt, implement and update. The standard provides advanced protection against phishing, man-in-the-middle and other common cyberattacks.
The FIDO Alliance published three sets of specifications, all based on public key cryptography:
- Universal Authentication Framework (UAF)
- Universal Second Factor (U2F)
- FIDO2
All communications are encrypted and private keys never leave the user's device, reducing the chances of someone discovering them during transmission. If biometric information is used for verification, it is also stored on users' devices, making these authentication processes stronger and more secure.
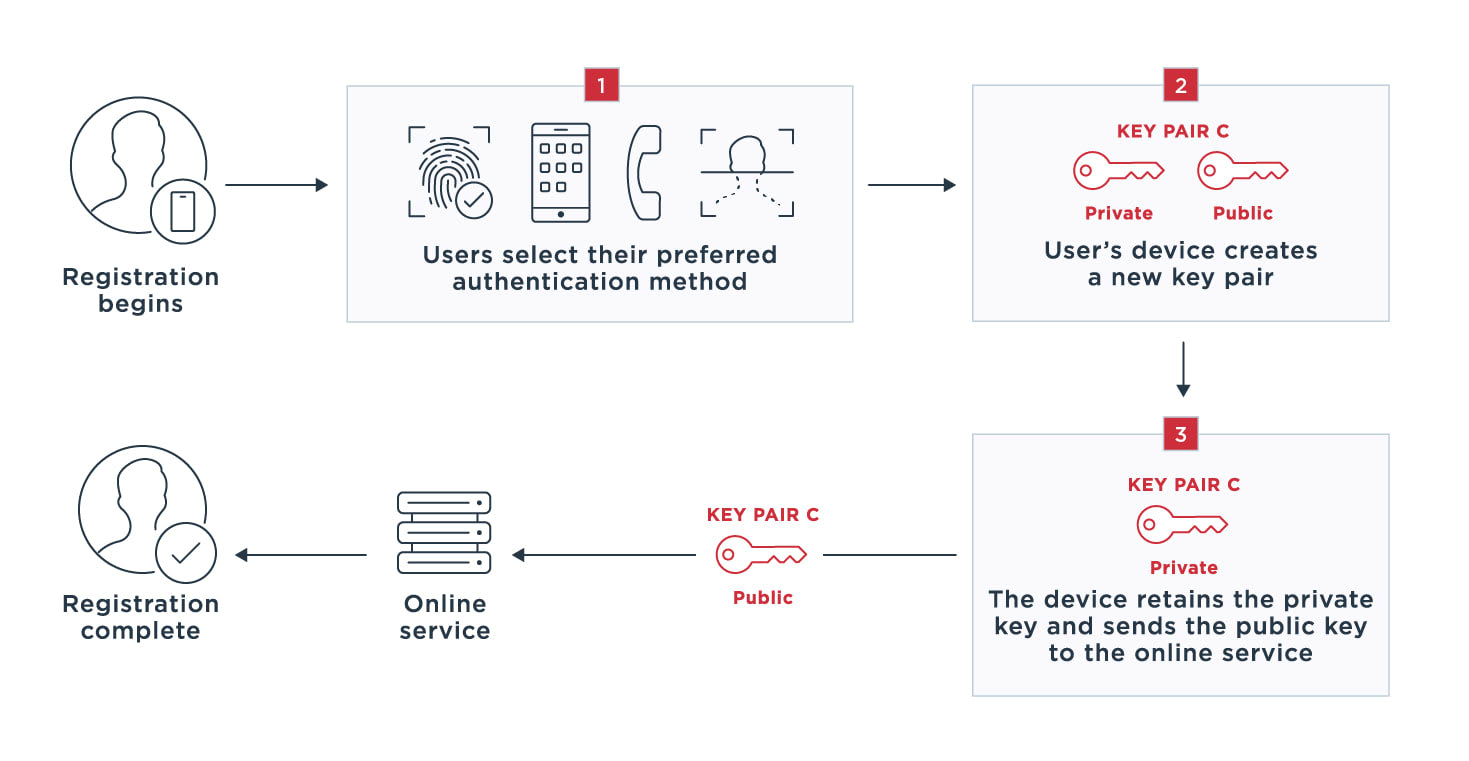
Users are able to sign on to a FIDO-enabled product or service using their preferred authentication method (fingerprint scan, entering a PIN, etc.) among the methods the product or service accepts.
You're Ready to Move to Passwordless
Start with the account creation process. Rather than using passwords during account creation, use a fingerprint scan or other authentication method. Identity proofing can also be part of your move to passwordless—at registration, during account recovery or at some other high risk event triggered by a signal. Having greater assurance that your users are who they say they are makes the transition to passwordless easier.
Usernames and passwords will become a thing of the past, along with the security issues associated with them. Eliminating passwords also eliminates the friction associated with creating, remembering and resetting passwords. Because more secure authentication methods already exist, the tools are currently available to reach your passwordless goal.
To learn more about passwordless, watch this short video.
Final Tips for Passwordless Authentication Success
There is no one-size-fits-all approach to make the move to passwordless. Each enterprise has to assess their current situation and proceed at their own pace. Finding an in-house champion and a passwordless partner to help with apps and resources can make the journey easier.
For more information and tips on the passwordless journey, please watch my webinar: Be a Cybersecurity Champion - Tips for Passwordless Success.
