Risk-based Authentication: Integrations for Better Digital Experiences
In the digital world, determining whether someone is who they say they are can be a delicate balancing act. Strong security is vital for protecting your enterprise from breach and privacy violations, and you can’t simply fling open the virtual door to your resources before verifying who is ringing the bell. But make the authentication process too cumbersome and you end up with frustrated end users, which can lower employee productivity, annoy valued partners and drive away customers in search of a better user experience.
Creating the best digital experience possible while providing the necessary security often hinges on risk-based authentication: the concept of dynamically assessing the risk of a given interaction based on a variety of factors and adjusting the authentication process accordingly. Risk-based authentication can provide just the right balance of strong protection with frictionless user experience, and Ping’s powerful integrations enable your enterprise to choose the optimal authentication techniques for your business needs.
What is Risk-based Authentication?
Before we dive into how you can implement secure and user-friendly authentication with specific Ping integrations, let’s start with a quick overview. Risk-based authentication is essentially a subset of multi-factor authentication where a user is asked to provide an additional authentication factor when an access request is considered to be outside predefined safety parameters. It considers, in real time, the potential danger of a given operation based on factors such as:
- The user’s current authentication status
- The risk associated with the resource in question
- The context of the request
By evaluating whether adequate security requirements have been met for each individual transaction and stepping up authentication when they haven’t, it adds an additional layer of security without introducing unnecessary friction into the process. You are able to define a risk level that you are willing to accept to minimize friction, based on the resource being accessed, and if the risk is too high you can introduce stronger authentication.
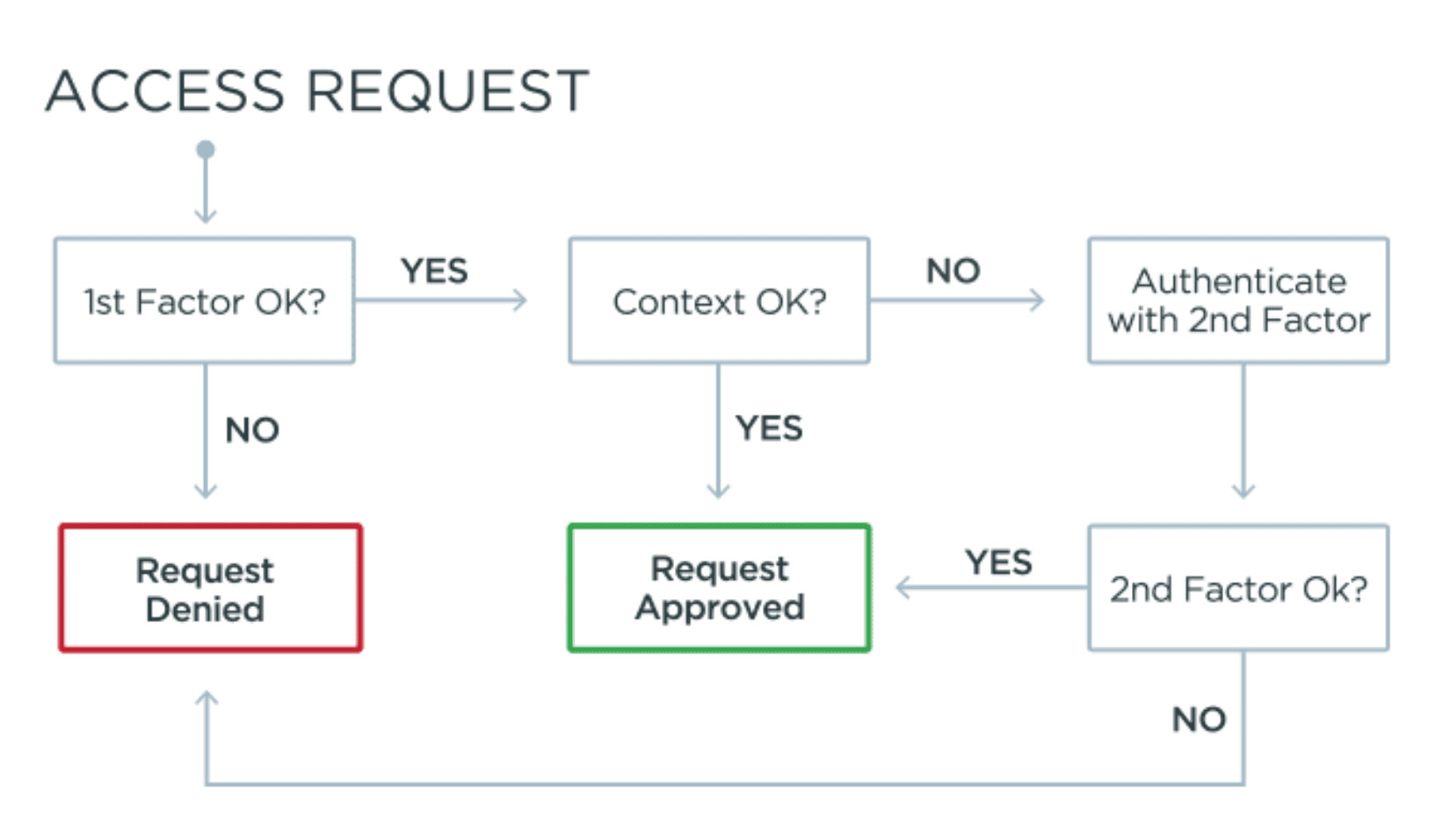
Risk-based step-up MFA is triggered by atypical and anomalous context or behavior. It's only when the context collected via the first authentication factor indicates something unexpected that a second factor of authentication is requested before access is granted.
Risk-based authentication encompasses contextual authentication, the use of logic-based mechanisms such as geolocation and device identifiers to determine whether a user should be required to use an additional factor. It can enable frictionless goals such as passwordless authentication, which has been shown to help achieve that desired balance of strong security and great user experience.
And it’s what your users want. Your workforce desires a simple and consistent sign-on experience, with secure and streamlined access to resources that allows them to be more productive. This is especially important in today’s remote work environment, when more employees than ever before need access while working from home or from other remote locations. And your customers are increasingly demanding that you provide them with experiences that are both seamless and secure:
- 67% of customers claim they have higher CX standards than ever before
- 66% of enterprises say their customers demand stronger security and privacy
- 40% of customers will abandon a brand after one bad experience
The Four Categories Used in Identifying Risk Signals
So how do you go about defining whether a user interaction is potentially risky and therefore in need of stepped-up authentication? Broadly speaking, risk signals originate from one of four categories: device reputation, user behavior, network risk and behavioral biometrics.
Device reputation. Device reputation is exactly what it sounds like: determining the risk of the device being used during the authentication process by looking at its history and factors such as whether the device has been involved in any known fraudulent activity. Crowd-sourced consortiums correlate users to devices to define fraud rings and to identify lone bad actors attacking multiple accounts, and then build rules based on these profiles.
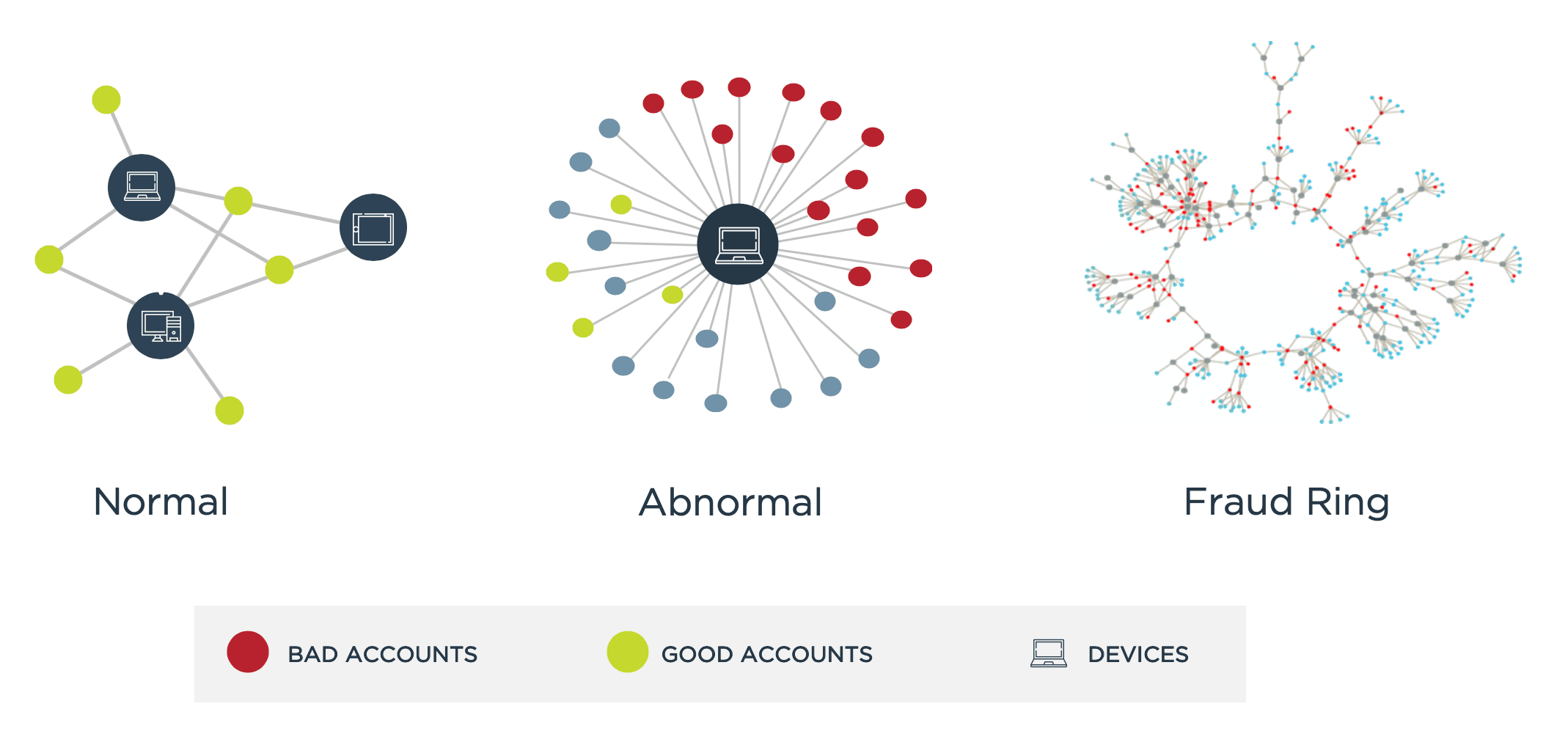
Credit: TransUnion
- User behavior. Stolen or compromised credentials pose huge threats to security and privacy. As a user moves laterally on the network, you can determine threats by building a baseline of user behavior and adding real-time risk if/when the user deviates from this behavior.
- Network risk. Along with the user and the device, a third point of potential vulnerability lies in the network used for access. One mitigation technique is to determine risky behavior from network inputs, base the risk score on what the web traffic looks like, and then correlate it to a user for a risk score. This will give you a better understanding of what “normal” traffic looks like, and you can then check that to determine if strong authentication is required.
- Behavioral biometrics. This innovative approach to risk-based authentication compares a user’s physical movements—typing cadence, keyboard patterns, strength of key pressure, mouse movements, etc.—to their standard profile to determine risk. It works for mobile devices as well, looking at factors such as whether the user holds the device at the same angle, presses the screen with the same pressure, and swipes in the same fashion.
Ping Identity’s Integrations
Ping has partnered with a number of solutions providers to integrate risk signals into the authentication workflow for both workforce and customer use cases. By sending an API call from PingFederate to the solution, we can compare the device, behavior or biometrics of the current user to that user’s baseline and determine what the policy should do: approve, step up authentication, deny the request or do something else.
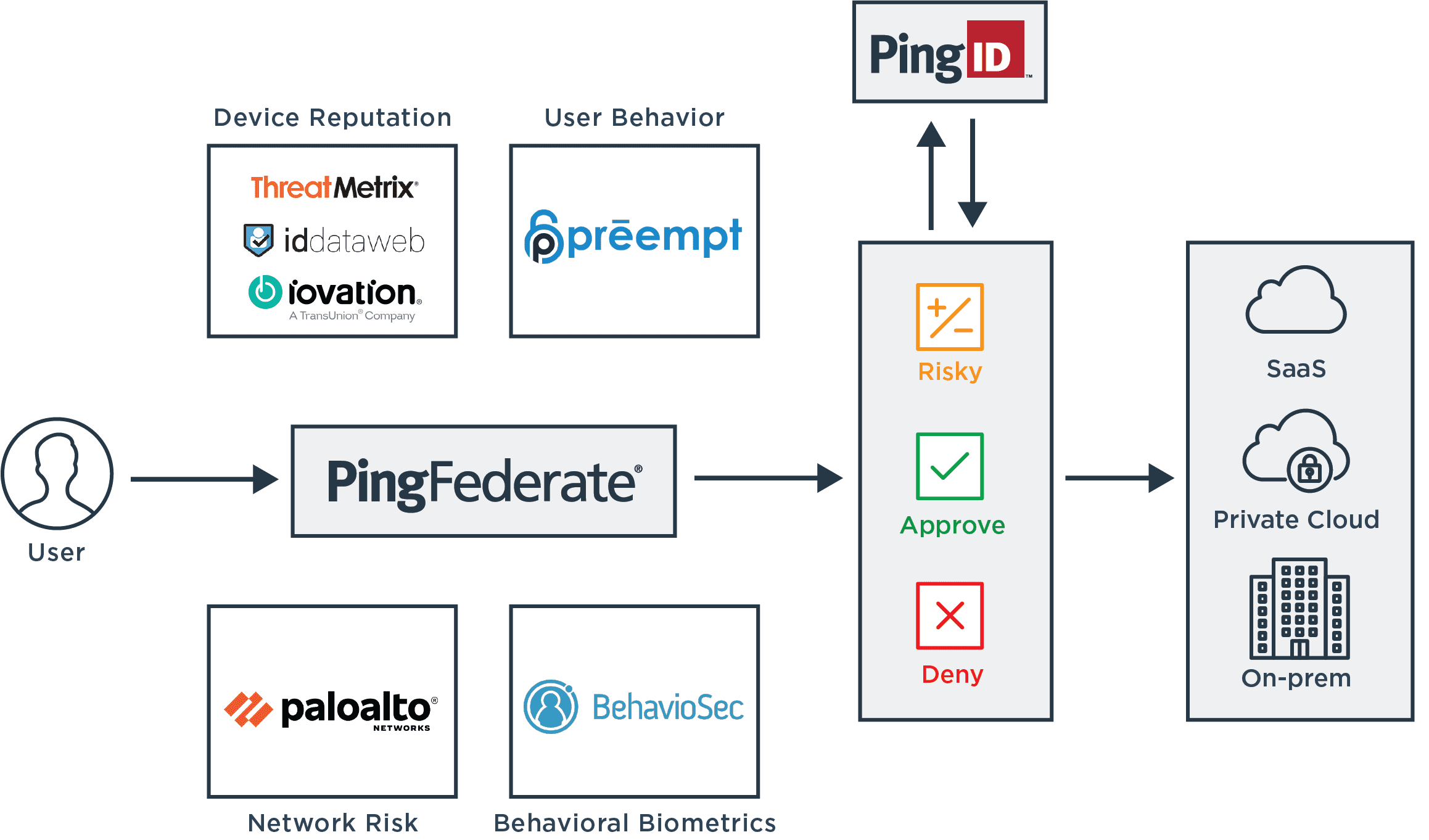
Device Reputation: Ping’s LexisNexis Digital Identity Network Integration
Jointly developed with LexisNexis Risk Solutions (formerly ThreatMetrix), this integration kit allows for a simple, easy-to-configure risk assessment on every authentication. Administrators can define policies to determine the riskiness of the user and device, deciding within milliseconds if you need to step up authentication to a second factor like PingID.
The Digital Identity Network is built from crowdsourced intelligence aggregating more than 30 billion global transactions each year, including logins, payments and new account creations. It allows you to differentiate between a trusted customer and a cyberthreat in milliseconds, while leveraging a multi-layered analysis completely invisible to the user.
Learn more and download the Digital Identity Network integration kit.
Device Reputation: TransUnion (Formerly iovation) Integration with PingAccess
Now, in addition to protecting initial authentications with TransUnion’s contextual risk score, an enterprise can perform fine-grained authorization with the new integration with PingAccess. Protect the front door with one policy (the PIngFederate integration) and have a stronger policy for the cash register (the PingAccess integration).
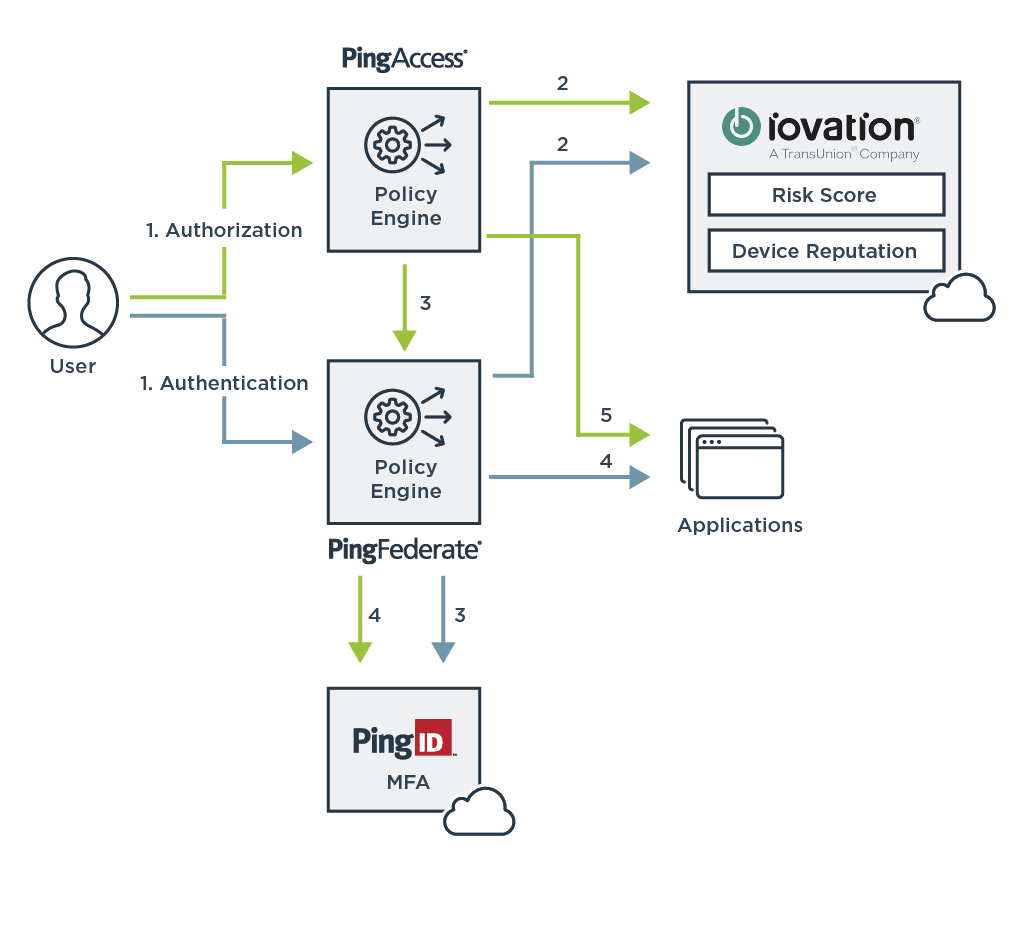
The benefit of this approach is that you can apply the risk policy specifically to the most valuable assets in your enterprise. Apply friction in the form of a second factor only if the risk level is high and the resource is valuable. Examples would be when a workforce user is accessing accounting software or when a consumer is transferring money or accessing healthcare records.
Learn more and download the TransUnion integration kit or check out the TransUnion/iovation demo.
User Behavior: Ping’s Preempt Integration
Preempt continuously monitors and learns the behavior of all users, service accounts and devices to identify and prevent risky activity and potential threats. This includes detecting and preventing compromised credentials, attackers impersonating devices or service accounts, ransomware, lateral movement attacks, malicious insiders and more.
The integration between Preempt and Ping allows an enterprise to have a baseline of a user’s behavior and prompt a second-factor authentication any time a user deviates from that baseline. Even in the middle of a session, Preempt can determine if the user’s lateral movement is anomalous and trigger a PingID second factor.
Learn more and download the Preempt Intelligence integration kit.
Network Risk: Palo Alto Networks’ Cortex XDR
Palo Alto Networks’ Cortex XDR platform collects network signals, and analyzes these signals using machine learning and artificial intelligence to determine the likelihood of that network traffic being risky. By compiling data from all of its network sources, Cortex XDR has an incredible data lake for determining if the network traffic is anomalous or risky.
To make this data even more powerful, Cortex XDR can also pull in PingFederate logs to tie user authentication data into the data lake for analysis. Having this tie between user authentication behavior and network traffic gives much deeper insight into the risk level. Integrations between Palo Alto Networks’ NGFW and GlobalProtect and PingID for MFA complete the picture by stepping up authentication when Cortex XDR indicates a higher risk level.
Learn more about Cortex XDR or the integrations here.
Behavioral Biometrics: Ping’s BehavioSec Integration
Ping Identity and BehavioSec integrate to provide a risk-based authentication solution based on behavioral biometrics. PingFederate captures the user's behavioral biometric signals and then sends this information to BehavioSense to compare to the user's baseline. If the patterns deviate from the baseline, the PingFederate policy can either deny authentication or step up authentication to PingID.
Learn more and download the integration kit here.
Device Reputation: Ping’s ID DataWeb Integration
ID DataWeb’s AXN Manage offers an exchange that can aggregate risk scores across several vendors, including LexisNexis. This allows an enterprise to weigh the riskiness to their specific needs without locking into a single vendor. Ping’s integration kit allows an enterprise to easily define a policy to read this aggregated risk score and provide advanced risk-based authentication.
Learn more and download the integration kit here.
Striking the Right Balance
Risk-based authentication is the key to balancing strong security with a frictionless user experience. With a layered approach to authentication, you can create the types of digital experiences your users crave.

