The One-time Password (OTP)
Ultimate Guide
Ultimate Guide
Organizations that don’t have the time or the resources to fully eliminate usernames and passwords know compromised credentials can be used to execute fraudulent attacks and data breaches. Supplementing a username and password with another authentication factor, known as multi-factor authentication (MFA), can be done with a one-time password (OTP). According to Microsoft, MFA can “prevent 99.9 percent of attacks on your accounts.”
What is a One-time Password (OTP) and How Does it Work?
The acronym OTP stands for both one-time password and one-time passcode, an automatically generated sequence of characters valid for a single login session or transaction. The OTP can be letters and/or numbers and sent via SMS, email or as a voice message as part of the MFA process. OTPs can also be sent as push notifications to an enterprise’s custom mobile apps or a third-party authenticator app can be used, like Google Authenticator.
An algorithm is used to create a new, random code each time a passcode is requested. Here are some examples of how a user might receive the OTP.
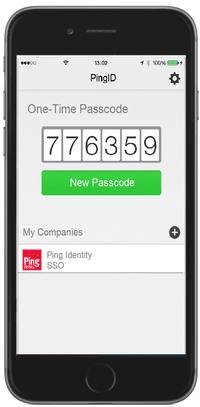
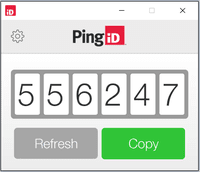

Once the OTP is generated, the user copies the code or it is automatically transmitted to an authentication window or other form that verifies the code with the authentication server to ensure there is a match.
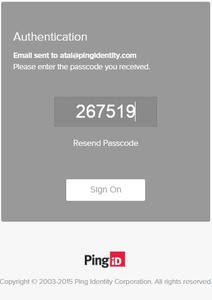
The user then receives an “Authenticated” message and is able to access their account and associated resources if the OTP is the final authentication factor required.

After the OTP is used or the timeframe for use has expired, the code is no longer valid and cannot be reused.
Time-based One-time Password (TOTP)
Time-based one-time password (TOTP) uses time as a moving factor, and passwords typically expire within 30-240 seconds. The temporary password is generated by an algorithm that uses the current time of day as one of its factors.
Enterprises need to make sure users are able to receive their passwords before the time limit expires, so TOTPs can have limited use in areas without high-speed broadband or reliable internet connections.
HMAC-based One-time Password (HOTP)
HMAC stands for hash-based message authentication code. HMAC-based one-time password (HOTP) is event-based and uses a counter as the moving factor instead of time, with seed values and hashes used to generate passwords. HOTPs were introduced and used before TOTPs.
The HOTP algorithm is based on an increasing counter value (hash) and a static symmetric key (seed) known only to the token and the validation service. Because HOTPs use counters instead of time, they are available for a longer period of time. The HOTP is valid until another one is actively requested and validated by the authentication server.
What are One-time Passwords Used For?
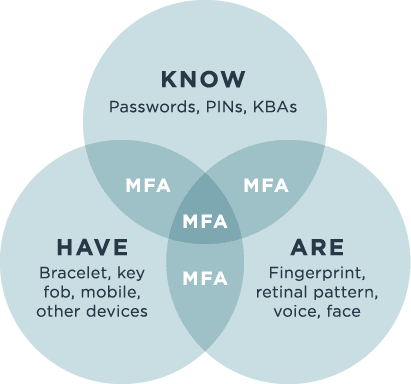
Multi-factor authentication (MFA) requires digital users to provide at least two pieces of evidence to prove their identities from different categories—something they know, something they have or something they are. One-time passwords fall into the “something they have” category, since OTPs are sent to a smartphone or other device in the user’s possession. OTPs can also be generated via a key fob or other hard token the user has
MFA prevents bad actors from using compromised credentials because they cannot provide the second and/or third authentication factor. Since the OTP is sent to the user’s device, as long as the user still has possession of their devices, the hacker won’t receive the OTP and authentication will fail.
OTP can be used for a variety of applications and services. To see how a one-time password is used to verify a user’s identity, watch this short video on payment flow.
What Do I Need to Do to Use a One-time Password?
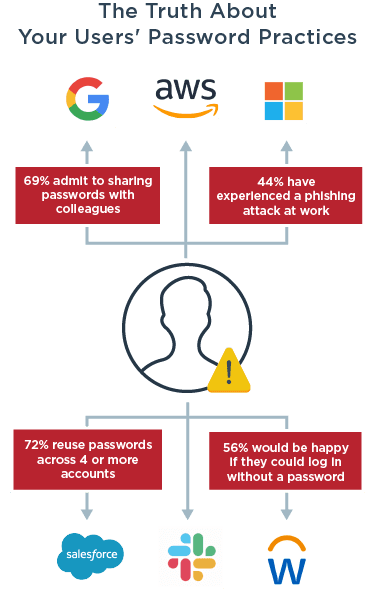
A one-time password increases security for a user’s account. Users often share or reuse their passwords, making them less secure. They can also have their passwords compromised and sold on the dark web. An added layer of security, such as an OTP, is required to keep bad actors out of your network.
Typically used as a second authentication factor, an OTP sent to a user’s device serves as an additional verification method. MFA is especially important for high-value transactions and accessing sensitive data, as well as logins from high-risk locations, such as airports and unknown networks.
Once the OTP is generated and sent to the user’s mobile device or generated by a hard token in the user’s possession, the code is copied to the authentication window or other form that verifies the code with the authentication server. The user is then allowed access to their account.
What are the Benefits of Using One-time Passwords?
A one-time password expires quickly and cannot be reused, making it more secure than traditional passwords that users may reuse for multiple applications. Benefits include:
Prevents Compromised Credentials from being Successfully UsedBecause an OTP is a form of authentication factor required for MFA, a hacker using a compromised credential won’t be able to gain access to your resources without it.
| ||
Randomly-generated OTPs are Difficult to GuessHackers will have a hard time guessing OTPs, even if they have automated password cracking tools. The additional constraints of TOTP and HOTP make cracking the code even more difficult. | ||
Reduces Password FatigueUsers often have a hard time remembering passwords or use the same passwords for multiple applications. OTPs are automatically generated for a single use and don’t require the user to create or remember the password. | ||
Limits Friction for UsersPush notifications sent via SMS, email or voice make it fast and easy for users to verify themselves.
| ||
Reduces IT Staff Time for Password ResetsBecause OTPs are single-use passwords, help desks won’t have to worry about users forgetting them or needing to reset lost or stolen OTPs. | ||
Easy Integration and ImplementationOTPs can be integrated with MFA or third-party OTP authenticator apps can be used. OTPs are easy to scale to fit your needs, including big events and promotions. |
OTPs are just one type of authentication that may be used to verify a user's identity. To learn more about other types of authentication, read our Ultimate Guide to Authentication.
