What is Cloud Identity and Access Management (Cloud IAM)?
Cybercriminals are becoming more sophisticated in their efforts to breach networks, steal data and use ransomware to wreak havoc in order to get multi-million dollar payouts. Cloud identity and access management (cloud IAM) is a security framework deployed in the cloud used to verify users and control their access rights, including issuing and denying access privileges. Even if it resides in the cloud, a cloud-based authentication solution should let enterprises secure and control access to resources across all domains and platforms, from public and private clouds to on-premises systems, and allow users to authenticate from any device at any time.
According to the Digital Shadow Photon Research team, the average person uses almost 200 services that require them to enter passwords or other credentials. Its 2020 study found that 15 billion stolen credentials allowing account takeovers were available on the dark web, including username and password pairs for online banking, social media accounts and music streaming services. Ensuring compromised credentials cannot be used by bad actors to access your network is part of a strong cybersecurity strategy.
Read on to learn:
- What cloud IAM is
- How cloud IAM works
- The benefits of using cloud IAM
- Cloud IAM as part of a hybrid cloud strategy
- Types of cloud environments
What is Cloud IAM?
Authentication and access control are two of the capabilities of identity and access management solutions. Cloud IAM allows you to authenticate users no matter where they are and secure access to resources across cloud, SaaS, on-prem and APIs, all the while increasing your speed, agility and efficiency. IAM solutions are available for customers, employees and partners, and can be integrated to provide a complete solution for your enterprise.
With identity verification and access control located in the cloud, the limitations and costs associated with on-premises IAM are replaced by a more flexible, scalable solution. Cloud IAM is key to ensuring security outside of network perimeters and capabilities include:
- Authentication
- Access management
- Directory
- Identity verification
- Consent collection and data privacy management
- Risk management
- Personal identity
- API security
- Self-service for users and developers
The most common starting places for enterprises moving to the cloud are authentication and access security.
Authentication
Ensuring an individual is who they claim to be isn’t a new concept. Banks require proof of identity in order for customers to withdraw money and bartenders require youthful looking customers to verify they are old enough to buy alcohol. Authentication takes that process online, with multiple forms of proof required for increased security.
- Multi-factor authentication (MFA) uses two or more authentication factors to verify a user’s identity, and encompasses two-factor authentication (2FA). Authentication factors include something you know, something you are, and something you have. MFA and 2FA both provide layers of security to protect a user's account from hackers who may have guessed, stolen or bought passwords or primary credentials. For a high-value transaction, an enterprise using MFA could require a password (something you know), a one-time passcode sent to a smartphone or email (something you have), and a fingerprint scan on the smartphone (something you are). If any of these actions are not correctly completed, access is denied.
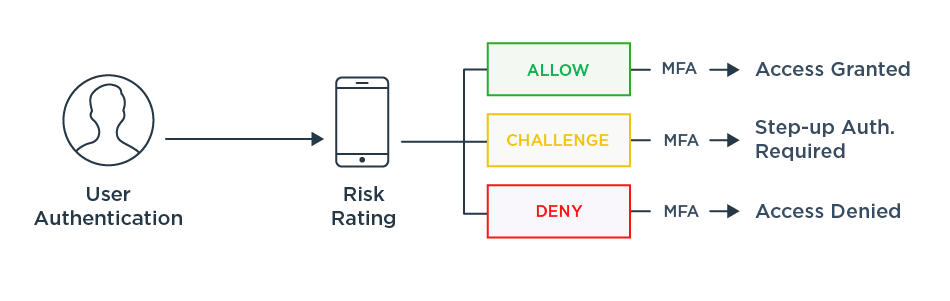
- Single sign-on (SSO), used in conjunction with MFA, gives users the ability to sign on once with their verified credentials to gain access to multiple services and resources. SSO combined with adaptive authentication lets you match authentication requirements to the access being requested, stepping up authentication requirements where needed, like a login from a high-risk IP address.
Access Control
Access management makes sure the right people are granted access to the right resources and nothing more. Even verified users can pose a threat to an enterprise, so following the principle of least privilege ensures access is limited to just what is needed by a user to safeguard sensitive information. For example, you don’t want customers to have access to employee-only resources or give all employees access to personnel files maintained by the HR department.
What are the Benefits of Cloud IAM?
Comply with Cloud-first Mandates
Digital transformation, including moving identity infrastructure to the cloud, is a high priority for some companies. Cloud IAM increases deployment speed because implementation is hosted in the cloud rather than on-prem, which would require investments in equipment and personnel. Upgrades are also easier, particularly when the service is managed by the vendor in the cloud.
Reduce IT Infrastructure and Support Costs
With more people working from home and using personal devices for work, shopping, social media and other activities, IT teams are required to manage more apps, resources and devices. On-prem IAM may be insufficient and the costs associated with employing and keeping in-house identity experts current on threats continue to rise, as does purchasing and maintaining equipment. Those costs can be greatly reduced using an Identity as a Service (IDaaS) or managed cloud service provider for cloud IAM.
Flexibility and Scalability
IAM solutions deployed in the cloud are available as a SaaS service, a managed service deployed in the vendor's private cloud, and as software deployed in the organization's own private or public cloud. Cloud IAM solutions are easy to scale for new users, such as when a company is adding hundreds of employees at a new location or an ecommerce site is running a promotion to attract thousands of new customers.
Enhance Security
Cloud IAM enhances security with capabilities like two-factor authentication (2FA) and multi-factor authentication (MFA) that reduce reliance on passwords and the potential data breaches that come from compromised credentials. Both 2FA and MFA verify a user’s identity using multiple authentication factors. Passwordless authentication streamlines access even further by reducing or even eliminating the use of passwords.
Improve User Experience
Single sign-on streamlines the login process and gives users faster and easier access to the resources they need. Cloud IAM solutions are available for customers, employees and partners. From customers looking for a frictionless login experience at ecommerce sites to employees trying to get their work done using multiple applications throughout the day, using one set of credentials saves time and frustration.
Minimize Password Reset Requests
IAM solutions minimize reliance on passwords and the risks associated with stolen or compromised passwords. It is estimated that upwards of 50% of IT help desk calls are attributed to password resets. Forrester estimated that a single password reset request costs companies an average of $70.
Increase Productivity and Reduce Frustration for your Workforce
Employees typically need access to a range of applications every day, such as email, online meetings, HR, finance or CRM systems, to name just a few. When workforce users are required to create new accounts for each and use multiple passwords, which they may forget, productivity goes down. By minimizing the time spent on logins, IAM helps employees, contractors and other workers gain access to the resources they need faster and with less friction.
Regulatory Compliance
Cloud IAM helps enterprises comply with open banking requirements like the Payment Service Directive 2 (PSD2) and data privacy regulations like the General Data Protection Regulation (GDPR) and the California Consumer Protection Act (CCPA). As regulations are updated and new regulations are implemented, IAM allows you to quickly adapt and stay in compliance.
Moving to the Cloud with a Hybrid Cloud Strategy
Even if your organization isn’t planning to migrate everything to the cloud, or is migrating to the cloud in stages, cloud IAM is the right place to start. A hybrid cloud strategy gives enterprises greater flexibility by balancing workloads between cloud and on-premises as IT needs shift and costs fluctuate.
Transitioning Identity and Access Control to the Cloud
You can transition IAM to the cloud using best practices for establishing and optimizing a cloud authentication authority, and following established paths to consolidate disparate legacy identity systems.
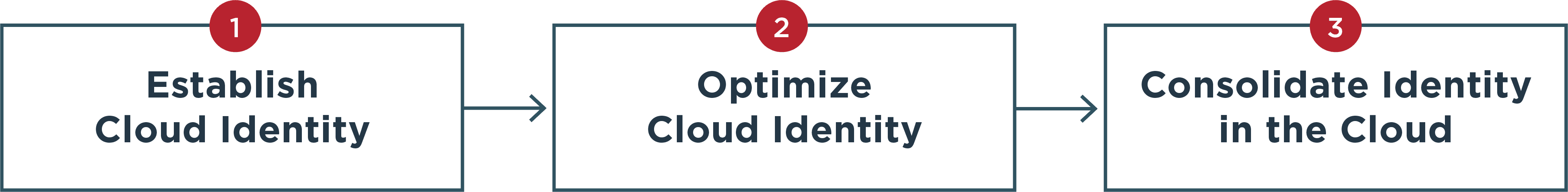
The journey to identity in the cloud commonly follows a three-step process to increase your speed, agility and efficiency while providing the flexibility to support unique requirements every step along the way.
- Establish Cloud Identity
A cloud authentication authority allows you to secure and control access to resources across all of your domains, from public and private clouds to legacy on-premises environments. - Optimize Cloud Identity
You can remove friction and make security visible only when it’s needed, creating seamless and secure experiences for your customers, employees and partners. You can also continuously validate identity, device and context data with cloud-based services like MFA, risk management, identity verification and others. - Consolidate Identity in the Cloud
Eliminate outdated, expensive, proprietary systems by modernizing your IAM infrastructure. Out-of-the-box or custom migration tools and integrations help you consolidate your legacy MFA, WAM and directory services in the cloud.
What Cloud Options are Available?
You can select the appropriate cloud option based on your needs, budget and use cases.
- Public clouds are hosted off premises, typically by major cloud service providers, including Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP).
- Private clouds are usually hosted locally by the enterprise, which provides security and flexibility.
- Partner clouds are often hosted in a public cloud by a partner, who manages the environment in a dedicated tenant that is unique to the enterprise.
- Hybrid clouds combine any or all of the above options. Enterprises often choose a hybrid cloud option for the balance of security, cost and flexibility.
- Multi-clouds (or multiclouds) often combine more than one of the three main public cloud providers: Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP).
Cloud IAM offers enterprises a cost-effective solution for verifying users’ identities and allowing them access to only the resources they need. Want to learn more? Read Ping’s Cloud Identity Buyer’s Guide.
FAQs for Cloud IAM
What is the Role of IAM in Cloud Computing?An identity and access management solution verifies users are who they claim to be before granting privileges to access information stored on cloud systems. IAM also manages access rights, such as granting rights to new employees or denying access to former employees. | ||
What is the Difference Between IAM and Cloud IAM?On-prem IAM software was an effective way to maintain identity and access policies when users worked within secure perimeters. As enterprises expand beyond on-prem and users need to access apps, websites and services from anywhere at any time on any device, moving IAM solutions to the cloud provides a more cost-effective, efficient solution. | ||
What are Cloud IAM Permissions?Cloud IAM permissions allow IT and security teams to control access to the resources in their cloud environments. Each cloud provider offers its own set of IAM capabilities with distinct permissions. | ||
What is the Difference between IAM and Privileged Access Management (PAM)?IAM focuses on identity and access control of general users, including customers, employees and partners. PAM focuses on privileged users, like system administrators, with elevated access and permissions for systems, processes, users and accounts. |
