What is Identity as a Service (IDaaS)?
Enterprises are embracing cloud and mobile technologies. As they do, they’re moving beyond traditional network boundaries and the capabilities of their legacy identity and access management (IAM) solutions.
Identity as a service (IDaaS) is a cloud-based subscription model for IAM, where identity and access services are rendered over the internet by a third-party provider rather than deployed on-premises. IDaaS can contain a range of services, but typically includes single sign-on (SSO), multi-factor authentication (MFA) and directory services that provide organizations with simple and cost-effective identity and access management capabilities. SSO typically uses either Security Assertion Markup Language (SAML) or OpenID Connect (OIDC).
Gartner defines IDaaS as, “a predominantly cloud-based service in a multi-tenant or dedicated and hosted delivery model that brokers core identity governance and administration (IGA), access and intelligence functions to target systems on customers' premises and in the cloud.”
Gartner states that the core aspects of IDaaS are:
- IGA: Provisioning of users to cloud applications and password reset functionality.
- Access: User authentication, SSO and authorization supporting federation standards such as SAML.
- Intelligence: Identity access log monitoring and reporting.
Why is IDaaS Growing in Importance?
The goal of IDaaS, as with a traditional identity and access management solution, is to determine that a user is who they claim to be and then grant access to applications once the user has been authorized. However, with current trends of a more mobile workforce and the proliferation of SaaS apps such as Salesforce.com, managing identities is much more complex and costly than it used to be.
Identity as a Service allows an organization to let a specialized third-party vendor manage the operational nuts and bolts of an identity and access management solution, saving administrative overhead for the organization because there is no longer a need to manage infrastructure, provide security, install and upgrade software, back up data, etc. IDaaS offers a scalable IAM solution that accelerates digital transformation while reducing cost and risk.
What are the Types of IDaaS
From a user's point of view, IDaaS provides similar capabilities to an on-premises deployment of identity and access management, assuming the user has access to the IDaaS cloud solution. The biggest difference is that IDaaS is hosted in the cloud by a third-party provider, which allows users to securely access their account from anywhere via different devices. This is done through a combination of single sign-on, multi-factor authentication and directory solutions.
There are many different types of IDaaS solutions. Some IDaaS providers support only one piece of the puzzle (e.g., providing only a directory) while other IDaaS providers deliver a more comprehensive suite of functionality encompassing multiple pieces of the puzzle (e.g., combined SSO, MFA and directory).
In addition to these different configurations of IDaaS solutions, different categories of IDaaS cater to different end users. Classes of end users include customers, employees and business partners.
Basic IDaaS
Basic IDaaS usually supports SSO into SaaS apps and provides the aforementioned benefits, which tends to work well for small- and medium-sized businesses and those organizations that were "born in the cloud." Organizations of this type and size do not usually have their own on-premises IT infrastructure to worry about and they are usually large consumers of SaaS apps. Multi-factor authentication can be used for increased security, and a cloud directory stores user data and credentials. Thus, basic IDaaS solutions can provide all the functionality needed for these businesses.
Basic IDaaS solutions also tend to have more streamlined interfaces, often including set-up wizards so that administrators can more easily solve less complex administrative use cases.
Enterprise IDaaS
Enterprise IDaaS is more robust due to the more complex IT environments that almost always exist in larger and older enterprises. These enterprises have a mix of on-premises, IaaS, PaaS and SaaS applications. In addition, enterprises typically use IDaaS to extend their existing IAM infrastructure. As a result, enterprise IDaaS providers must deploy solutions that can:
Bridge to existing user directories (like AD) for authentication.
Integrate with existing web access management (WAM) products to comply with access policies.
Integrate with a diverse mix of non-SaaS enterprise applications that reside in the company’s data centers or hosted in a third-party data center such as AWS or Microsoft Azure.
Provide access management for web, mobile and API environments.
The connectors, bridges and integrations provided by IDaaS solutions for enterprises allow for a more comprehensive solution. This additional functionality is combined with more fine-grained administrative controls to better customize solutions to an enterprise's specific needs.
-
Analyst Report
Enterprise IDaaS Requirements
Five key capabilities are required to make enterprise IDaaS solutions possible:
Single Sign-on (SSO): With single sign-on employees, partners and customers obtain easy, fast and secure access to all SaaS, mobile and enterprise applications with a single authentication using corporate credentials.
Multi-factor Authentication (MFA): MFA typically includes adaptive authentication methods—options to step up as risk increases based on situational changes, user behavior or application sensitivity.
Access Security: Access security is policy-based access management for applications and APIs to enhance security beyond SSO.
Directory: While most enterprises prefer to integrate IDaaS with their existing user stores, they may use a cloud directory, especially to support customers and/or partners.
Provisioning: Through SCIM support and integration with on-premises provisioning, user data is synced with web and enterprise applications.
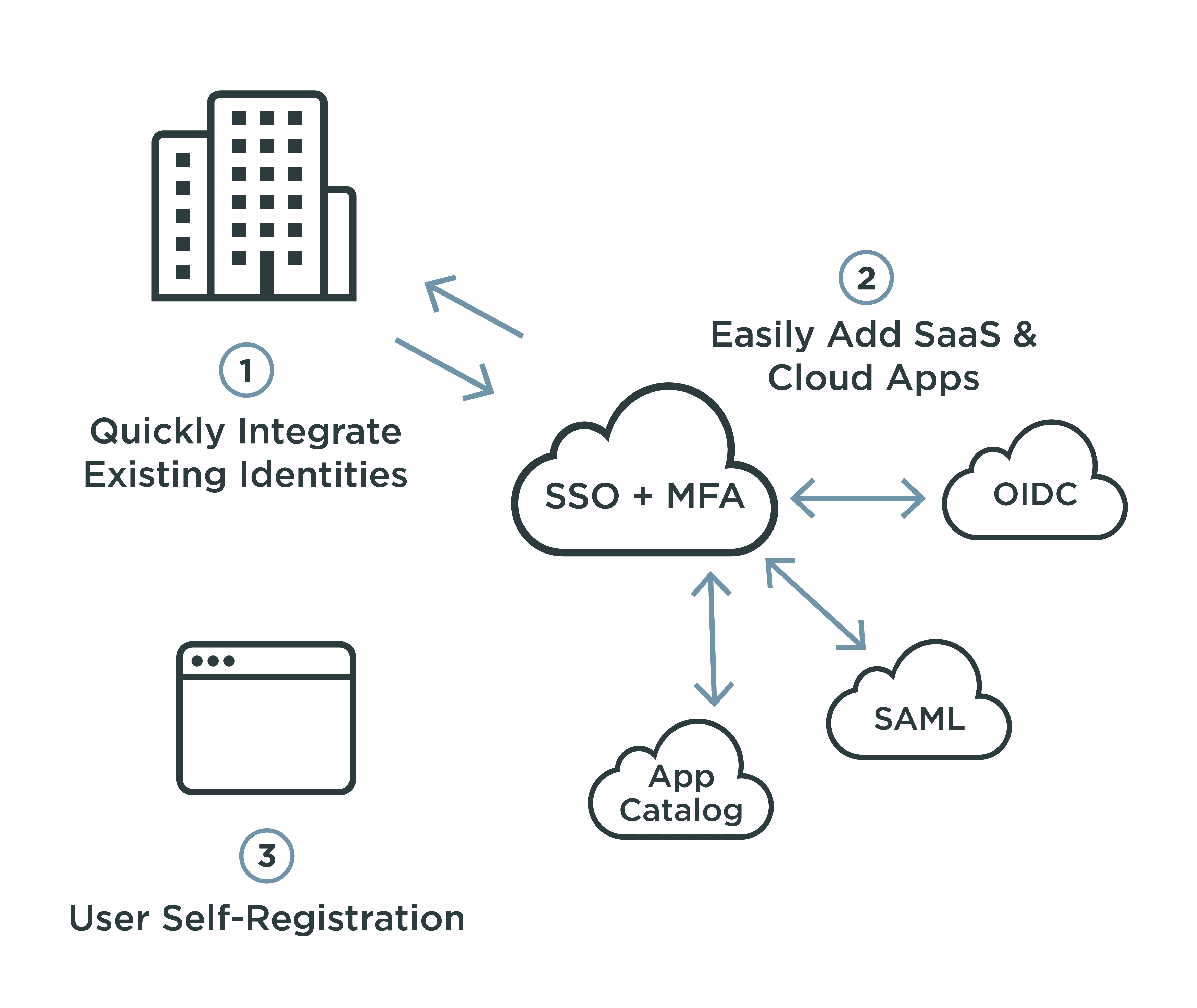
API-first IDaaS for Development Teams
Another way enterprises can leverage IDaaS is through API-first developer platforms. Often used for customer identity and access management (CIAM), these platforms expose all IDaaS capabilities through APIs. This approach allows enterprises to give their development teams a common IDaaS platform that makes it easy for them to embed identity services into their applications. It’s also important to ensure these platforms can meet broader enterprise requirements across all of their applications with:
A focus on security and reliability.
Support for common identity standards (OAuth, OpenID Connect, SAML).
Integrations that allow for coexistence with their on-premises identity infrastructure.
The ability to model their existing identity architecture in the IDaaS platform.
What are the Benefits of IDaaS
Reduce costs. Using a cloud-based IDaaS solution eliminates the need for equipment purchases, specialized IT staff and ongoing training, allowing your IT team to stay focused on day-to-day operations.
Better user experiences. Single sign-on and multi-factor authentication let users login with a single set of credentials, which reduces friction and password reset assistance.
Increase revenue and customer loyalty. A good first impression from a smooth login process leads to more customer interactions and sales.
Strengthen security. Outsourcing your IAM solution to experts limits the ability of bad actors with compromised credentials from entering your system and stealing data.
Scalable to meet your needs. Cloud-based subscription services adapt easily to changing user bases, such as an influx of new customers for events and promotions.
Risk mitigation. Identity solutions reduce your risk of a data breach, which could cost your organization millions of dollars.
Learn more about the benefits here: The Impact of Identity
IDaaS helps organizations save money and time while taking advantage of specialized IT expertise. It enables users to securely and easily access needed apps on a variety of devices while on the go or at the office.
Start Today
See how Ping can help you deliver secure employee and customer experiences in a rapidly evolving digital world.
Request a free demo
Thank you! Keep an eye on your inbox. We’ll be in touch soon.