What Is Single Sign-on (SSO)?
What is Single Sign-on?
Single sign-on (SSO) allows a user to sign on with one set of credentials and gain access to multiple applications and services. SSO increases security and provides a better user experience for customers, employees and partners by reducing the number of required accounts/passwords and providing simpler access to all the apps and services they need.
How Does Single Sign-on Work?
To enable SSO, an organization known as the identity provider (IdP) must implement a centralized authentication server that all apps can use to confirm a user’s identity. This server can validate user identities and issue access tokens, the encrypted bits of data that confirm the user’s identity and privileges.
The first time a user signs on, the username and password are directed to the identity provider for verification. The authentication server checks the credentials against the directory where user data is stored and initiates an SSO session on the user’s browser.
When the user requests access to an application within the trusted group, instead of requesting a password, the service provider requests that the identity provider authenticates the user’s identity.
The identity provider provides an access token, and the service provider grants access without ever showing the sign-on screen to the user.
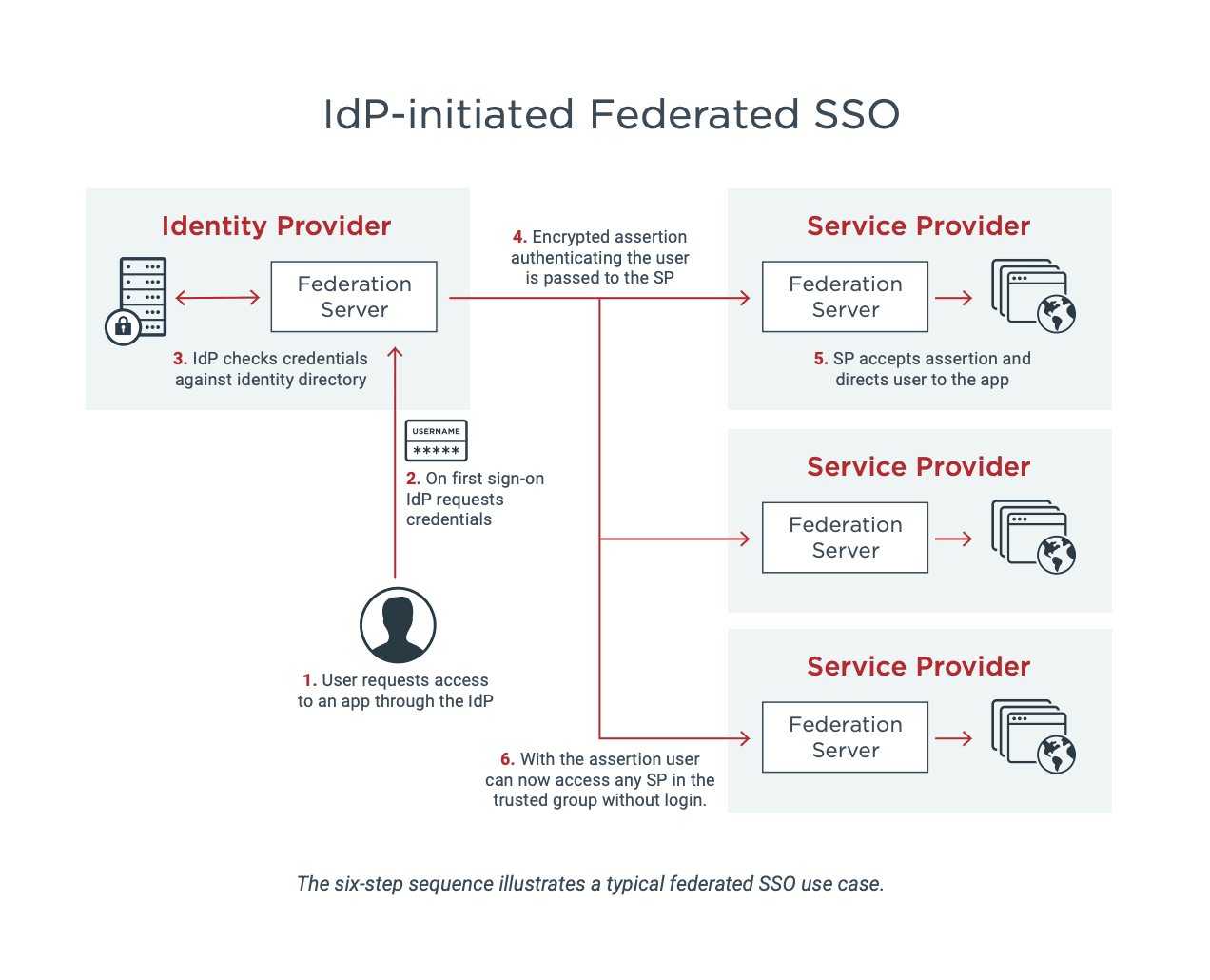
Types of Single Sign-on
In the past, when all applications were on-premises, the requirements for single sign-on solutions were simpler. An employee would sign on to an SSO session, be authenticated against the single directory and gain access to multiple apps that were all within the same organization, without needing to re-enter a username and password each time. This is single sign-on at its most basic.
But today’s business environments are much more complex. The proliferation of on-premises, cloud and SaaS applications requires more robust single sign-on solutions—but makes SSO exponentially more valuable. Many enterprises today employ federated SSO to enable authentication with a single set of credentials across multiple organizations and security domains. This means they can provide secure single sign-on to a trusted group of applications or “service providers,” even when the apps are owned by third parties or sit outside their firewalls.
What is Cloud Single Sign-on (Cloud SSO)?
Another type of single sign-on is cloud SSO. Cloud applications have become a vital part of an enterprise's productivity, infrastructure and operational needs. With more employees working from home and rising customer experience expectations, organizations are looking to easily connect everyone to everything with cloud SSO. Cloud single sign-on provides centralized access management and lets users authenticate their cloud-based applications and services with a single identity for trusted providers. By eliminating the need for re-authentications, cloud SSO streamlines the process while offering secure user access to multiple apps and services.
Standards for Single Sign-on
What makes this exchange possible is the use of identity standards such as SAML, OAuth and OpenID Connect. Standards enable the secure sharing of identity data among multiple service providers and identity providers. Without standards, each connection would require customized development, which would quickly become cumbersome and unsupportable.
There are a few different standards because newer standards have been established over the years that are more suited for web-based and SaaS-based apps than older standards that work better with older apps. They each have their own strengths, so any enterprise SSO system should support the full set.
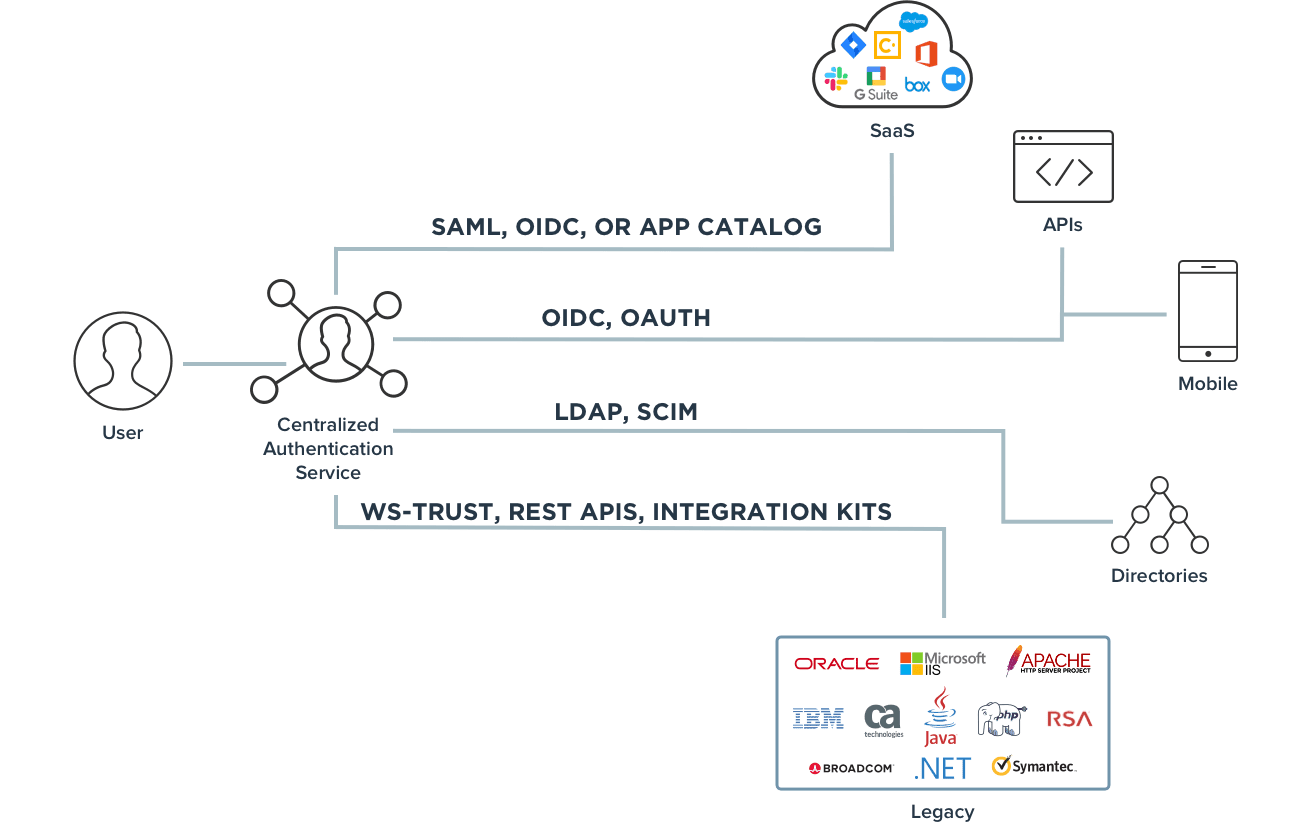
Benefits of Single Sign-on
From social media to online shopping, collaboration tools to specialized business applications, it’s becoming an impossible task to remember so many unique usernames and passwords. Many of us are probably guilty of choosing weak passwords that are easier to remember or writing our passwords down, and more than 80 percent of people ages 18 and up reuse the same password across multiple accounts.
Repeated sign-on requests are also a hassle, for both customers and employees. An online business might require separate passwords for different parts of its website. An employer might require an employee to sign on to each business application individually. Talk about a time suck!
When it comes to providing the most simple, secure experience across all channels, single sign-on goes a long way toward reducing frustration while also decreasing the chance of a security breach.
Improved Experience
Single sign-on replaces the frustration of signing on to each app individually and remembering multiple sets of credentials with the convenience of single-click access. Employees can be more productive, and customers and partners get a frictionless experience that makes it easier to do business. SSO on mobile devices also offers a key advantage at a time when customers use their phones for everything and 72% of organizations allow or plan to allow “bring-your-own-device.”
Higher Security
By requiring single sign-on, an organization reduces the heavily targeted attack surface of user credentials down to one. And that one set of credentials can be more carefully secured. For example, single sign-on helps keep user data more secure by using tokens to authenticate, rather than forwarding passwords or storing credentials on user devices.
Lower Costs
Password resets can cost enterprises an average of $179 per employee per year, according to a Forrester Research study. Multiply that by the number of users and the IT costs get high, fast. Fewer passwords mean fewer resets and less time and money spent on user administration.
Single Sign-on Examples
To illustrate how helpful single sign-on can be, here are a few real-world examples:
- An employee signs on to their company email account in the morning, using their email address and password. For the rest of the day, they access all their applications—instant messaging, the intranet site, sales data, IT help desk and their timesheet—without ever needing to provide another password.
- A banking customer signs on to their bank to check their savings balance. They then seamlessly transition over to the mortgage application, check their credit score and alert customer service about an upcoming trip. On the backend, each of these services is a separate application, but the customer never has to provide another password.
- A retailer has an extensive network of supply chain and distribution partners. These partners can log into the application dock once, and then access all the applications and services the retailer has enabled for their use from one place, without further logins.
Is Single Sign-on the Best Security Approach?
Although single sign-on has many benefits, some might still question whether it’s the best approach to security for their employees and customers. If you allow users to rely on one set of credentials to access everything, you’d better be sure those users (and your systems) are protecting their credentials properly. Once a hacker gets their hands on them, their access will extend to all the user’s apps and services. Unfortunately, even if you have the best security technology in the world, a user’s password can still be compromised through phishing scams, reuse on a hacked site or other unsafe behavior.
Securing one strong set of credentials is still much easier than managing many, and smart organizations are implementing multi-factor authentication to beef up security at the point of sign in. This requires users to provide an additional piece of evidence beyond a password to prove they are who they say they are. Advanced solutions can even use intelligence to assess the risk level of a given user or their actions to decide whether to step up security or not.
SSO Gives Users the Experience and Security They Expect
As IT environments get more complex and user experience expectations get higher, organizations that invest in single sign-on will have a leg up over the others. With single sign-on, they can improve security by reducing the number of required passwords, decrease IT costs associated with password management, and provide a seamless experience. They’re empowering employees to be more productive, and giving customers effortless access to all their applications—sometimes without the users even knowing it!
To learn more about single sign-on and how it works, check out our Essential Guide to Single Sign-on.
FAQs for Single Sign-On
What does sign-in with SSO mean?Single sign-on, or SSO, allows users to access multiple applications with one set of credentials. That means you can sign in once to a business’ system (your employer or a business site you’re using online) and then you don’t have to enter your username and password each time to access each app they have. It reduces the number of separate accounts and passwords you need to manage. | ||
What is SSO authentication?SSO authentication enables users to sign on via an identity provider, which then gives them access to all the applications that are a part of the same trusted identity system. SSO authentication is different from a password manager, which simply stores multiple passwords in a vault for easy retrieval during sign-on. | ||
How much does SSO cost?The cost of single sign-on can vary based on the complexity of the solution and the features that come with it, such as contextual authentication. It’s usually priced per user per month. | ||
Is single sign-on safe?Yes. SSO offers a safe way for users to access multiple related applications without having to re-enter their credentials every time. This reduces the number of opportunities for a bad actor to take advantage of a compromised password since each user only has to sign on once. SSO systems also exchange secure access tokens, rather than sending passwords back and forth, keeping the sensitive information more secure. | ||
What is meant by a single sign-on?Single sign-on, or SSO, means that a single log in will give a user access to multiple applications within the same system. For example, employees can access all their company’s apps and websites, usually through an application portal, after signing in just once. Customers can also get access to multiple separate services provided by a business without needing to create separate accounts. | ||
What is the best single sign-on solution?SSO from Ping Identity can authenticate users from any device, for any application, using any directory. It easily integrates with apps across the enterprise, as well as third-party services and existing infrastructure, with comprehensive support for modern identity standards. Ping Identity has helped enterprises around the world improve security, customer engagement and workforce efficiency. | ||
What is the difference between SSO and MFA?The main difference between single sign-on (SSO) and multi-factor authentication (MFA) is that with SSO, you only need to enter one set of credentials to log in to all applications. MFA requires users to enter two or more authentication factors when signing in. SSO and MFA are often used together to make log in easier and more secure by eliminating the need for multiple logins but then adding MFA security to the single point of authentication. | ||
Why is SSO required?Single sign-on (SSO) is important, and often required by large enterprises, because it decreases the potential for data breach by reducing the number of passwords in use across the business—a highly targeted hacking attack vector. It also improves the experience for employees and customers: employees get faster, easier access to all the resources they need to do their jobs, while customers get a seamless experience with minimal friction around logging in. |
