Top Benefits of SSO and Why It's Important for Your Business
Benefits of Single Sign-on
Single sign-on (SSO) has been prevalent in many organizations for years, but its importance is often overlooked and underappreciated. With many enterprises moving to the cloud and taking advantage of third-party services, seamless access to multiple applications from anywhere and on any device is essential for maintaining business efficiency and a seamless customer experience.
Read on to learn about what single sign-on is and the benefits of this incredible technology for both businesses and end users.
What is SSO and How Does it Work?
Single sign-on is an authentication process that allows users to securely access multiple related applications or systems using just one set of credentials. Ideally, once SSO has been set up, employees or customers can sign on just once to gain access to all authorized apps, websites and data from an organization or a connected group of organizations.
SSO works based on a trust relationship established between the party that holds the identity information and can authenticate the user, called the identity provider (IdP), and the service or application the user wants to access, called the service provider (SP). Rather than sending sensitive passwords back and forth across the internet, the IdP passes an assertion (often via an identity standard such as SAML) to authenticate the user for the SP.
If the user is not already authenticated, here’s a simple explanation of the sign-on process:
Step 1: The user browses to the website or application they want access to (the SP).
Step 2: The SP sends a request and redirects the user to the SSO system (the IdP).
Step 3: The user is prompted to authenticate by providing credentials required by the IdP, such as a username and password.
Step 4: Once the IdP validates the user's credentials, it sends an assertion back to the SP to confirm successful authentication. The user will then be granted access to the desired application.
Once this process is completed, any other SPs the user wants to access will confirm the user’s previous authentication with the IdP and not require a username or password.
What is the Purpose of SSO?
Single sign-on’s main purpose is to give users the ability to log in to individual apps and resources within a trusted group using a single set of credentials. This makes it much easier for the user, who doesn’t have to sign on multiple times, and more secure for the business, since there are less opportunities for a password to be lost, stolen or reused.
What are the Benefits of SSO?
Your employees and customers probably don't like memorizing many different credentials for multiple applications. And if your IT team has to support multiple apps, setting up, switching and resetting passwords for users requires countless hours, IT resources and money that could be spent elsewhere.
Below are the reasons why you should start using SSO in your business as soon as possible.
Increased Productivity
Single sign-on increases employee productivity by reducing the time they must spend signing on and dealing with passwords. Employees need access to many apps throughout their workday, and they have to spend time logging in to each of them, plus trying to remember which password goes to which, plus changing and resetting passwords when one is forgotten. The wasted time adds up.
Users with just one password to access all of their apps can skip all that extra time spent logging in. They also won't need password support as often, and SSO solutions often give them access to a handy dock where all their apps are at their fingertips.

Improved Security
A common myth about SSO solutions is that they compromise systems' security. This misconception is based on the idea that should a master password be stolen, all related accounts will be exposed.
However, the reality is that with good practices, SSO significantly decreases the likelihood of a password-related hack. Since users only need to remember one password for all their applications, they are more likely to create solid, complex and hard-to-guess passphrases. They are also less likely to reuse passwords or write them down, which reduces the risk of theft.
An excellent strategy to provide an additional layer of security is to combine SSO with multi-factor authentication (MFA). MFA requires that a user provide at least two pieces of evidence to prove their identity during sign-on, such as a password and a code delivered to their phone.
Risk-based authentication (RBA) is another good security feature, in which your security team uses tools to monitor user behavior and context to detect any unusual behavior that may indicate an unauthorized user or cyberattack. For example, if you notice multiple login failures or wrong IPs, you can require MFA or block the user completely.
Decreased IT Costs
A recent study by Gartner reveals over 50 percent of all help desk calls are due to password issues. Another study by Forrester reveals password resets cost organizations upward of $70 per fix. The more passwords a user has, the greater the chance of forgetting them, so SSO drives down help desk costs by reducing the number of required passwords to just one.
And some organizations have been implementing specific password requirements like length and special characters that may make passwords more difficult for users to remember—a trade off of more secure passwords for more password resets. SSO can help alleviate some of those costs.
Improved Job Satisfaction for Employees
Employees are using more and more apps at the workplace to get their jobs done, and each third-party service requires a separate username and password. This places a lot of burden on workers and can be frustrating. Notably, an average of 68 percent of employees have to switch between ten apps every hour.
Only having to sign on once improves employee productivity, as discussed above, but it also enhances their job satisfaction by allowing them to work without interruption, quickly access everything they need, and take advantage of all the useful third-party apps that make their jobs easier. Easy access is particularly valuable for employees that are in the field or working from multiple devices.
Enhanced Customer Experience
One of the most valuable benefits of implementing SSO is an enhanced customer experience. A recent study reveals up to 18.75% of users abandon their carts because of password reset issues or forgotten passwords. Whether you’re a retailer, a healthcare provider or a bank offering multiple services, SSO will help you alleviate these issues and give your customers access to everything they need with just one sign-on. They’ll enjoy a more seamless experience with less friction and less frustration. The immediate benefits of improved user experiences include customer loyalty, higher conversion rates and enhanced brand visibility.
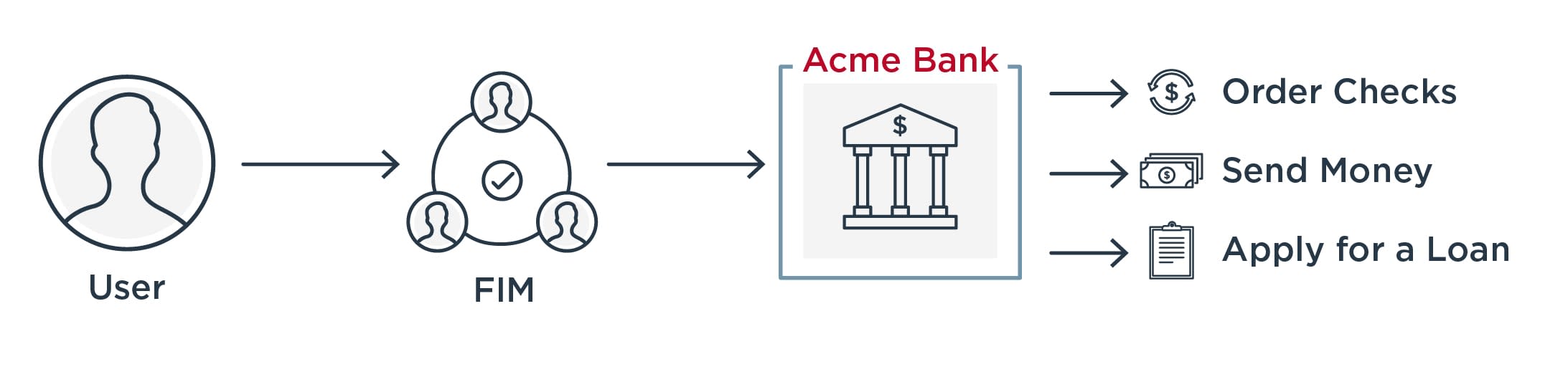
Increased Adoption Rates
There is no doubt that a new app that frustrates customers with a painful sign-on process will not enjoy as much success as one that offers an easier experience. Today’s competitive landscape ensures that there is always another option for customers to choose if yours presents them with too much friction or confusion. SSO increases the chance that users will choose your app and use it more frequently.
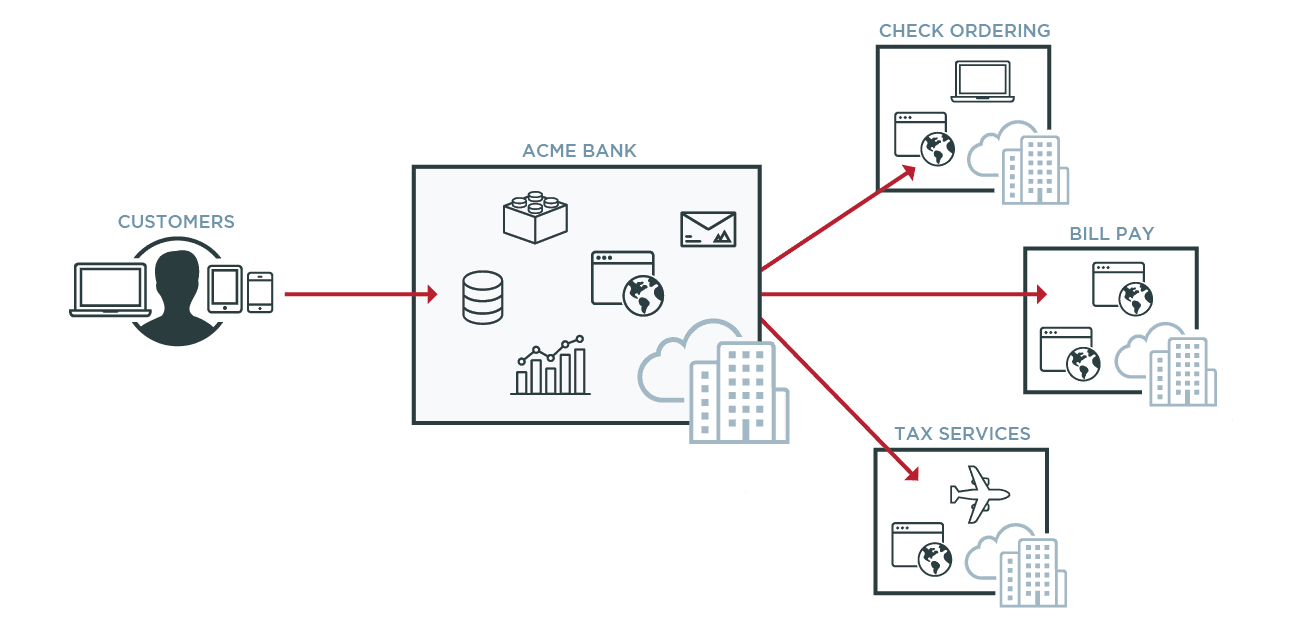
Tighter B2B Collaboration
SSO plays a critical role in the success of B2B partnerships as well. Everything from cars and phones to essential home items are built and distributed through collaborative efforts between multiple enterprises. This type of business collaboration requires giving employees from other companies access to specific data, digital tools and applications. Federated SSO (or federated identity management) can help create more efficient and effective collaboration between businesses by bridging identity systems.
Businesses also often collaborate to provide related services to joint customers. Setting up federated identity management across security domains makes it easier for customers to access related services from their single account, even if those services are coming from different companies.
Regulatory Compliance
Industry regulations like Sarbanes-Oxley and HIPAA require companies to implement security measures to protect data against cybercriminals and unauthorized use or disclosure. Single sign-on is often implemented as part of a broader identity and access management (IAM) solution which can help you comply with regulations that require strong authentication and access control. IAM can also help businesses comply with other regulatory requirements pertaining to privacy, activity tracking and single logout.
Single Sign-on Enables Customers and Employees
With each passing day, the tech world presents us with more systems and applications to use in our everyday lives. Memorizing complex passwords for each of these apps is a challenge and can become a security risk. However, by implementing single sign-on, you can give your customers and employees the ability to access different applications and services easily, quickly and more securely.
Chances are you’ve accessed a website or an app via single sign-on in the last few days. Now you understand how the technology works and why it’s critical for your business. If you’re ready to start evaluating SSO vendors to enable your employees, read our buyer’s guide to understand the most important requirements and considerations for workforce SSO.
What’s an Example of Single Sign-on?An excellent example of SSO can be found within Google's suite of applications. Once a user signs on to Gmail, they automatically gain access to other Google services, including YouTube, Google Drive and Google Photos. | ||
What are the Disadvantages of Authentication Without SSO?An immediate impact of not having SSO is the need for each user to maintain several passwords for different applications. Due to the complexity of passwords, users may keep their login information in unsecured places, choose only simple, easily guessed passwords or reuse passwords multiple times. All of these practices increase the risk of password theft and cyberattacks as well as the need for password resets. Users must also ensure they manually log out of each app once they are done. | ||
Does SSO Improve Security?Usernames and passwords are the most critical details that cybercriminals target. Every time a user creates a new password for a new application, they are opening up another opportunity for hackers to compromise the system. Reducing logins to one set of credentials definitely improves your organizational security. Ideally, with single sign-on, users only log in once each day and only use one set of credentials, reducing the number of attack vectors substantially. | ||
Is SSO Encrypted?In a typical SSO flow, assertions are passed between the identity provider and the service providers, and these assertions can be encrypted. Additionally, the identity provider typically checks a user’s credentials against the encrypted identity data stored in a highly secure directory. | ||
How Can I Secure My SSO System?Even though SSO features robust protection, it’s still important to strengthen your system by filling the security gaps. You can boost the security of your SSO system by doing the following:
| ||
What Does SSO Mean in Zoom?If the company has a Zoom account and has set Zoom up as a service provider in their SSO network, employees don’t have to sign on to Zoom directly to use the service or register for an individual account. They can use the same set of company credentials to get access, usually through a company application dock. | ||
What are the Major SSO Challenges Organizations Should Know?Some of the major SSO challenges that organizations should expect are: Challenges integrating applications: One of the main challenges during the implementation of SSO is integration with various systems and applications. Legacy technology with obsolete architecture that lives on-premises or homegrown applications that don’t work with typical identity standards can often be challenging to connect. The best way to ensure interoperability is to choose an extensible identity vendor that supports open standards as well as many out-of-the-box integrations. Accessibility challenges: When the single sign-on service is down, access to all connected sites may also go down. The provider's vulnerability to any interruptions becomes yours. For this reason, organizations need to exercise a lot of care when choosing an SSO vendor. An ideal system should be exceptionally reliable—99.99% uptime is ideal. You should also develop backup plans in case of outages. Data Breaches: Should a hacker steal a user’s credentials, all of that user’s applications would be compromised because of the reliance on one password for access. However, you can significantly reduce this risk by requiring your users to follow good password practices, educating about the common signs of phishing and implementing MFA. |
