What is Online Fraud Monitoring?
Online fraud includes financial fraud and identity theft on digital channels, such as websites and mobile apps. The amount of money lost to online fraud continues to rise, accelerated by enterprises unprepared for the sudden shift from brick-and-mortar transactions to online engagements during the pandemic. Javelin Strategy & Research reported that consumers lost $56 billion to identity fraud in 2020. Juniper Research projected eCommerce losses due to online payment fraud could exceed $20 billion in 2021.
Online fraud can occur at any stage of the user journey, not just at checkout. Unlike real customers who spend time browsing or searching for what they need, bots and fraudsters work quickly and directly to complete their fraudulent activity. Monitoring and early detection reduce the number of fraud incidents and the overall cost of fraud.
Read on to learn about different types of online fraud and ways to detect, monitor and prevent bad actors from scamming your enterprise.
Types of Online Fraud
There are numerous types of online fraud that occur at various stages of the user lifecycle, including account takeover (ATO) fraud, new account fraud and checkout fraud. Bots can be used for all types of fraud, often as an initial test to see how your system responds.
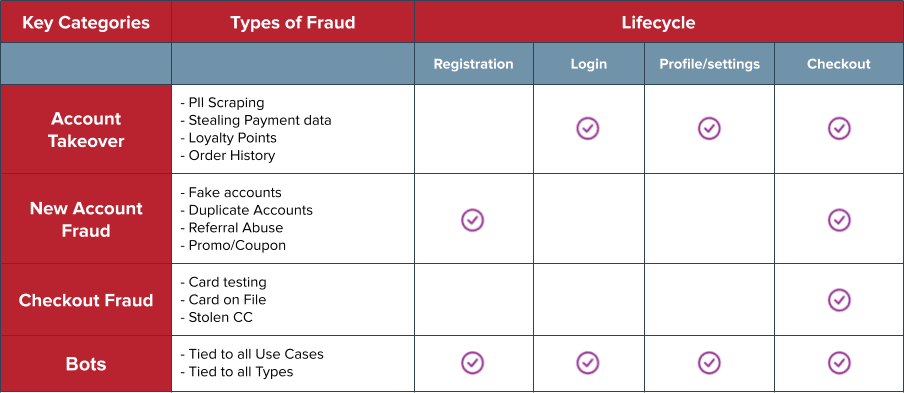
There is a ripple effect with each type of fraud. Riskified's 2021 study found that account takeovers are on the rise, with 43 percent of U.S. merchants saying ATO fraud accounted for over 10 percent of their chargebacks. Since compromised accounts and fake accounts are often used multiple times, fraud detection stops more than an isolated incident.
Account Takeover Fraud
Account takeover (ATO) fraud can include transaction fraud and non-transaction fraud, such as stolen loyalty points. Fraudsters use compromised credentials obtained through phishing attacks, data breaches or bought on the dark web to access a legitimate user's account. After initial tests of the compromised credentials, such as changing a shipping address or password, the fraudster moves on to financial transactions. The personal identifiable information (PII) obtained through account takeover fraud allows fraudsters to open new accounts or take over additional accounts in the future.
New Account Fraud
Using stolen credit cards and/or PII obtained through account takeovers, new accounts are created by fraudsters to carry out a variety of activities. Coupon and promo codes designed for new users can be used by fraudsters to purchase goods and services. Referral codes can be exploited by bots or shared on social media, racking up referral points from strangers. After goods or services are purchased, the fraudster can seek refunds and leave merchants liable for chargebacks.
Checkout Fraud
To avoid creating new accounts, fraudsters use stolen credit card information and the "Guest Checkout" option on websites and apps to commit checkout fraud. Bad actors often use bots to automate the testing of stolen credit card numbers on one website or app, then manually enter the same card information at a later date on different sites, along with discount codes, to look more like legitimate customers.
Online Fraud Detection
When you are able to prevent fraud by challenging fraudsters during their initial interaction with your site or app, you avoid problems for your enterprise and your customers. Whether it is new account fraud, account takeover fraud or checkout fraud, detecting fraudulent activity before the transaction occurs limits financial and reputational damage.
Online fraud detection uses machine learning and artificial intelligence (AI) to prevent fraudsters from creating accounts, logging in and completing transactions. Legitimate login attempts and account activity by customers, employees and partners follow predictable patterns, while bot and hacker behavior tends to deviate from the norm.
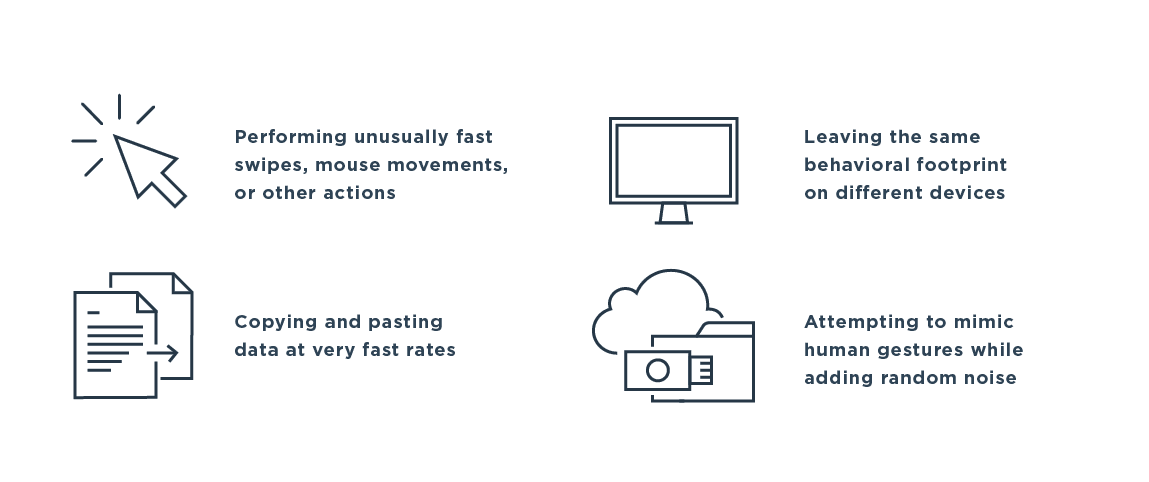
Insight into the difference between normal and atypical behavior requires collecting and analyzing multiple data points on an ongoing basis from different enterprises to identify new threats as they develop.
User and Entity Behavior Analytics (UEBA)
To customize fraud detection and monitoring for your organization, data points for every authentication attempt are analyzed to distinguish between normal and anomalous behavior. User and entity behavior analytics (UEBA) risk assessments include variable such as:
- Username
- Device type, operating system and version
- Browser type and version
- Date, time and location of authentication
For example, a finger swipe on a mobile device has multiple dimensions, such as pressure, angle and device orientation. A bot trying to login as that user will not be able to replicate those actions. A red flag could also be a user account logging in from a mobile device in one country and a desktop device in another country in a short period of time.
Bot Detection
Bots can be used at any stage of the user lifecycle for online fraud, using scripts to conduct the same actions over and over again. Bots are becoming increasingly capable of mimicking human behavior, with some bots being more successful with Captcha challenges than real people. These challenges add friction for actual customers, who give up in frustration. Bot detection tools need to limit friction for legitimate users while identifying and stopping bots.
Online Fraud Monitoring
Online fraud detection tools are also used for fraud monitoring throughout the user journey - from how accounts are created to where and when users access their accounts. Beginning with a user's first interaction, online fraud monitoring uses machine learning and artificial intelligence (AI) to spot anomalies between legitimate users and fraudsters or bots. Monitoring sessions in real-time rather than focusing solely on transactions means fraudulent activity is uncovered before a transaction occurs.
Online Fraud Prevention
In addition to fraud detection and monitoring, a comprehensive risk management strategy also includes fraud prevention.
Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) and two-factor authentication (2FA) require users to provide proof of their identity from multiple categories before access to an account is granted, including:
- Something you know
- Something you have
- Something you are
While fraudsters may be in possession of compromised credentials, like username-password combinations, they rarely possess other forms of authentication. Without the additional forms of authentication, access to legitimate user accounts is denied.
Identity Proofing
Identity proofing, also known as identity verification, ties users' digital identities to their real-life identities. Identity proofing typically occurs during the registration process and can be integrated into mobile apps to help ensure customers are who they claim to be. Without the verification step, fraudsters with stolen credentials or identities may go undetected. Identity verification can include a driver's license, government issued ID card, or biometric data, such as fingerprints or photos that can be used for facial recognition.
Learn More about Online Fraud Detection
Please watch our webinar to learn more about proactively detecting fraud: Early Bird Gets the (Fraud) Worm: How to Proactively Detect Online Scams.
