What is Account Takeover (ATO) Fraud?
Account takeover fraud, also known as ATO fraud, is a form of identity theft where fraudsters use your compromised credentials to log in to an online app or service as you. Imagine trying to get money out of an ATM, but your ATM card PIN no longer works. When you try to log into your account using the bank’s app, you discover your password has been changed. You must now prove your identity to the bank, after which you learn your bank account has been completely drained by a fraudster.
Financial services, online retail, social media, video streaming and entertainment are among the most targeted industries for account takeover fraud. ATO fraud uses existing, legitimate accounts and their stored (or stolen) credit card information, loyalty points and other data. A fraudster gains access to the account, makes purchases, then uses or resells the merchandise, seeks refunds and/or sticks merchants with chargebacks.
Riskified's 2021 study found that ATOs are on the rise, with 43 percent of U.S. merchants saying ATO fraud accounted for over 10 percent of their chargebacks. Losses went beyond direct costs and included lost customer lifetime value (CLV), costs associated with customer service operations, and long-term damage to the brand's reputation.
Credential stuffing tools, password cracking tools, phishing and social engineering schemes, combined with personal identifiable information (PII) available on the dark web, make account takeover attacks common. A 2020 study by the Digital Shadows Photon Research Team found 15 billion stolen credentials available on the dark web, including username-password pairs for online banking, social media accounts and music streaming services.
Online payment fraud will cost eCommerce merchants $25 billion annually by 2024.
Online Payment Fraud: Emerging Threats, Segment Analysis & Market Forecasts 2020-2024, Juniper Research
Account Takeover Fraud Statistics
According to research by Security.org and data from cybersecurity firm Deduce, 22 percent of U.S. adults have been victims of account takeovers, which amounts to over 24 million households. The research also found that 60 percent of account takeover victims used the same password as the compromised account for multiple accounts. In addition, one third of login attempts for financial services and financial technology companies were suspected account takeover attempts.
The pandemic led to more people shopping online and a significant increase in ATO attempts. According to research by Sift, attempted fraudulent logins increased 282 percent. Merchants specializing in the sale of physical goods saw an increase in ATO attempts of 378 percent. ATO fraud also damages brands, with 28 percent of survey respondents saying they would completely stop using an e-commerce site or service if their accounts on that site were hacked.

https://www.pymnts.com/news/retail/2020/ecommerce-fraud-costs-prevention/
ATO fraud isn't limited to personal accounts. According to the FBI, business email compromise (BED) was one of the costliest forms of fraud in 2020, accounting for $1.8 billion in losses. With this form of account takeover, the fraudster gains access to a business's email account and makes unauthorized fund transfers.
How does Account Takeover Happen?
Account takeover is completed through a series of steps:
- The fraudster gains access to victims' accounts, typically using compromised credentials.
- The fraudster starts with small, non-monetary changes to account details, such as:
- Modifying personally identifiable information (PII)
- Requesting a new card
- Adding an authorized user
- Changing the password
- After one or more of the changes is successfully completed, the fraudster is free to continue with financial and other transactions. Victims' accounts may include saved payment information, additional PII or rewards points that provide useful data for money transfers, large purchases, taking out loans in victims' names and taking over more accounts. The more information the fraudster can gather, the easier it becomes to access more of the victim's accounts and services.
Account Takeover Fraud Methods
There are numerous methods a bad actor can use to get the credentials needed for account takeover, in addition to data breaches or buying them on the dark web. Account takeover fraud methods include:
Phishing and Social Engineering
Phishing schemes, often conducted via email or text, are designed to get victims to provide account information to fraudsters. Social engineering takes phishing to the next level, tricking victims by impersonating legitimate organizations, like government agencies and banks, or victims' family and friends. We've all gotten emails or texts from "banks" saying our accounts are locked and we need to provide login information for account recovery. Or "friends" who ask us to click on a link, which will install spyware or other malware on our computer or mobile device. Victims who unknowingly fall for these types of fraud provide bad actors with easy access to their accounts.
Phone Scams
Seniors are often the target of phone scams, since they may have listed phone numbers, own a home and have savings and good credit. Seniors with dementia or other challenges are at higher risk of fraudsters repeatedly taking advantage of them. Scammers pretend to be tech support in need of access to the victim's computer or a grandchild who needs banking information in order to transfer funds for an emergency. The FBI estimates elder fraud results in $3 billion in losses annually.
Unsecure WiFi
Personal WiFi needs to be secure, which may require changes to default settings. The same is true of security settings on Internet of Things (IoT) devices that use WiFi, like doorbell, thermostat and garage door apps, which can be hacked and allow access to a network. Public WiFi should never be used for anything important, especially when it involves logging into accounts. A bad actor can set up a man-in-the-middle attack by creating a fake wireless access point in a public location, like a coffee shop, and use it to intercept your internet activity.
Credential Stuffing / Password Cracking / Brute Force Attacks
Credential stuffing uses bots to test compromised credential combinations on multiple websites or apps to access accounts. Password cracking tools automate the use of leaked or stolen usernames with dictionaries of common passwords, sometimes supplemented with custom dictionaries, to access accounts. Brute force attacks are a popular cracking technique that involve trying different variations of symbols or words until the correct password is figured out.
Account Takeover Fraud Examples
Examples of account takeover fraud exist in many industries. Because these attacks can go undetected for months, bad actors remain active. When financial gain is the goal, account targets can include banking, credit cards, e-commerce sites and any business where employee credentials could lead to a payout. A bad actor that takes over a bank account or credit card account can send funds to their own accounts or make purchases on e-commerce sites, including gift cards. The purchases can then be sold, making them hard to trace.
In addition to financial gain, other reasons for account takeovers include: collecting data about family, friends and colleagues for additional attacks; collecting healthcare and other sensitive information for extortion; and/or damaging reputations using compromised social media accounts. Social media account takeover can be detected quickly if the user is high profile and the fraudulent posts are obvious. For example, in 2016, Katy Perry's Twitter account, with 89 million followers, was taken over and used to slur other singers and urge Perry's followers to follow another account.
Cybercriminals can get creative with their actions. For example, a fraudster can take over a victim's Airbnb account or other booking service account. The booking looks legitimate to Airbnb and the credit card company, so the fraud goes undetected. The victim only discovers the fraud after seeing the credit card bill, but the victim is locked out of their Airbnb account. The fraudster can continue booking trips while the victim attempts to reclaim their account and get the charges removed.
Preventing Account Takeover Fraud
Protecting data from cybercriminals has to be a joint effort by individuals, enterprises and law enforcement. The cost of ATO fraud grows exponentially if left unchecked. For enterprises that fail to stop compromised accounts, the losses extend beyond the direct costs connected to each individual account. Customers often hold companies responsible for the success of fraudsters and high-profile ATOs make the news. The effects of ATO fraud continue for years, from lost customer revenue to damage to brand reputations.
Watch this short video to learn more about the challenges associated with account takeover fraud and ways to mitigate the danger.
Data Protection
As an individual, there are a few things you can do to reduce the risk of ATO fraud. Stay current on threats and guard your credentials from phishing attacks, phone scams and other cyberattacks. Use unique, complex passwords every time and don't share them with anyone. Make sure your WiFi and IoT devices are secure, and avoid using public WiFi to access your business and personal accounts.
Security Protocols
Businesses need to be proactive in their efforts to reduce account takeovers, while making sure they don't frustrate or overburden legitimate users with endless verification steps. A holistic approach of combining identity and access management (IAM) solutions with fraud detection tools can stop bad actors before they are able to access user accounts.
Two-factor authentication (2FA) and multi-factor authentication (MFA) provide enterprises with an added layer of security to prevent cybercriminals from using compromised credentials to access accounts, and individuals should add these options to their accounts when available. MFA and 2FA require users to provide additional forms of authentication to prove their identity, which fraudsters do not possess, so access to accounts is denied.
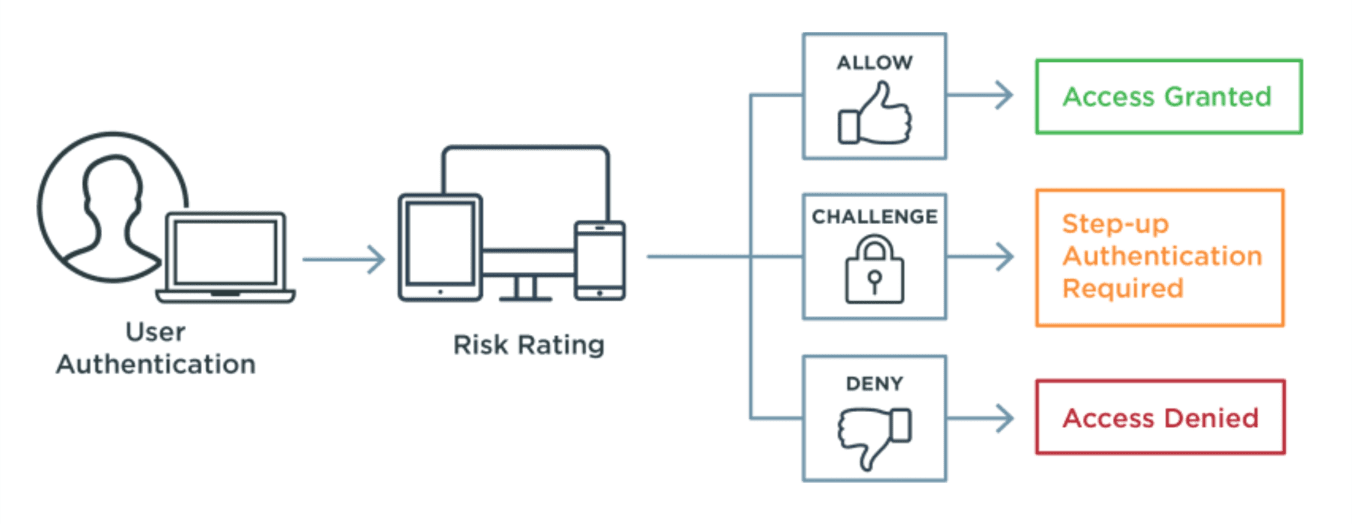
Identity verification, also called identity proofing, is another security tool that is used to ensure a user's digital identity is tied to their real-life identity. Businesses can choose to deploy an identity verification step for high-risk or high-value transactions to further reduce the chance of fraud.
For enterprises, the threat of fraudsters taking over legitimate user accounts is amplified by the fact that insiders and verified users can also be bad actors. An identity and access management (IAM) system integrated with fraud detection tools can help enterprises automate real-time fraud mitigation during a session to prevent bad actors from carrying out their fraudulent activities.
Fraud Detection Tools
Modern online fraud detection tools use artificial intelligence (AI) to examine hundreds of unique user data points generated by human-to-device interactions, device attributes and account activities to distinguish between legitimate users and fraudsters. Behavioral and context-based analysis identify automated (bot) and fraudster behavior because they don't follow the same pattern as legitimate user activity. Fraud detection tools can be activated when a session begins, which allows them to recognize unnatural activity during the session and stop fraud before transactions are made.
To learn more about online fraud, please read Everything You Need to Know about Online Fraud.
