What Is Multi-factor Authentication (MFA)?
Multi-factor authentication (MFA) is used to ensure that digital users are who they say they are by requiring that they provide at least two pieces of evidence to prove their identity. Each piece of evidence must come from a different category: something they know, something they have or something they are.
If one of the factors has been compromised by a hacker or unauthorized user, the chances of another factor also being compromised are low, so requiring multiple authentication factors provides a higher level of assurance about the user’s identity.
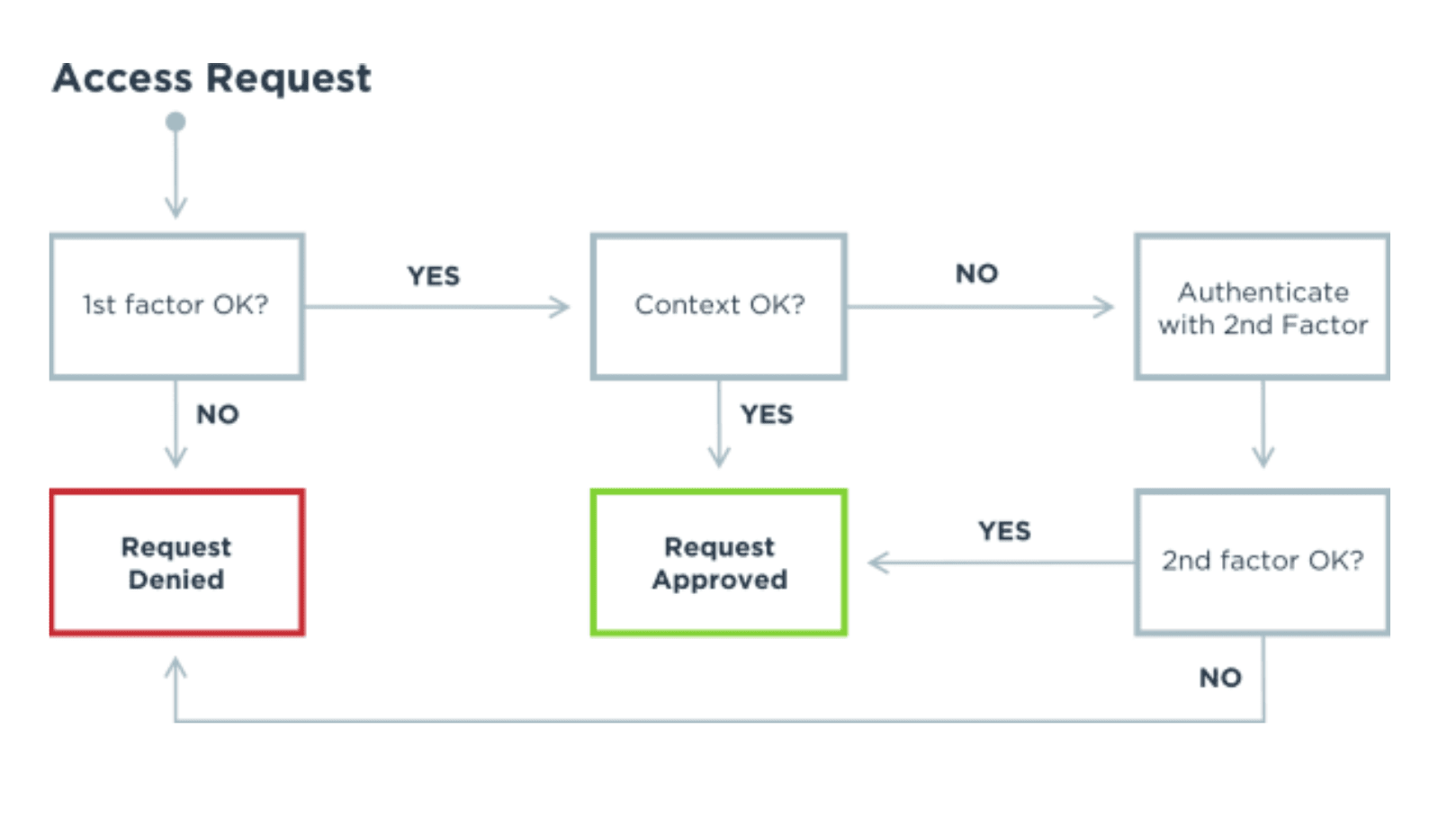
What are the benefits of multi-factor authentication?
Passwords may reign supreme as the most common way to authenticate your online identity, but they increasingly provide very little protection. Once a password is stolen, hackers can use those credentials to log in to applications and business systems, bypass other access controls and wreak serious havoc. In fact, according to the 2020 Verizon Data Breach Investigations Report, stolen login credentials are the top tactic used by hackers to achieve data breaches.
And there are an alarming variety of attack vectors hackers can take advantage of to steal passwords or gain access, including phishing attacks, brute force attacks, web app attacks, point of sale intrusions and even stolen hardware.

Unfortunately, users often make it easier for hackers by choosing weak passwords, using the same password for multiple applications, storing passwords in insecure locations and keeping the same password for long periods of time. These practices may help them remember their logins, but they invite hackers in through the front door.
Multi-factor authentication provides a layer of protection for both employees and customers that addresses all of these weaknesses. It mitigates the ripple effect of compromised credentials—a bad actor may steal your username and password, but if they’re prompted for another factor before they can access critical data, make a transaction or log into your laptop, they’ll be sunk.
A recent Ping Identity survey revealed that IT and security professionals consider multi-factor authentication to be the most effective security control they have in place for protecting both on-premises and public cloud data. Not only that, but many MFA solutions on the market are fast and easy to implement, meaning an organization can put this highly effective security measure in place without expending a great deal of time or effort.
Multi-factor authentication is also an excellent way to enable enterprise mobility, an initiative that’s always high on the priority list for companies undergoing a digital transformation. Productivity increases when employees can use their preferred devices to easily and securely access all of the resources they need without being tied to the office. By using MFA to log into business applications or to the network remotely via VPN, they get the flexibility and on-demand access that they value, and organizations can make sure their network and data are protected.
MFA can also be a key requirement when it comes to complying with certain industry or geographical regulations. For example, PCI-DSS requires that MFA be implemented in certain situations to prevent unauthorized users from accessing systems that process payment transactions, and MFA can help healthcare providers comply with HIPAA. It’s also a key part of meeting strong customer authentication requirements dictated by PSD2, a regulation pertaining to financial institutions in the EU.
How does multi-factor authentication work?
A user's credentials must come from at least two of three different categories, or factors. Two-factor authentication, or 2FA, is a subset of MFA where only two credentials are required, but MFA can use any number of factors.

What you know (knowledge)
The most common example of this factor is, of course, the password, but it could also take the form of a PIN, or even a passphrase--something only you would know.
Some organizations may also set up knowledge-based authentication like security questions (e.g., "What is your mother's maiden name?"), but basic personal information can often be discovered or stolen through research, phishing and social engineering, making it less than ideal as an authentication method on its own.
What you have (possession)
It's much less likely that a hacker has stolen your password and stolen something physical from you, so this factor confirms that you are in possession of a specific item. This category includes mobile phones, physical tokens, key fobs and smartcards.
There are a few ways that this authentication works, depending on the item, but some common methods include confirming via a mobile app or pop-up notifications from your mobile phone, typing in a unique code generated by a physical token, or inserting a card (e.g., at an ATM).
What you are (inheritance)
This factor is commonly verified by a fingerprint scan on a mobile phone, but also includes anything that would be a unique identifier of your physical person--a retinal scan, voice or facial recognition, and any other kind of biometrics.
There are a lot of possibilities spread across these three categories, and different authentication mechanisms may be better for different companies depending on their unique needs and use cases. By evaluating the relative strength, costs and benefits to both IT and users, an organization can find the combination that works best for them and their users.
Examples of modern multi-factor authentication
Some organizations may want to set up multi-factor authentication for all users, employees and customers alike. It's especially effective when combined with a single sign-on (SSO) solution, which removes many passwords from the equation, strengthening security even further and improving the user experience.
That said, some organizations may not feel the need to require MFA in all cases. To optimize employee and customer convenience, they might choose to bypass MFA in low-risk scenarios, while requiring stronger security in high-risk situations, for particularly sensitive data or for high-value transactions. For example:
- A bank may allow a customer to log into his online account with just a username and password, but require a second authentication factor before transactions can be approved.
- An organization may want a higher level of assurance that an employee is who she claims to be when accessing an HR application from a coffee shop or other off-domain location.
- A retailer may set up MFA to kick in when a vendor logs into their portal from a new device, to make sure it's not a hacker trying to get in with a stolen password.
This kind of multi-factor authentication is called contextual, adaptive or risk-based MFA. The beauty of using contextual MFA is that it can strengthen security only when warranted, and these requirements or use cases can easily change and evolve over time.
Watch the video to see how a modern MFA solution with support for multiple authentication methods and contextual policies can increase protection for your enterprise, but also provide a better experience for your employees, customers and partners.
What is cloud MFA?
Cloud-delivered multi-factor authentication (cloud MFA) provides enterprises with a secure and seamless experience for customers and users. Cloud MFA protects applications and data without the administrative and hardware costs associated with on-premise MFA. It also improves productivity and convenience while mitigating risks.
How does cloud MFA work?
As with on-prem MFA, cloud-based MFA uses two or more factors to authenticate a customer or user. Let’s use PingOne MFA as an example. Users can choose to authenticate by swiping, tapping or using fingerprint or facial recognition via a secure push notification from their mobile device or using FIDO2 bound biometrics on their laptop or security keys. Alternatively, they can use a one-time passcode sent to their email or SMS to verify their identity or use 3rd party TOTP authenticator apps (such as Google Authenticator).
What are the benefits of cloud MFA?
Easy to use: Cloud-based MFA integrates easily with a company’s resources.
Cost-effective: Unlike on-prem MFA, there is no need to purchase equipment or have staff monitor and maintain it.
Scalable: Cloud MFA easily adapts to an organization’s needs.
How does the cloud take multi-factor authentication to the next level?
Cloud multi-factor authentication removes the limitations of on-premise MFA. With ever evolving cybersecurity threats, having in-house employees stay current on risks and investing in the latest software and equipment can be a daunting task. Cloud MFA lets organizations turn over those challenges to experts so they can remain focused on their core business.
MFA in practice
It’s usually a simple process for employees to download an app or carry a token that can be used regularly for multi-factor authentication at work. When it comes to MFA for customers, it gets a bit tricky, since they have high expectations for streamlined experiences, and are quick to abandon clunky log-ins. Given the choice, customers have not been keen on enabling MFA protection for their accounts, even when it’s available for free from the service provider.
Organizations are encouraging customers’ use of MFA by explaining how it can not only enhance account security without significantly impacting their sign-on experience, but also make their other interactions (e.g., verifying their identity during a customer service call) more streamlined. And some organizations are even making MFA available through their own customer-facing mobile applications, rather than forcing customers to download a separate app or use less secure factors.
A good MFA strategy will carefully balance the risks of compromised credentials against the impact on employee productivity or customer experience when determining MFA requirements and risk-based policies.
The best modern MFA solutions can strike the balance between security and convenience by supporting multiple authentication options, implementing adaptive policies and integrating seamlessly into existing applications.
FIDO2, passwordless and the future of MFA
The FIDO Alliance is an industry consortium designed to make passwordless MFA available to all users and the online services they interact with. Given the magnitude of costs associated with a typical breach—not to mention the lost revenue and residual damage to your company’s reputation—it’s risky to rely on passwords and other knowledge factors such as KBA and one-time passcodes, which have proven vulnerable to attacks. The FIDO2 standard defines a common way for browsers and online services to implement MFA. It provides users with passwordless options such as security keys, biometrics and other mobile-device-based solutions, removing knowledge factors (what you know) to improve security for end users and online services.
Check out this video for a demonstration of how FIDO and MFA can thwart phishing attacks.
FAQs for MFA
What are multi-factor authentication examples?A common example of multi-factor authentication is using a password together with a code sent to your smartphone to authenticate yourself. Another example is using a combination of a card (something you have) and a PIN (something you know). You may also use a fingerprint or other biometric on your phone as a second factor. | ||
What is meant by multi-factor authentication?Multi-factor authentication is when a user must provide two or more pieces of evidence to verify their identity to gain access to an app or digital resource. Multi-factor authentication (MFA) is used to protect against hackers by ensuring that digital users are who they say they are. | ||
What kind of attack does multi-factor authentication prevent?Multi-factor authentication can help prevent some of the most common and successful types of cyberattacks, including automated credential stuffing, brute force and reverse brute force attacks and man-in-the-middle attacks. It also limits the impact of phishing, since a stolen or guessed password alone is insufficient for a hacker to gain access. | ||
What are the three types of authentication?The three types of authentication factors are:
| ||
Why use multi-factor authentication?Multi-factor authentication has a lot of advantages. Below are some of the reasons why you should be using MFA:
| ||
Why is multi-factor authentication better than a strong password changed regularly?Multi-factor authentication is better than a strong password changed regularly because even a strong password can be stolen through social engineering, and hackers have a wide variety of ways to steal credentials regardless of the strength of the password itself. With MFA, a hacker would still not have access to a user’s account due to the protection of the second factor. | ||
How effective is MFA?Multi-factor authentication is extremely effective in preventing any attack that involves a bad actor obtaining or guessing the user's credentials. In fact, MFA via on-device prompts blocks 99% of bulk phishing attacks and 90% of targeted attacks, according to Google. | ||
What are the benefits of multi-factor authentication?Multi-factor authentication has a lot of benefits. Some of them are:
|
