Qu’est-ce que la gestion des identités et des accès clients (CIAM) ?
La gestion des identités et des accès (IAM) est un cadre de sécurité qui aide les organisations à identifier un utilisateur du réseau et à contrôler ses responsabilités et ses droits d’accès, ainsi que les scénarios dans lesquels les privilèges sont émis ou refusés. L’IAM fait généralement référence à des fonctionnalités d’autorisation et d’authentification telles que :
Le single sign on (SSO) ou authentification unique afin que vos utilisateurs puissent se connecter une seule fois et avec un seul ensemble d’identifiants pour accéder à plusieurs services et ressources
L’authentification multifacteur (MFA) pour avoir un plus haut niveau de confiance dans l’identité d’un utilisateur en exigeant de ce dernier qu’il fournisse deux ou plusieurs facteurs à titre de preuve d’identité
La gestion des accès pour vous assurer que seules les bonnes personnes ont accès aux bonnes ressources
Ces capacités sont fondamentales pour assurer la sécurité dans un monde où les périmètres de réseau ne sont plus fiables ou pertinents. Mais toutes aussi importantes pour de nombreuses organisations sont les fonctions de sécurité des identités suivantes :
Annuaire
Vérification d’identité
Collecte des consentements et gestion de la confidentialité des données
Gestion du risque
Identité personnelle
Sécurisation des API
Libre-service pour les utilisateurs et les développeurs
Ces fonctionnalités avancées offrent une protection supplémentaire contre les menaces en constante évolution, vous aident à vous conformer à un éventail croissant de réglementations et offrent aux utilisateurs les expériences qu’ils attendent.
Quel est le but de l’IAM et pourquoi est-ce important ?
Vos utilisateurs ne sont plus limités aux employés protégés par un pare-feu. Alors que le travail à distance gagne en popularité, vous devez pouvoir donner aux divers utilisateurs un accès aux ressources depuis n’importe où et sur n’importe quel appareil pour garantir que la productivité n’en souffre pas.
Vos clients interagissent également avec vous via un nombre croissant de canaux numériques. Étant donné que le comportement des clients a changé, vous devez désormais fournir un accès à ces utilisateurs également, sinon vous risquez de perdre votre avantage concurrentiel.
Ces changements dans la façon dont le travail est effectué et les décisions d’achat sont prises ont poussé les approches de sécurité traditionnelles à leurs points de rupture. Mais les exigences de sécurité ne sont pas la seule chose qui a changé.
Vos utilisateurs, à la fois les employés et les clients, se sont habitués à la commodité. En conséquence, ils s’attendent à un accès rapide et facile aux ressources, services et biens, quand et où ils le souhaitent. Alors que votre personnel peut être plus enclin à se contenter de ce qui est fourni, vos clients, eux, peuvent et vont explorer les options mises à leur disposition.
Dans le monde numérique et sans frontières d’aujourd’hui, l’approche traditionnelle de la sécurité du périmètre n’est plus fiable ni pertinente. L’IAM déplace la frontière vers l’utilisateur et place l’identité au centre de la sécurité. Vous pouvez vous assurer que les utilisateurs sont bien ceux qu’ils prétendent être avant de leur donner accès à des ressources ou des données sensibles. Mais vous ne pouvez pas non plus rendre le processus trop lourd. Trouver le bon équilibre entre sécurité et expérience est essentiel, et l’IAM vous aide à le faire.
Customer Identity & Access Management (CIAM) : l’IAM conçue pour les cas d’utilisation des clients
Il est presque impossible, et peut-être même irresponsable, de parler d’IAM sans inclure au moins une brève discussion sur l'IAM client (CIAM). Alors que de nombreuses entreprises constatent que l’IAM répond aux exigences de fourniture d’un accès sécurisé au personnel, elle manque souvent des fonctionnalités nécessaires pour les cas d’utilisation des clients.
Avec la CIAM, vous obtenez des capacités qui vous permettent d’offrir des expériences client exceptionnelles, notamment :
Des profils unifiés pour que vous puissiez offrir des expériences multicanaux cohérentes et des interactions personnalisées à vos clients
Des fonctionnalités de sécurité puissantes qui s’étendent à la couche de données afin que vous puissiez protéger vos précieuses données client et réduire votre risque de violation
Des performances et évolutivité afin que vous puissiez offrir un accès instantané et sans friction pendant les heures de pointe et lorsque vous attirez de nouveaux clients
La confidentialité et la conformité réglementaire afin que vous puissiez donner aux clients la possibilité de contrôler comment et avec qui leurs données sont partagées et de se conformer aux réglementations telles que le Règlement général sur la protection des données (RGPD)
What is Cloud Identity and Access Management (Cloud IAM)?
Digital transformation prompted organizations to migrate infrastructure to the cloud in order to optimize IT operations and decrease costs. IAM solutions deployed in the cloud are available as a SaaS service, a managed service deployed in the vendor's private cloud, and as software deployed in the organization's own private or public cloud. Cloud IAM allows you to authenticate users no matter where they are and secure access to resources across SaaS, cloud, on-prem and APIs, all the while increasing your speed, agility and efficiency.
What are the Top Benefits of Cloud IAM?
Cloud IAM streamlines your move to the cloud, and different cloud deployment options offer different levels of customization and management responsibility. Top benefits include:
Comply with executive cloud-first mandates by moving identity infrastructure to the cloud.
Reduce infrastructure maintenance and support costs, especially when using a SaaS or managed cloud service.
Enable faster time to value when deploying identity capabilities.
Increase IAM flexibility and scalability.
Enjoy easier and more frequent upgrades, particularly when the service is managed by the vendor in the cloud.
Reduce reliance on expensive in-house identity experts if the identity vendor is managing the IAM service.
What is the Difference Between IAM and Cloud IAM?
In the past, on-prem IAM software was an effective way to maintain identity and access policies. The process of managing identities and access became more complex as organizations expanded beyond on-prem services to meet remote work demands and people started using mobile devices for work and play. Moving IAM solutions to the cloud is a logical step for enterprises with cloud-first mandates. While identity as a SaaS service (also called IDaaS) is common, there are other ways to achieve identity in the cloud, such as deploying cloud-enabled software in your own public or private cloud with the help of DevOps tools like Docker and Kubernetes.
Check out this video to see how you can move faster to embrace the benefits of identity in the cloud.
What’s the Difference Between Access Management and Identity Management?
When looking at IAM solutions, it’s often difficult to differentiate between identity management and access management, and in fact you might see both terms used to describe the overall IAM space. Arguably, they work hand in hand and both are needed to ensure you’re giving the right people access to the right things at the right time and for the right reasons.
But fundamentally, they aren’t one in the same. Identity management speaks to the process of authenticating users while access management is about authorizing users. Specifically, identity management combines digital attributes and entries in a database to create a unique identity for each user, which can be checked as a source of truth during authentication. Access management determines who can access a resource or database at any given time. The access management system manages the access portals through login pages and protocols while also guaranteeing that a specific user requesting access has proper clearance.
IAM as a whole gives you the ability to verify a user’s identity before they are provided access. In their simplest forms, identity management authenticates the user, then access management determines the person's level of authorization based on the user’s identity attributes.
What Are the Benefits of Identity Management?
Identity and access management helps you strike the ideal balance between security and experience. Additionally, it can help you save money and meet compliance requirements while enhancing your employee and customer experience. The main benefits of integrating IAM into your operations include:
IAM Enhances Security
Improved security is arguably the number one benefit that you stand to gain from IAM. Capabilities like multi-factor authentication reduce your reliance on passwords, which in turn reduces your risk of breach as a result of compromised credentials. As remote work becomes the norm and your IT team must manage an increasing number of apps and devices, you need new ways to protect against cyberattacks and data breaches. IAM helps you combat increasingly sophisticated threats with capabilities like API security and identity verification so you can feel confident that only the right people are accessing the right resources.
IAM Improves User Experience
By combining just-right security with seamless access, IAM helps you keep your workforce connected and your customers coming back for more. Single sign-on lets you give your users faster and easier access to the resources they need. When you combine SSO with adaptive authentication, you’re able to match authentication requirements to the access being requested. By stepping up security only when warranted, you minimize friction and deliver a better user experience. IAM advances like passwordless authentication further streamline access (without compromising security) by reducing or even eliminating the use of hard-to-keep-track-of passwords.
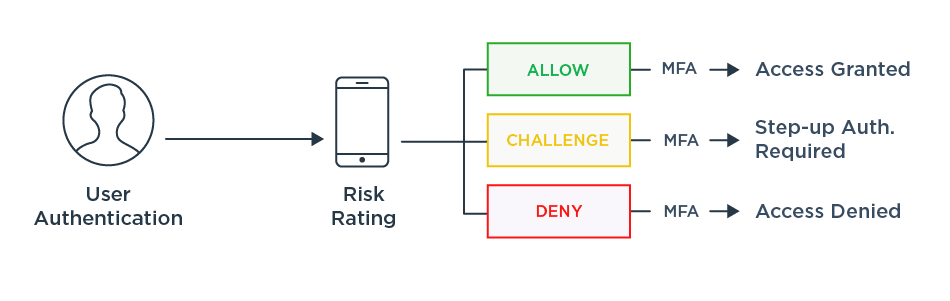
IAM Enables Workforce Productivity
Workforce users need to access a range of different applications to do their jobs. When access is impeded by forgotten passwords and restricted permissions, productivity suffers. IAM capabilities like SSO help work get done more efficiently by reducing the time it takes to log in and gain access to resources.
IAM Streamlines IT Workload
Speaking of forgotten passwords, it’s estimated that upwards of 50% of IT help desk calls are attributed to password resets and that a single password reset request costs companies an average of $70. IAM solutions minimize your reliance on passwords and the headaches that come with them. IAM also makes it easy to implement identity services and change privileges across your organization based on roles as well as more granular attributes.
IAM Supports Regulatory Compliance
By providing capabilities like API security, IAM eases compliance with Open Banking requirements. Similarly, privacy and consent management capabilities simplify compliance with data privacy regulations like GDPR and the California Consumer Protection Act (CCPA). With regulations on the rise across a range of industries, from financial to healthcare to retail, IAM gives you the agility to quickly adapt.
Types of Digital Authentication
There are many methods you can employ to prove your user’s identity. But not all digital authentication is created equally. Some types, like biometric, contextual and behavioral authentication, are not only more sophisticated and secure but also reduce user friction. Here’s a breakdown of some common digital authentication methods.
Pre-shared Key (PSK)
PSK is a digital authentication protocol where a password is shared among users accessing the same resources. Typical examples include a single network WiFi password shared by many workers in an office setting. While this practice is common and convenient, shared passwords are less secure than individual ones and expose you to threats like layer 2 and man-in-the-middle attacks. Digital certificates provide a more secure form of authentication than PSKs by tying identity to access so you know who or which device is using the network. They also eliminate the need for frequent password changes.
Unique Passwords
Unique passwords require a minimum number of characters and a complex combination of letters, symbols and numbers that makes them harder to compromise. But these requirements also make unique passwords a burden for your users to create and keep track of. In addition to creating a unique password for every application, users must come up with original passwords every 60-90 days. All of these factors lead to password fatigue and increase your security risks. In contrast, single sign-on lets your users access multiple resources with a single username and password combination.
Hardware Tokens
Hardware tokens are small physical devices like a smart card, key fob or USB drive. The device itself contains an algorithm (a clock or a counter) and a seed record used to calculate a pseudorandom number. Users enter this number to prove they have the token, or they might press a key on the device, which generates a one-time passcode (OTP) and sends it to the server. The physical nature of hardware tokens makes them expensive and burdensome to roll out and puts them at risk of breakage, loss and theft. An easier and less costly alternative is mobile authentication that relies on soft tokens to generate an OTP for sign on.
Biometric Authentication
While other forms of authentication rely on something your users know (passwords) or have (devices, tokens), biometric authentication uses characteristics of who your users are to prove identity. Examples of biometric authentication include fingerprints, facial recognition, voice recognition, hand geometry and retina or iris scans. These forms of authentication are more secure as they’re highly unique to the individual and harder to replicate, steal or compromise. They’re also growing in usage as mobile device, tablet and PC manufacturers have begun incorporating these technologies into devices. Additionally, the use of FIDO protocols provides stronger authentication by using standard public key cryptography. With FIDO, the biometric information never leaves the user’s device. This protects user privacy by making it impossible for online services to collaborate and track a user across services.
Contextual Authentication
A form of risk-based authentication, contextual authentication uses information such as geolocation, IP address, time of day and device identifiers to determine whether a user’s identity is authentic or not. Typically, a user’s current context is compared to previously recorded context in order to spot inconsistencies and identify potential fraud. While these checks are invisible to the authorized user, they create a significant barrier to an attacker.
Behavioral Biometrics
Another form of risk-based authentication, behavioral biometrics leverages machine learning to identify unique user behaviors like mouse characteristics and keystroke dynamics. By learning about how a user typically behaves and interacts, behavioral biometrics allow you to detect abnormal behavior that could indicate suspicious activity or a malicious attack. Because each person exhibits unique device behaviors, behavioral biometrics help you differentiate between the authorized user and a bad actor.
Multi-factor Authentication (MFA)
More secure than passwords and hardware tokens alone, multi-factor authentication requires users to provide at least two pieces of evidence to prove their identity. They must provide something they know, something they have or something they are, with only one form of evidence coming from each category. For example, an MFA authentication flow might require a user to sign on with a username and password (something they know). They might then need to complete authentication by confirming the request on a mobile app (something they have).
What Are the IAM Risks?
Any effective risk management strategy starts with identifying the potential risks you face. Information security analysts at KuppingerCole suggest evaluating your organization across these five areas to identify and mitigate potential risks, and set up your IAM initiatives for success.
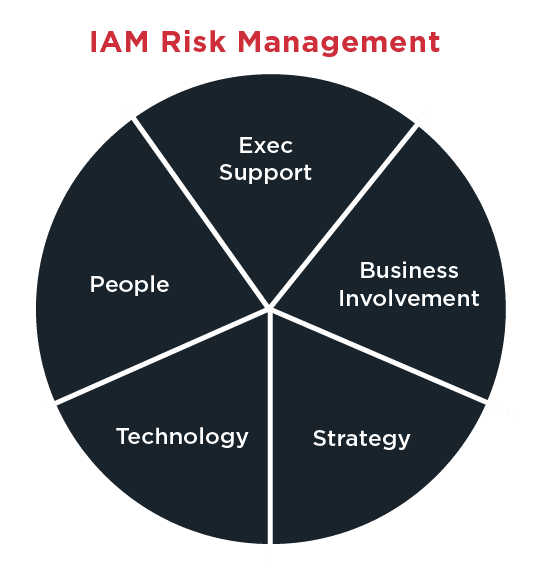
1. Executive Support
Risks: If IAM lacks executive buy-in, it’s difficult to gain the financial and resource support needed throughout the organization to make IAM successful.
Issue: The identification of responsibilities is often the most complex challenge. You need top-down support for organizational shifts and decisions.
Mitigation: Executive support is much easier to gain when the business value can be explained in clear, simple terms. Executive sponsors need to be well informed and ready to influence the direction of IAM initiatives, as well as understand the purpose and objectives of the individual projects within them.
2. Business Involvement
Risks: Without business involvement, IAM projects suffer from unclear scope, scope creep and being overtaken by technology requirements.
Issue: The business needs to drive the programme and lead the technology, not vice versa.
Mitigation: In addition to meeting regulatory specifications and audit requirements, there are other IAM benefits that need to be communicated including gaining an overall view of users, the ability to quickly connect new business partners and added agility for the business. It’s important that the business environment is understood and mapped out before the technology can be deployed in the proper context.
3. Strategy
Risks: IAM projects can be complex, making a “big bang” approach difficult to control. The multiplication of corporate identities requiring management has to be considered from the outset.
Issue: Even though the first implementations might only give a small set of functionality to a group of employees, they must be designed so they can scale.
Mitigation: IAM implementation should be broken down into individual and clearly scoped projects—not a single large one with unclear boundaries.
4. Technology
Risks: An IAM implementation can be stopped in its tracks by technology missteps like choosing the wrong product, trying to leverage existing failed products or letting the program be driven by vendors or other technology “experts.”
Issue: Technological expertise isn’t enough to make a successful IAM implementation. It requires a holistic understanding of the environment and a vested interest in the program’s success.
Mitigation: Ensure that system integrators, vendors and technical teams are leveraged and respected but that the implementation is ultimately guided and controlled by the business. Give technical teams a platform to express their concerns and take them on board, but do not allow them to constrain business requirements.
5. People
Risks: People are vital to IAM success. But individuals will have different understandings of how IAM functions based on their role and/or previous experience with technology. With conflicting views of what IAM should entail, projects can quickly become politicized, creating division and in-fighting between business and technical teams.
Issue: Departments need the ability to control access to their own systems. New user groups need to be easily onboarded.
Mitigation: Individuals and their respective needs and understandings must be considered from the beginning. Knowledge must be freely shared, progress communicated regularly and successes celebrated. Lastly and most importantly, IAM must be simple enough that it works for the end user.
What is the Future of IAM?
Trends in remote work, cybersecurity, data privacy and customer experience continue to shape IAM priorities. While the future is never entirely predictable, indicators point to six imminent shifts in identity security.
Greater Control Over Personal Data
Buoyed by consumer privacy regulations, customers are demanding more control over how their personal data is used and shared. To address this demand, new personal identity frameworks are evolving that give customers control over their identities and which attributes to share with service providers, as well as enable secure validation of identity without requiring excessive personal data.
Acceleration of Zero Trust
Zero Trust will become the foundation of enterprise security. As a security model that streamlines workflows and implements adaptive authentication, authorization and identity verification services, Zero Trust gives organizations a fundamentally stronger security posture to protect against evolving threats.
End of SSN as Secure Authenticator
More than $60 billion in fraudulent unemployment insurance claims plagued state-run unemployment agencies in the U.S. during and in the wake of the pandemic, highlighting the consequences of using social security numbers as a trusted authenticator. If we weren’t convinced before, this costly lesson underscores the imperative to eliminate the usage of SSN as a secure authentication factor.
More Secure Remote Work
Working from home at least part of the time is here to stay. But providing a seamless experience to remote workers presents challenges. IAM supports WFH by giving workers frictionless access through single sign-on and adaptive authentication. At the same time, you gain increased confidence that only the right people are accessing company resources and increased agility to further your cloud initiatives.
Rise of Passwordless Customer Authentication
In keeping with the trend toward working from home, consumers are also shopping from home more than ever. As the battle for customer experiences continues to wage, companies will transition customers to a passwordless experience to minimize friction without sacrificing security. Passwordless authentication lets customers authenticate with something other than risky passwords, like biometric push notifications on a trusted device.
More Pervasive AI and Machine Learning
As use of artificial intelligence becomes more widespread, it’s possible it could also become the new attack mechanism. To quickly identify suspicious activity and adapt access based on the level of risk, behavioral analytics and risk signals should be integrated into all access and lifecycle management flows. Not a cure-all, however, AI and machine learning are best used in combination with existing threat detection methods.
Get Help from IAM Experts
In today’s business environment, user experience is king, but security can’t be sacrificed. The right IAM solutions help you optimize both.
The PingOne Cloud Platform is a comprehensive, standards-based IAM platform designed for hybrid, multi-generational and multi-cloud environments. Providing comprehensive capabilities to support workforce and customer use cases, it empowers you to leverage unified digital identities and give all users and devices secure access to cloud, mobile, SaaS and on-premises applications and APIs.
Explore Ping’s IAM platform and learn how you can take identity to the cloud for your workforce and customers.
