Single Sign-on vs. Federated Identity Management: The Complete Guide
What is Single Sign-on (SSO)?
Single sign-on, or SSO, allows a user to access multiple applications using a single set of credentials. This capability can be applied to both employees and customers to streamline their login experiences. Typically, employees sign on to multiple business applications to do their jobs, such as messaging and email accounts, HR functions, intranet sites, financial records, etc. With SSO, they can access all of the resources they need with one set of login credentials, eliminating the need to remember or enter a unique password for each account.
Similarly, customers often access multiple services or applications through one business account or portal. Banking is a good example. As shown in the diagram below, SSO makes it possible for bank customers to sign on with a single set of credentials and be able to perform a variety of actions like checking their account balance and transferring money. Even if these services are actually separate applications managed by the bank behind the scenes, SSO provides your customers with a seamless experience.
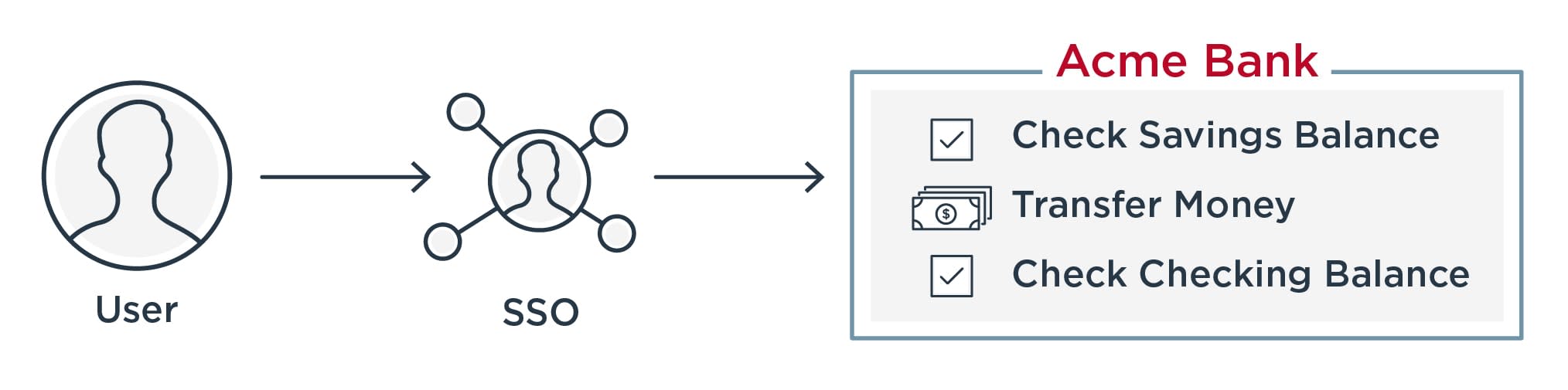
Benefits of Single Sign-on
STRONGER SECURITY
SSO strengthens enterprise security by reducing the number of passwords your users have to manage. Since passwords are a popular attack vector, reducing reliance on them also reduces the potential for a breach. Asking your users to only remember one password also decreases their tendency for risky password behavior, such as reusing passwords, writing them down or sharing them with others.
BETTER CUSTOMER EXPERIENCE
Single sign-on eliminates the frustration of having to juggle multiple passwords and sign on multiple times. Customers can sign in once and easily access all of the products and services they need. With nearly 3 in 4 customers reporting that experience is an important factor in purchasing decisions, single sign-on is a great place to start impressing them.
IMPROVED EMPLOYEE PRODUCTIVITY
Single sign-on gives your employees easier access to the resources they need to do their jobs. By making access faster without sacrificing security, you’re streamlining their experience, giving them more time to focus on important tasks.
LOWER IT COSTS
Decreasing the number of passwords also decreases the number of help desk tickets due to password-related problems. Fewer password resets may not sound like a big deal, but some organizations budget over $1 million annually for password-related support costs alone. By minimizing the number of passwords in use, you can save a lot of money.
What is Federated Identity Management (FIM)?
Federated identity management, also known as federated SSO, refers to the establishment of a trusted relationship between separate organizations and third parties, such as application vendors or partners, allowing them to share identities and authenticate users across domains. When two domains are federated, a user can authenticate to one domain and then access resources in the other domain without having to perform a separate login process.
FIM is achieved through the use of standard protocols like SAML, OAuth, OpenID Connect and SCIM. These open standards enable the secure transmission of authentication and access information across domains. As a result, a user can sign on once and gain access to applications and systems across all federated domains. Essentially, federated identity management enables single sign-on across company lines.
SSO vs. FIM
Although you may hear SSO and FIM frequently used together, they are not synonymous. Single sign-on enables access to applications and resources within a single domain. Federated identity management enables single-sign on to applications across multiple domains or organizations.
For example, FIM is necessary for an organization to give employees one-click access to third-party applications like Salesforce, Workday or Zoom. Using our banking example from before, FIM allows bank customers to seamlessly access bank services that are externally managed, like ordering checks, sending money via Zelle, and applying for a loan.
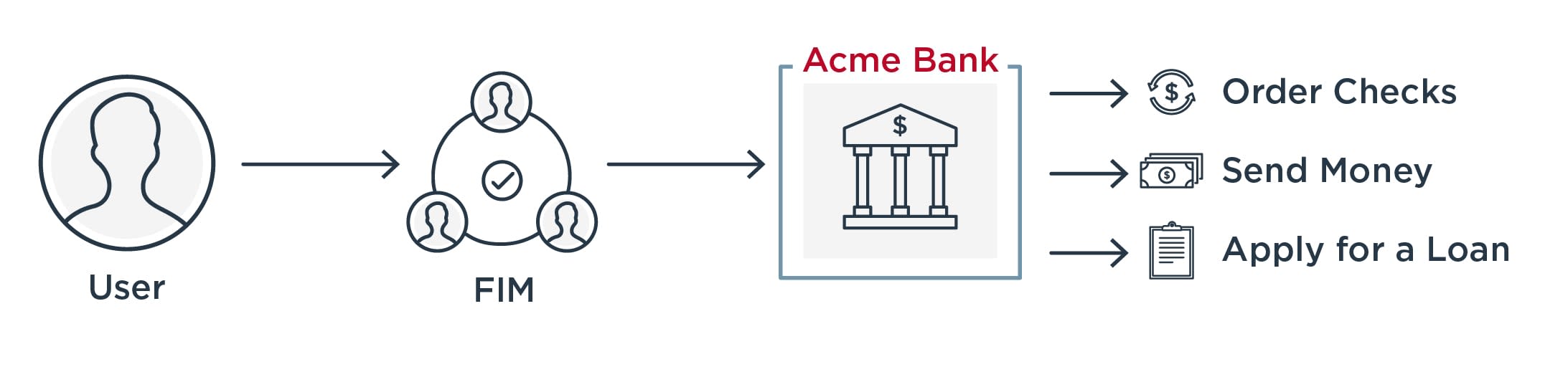
How Does Federated Identity Management Work?
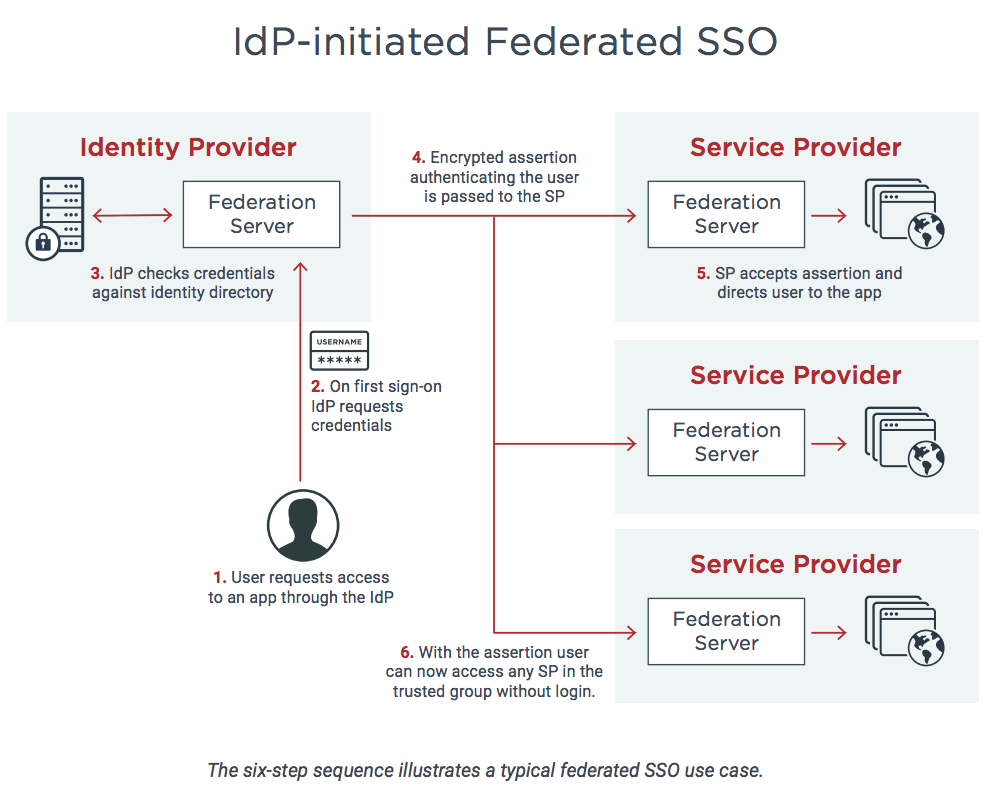
There are several workflows federated identity might use, but a common set up is for one organization to serve as the identity provider (IdP), where a user’s identity is stored. The IdP establishes a trusted relationship with service providers (SPs), which are outside the security domain of the original organization.
For example, an employee’s organization might be the IdP, and the third-party apps they use to do business are SPs. The diagram below illustrates the six-step sequence for this use case.
- The employee requests access to an app through their organization, which is the IdP.
- The IdP requests the employee’s credentials.
- The IdP authenticates the employee’s identity using stored data that was created when the user set up their account or joined the organization.
- When the authenticated employee tries to access one of the third-party apps, the SP sends a request to the IdP.
- The IdP indicates, usually through a SAML assertion or other protocol, that the user has been authenticated and has permission to access that service.
- The employee proceeds without needing to sign on again.
Benefits of Federated Identity Management
Your ability to give your employees and customers easy access to all of the resources they need, even if those apps and services sit outside your firewall and are managed by third parties, is foundational to digital transformation.
Federated identity management helps you:
- Strengthen security against growing threats and costly data breaches
- Increase workforce productivity by enabling your employees to work from anywhere and any device
- Enhance customer experience to drive loyalty and revenue
- Lower costs and increase the efficiency of your IT resources
To learn more about federated identity management, read the SAML 101 white paper.
