Role-based Access Control (RBAC) vs. Attribute-based Access Control (ABAC): What's the Difference?
Controlling access to data and networks is a high priority for any organization. Enterprises use access control, also known as authorization, to grant access to resources using predetermined or customized permissions based on the user's role, identity attributes or risk factors.
Protecting access to customer data is also critical, and it's driven by three main factors: data privacy regulations, enterprise security needs and customer experience expectations. Ensuring a good customer experience as well as security and regulatory compliance can be difficult given the number of apps and APIs involved, along with the number of people and processes required to make necessary changes and updates.
Let's look at two access control options:
- Role-based access control (RBAC) enables access to resources or information based on user roles. These roles might be defined by job titles, departments, locations and/or specific duties and responsibilities.
- Attribute-based access control (ABAC) is a more flexible approach to authorization decisions, using additional information (attributes) to inform policy decisions. Moving beyond roles allows the use of granular attributes, including contextual attributes, in order to authorize an individual's access.
Read on to learn more about RBAC and ABAC, including differences, pros and cons.
What is Access Control?
Once a user is authenticated, authorization is used to control what data, apps and resources a verified user has permission to access. This keeps unauthorized users from accessing sensitive information, including on-premises and cloud-based apps.
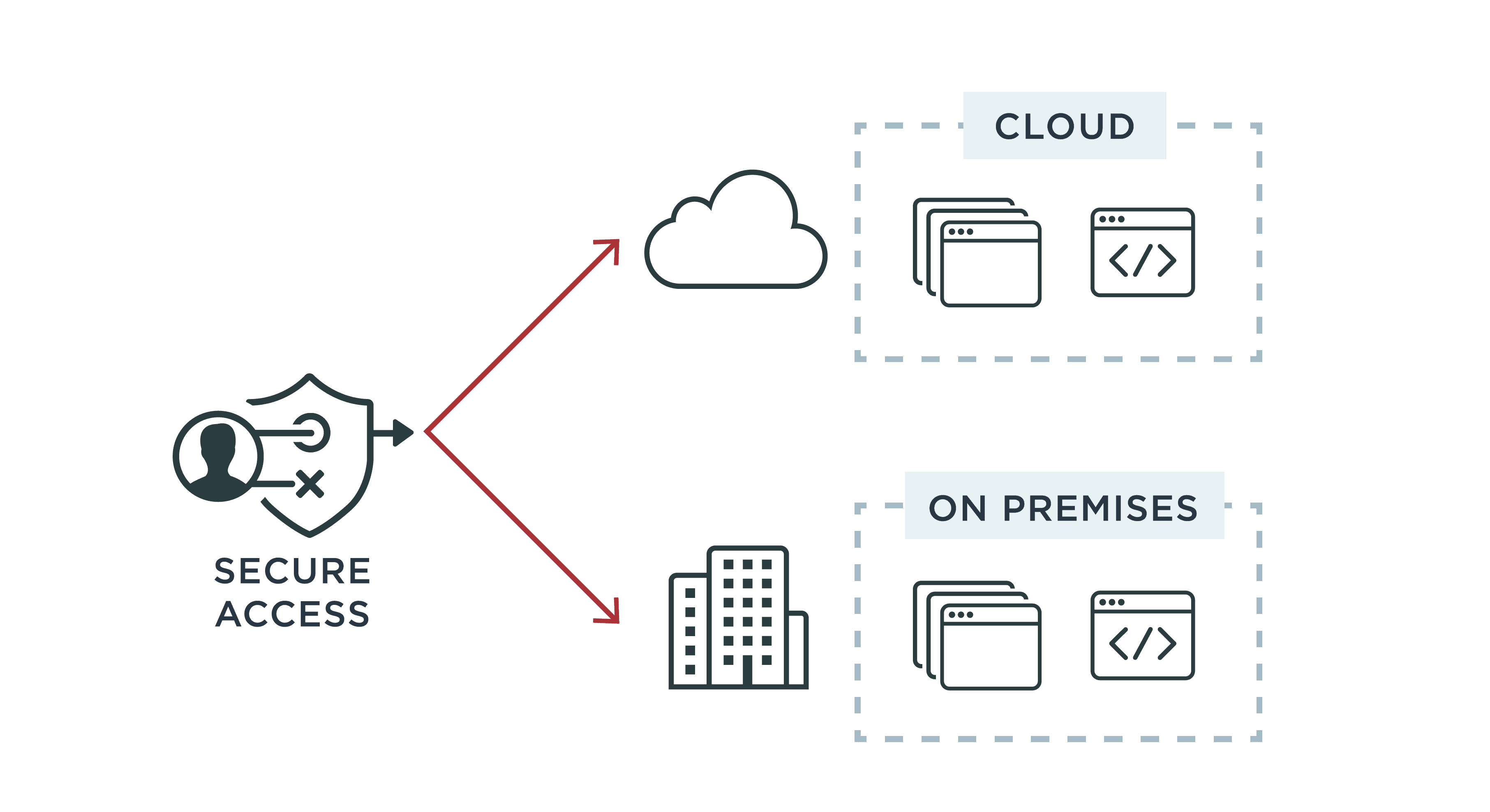
Enterprises that follow the principle of least privilege (PoLP) ensure access is limited to only the resources a user actually needs. For example, you don't want an intern to have the same access and privileges as a system administrator. Other examples include:
- HR teams are able to access apps that store sensitive employee information, but finance and marketing teams cannot.
- Two customers can be logged into the same retail website, but only one, a member of the VIP rewards program, is able to access VIP rewards resources.
Access control solutions can also be used to approve or deny access to stored data based on consumer consent directives, which helps adhere to data privacy regulations like the General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA).
What is Role-based Access Control (RBAC)?
Role-based access control (RBAC) grants permissions based on the user's roles. Roles can be defined by criteria such as authority level, responsibility, job title or status (employee vs. contractor) as well as task-based needs (viewing vs. editing rights). For example, when a new salesperson is hired, they can quickly be granted access to the same predefined resources as other members of the sales team because they share the same role.
Benefits of Role-based Access Control (RBAC)
- Streamlined approach. Predefined roles make this a plug-and-play option, limiting the amount of work required by the IT department to onboard new employees. The RBAC approach also limits the chance of data entry errors being made when large numbers of employees are hired at the same time.
- Temporary access is easy to facilitate. Users that need temporary access to resources, such as seasonal workers, can be given limited access to just the resources required for their assignment.
- Quickly handle job changes and terminations. When an employee changes jobs or leaves the company, that user's access to resources can either be changed to a new role or revoked when the user leaves the company.
- Regulatory compliance. Regulations regarding data privacy require enterprises to limit access to resources. By automating access based on roles, errors allowing the wrong people access to sensitive data, including consumer data covered by regulations, are less likely to occur.
What is Attribute-based Access Control (ABAC)?
Attribute-based access control (ABAC) offers improved security and flexibility by evaluating more than just roles for authorization decisions. Attributes can include user attributes (e.g., security clearance, age), resource attributes (e.g., creation date, type of resource) and context (e.g., access location, time of day). For example, a salesperson may be blocked from logging in to sales resources from high-risk locations, like coffee shops or airports, or be required to go through additional safeguards before access is granted.
Dynamic Authorization
Dynamic authorization enhances ABAC by enabling real-time enforcement of fine-grained business logic. This allows you to control access by requiring that certain conditions are met. Dynamic authorization also centralizes access controls rather than incorporating them at the individual application level, governing access to entire resources or individual attributes.
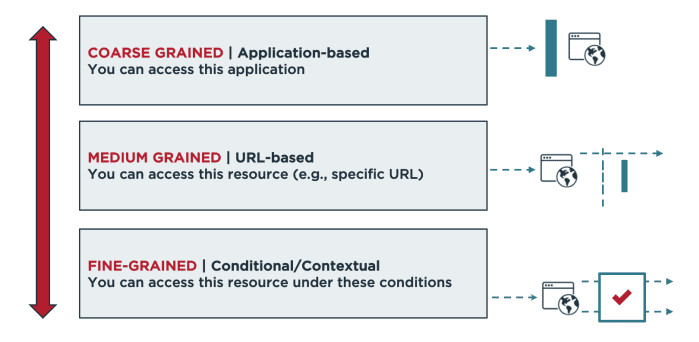
Benefits of Attribute-based Access Control (ABAC) with Dynamic Authorization
- Increase security and flexibility. Key attributes can be evaluated in real-time at the moment of a transaction to determine the validity of the access request. Adding context improves decision-making.
- Deliver better customer experiences. Give customers greater control over and insight into their data, and allow them to easily manage consent so you can protect their data from being accessed through unapproved data stores and APIs.
- Regulatory compliance. Data privacy regulations require enterprises to limit access to customer data. Security teams can move faster by controlling the access that all digital application teams and channels have to customer data.
- Increase agility. Enterprises can evaluate data, react more quickly to market changes and launch new applications and APIs without sacrificing regulatory compliance or security.
What are the differences between Role-based Access Control (RBAC) and Attribute-based Access Control (ABAC)?
Role-based access control (RBAC) made sense when access was limited to users inside a network perimeter, but is too limiting for many of today's use cases. It can be a good option for simple, static logic, such as ensuring only employees in a single role can access the tools they need to do their jobs. RBAC is not effective at providing fine-grained data access governance and authorization needed to secure customer data. While roles and group memberships may be well defined, RBAC relies on the applications themselves to make decisions about user access and permissions.
The National Institute of Standards and Technology (NIST) recommends attribute-based access control (ABAC) over role-based access control (RBAC) for organizations with multiple business cases. ABAC provides centralized control and the flexibility to handle permissions for different users, environments and conditions.
“Most businesses today use Role-Based Access Control (RBAC) to assign access to the network and systems based on job title or defined role. But if an employee changes roles or leaves the company, an administrator must manually change access rights accordingly—perhaps within several systems. As organizations expand and contract, partner with external entities, and modernize systems, this method of managing user access becomes increasingly difficult and inefficient.”
—National Institute of Standards and Technology (NIST) / National Cybersecurity Center of Excellence (NCCoE)
To learn more about the differences between RBAC and ABAC, and which option is best for your organization, download our whitepaper Attribute-based Access Control and Dynamic Authorization.
