What is Dynamic Authorization?
Your customers are increasingly choosing online over in-person to make purchases and conduct transactions. And they want the ability to use any device at any time and from anywhere to do so. This new digital freedom is providing unprecedented flexibility and options for customers. But it’s creating more complexity and competitive pressure than ever for the enterprises and organizations that serve them.
Online shopping is one of the most popular digital activities worldwide with global e-retail sales reaching $3.5 trillion in 2019, or 14.1% of total global sales. E-commerce is expected to grow an additional 8% and account for 22% of all global sales by 2023.
— ”E-commerce share of total retail sales worldwide 2015-2023,” Statista, Nov 26, 2020
Should you not deliver the efficient customer experience expected, your customers can and will seek out more convenient options. Depending on your industry, you must also ensure compliance with regulations like GDPR, CCPA, HIPAA and the Cures Act. And as the amount of digital data being gathered, stored and shared grows, you’re also exposed to greater risk of data breach and the reputational damage that comes along with it.
To succeed in today’s business climate, you need the ability to manage data and service access so that you can maintain strict control over what’s accessed and by whom. At the same time, you must balance security and regulatory realites with your customers’ expectations for secure and seamless experiences.
Why Role-based Access Control Doesn’t Work in Today’s Digital World
Traditional authorization approaches rely primarily on identity or logical extensions of identity. Known as role-based access control (RBAC), this approach relies on the role of the individual to which the identity is associated to make access decisions, and it delegates authorization decisions to the application being accessed. For example, members of the HR team can get access to the payroll application, and members of the finance team can access financial reporting tools.
This made sense when access was typically limited to internal users inside a network perimeter. But the RBAC approach, while fine for certain applications, is too limiting when it comes to many of today’s use cases. Given the number of applications and people requesting access to them, making authorization decisions is rarely that binary anymore, and the use of additional attributes can ensure better and safer decisions.
While you could theoretically delegate this responsibility to the individual applications, doing so can create inconsistencies and a lack of visibility and control. Relying on the individual application also makes implementing changes a tedious and time-consuming process, and sets you up for audit headaches and potential compliance violations.
How Attribute-based Access Control and Dynamic Authorization Helps
Dynamic (aka external) authorization management solves for the disadvantages and risks of RBAC by utilizing additional attributes for authorization decisions. Attribute-based access control (ABAC) is a better and safer alternative according to the National Institute of Standard and Technology (NIST). It provides greater flexibility and security by allowing the evaluation of additional information (attributes) to make authorization decisions.
Recognizing that attributes alone may not be sufficient, dynamic authorization takes ABAC a step further by enabling the use of fine-grained access control and externalizing authorization outside of applications. The addition of fine-grained attributes allows you to evaluate the context of each request. Unlike traditional authorization, which typically has static rules for access, fine-grained authorization lets you control access beyond the application level and resource level to require that certain conditions are met.
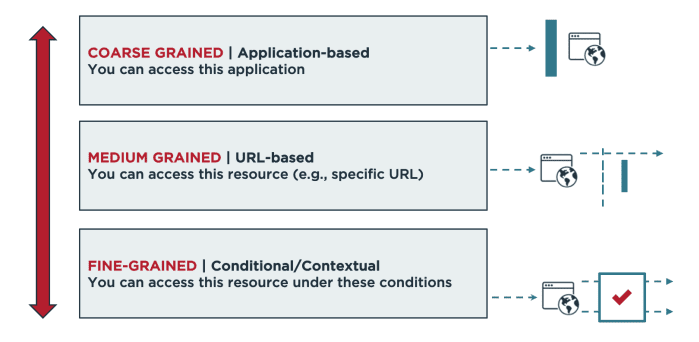
Another key principle of dynamic authorization is the abstraction of business logic from the applications that consume it. Because of the disadvantages of hard-coded, static logic that resides inside applications and is distributed and duplicated across our enterprise, dynamic authorization centralizes access controls instead of incorporating them at the individual application level.
How Dynamic Authorization Works
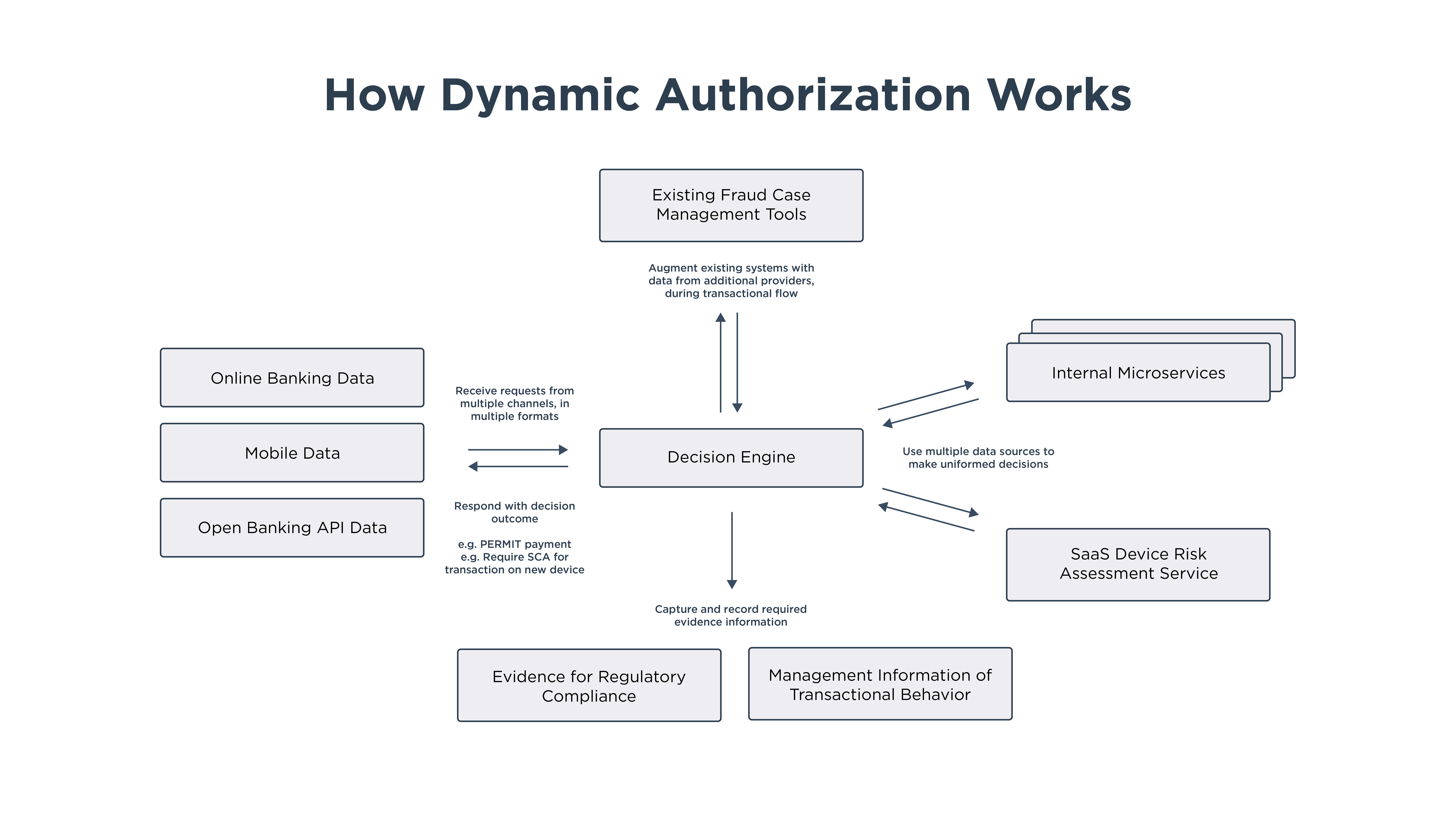
During dynamic authorization, the application provides data to the central authorization system that identifies the nature of the request, for example a user ID and a target service or target data. From there, the authorization system takes responsibility for collecting all additional data required to make the right authorization decision. This could include:
Retrieving additional context, such as organizational roles and user attributes, from a directory service
Interrogating a cloud-based device risk service
Checking customer financial account balances
Evaluating fraud and risk systems to get an update on the organization's current risk status
All of this is done dynamically in real-time as the request is being made or transaction is occurring. Having gathered all of the necessary attributes, the central authorization system assesses these attributes in real time to make the right decision as defined by the organization’s access policies. Access is then granted, denied or if more information is needed, control can be passed back to the requesting application. The whole process happens with zero or minimal friction for the customer.
Centralized Control of Authorization Policies
Dynamic authorization centralizes authorization policies so the applications themselves do not need to maintain their own access policies. Serving as a central authorization system, the dynamic authorization service stores the rules and effectively acts as a “decision-as-a-service” resource.
Because the body of authorization rules is managed centrally, the organization also becomes more agile and responsive to evolving priorities. Changes to a policy can be made in a single place and automatically applied to the various applications which use that policy.
Dynamic authorization makes your authorization policies:
Centrally controlled and visible
Easily changed
Auditable for compliance
Replicable across applications
Dynamic Authorization Removes the Burden from IT
Dynamic authorization also lets you delegate policy control to the appropriate line of business. In this way, dynamic authorization eases the burden on IT teams to perform this role.
Instead of allocating IT resources to this task, you can give business users a policy management interface that makes it easy for them to safely build and test policies themselves and according to their specific needs.
Dynamic authorization helps your organization:
Be more agile
Save time and money
Remove reliance on software release cycles
Learn More about Dynamic Authorization
By centralizing authorization policies and decision-making while externalizing policy application to business users, dynamic authorization creates efficiencies like cost savings and reduced time to market.
In a world where the only constant is change, dynamic authorization helps you:
Improve security by protecting data accessed through data stores and APIs
Ensure compliance by streamlining management of data privacy and consent
Increase agility by enabling new digital business initiatives
To learn more about how dynamic authorization can help your enterprise, get the white paper.
