PingOne API Intelligence: Leveraging Artificial Intelligence to Protect Your Valuable APIs
The Need for API Security and Governance
APIs are the pillars of digital transformation initiatives. They offer many great benefits and because of this, organizations are now deploying APIs across multiple clouds and data centers, leveraging a variety of API gateway environments.
Unfortunately, this leads to blind spots and the inability to properly track who is doing what with your APIs. And, while APIs provide accessibility and the platform for innovation, they significantly increase the risk of mishaps and data breaches, challenging all organizations to layer an effective API security and governance protection over those APIs.
PingOne API Intelligence enables you to proactively address some of the most challenging API infrastructure risks. You will be able to:
Respond to production API security issues and vulnerabilities before they become costly, are reported by the press or exploited by hackers.
- The press recently reported on several public companies with API security flaws that exposed their customers' private information. See TechCrunch reports on Peloton and Echelon API issues: Peloton and Echelon. Similarly, see the issue with John Deere's API: John Deere Motherboard article and John Deere Leaky API.
- API design flaws are the entry doors hackers are looking to breach.
Protect your brand from partners misusing or abusing your APIs
- A very embarrassing case of a partner misusing an API recently exposed financial and private data of millions of Americans. See this KrebsOnSecurity article Experian API Exposed Credit Scores.
Protect against financial losses and reputational damages from API breaches and fraud
- Hackers are launching new types of attacks that use valid credentials to exploit APIs in order to take over accounts, steal data and commit fraud.
- Because they are authenticated users and are "freestyling" their attacks, existing security solutions are inadequate at detecting API hackers.
Demonstrate adherence to internal policies and industry regulations
- CIOs and CISOs are increasingly uncomfortable with the proliferation of APIs and the lack of oversight over user activity. This is driving the need for detailed API traffic info for governance, audit and forensic reports–linked to the identity of each user.
- APIs are deployed everywhere, creating blind spots and the fear of not knowing about all active APIs. Tracking APIs across all clouds and data centers is critical to the security of the organization.
PingOne API Intelligence AI-powered Visibility and Security
API security risks can be mitigated through the implementation of a Zero Trust model that includes robust identity and next generation API security controls. This would mean authenticating and authorizing all requests, monitoring all API activity and continuously assessing each session's risk to apply proper remediation when necessary.
PingOne API Intelligence enables you to do just that. It's a cloud-based AI service that monitors API activity and identifies abnormal situations across all your API gateway clusters, clouds and data centers. It can detect partners that are misusing or abusing APIs, catch production API bugs and vulnerabilities and automatically block cyberattacks on APIs.
PingOne API Intelligence adds an AI security layer to your API gateways to boost the security and governance of your API infrastructure. It effectively complements the security of API gateways by recognizing abnormal activity and bad user behaviors on API resources—with no rules or policies to manage.
With PingOne API Intelligence, API traffic is linked to the identity of each user so you can track what each user is doing across all your API clusters and clouds. Existing and new APIs are discovered automatically to eliminate visibility blind spots, such as shadow and forgotten APIs. Session activity is continuously monitored and analyzed for each user. Any abnormal situation is reported and can be blocked and deep activity insights are delivered for auditing, forensic and governance reports.
PingOne API Intelligence at a glance:
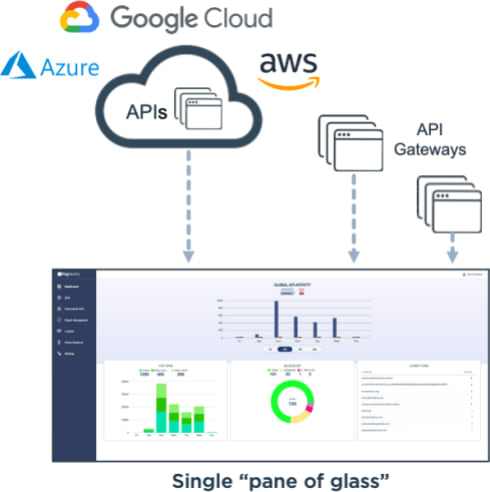
- Single "pane-of-glass" to monitor the entire API infrastructure and provide global visibility into user activity on all APIs across all API gateways, data centers and clouds.
- Dynamic API discovery to eliminate visibility blind spots. This detects new APIs, shadow APIs, old API versions still active and surfaces forgotten APIs so that you can add security before hackers go after them.
- AI/ML-based detection of anomalous API behaviors to identify API design flaws, bugs and vulnerabilities in production, as well as partners and third party developers that are misusing or abusing your APIs.
- AI/ML-based detection and blocking of API cyberattacks to prevent account takeover, fraud and data breaches, flagging today's constantly evolving attacks on APIs that are not detected by traditional security.
- API deception with honeypot to instantly detect and block probing hackers.
- Self-learning with no rules or policies to configure, write or maintain.
Comprehensive Visibility Across all API Environments and Clouds
The demand for data and seamless application control has never been higher and organizations are now leveraging APIs and API gateways to provide internal teams and third party developers with the interface layer needed for fast tracking mobile and other application integrations.
These APIs are finding their way into public and private cloud environments distributed across datacenters. As a result, most DevOps and security teams are uncertain that they know about all exposed APIs, both internal and external.
Teams need to eliminate blind spots and identify all APIs, including shadow APIs and old versions accidently left active during an application migration. Hackers look for forgotten APIs and exploit them to breach organizations. Such mishaps have occurred among social networks, financial, healthcare and retail verticals.
Effective monitoring of an API infrastructure also requires tracking each user's activity across all APIs, regardless of the APIs' location. Could you detect that a user accessed AWS-based APIs and APIs in your own datacenter using different tokens and IP addresses? This requires the ability to link all API traffic to the identity of each user along with tokens, cookies and IP addresses used across all on-premise and cloud-based API gateways accessed.
PingOne API Intelligence delivers those capabilities and more:
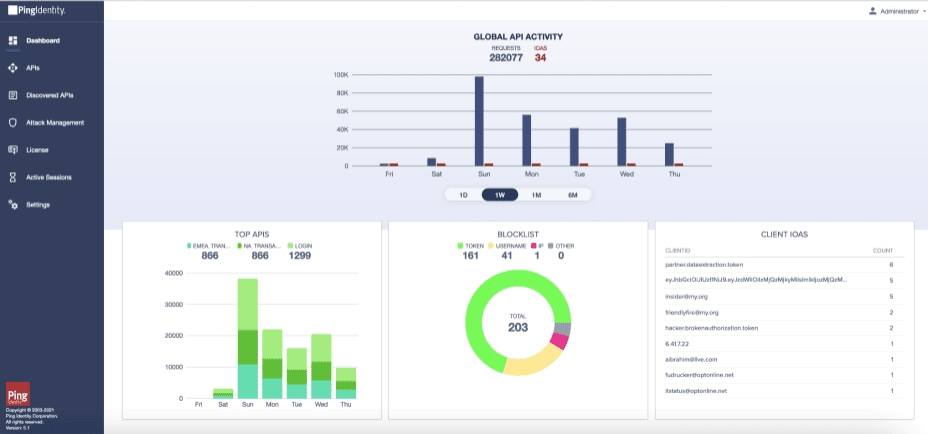
- Brings all API traffic into a single pane-of-glass with a dashboard to monitor your entire API infrastructure across all on-premise and cloud API gateways.
- Continuously monitors all API traffic to track sessions associated with each user identity. This in order to deliver in-depth insights into all user API activity for auditing and forensic reports.
The PingOne Dashboard delivers detailed activity information which can be used for auditing, forensic and governance reports, including:
- Which APIs are active—APIs discovery detects all active APIs including known, forgotten and unknown APIs.
- For each API, API endpoints (URLs) are reported along with users, tokens, cookies, API keys and IP addresses used. API definitions are also built from observed traffic.
- What each user is accessing. For each user identity the following is reported: APIs and URLs accessed across all API gateways and clouds along with tokens, cookies, API keys and IP addresses used.

User Activity Across APIs
Summary of API visibility capabilities:
Single pane-of-glass dashboard monitors the entire API infrastructure across all gateways, data centers and clouds
- Track all API activity and associates traffic to each user identity–with all APIs, URLs, tokens and IP addresses used by each user
- Discover APIs including shadow APIs, forgotten APIs and old API versions still active
- Deep activity insights are delivered for auditing, forensic and governance reports
Expose Anomalous APIs and Partners Behavior in Production
With nearly 83% of network traffic attributed to APIs, it is critical to identify good and bad behaviors for utmost API security. Of course, bad behavior doesn't always have to be a hacker causing a breach and not all API issues are about hacking.
PingOne API Intelligence uses AI/ML to help you recognize a wide variety of abnormal situations with APIs in production before they become costly and embarrassing—or exploited by hackers. It can detect and alert your DevOps and security teams on anomalous API behavior such as API bugs, deployment issues, OWASP API Top 10 vulnerabilities and other mishaps, which can lead to data leaks, service disruption and account takeover situations.
An example of a situation in production is an API processing requests without proper authentication and authorization checks. This results in the API returning data that it shouldn't because of a design flaw or implementation mistake. Peloton, Echelon, John Deere and several other organizations made the news recently because of this issue. At Peloton, the vulnerability could allow anyone to look up any user's private account data, despite their profile being on private mode. Peloton has since fixed the bug. A couple of vulnerabilities in John Deere's APIs would have exposed personal data about their customers. Those bugs have been fixed as well.
Another example of an abnormal situation with an API in production is at an e-commerce site with an API responsible for computing sales taxes. The API was overrun by an internal application, which prevented customers from completing purchases. Not only did this add considerable friction to the customer experience but it also resulted in sizable losses for the retailer that day.
PingOne API intelligence can help remediate these issues in production. In the first scenario, requests can be blocked automatically and the team alerted to fix the API. In the situation in which an API is being overrun by another application, the team would be alerted with insight into the issue and action can be immediately taken, including modifying the rate-limiting configuration on the API gateway. The guilty application could be automatically blocked as well.
It is also essential to monitor partners and third-party application developers that are using your APIs in order to detect any abuse quickly. Several mishaps linked to partners misusing APIs have recently surfaced in the news, negatively impacting the reputation of the organizations that provided the APIs. In one known instance, the misuse of an API by a partner resulted in a massive security breach. This is why dentifying those issues in a timely manner is critical.
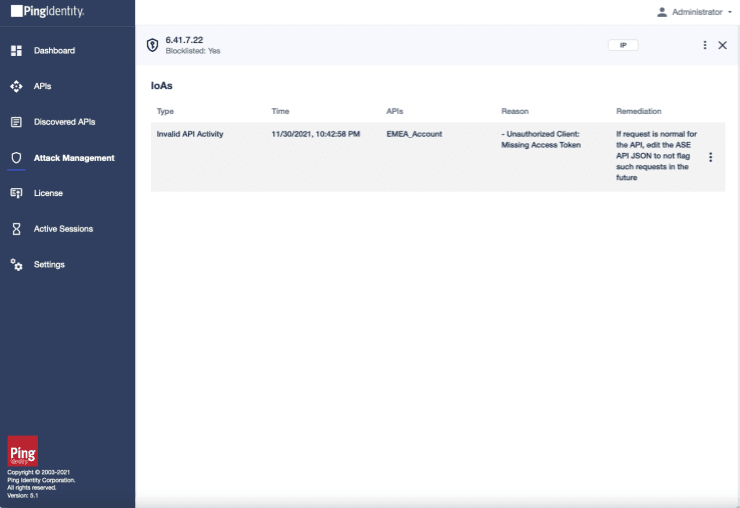
Potential API Bug
Summary of API anomalies detection capabilities:
AI-based detection of API issues and vulnerabilities before they become costly and embarrassing, or worst exploited by hackers
- Session activities are continuously analyzed for each user with AI/ML, pre and post-authentication, to identify situations that deviate from normal
- Identify API design flaws, API bugs, misconfigurations, deployment issues and other OWASP top 10 vulnerabilities, while in production, to prevent accidental data leaks, service disruption and account takeover situations
- Remediate with automated blocking and alerts to responsible teams
- Provide insights to the DevOps team on how to address issues
- Detect partners and 3rd party developers misusing or abusing APIs so that proper actions can be taken quickly
Detect and Automatically Block API Cyberattacks
Given the high value that stolen private data commands, bad actors are conducting sophisticated and successful attacks that bypass traditional API security measures, such as those provided by CDNs, WAFs and next gen WAFs.
These hackers look like normal users with valid credentials and accounts, which makes them particularly difficult to detect with traditional security. Hackers obtain credentials through phishing attacks, snooping access tokens or simply by opening their own accounts.
One tactic hackers are taking advantage of is to orchestrate API attacks using their own valid credentials. They simply sign up for a new bank account, a healthcare provider or a social site. Then, they use the provided app to reverse engineer the APIs. Once logged in, they bypass the application user interface and "work" directly on the API looking for vulnerabilities to exploit in order to take over accounts.
Thus, hackers look like real users—or are real customers—that passed the authentication and authorization steps and are now accessing applications and APIs at will. That makes it difficult for security teams to spot breaches. In fact, most API-based breaches are rarely detected and when they are, it is usually after many months.
Therefore, one cannot rely on rule-based systems such as those used for traditional web security as the hackers do not follow templated attacks. API attacks are "free-styled" and constantly changing as they are specific to the API targeted. You could think of each attack as custom crafted for the API, and that is why signature and rule-based security—such as those used in WAFs—do not offer protection against most API attacks.
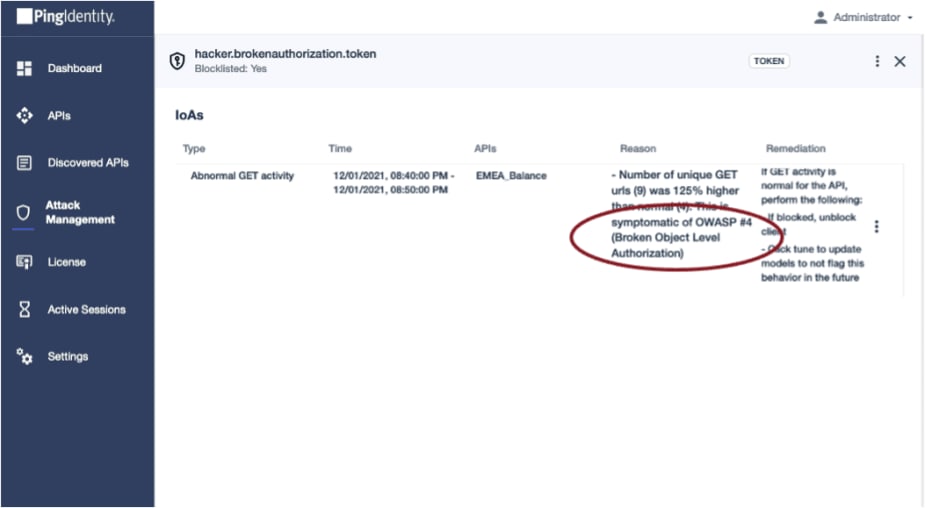
Hacking on API automatically blocked
AI-based hacking detection and blocking:
PingOne API Intelligence leverages AI/ML to expose and block this new generation of constantly evolving cyberattacks including:
- Authentication system attacks: Bad actors use brute force attacks to breach API infrastructures using:
- Stolen API keys and tokens
- Stolen username and password through phishing attacks
- Credential stuffing on API login services with bots that stay below rate limits
- Data and application attacks: Hackers typically use a valid account to reverse-engineer APIs in order to take over other accounts to steal information, commit fraud, disrupt a service, control a system or compromise data.
Some examples of common application and data attacks include:
- Data extraction or theft: When a hacker programs an attack to hit multiple accounts for information as opposed to going after just one.
- Account takeover attack: When hacker used its credentials to work out the API and reach other accounts.
- Fraud: When a hacker leverages the stolen account information for financial gain.
- Broken object level authorization: When a hacker finds vulnerabilities by manipulating API calls to access data, which should be restricted to authorized users.
- Data deletion or manipulation: When a hacker or employee erases or changes data to compromise or sabotage a system.
- Data injected into application service: When a hacker attempts to overload an API service by injecting excessive data, malicious code such as a keylogger or loading overly large data files.
- Query string or API header manipulation: When a hacker modifies the query string or headers to access unauthorized services or disrupt API processing.
- Targeted API DoS/DDoS Attacks: Hackers tune attacks to stay below rate limits, which can disable services provided by APIs and/or damage the user experience.
- API DDoS attacks are created to overwhelm services and take them offline. Hackers use many machines to send normal amounts of traffic to an API service, making it very difficult to detect; especially if they stay below the rate limits. Altogether, it creates a massive traffic overload.
- While API gateways specifically implement rate limiting to control individual activity, they generally cannot view aggregate traffic rates involving multiple clients. Therefore, they are powerless against a distributed DDoS attack.
- DDoS attacks target session management, login and other services key to application reliability, disrupting the application and hugely impacting both customer access and computing costs.
API honeypot for instant API probing detection and blocking
PingOne API Intelligence also leverages API deception techniques with API honeypots. These are fake APIs that would never be used by the application developers but are exposed as—and look—real. Common hacking techniques involve probing, or fuzzing, an organization's APIs to understand how they work and to trigger error messages that may include valuable information in the error message—such as tracing used by developers to debug and left by mistake in production, etc. Once a hacker "touches" a honeypot API, it is instantly detected and any access to production APIs is blocked.
Summary of API Cyberattacks detection and blocking capabilities
AI-based detection and blocking of cyberattacks on APIs to prevent account takeover and data breaches
- Can identify today's freestyle, constantly changing attacks on APIs–not detected by traditional security
- Detects hackers that use stolen credentials to steal data, commit fraud, etc.
- Recognizes when hackers are reverse engineering an API to breach
API Deception for instant attack detection and blocking. Use of honeypots to identify and quarantine potential hackers before they can access production APIs.
API Security Deployment Flexibility
Ping Identity provides two deployment options to meet your business requirements: SaaS cloud service or software, for on-premise and cloud deployments using DevOps techniques such as Docker containers and Kubernetes.
PingOne API Intelligence is a cloud service where the AI engines, data stores and dashboard environment are managed for you. Alternatively, if your preference is for keeping those functions on-premise under your control, you can deploy PingIntelligence for APIs in your datacenters and cloud environments using Docker/Kubernetes containers or virtual machines. Just select the option that best fits your business needs and API infrastructure.
API Gateway and Load Balancer Integrations
You can leverage your existing API infrastructure investments with integrations available to connect to a wide variety of API gateways and some load balancers. An agent is used to capture your gateway clusters' traffic metadata for processing by the AI engine deployed in the cloud or on-premise, depending on your deployment choice.
You can deploy with your API gateways in two ways:
- Sideband mode where the agent is placed next to the gateways to minimize network and infrastructure modifications.
- Inline mode with the agent deployed as a high-performance reverse proxy. When deployed inline, the solution also supports APIs that are implemented directly on application servers and not on an API gateway.

Ping Identity's API security solutions offer a great deal of scale and deployment flexibility to accommodate the most demanding API infrastructures.
An Intelligent Approach to API Security
As APIs are now being deployed across multiple datacenters, private clouds and public clouds, organizations need to evolve their approach on how to protect the valuable resources they interface. This requires businesses to leverage AI/ML to centralize all monitoring and traffic analysis to create a single pane-of-glass of API traffic, alongside anomaly and attack detection and remediation. Ultimately, taking an intelligent approach to API security enables your business to protect essential digital infrastructures against mishaps and hackers, while enabling teams to demonstrate compliance with internal policies and regulations.
Try PingOne API Intelligence today to start monitoring your API traffic, gain in-depth insights into anomalous API behavior and detect and block potential threats to your organization.
