Securing Sensitive Customer Data with Fine-grained Access Controls
Allowing applications access to personal data can greatly enhance the user experience, but unfettered access to sensitive or regulated data can result in diminished security, compliance violations and lost customer trust. To achieve just the right balance of privacy and preferences, enterprises look to implement centralized data access governance policies that enable consent based on customer wishes.
Fine-grained access control is a vital piece of this approach. Attribute-level, dynamic and externalized authorization helps enterprises comply with regulations, enforce consents, enable Zero Trust security and secure customer data APIs—all key requirements in meeting your customers’ privacy expectations.
Four Common Data Obstacles Facing Enterprises
There are a multitude of reasons why it’s hard to secure and authorize access to customer data, but here are a few of the biggest obstacles you need to overcome:
- Data is detailed and complex.
- Data is everywhere and accessed in many ways.
- You’re dealing with multiple stakeholders on data security.
- It’s often seemingly impossible to reconcile requirements.
Data is complex and everywhere
By its very nature, data is nuanced, detailed, and massive—Big Data, anyone? Additionally, even if your customer profiles are already consolidated in a powerful, scalable user directory, there is always going to be non-profile, user-related data in siloed data stores across your organization. It’s being accessed in many ways by all kinds of clients, users, applications, microservices and APIs through all sorts of retrieval and access mechanisms including LDAP, RDBMS, NoSQL, microservices and APIs.
Multiple stakeholders have different requirements
Everyone seems to think they get a say in how user-related data is protected: regulatory compliance professionals, internal marketing analysts who collect the data, IAM, security, network admins and even customers themselves (because we all seem to think we own our own data). But nobody is getting all of those stakeholders together and figuring out a good way to collaborate on what fine-grained data access policies need to be.
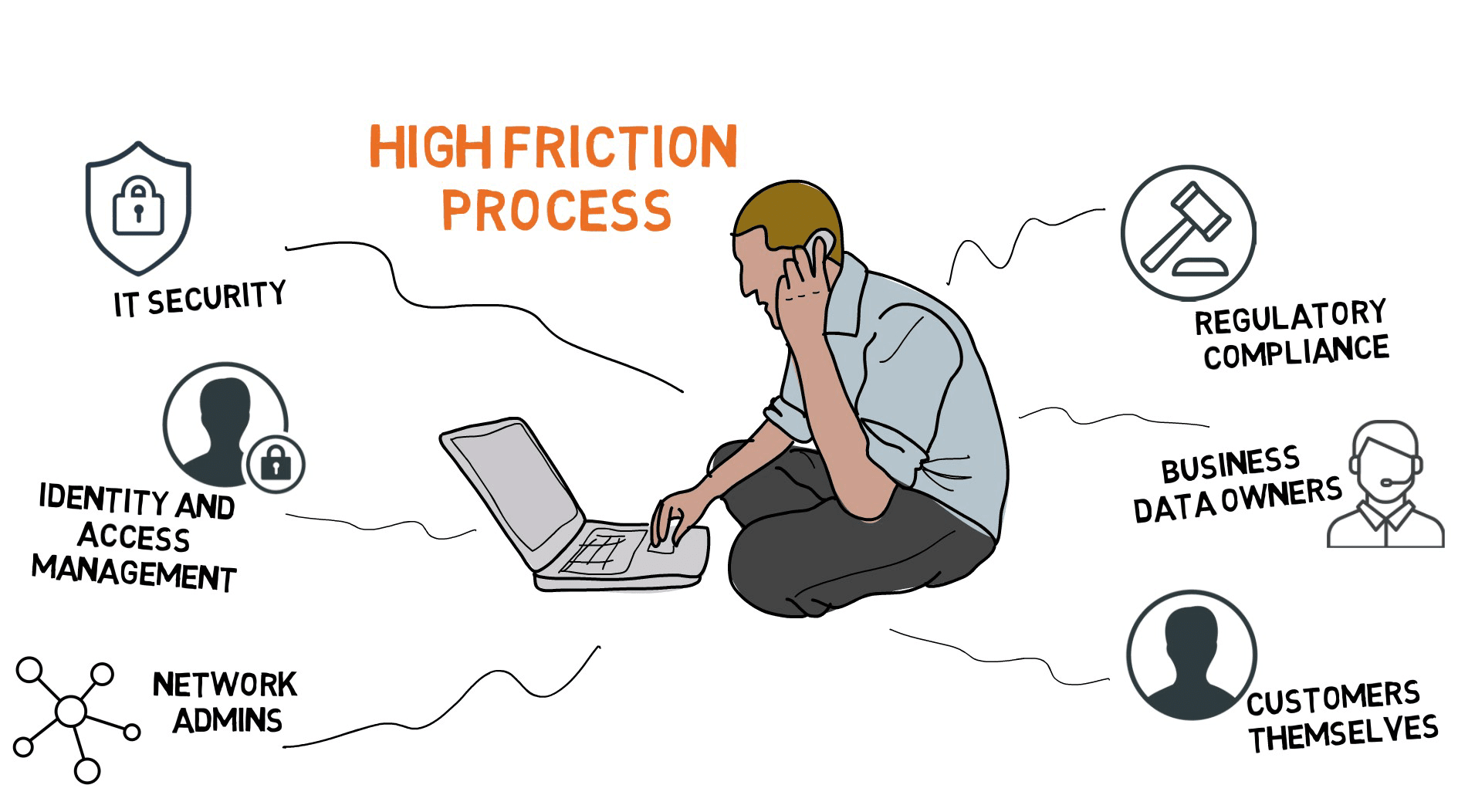
Today, gathering data security input, reconciling requirements, and coding, testing and validating policies falls to developers. Meanwhile, all of your stakeholders are impatient and annoyed because they don’t have visibility into other stakeholder requirements.
Business Initiatives Around Fine-grained Customer Data Access
All by itself, this high-friction process and burden on API developers and database admins may be enough for an enterprise to take action. However, there are many different business initiatives that also come into play, including:
- Enforcing data privacy preferences & customer data consents
- Complying with customer data protection regulations (e.g., GDPR, CCPA, etc.)
- Enabling Zero Trust data security (attribute-level access controls)
- Securing customer data accessed by third parties through open business APIs
To further these initiatives, enterprises are turning to fine-grained customer data authorization solutions.
Meet PingDataGovernance
As part of the Ping Intelligent Identity Platform, PingDataGovernance is an identity and access management capability that helps secure access at the data layer. Think of it like a centralized control panel for data authorization across your enterprise. It’s a fine-grained data access policy engine that helps overcome the four common obstacles around data and enables a diverse set of business initiatives that point to the need for customer data access controls.
Features in This Month’s Release
This month, a major release is available that includes key features such as its fine-grained authorization policy engine, graphical user interface (GUI) and flexible deployment options.
- Fine-grained policy engine: Helps achieve most of the business initiatives around securing access to customer data across your enterprise
- GUI and deployment flexibility: Helps operationalize fine-grained access controls within the realities of the data obstacles you’re facing
The key benefits of PingDataGovernance for your organization are that it enables:
- fine-grained authorization
- dynamic authorization
- externalized authorization
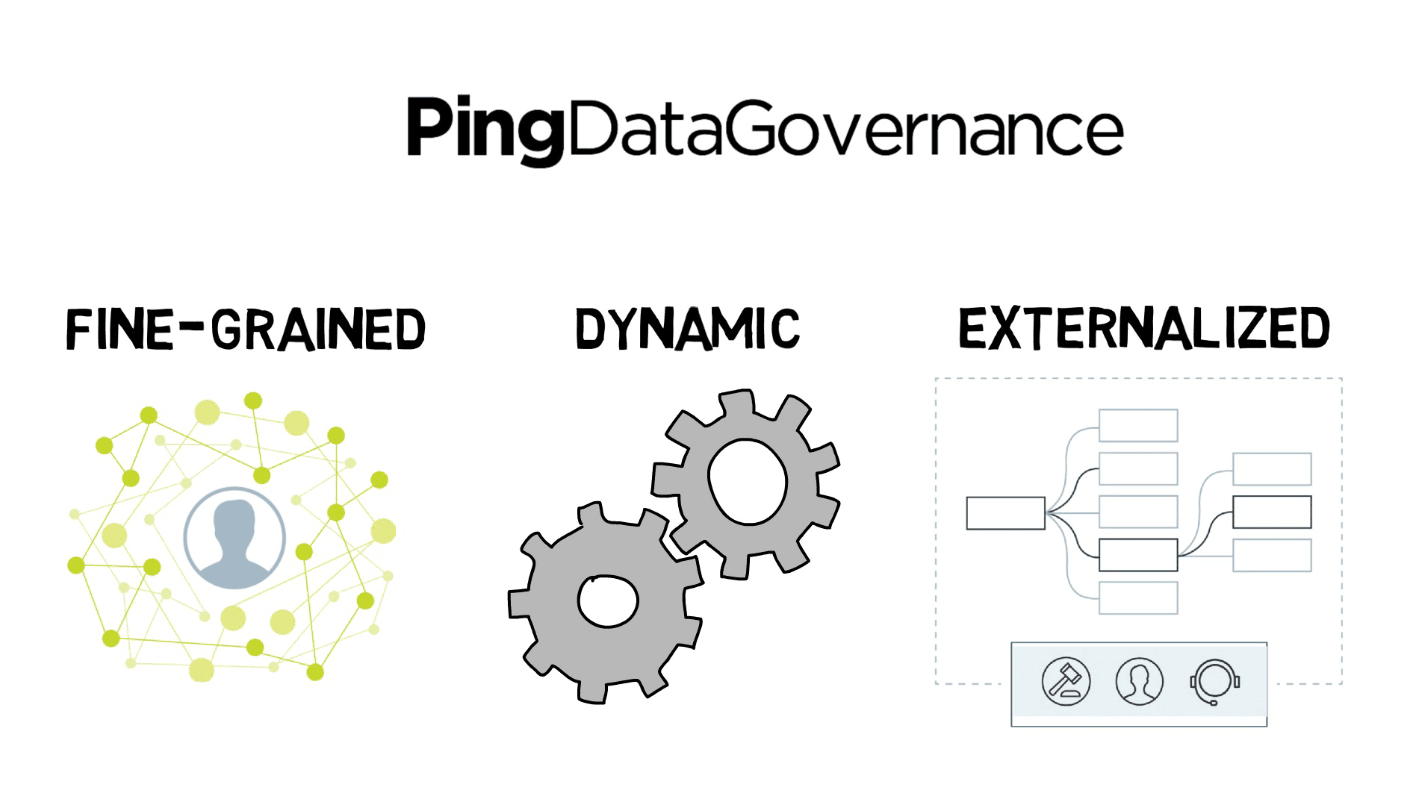
Let’s take a closer look at what we mean by fine-grained, dynamic, and externalized authorization for data, and how they benefit your enterprise.
What is Fine-grained Authorization?
Fine-grained Authorization for Data
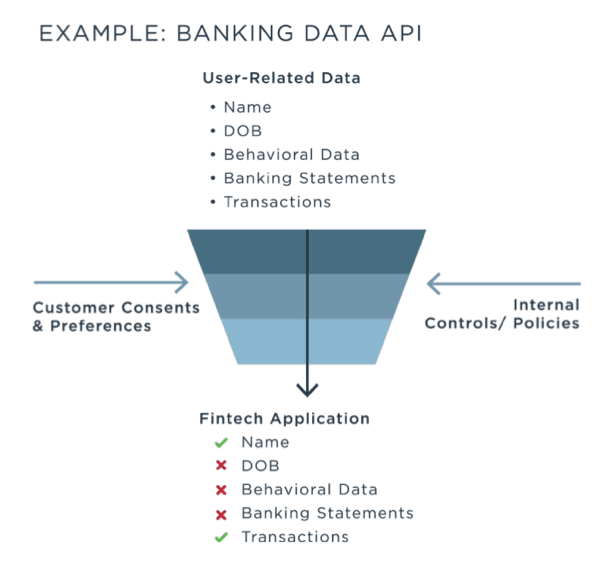
PingDataGovernance enables administration and enforcement of attribute-level authorization policies for consents, consumer data privacy and internal data security controls. It can allow, block, filter or obfuscate a data request, limiting the response to allow only authorized user-related data attributes instead of just allowing or blocking everything about a user. Filtering and obfuscating is a big deal—PingDataGovernance actually modifies the body of the response instead of just determining whether to allow the request. The ability to extract and dynamically transform data from many different kinds of sources without writing any code is pretty powerful.
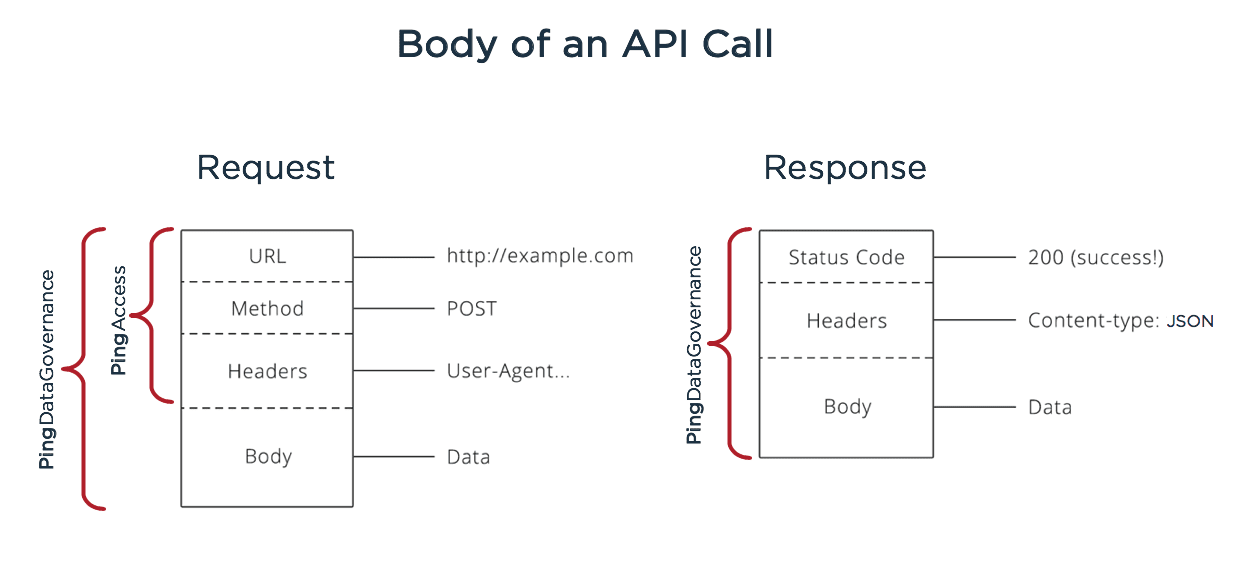
PingDataGovernance Enables Policies on the Body of an API Call
API calls have both a request and a response, and each of them has a body. PingAccess and other resource server components acting as an API gateway can handle API authorization too, but not down to the body level. On API requests, fine-grained authorization policies at the body level can limit what a user can do in an otherwise authorized API call (e.g., if they're authorizing a payment that exceeds a certain limit, modifying a high volume of data entries, etc). On API responses, outbound data gets examined against policy and consent records for unauthorized, unintended, sensitive or restricted data that should be dynamically modified or removed from the response prior to release to the client.
How Fine-grained Authorization for Data Helps
Organizations turn to Ping Identity for help with data access controls for very different business initiatives.
Quick Question:
Which business initiative is driving you to look into fine-grained data access today?
A. Enforcing data privacy preferences & customer data consents
B. Complying with customer data protection regulations (e.g., GDPR, CCPA, etc.)
C. Enabling Zero Trust security (attribute-level access controls)
D. Securing customer data accessed by third parties through open business APIs
I suggest you scroll specifically to the business initiatives (A, B, C or D) that matter to you. There's a slight overlap because all of them point to the need for fine-grained access to customer data, but mostly these are separate business initiatives, and you may not find all of them relevant.
A. Customer Data Privacy Preferences & Consent Enforcement
Apparently we’re all getting a little suspicious of corporations tracking data about us and using it for who knows what. Technically, if it’s data about you, you should be the official owner and have rights regarding what’s being collected and how it’s used. Even when it’s not required by regulation, many enterprises are balancing data privacy and personalization by providing user-managed consent as a mechanism to build trust with consumers.
With so much user-related data including user profiles, transactions and browsing behavior, it’s one thing to provide a simple interface to be able to collect and allow customers to manage and revoke access to their data being shared or used. It’s another thing entirely to be able to request and enforce consents at the points where customer data is being requested. Data is everywhere, and it’s being accessed at a lot of different places; it’s critical to have an enforcement point that can span all those possibilities.
How PingDataGovernance Helps With Privacy Preferences and Consents
Centralized, fine-grained data authorization policies can enable delegated consent to data access, preference lookups and enforcement of data access decisions based on customers’ wishes, everywhere the data is stored or accessed.
B. Regulatory Compliance with Consumer Data Privacy Legislation
In the wake of consumer data breaches and exposure, many regulatory bodies aren’t leaving consumer data privacy up to corporations anymore. Around the world, a patchwork of data protection regulations imposes complex requirements for consumer data privacy and data rights, including transparency, consents and the ability to opt-in/opt-out of data collection and usage.
There are several types of consumer data protection regulations with similar motivations. For example, the California Consumer Privacy Act (CCPA) and the EU’s General Data Protection Regulation (GDPR) are focused on consumer data privacy and require consent. The EU’s Revised Payment Services Directive (PSD2) and Australia’s Consumer Data Right (CDR) both require securely sharing customer data in open APIs, giving customers rights to share their own data with competitors in the hopes of increasing competition in the market. In the U.S., the Health Insurance Portability and Accountability Act (HIPAA) and Gramm-Leach-Bliley Act (GLBA), also known as the Financial Services Modernization Act, are industry-specific Acts of Congress around data safeguarding of sensitive customer information beyond just personally identifiable information (PII).
In fact, what all these different data privacy regulations, acts and directives have in common is that they aren’t plainly limited to data that’s in a user profile; they apply to any type of sensitive customer data. Some also have complex rules around the age of the citizen, location, classification of data, contracts between companies, and so on.
How PingDataGovernance Helps With Data Privacy Regulations
Fine-grained authorization policies can enforce compliance with new and changing consumer data protection legislation, often requiring consents. Using the GUI, non-technical users in regulatory compliance functions can flexibly build and enforce policies to meet requirements, while also complying with future legislation.
C. Zero Trust (i.e., attribute-based/attribute-level access controls)
Many organizations are looking to implement attribute-level access rules on data. Some are even subscribing to a Zero Trust, an IT security model. Are you striving to implement the principle of “least-privilege access”? If so, you might be adopting a Zero Trust mindset without knowing it. Zero Trust is all about strict verification of all users trying to access resources, regardless of whether they are on the network or connecting remotely. Instead, IT security microsegments the security perimeter into smaller zones for more granular access control on an attribute-by-attribute basis.
How PingDataGovernance Helps with Zero Trust for Data
Think of fine-grained authorization policies as “micro perimeters” around customer data attributes. You can set up policies around any requester/client or any type of user data, and even use risk scores and data in sources outside what’s contained in an access token to make real-time authorization decisions so that only data that is needed and authorized is allowed.
D. Delegated Authorization to Customer Data APIs (i.e., Open Banking, Open Business)
Businesses in all industries are creating open APIs for better integration with partners and other third parties. We like to call this trend “Open Business.” Some APIs allow customers to share and access their own data with a third-party app or service. This means that there’s a lot of sensitive customer data in APIs with lots of complex rules as to who can see or do what.
The use case that is probably the first that comes to mind is the financial industry, where the term “Open Banking” is used not only in reference to a named regulation in the UK, but also as a global movement. All around the world, whether required by regulation or not, financial institutions are opting to provide customer account APIs. So when a bank gets a request from a data aggregator (e.g., Mint.com) to access a particular customer’s data through the API, it’s important to make sure it’s really their banking customer on the other side and that the customer consented to this data being shared with the third-party app.
How PingDataGovernance Secures Customer Data in APIs
API security requires fine-grained authorization to API operations and access controls on API data. PingDataGovernance's authorization policies fit right into a secure API access workflow to check and enforce complex rules and customer consents to begin, continue or revoke sharing sensitive customer data with third parties in APIs.
What is Dynamic Authorization?
Dynamic Authorization for Data
Data is always growing, with frequent updates, and multiple stakeholders like customers and regulators are continually changing their preferences and rules, so it’s important not to rely solely on static token claims in order to make authorization decisions on data attributes. Dynamic authorization with attribute-based access control (ABAC) can incorporate real-time information outside of an access token as part of the policy.
Dynamic authorization policies can be based on anything: any state, attribute, token claim, data source, etc. The Trust Framework section of the GUI is an interface for IT administrators to set up live connections to REST, LDAP and RDBMS attribute sources (e.g., risk scores, privacy preferences, state, relationships, etc.) across your enterprise. Wherever you have a piece of information or data that you’d like to use as a policy attribute, you link to it in the Trust Framework; this is a great place to establish a lookup to third-party risk-scoring systems.
How Dynamic Authorization Helps
Rather than storing static copies of data attributes that might have just changed, thanks to real-time data connections, when attributes change, the policy outcome changes too. For example, if a user revokes data access for XYZ Company, the consent record changes and the outcome of XYZ’s data request is different (it is blocked), but no policy change was needed.
When data and information are stored all over your enterprise, it can be hard to bring all the key attributes together at run-time so that they can be used as attributes in dynamic authorization policies. The Trust Framework section of the GUI establishes real-time connections to structured data across your enterprise so that you can use it in an ABAC policy to achieve dynamic authorization.
What is Externalized Authorization?
Externalized Authorization for Data
Policy administration needs to be managed in collaboration among non-technical business users. PingDataGovernance provides visibility and control through a centralized, single pane of glass for data that organizes the whole policy authoring, testing and deployment process. The Policies section of the GUI is a central place where stakeholders drag and drop data attributes from the Trust Framework section into a collaborative, visual policy decision tree.
How Externalized Authorization Helps
With great fine-grained power comes great responsibility. The GUI distributes that responsibility, solving many of the issues of wielding, managing and operationalizing fine-grained access controls across an enterprise. Thanks to the graphical, drag & drop interface, policy authoring is abstracted from code into business users’ hands, and the burden of enforcing access controls doesn’t fall solely on developers anymore. This helps address the data obstacles of dealing with multiple stakeholders and reconciling requirements. And there’s a bonus—developers no longer need to code policies, which reduces friction and lengthy development cycles.
Granular Access Controls for Data Stores and APIs
Deployed Where It Counts
There are two key places where data is involved in data security:
- the data being used in an ABAC policy
- the data being protected
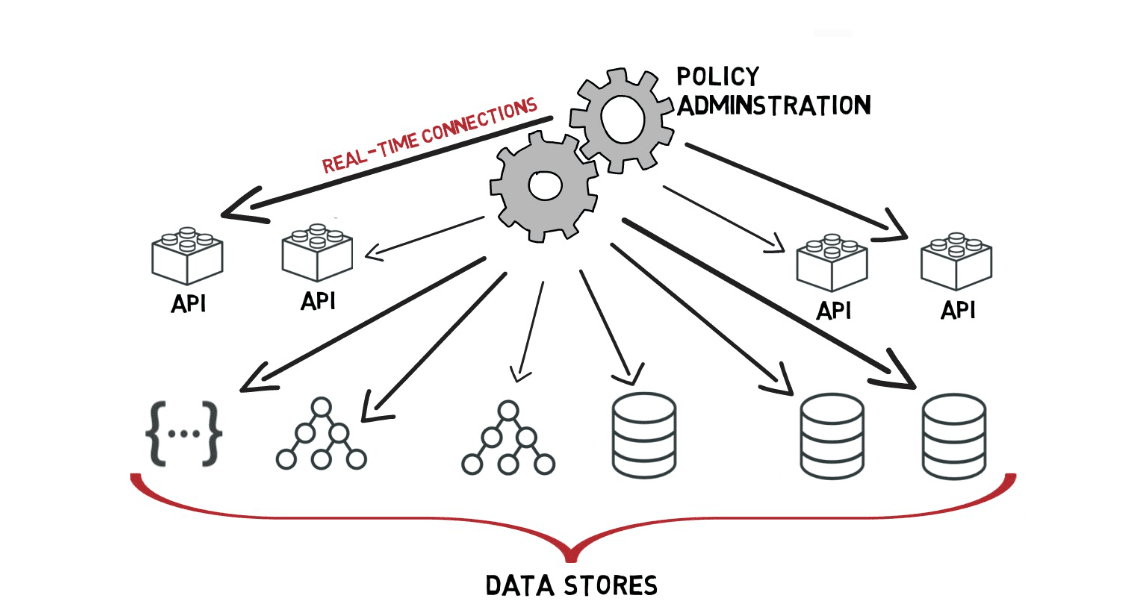
We already talked about how the Trust Framework interface allows you to hook to data sources that will be used as policy attributes. But how do you arrange for what data is under the protection of PingDataGovernance?
Since data and information is stored all over your enterprise, it’s challenging to manage its protection without a single access point. The solution is in how and where you deploy PingDataGovernance. You deploy PingDataGovernance in front of the resources and data on which you want to apply its access control policies.
PingDataGovernance provides an API layer of protection either as a proxy or sideband with existing JSON APIs or as a SCIM REST API layer in front of your data stores. So once you’ve done an inventory and figured out where all the data that you want to protect sits, you deploy it on the access points for all data stores and APIs.
Sharing data with third parties is becoming common in a digital ecosystem, which means more and more data is being accessed through APIs, but not all data authorization vendors can deploy a solution at the API layer. Putting data access controls at the API plane is closer to where and how data is actually being consumed. Deploying PingDataGovernance on your existing APIs enables data security policies to “see the forest for the trees,” since the API gateway layer already combines data sources.
Additional Use Cases
We’ve talked a lot about how PingDataGovernance can help with securing access to customer data. But we’d like to point out that it’s not limited to customer data; it can be applied to any user-related data, such as employees, partners, etc. In fact, it’s not only limited to user-related data—it can be applied to any structured data. And its capabilities even step outside its name since there’s a use case that doesn’t necessarily have to be data-related at all. It can enable fine-grained authorization to API controls that have nothing to do with data, such as initiating a payment or triggering a system change.
Watch This Video to See How PingDataGovernance Helps
Enterprises need fine-grained data access controls to comply with consumer privacy and data protection legislation, minimize the risk and impact of consumer data exposure or breaches, and meet user expectations about data rights, consents and privacy preferences. Protecting sensitive, personal data requires fine-grained, dynamic and externalized authorization capabilities that can be deployed where it counts.
View this ~3-minute video to learn how organizations are achieving attribute-based access controls, regulatory compliance, Zero Trust security, data privacy and consent enforcement with PingDataGovernance.
