PingAuthorize
Tour the Product
Meet PingAuthorize
PingAuthorize provides a centralized policy creation and enforcement engine that evaluates real-time data points and contextual information to allow access to applications and data. Have you outgrown role-based access rules? PingAuthorize gives you the flexibility to easily create policies based on a variety of data points through a drag-and-drop UI. This software makes it easy to comply with regulatory requirements, enhance security, and improve business agility.
How it Works
PingAuthorize allows your developers to access data by invoking a SCIM API rather than connecting directly, or at the API layer as a proxy or sideband to existing API management gateways. Administrators create a “trust framework” of access policies by connecting and defining the data sources, hierarchies of conditions, and evaluation rules. PingAuthorize’s policy decision engine evaluates all access requests and responses and enforces policies. At the API layer and beyond user data, PingAuthorize can govern any type of user-related structured data, like healthcare records, IoT device data, and banking transactions.
With PingAuthorize you can:
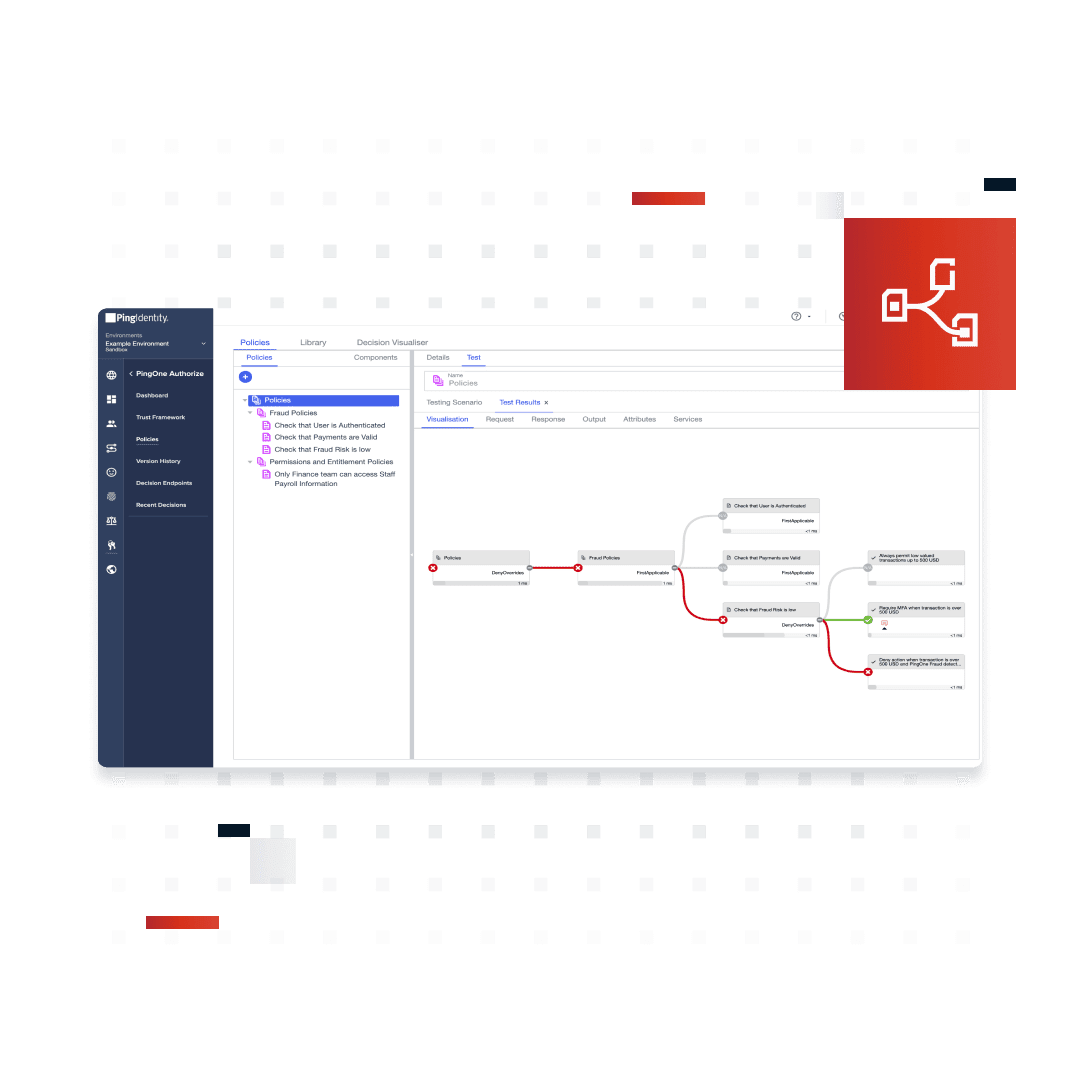
Easily control authorization logic and update policies with a simple drag-and-drop UI
Centrally enforce policies to comply with regulatory requirements, enhance security, and improve business agility
Move beyond role-based architecture controls for decisioning and save time by taking the burden off resource owners to make authorization rule changes
User Journey Alignment
PingAuthorize is integral to the “Authorized” stage of the user journey.
Enforce Data Anywhere
PingAuthorize can enforce data access policies at either the datastore or API layer. In either case, it monitors requests and responses and enforces policy decisions. Best of all, it doesn’t require API developers, database administrators, or app developers to modify their code to ensure that only compliant data is returned.
Filter Specific Attributes
Configure PingAuthorize policies to allow an API call, but then filter, obfuscate, or remove specific data attributes in the response. This gives you tremendous flexibility when it comes to managing fine-grained data authorization and control.
Delegate Data Access
PingAuthorize enables users to delegate access control of their data to customer service reps, trusted individuals, family members, third parties, and others. For example, you can limit search results to only those users a delegated administrator has the right to view. You can also enforce which attributes delegated administrators can view and the actions they can take.
Benefits & Features
Construct fine-grained access rules based on identity attributes, entitlements, consents, and any other contextual information
Externalize policy administration to business users instead of developers
Provide and enforce consent, data privacy, and other regulations in a single console
Ingest fraud and risk signals to build adaptive authentication and authorization
Anyone can update policies in minutes with a simple drag-and-drop UI
Orchestrate context-aware authentication and approval workflows
Allow, block, filter or obfuscate unauthorized data
Deployed as API security gateway or as SCIM API for data stores
Easily configure access policies with out-of-the-box examples and templates
Business Value
Gain business &
IT agility
Minimize friction
in the user
experience
Meet regulatory
requirements
Flexible Deployment Options
PingAuthorize can be deployed as:
PingOne Cloud Software - Deploy anywhere cloud containers
Platform Alignment
PingAuthorize is an integral part of the PingOne Platform and is essential to the “Authorize” phase of the identity and access management user journey.
Platform Alignment
PingAuthorize is an integral part of the PingOne Platform and is essential to the “Authorize” phase of the identity and access management user journey.