Every Passwordless Journey Begins With a Single Step
“For every lock, there is someone out there trying to pick it or break in.” —David Bernstein
Just like every lock can be picked, all password protections can be defeated. And just like with locks, there’s always someone in cyberspace trying to gain access to a password-protected account.
Cyber threats are growing rapidly and hackers are becoming more and more sophisticated. In October, Check Point Research reported a 40% increase in attacks globally compared to 2020, with 1 out of every 61 organizations worldwide impacted by ransomware each week.
Despite their vulnerability, passwords are still widely used. Datto’s Global State of Ransomware Report notes weak passwords are a top cause for ransomware attacks. Verizon reported in 2016 that 63% of network intrusions are the result of compromised passwords and usernames. Awareness of the need to adopt a more secure and convenient solution is growing in the security community, as is the understanding of the best alternative.
It’s time to implement highly secure passwordless protection for Windows machines.
Passwordless Adoption
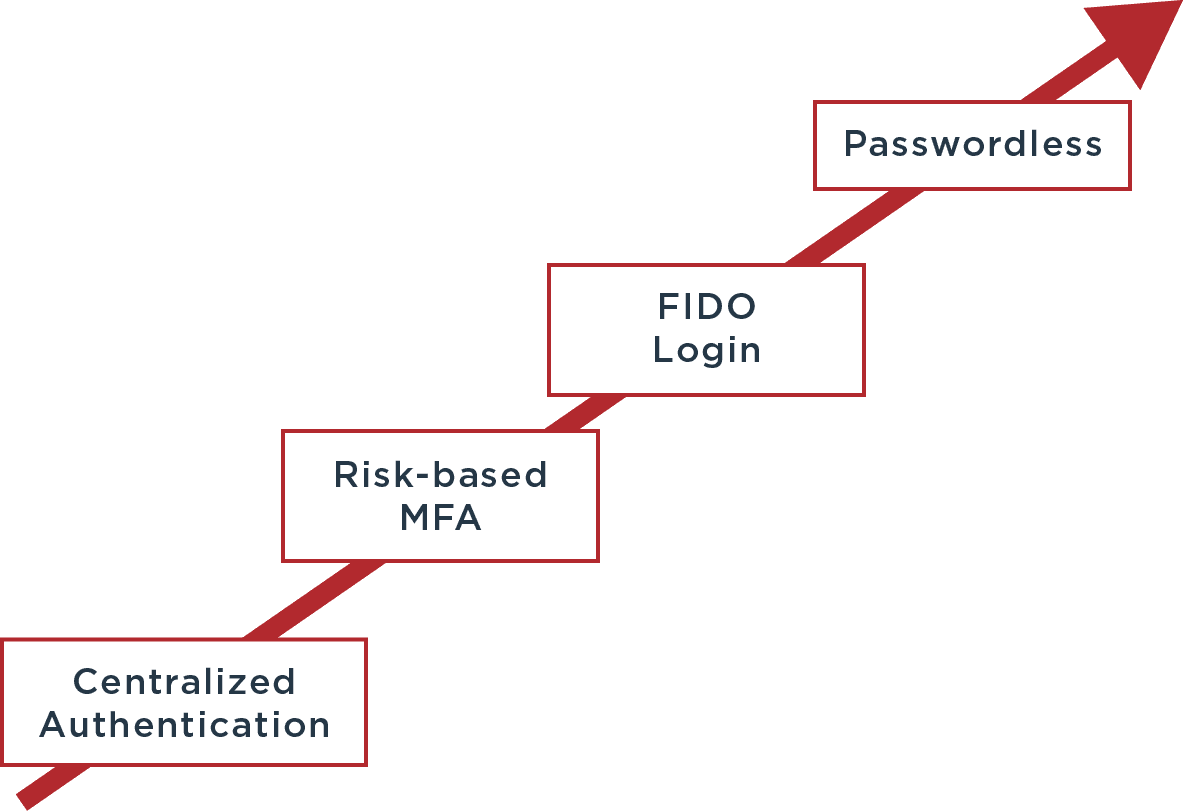
The journey to passwordless is not short, but there’s a clear roadmap to reaching that goal. You start with the basics—centralized authentication based on username, password, and multi-factor authentication (MFA) to provide a single sign-on experience.
Progress continues by phasing out passwords using risk services and biometric authentication. The home stretch of our trip expands the use of FIDO-certified products and devices, until you arrive at your destination. Passwords are history.
Ping Identity is the experienced guide to help get you there. We partner with our customers to share best practices and bring them the best solution among our identity and access management offerings. We have a few more steps before our own trek is complete, but we believe that by working together with you, we not only reach our destination sooner, we can also develop and fine-tune the tools and processes the market requires.
User Experience + Security
Security is always a top priority, but it can’t be the only one. Unhappy users inevitably abandon a well-protected solution if they find it difficult or time consuming to use. That makes experience an important topic, as no administrator can accept a solution that frustrates end users. A simple, fast solution is needed to convince potential users to give it a try. If it provides a good experience, your user base will readily adopt it.
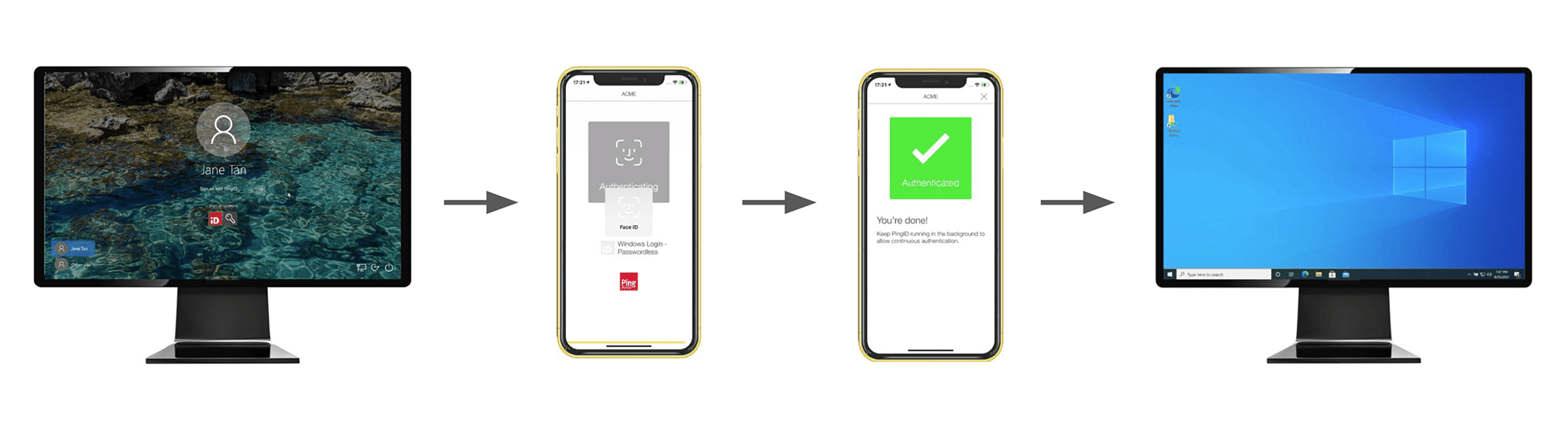
That’s why, as we developed our Windows Login Passwordless solution, we paid careful attention to end users and their experience. Everyone with the PingID mobile application installed and configured on a mobile device can quickly and easily sign in to Windows more securely than ever—without a password.
Just one click prompts approval in the mobile device using your biometrics to identify you. Within seconds, you’re signed in. Who wouldn’t welcome such a solution?
But what about security? A great user experience is not enough. Administrators must know their end users are well protected and have confidence that their most valuable assets—their laptops and desktops—are safe from hackers.
With security a top priority for our new solution, using certificates to authenticate users into Windows makes perfect sense. The challenge is to make certificates easy for administrators to configure and for users to use, while ensuring users are protected from hackers. Stealing a user’s password might be tricky, but it’s possible. It’s impossible to forge a user certificate, which is why their use is a security best practice.
What’s Next?
What’s the next step in the passwordless journey? Ping Identity team has several ideas. For example, allowing users authenticated through Windows Login Passwordless to skip MFA authentication to web applications, since MFA is redundant and adds friction to the user experience.
We can also see companies combining our simple passwordless authentication flow with our intelligent risk management service for even better security levels to create a great user experience with minimal security concerns.
This is just the tip of the iceberg. Much more is planned, and the future is bright for passwordless flows, which will soon be the most common way to authenticate users.
Check out our white paper to learn more about passwordless authentication.
