At Ping, we work with some of the largest enterprises in the world, who have the most complex passwordless use cases and goals. As a result, we’ve created the following journey, a phased approach for organizations to realize their passwordless visions. Of course, organizations can skip or reorder steps to address their specific applications, users and business needs.
Phase 1: Central Adaptive Authentication
The first step on your passwordless journey is to centralize single sign-on (SSO) and multi-factor authentication (MFA) in order to centralize and standardize authentication for all of your applications. This will provide a consistent user experience and give you a convenient control plane for determining which applications your users can access. This phase comes in two subsequent flavors of use cases.
Extended Session
The first and most basic use case is “extended session”. Users login with a username and password at predetermined time intervals as determined by an administrator—for example, once per day during the first week, once per week during the second week and then once per month, as long as they demonstrate normal usage and behavioral patterns. During extended sessions, users are only required to authenticate with a username plus MFA, thus offering a passwordless experience and only have to use full credentials sporadically.
This use case is similar to what users experience when loading their personal or work email accounts or websites such as Google or Amazon. This authentication scenario offers faster and more seamless experiences through fewer password prompts. After all, you are more likely to use a service if you don’t constantly have to enter credentials.
Policy-Based Authentication With Risk Signals
Also known as risk-based authentication, this scenario is policy-based and introduces risk signals to facilitate more flexible adaptive authentication to combat modern threats. With remote work growing, organizations face new challenges related to monitoring and securing their attack surface as users connect to the network from anywhere and on anything. Risk signals provide an effective way to move some of the authentication process into the background and make it invisible for the user.
Risk signals are a foundational piece of the passwordless puzzle. They are evaluated as customers and employees interact with an organization’s online channels to enable more intelligent authentication decisions. As a result, users are only prompted for MFA when there is elevated risk or during a high-value transaction. Multiple risk predictors can be used to establish baselines of normal user behavior and detect anomalies, thereby helping organizations make more intelligent risk decisions:
- User behavior analytics: Use machine learning to distinguish behavioral patterns of humans versus bots and illegitimate users.
- Device profiling & reputation: A method of acquiring device characteristics to determine any association with prior fraudulent activity.
- Anonymous network detection: Bad actors will commonly use VPNs, Tor and proxies to mask their actual IP addresses.
- IP reputation: Prevent users who emanate from malicious domains from accessing applications and services.
- Impossible travel: Prevent logins from locations the device could not have traveled to since its most recent login.
Risk-based authentication can be applied to both workforce and customer use cases. From a user experience perspective, if you have ever attempted to log into your mobile banking application while traveling abroad and had to perform a step-up authentication factor such as an OTP or a push notification, this was likely due to a risk score having been triggered. Risk-based authentication provides greater assurance that a user is who they say they are without introducing unnecessary friction.
Phase 2: Phase Out Passwords
Once you have those basic building blocks in place, you can begin to focus on replacing passwords with more robust and convenient authentication factors. The scenarios below require users to register with a password once initially. They can log into applications and services without passwords from then on. This phase has a wide range of use cases.
Username + MFA
The first step in this stage is to implement username plus MFA. A user fills out a username form without entering a password and is then prompted with an additional authentication factor from one of their known, trusted and pre-enrolled devices that the authentication authority has seen before. This second factor can be an application-based OTP, biometric scan or push notification, any of which will enhance both security and reduce friction by eliminating passwords from the authentication flow.
Email Magic Link
Another way to reduce password use is through email magic links. Users are prompted with a username form and then presented with a message that they have received an email with a link to the resource they want to access. Once the user clicks the link in their inbox, this completes the authentication flow and they are then granted access to the resource. This replaces “something you know” (a password) with “something you have” (an email address). As of now, it has not been widely adopted in workforce environments and is strictly a customer identity use case.
QR Codes
Also, strictly a customer use case, QR codes can save time and reduce frustration by leveraging users’ smartphone cameras to facilitate fast and frictionless authentication across devices. QR code authentication is particularly useful when authenticating to publically accessible devices (like a kiosk) or devices with limited options for controls (like a TV). Authentication via QR codes is both username-less and passwordless and can be application-based or app-less:
Application-based QR codes
Application-based QR codes enable users to leverage their mobile devices as authenticators with minimal friction. Users can access customer applications on new devices by scanning QR codes directly from within the same providers’ applications that they are already logged into on their smartphones.
Take the following example: a user is already logged into their favorite streaming service on their smartphone and wants to access the same service on their new smart TV. Two login options appear: 1) Login with two sets of credentials or 2) Login with a QR code. Rather than going through the painstakingly frustrating process of clicking their TV remote to enter their username and password, they can instead simply scan the QR code on their TV screen from within the streaming service application that they are already logged into on their phone and presto! A usernameless and passwordless transfer of the users’ login information is relayed from one device to another, instantly logging them in on their TV.
App-less QR codes
With app-less QR codes, the experience is similar but differs in that the user doesn't have to have an application installed on their phone. Rather they could navigate to the streaming service on a TV and scan a QR code on the TV screen directly from their phone camera to access the service via their phone’s browser. For this to work, the user must have already enabled passwordless authentication on both their phone and with the streaming service.
Each of these use cases replaces “something you know” (passwords) with either “something you have” (a smartphone) and/or “something you are” (biometrics) to deliver a seamless login experience that completely bypasses any usernames or passwords. They also prevent the risk of a user falling victim to password replay attacks.
Phase 3: FIDO
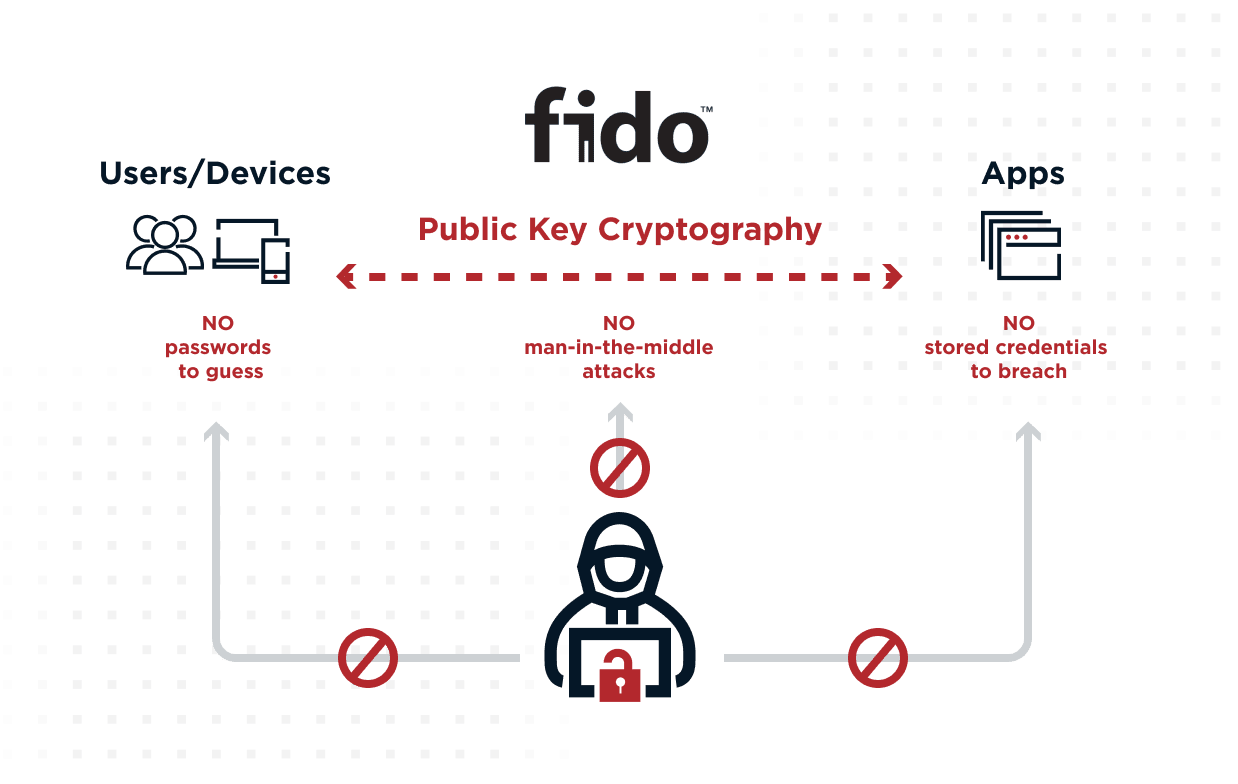
The next step is to standardize FIDO (Fast Identity Online) wherever possible. FIDO is an open standard that is designed to protect user privacy and store biometric data on users’ devices rather than on a server in the cloud. Biometric data never leaves the user’s device, enabling them to authenticate locally without their data traversing the internet. FIDO authentication requires users to register their device's authenticator application with each website they want to authenticate with. The authenticator then generates a public/private key pair for each site and returns the public key.
Understanding the technological underpinnings of how FIDO works can be complicated. To briefly summarize its value, FIDO simplifies the management of passwordless environments for IT departments by removing the need for credentials to be shared by pairing devices with specific applications and websites. It is also the greatest defense against phishing attacks. This is because phishing attacks that are designed to steal credentials by routing users to fake websites are rendered obsolete since the attackers’ bogus sites were never paired with the user’s device.
By 2025, more than 25% of multifactor authentication (MFA) transactions using a token will be based on FIDO authentication protocols, up from less than 5% today.14
FIDO Security Keys
Also referred to as cross-platform authenticators, FIDO security keys are external hardware devices—like a YubiKey—that plug into a user’s device via USB. Upon visiting a registered site, the user is prompted with a form button that wakes up any of the connected physical security keys. The user must then plug the key into their device and tap it to complete authentication.
FIDO Device (Platform)
Platform authenticators contain an embedded cryptographic key tied to a single user device. Users attempting to gain access to the device or registered applications or sites on that device are prompted with a biometric factor such as a fingerprint or facial scan to complete authentication. Common FIDO compatible platform authenticators include Windows Hello, Apple FaceID and Android. These serve a variety of use cases such as web authentication, Windows and Mac login, and more.
Phase 4: Zero Login
Also referred to as “true passwordless,” zero login reflects scenarios in which no passwords exist. Zero login combines device enrollment with the passive collection of other contextual authentication signals to optimize both security and user experiences via minimal logins.
During initial registration, the user is verified without needing a password or username, for example, by taking a selfie and providing additional identity-supporting documentation, along with the traditional device pairing process. Then, future logins are done via the user’s trusted device with a passwordless medium like a QR code or a biometric scan to authenticate regularly.
Zero login also relies on risk signals to optimize security and convenience. Most of a user’s authentication is done in the background, and only when a risk score alarm fires do they have to perform a step-up authentication. Also, in the event of a user having lost their device and requiring an account recovery, a selfie could be used to expedite the recovery process.
An Example of Zero Login
A user can have a certificate for a private key like a digital wallet on their phone and also have bluetooth on. The user biometrically unlocks their phone with a face scan. Then, by leveraging bluetooth—as the user approaches a device that they would normally have to authenticate on to access, such as a laptop—it will automatically unlock. Under this scenario, when a user is within proximity of a resource that they have permission to use, they will be granted instant access.
To summarize the above example, a biometric scan of the user’s face unlocks the user’s phone, which in turn, unlocks the FIDO security key that is physically close to or embedded in a resource the user needs to access. This resource could be a laptop or—hypothetically—even a door to a building. This example reflects true “zero login”. After initial registration, users never have to login at all. Instead, the user’s phone leverages bluetooth to project their identity wherever they go. As a result, whenever a user is in physical proximity of the secured devices in question, the bluetooth from their phone recognizes the presence of their known and trusted device and immediately grants them access.
Zero login is by far the most mature passwordless scenario. As such, few if any organizations have implemented it.