The Future of Digital Identity

Co-authored by Federico Carbone, Principal Solutions Architect, and Vinny Sagar, Sr. Solutions Architect, Ping Identity
As quickly as digital security improves, bad actors adapt and find new ways to hack into systems and misuse personal information. How do we ensure the safety and security of online activity and transactions while improving the user experience? To answer this question, our European identity experts discussed their expectations for the future of digital identity.
Vinny Sagar and Federico Carbone, regional solutions architects in the UK and Italy, respectively, along with several other thought leaders, explored many facets of digital experiences, personal identity and fraud protection. Where are we from market and user perspectives; what problems exist; what organizations and regions are pushing technology forward; what challenges must be overcome; and what does the future hold?
“Today, digital identity is a multi-faceted security concern that needs to be managed, secured and utilised properly. Personal, company and device identity require digital identity and secure management. The potential holes and touch points that could be misused are vast. Digital identity is absolutely key to any connected person or device.” —Neil Cattermull
Digital Experiences
Improving digital experiences has long been an important goal for businesses, but it remains high on the executive priority list even today. One of the more recent trends shaping the conversation is passwordless authentication.
Sagar said, “Passwordless isn’t new to the user experience. Some businesses have been using passwordless for a long time, especially in banking. That’s now trickling down to consumer technology. It’s only been in the last five to ten years, with FIDO and the mobile phone revolution, where we have technologies far less complicated and easier to set up compared to traditional PKI infrastructure. Consumers are already comfortable with mobile phones, which provide a strong security platform to drive a seamless user journey with no passwords or much friction.”
This opens myriad opportunities to improve the customer experience, facilitate online sales and increase app usage. And in the workplace, it also helps to cut down on help desk tickets to reset passwords and the resulting costs and drain on productivity.
There is both opportunity and risk here to ensure new technologies and approaches are accessible and easily used by anyone, no matter their age, digital literacy or disability.
“Individuals with disabilities could benefit from seamless digital identity experiences when using digital services, making payments or verifying identities. In this case, digital identity can help to establish trust between businesses and consumers to open revenue opportunities.” — Antonio Santos
Carbone agreed that the work of the FIDO Alliance, which is developing open, standardized authentication protocols aimed at eliminating passwords, is key to widespread adoption, but admits that it can be a slow process. “It takes time for companies to invest in a new standard. They have to wait until it’s finalized, then start adoption. It’s been talked about for ages; but when we think about the customer experience, very few companies get it right. Most are behind when it comes to adopting FIDO and mobile phones as modern authenticators. Google gets it right. Amazon gets it right. Many do not.”
Barriers to Adoption
When working toward the best possible scenario, we must examine what slows us getting there. There are many factors to overcome on the way to passwordless—cultural variables, resistance to change, fear, inadequate technology and standards, lack of knowledge and money, just to name a few.
While standard metrics like time, headcount and cost are easily quantified and tracked, human factors like comfort, loyalty, fear and resistance to change can be more challenging to overcome.
“Personally, for southern Europe,” Carbone said, “there’s a cultural aspect. People can be hesitant about new technology. Smartphones and FIDO2-compliant devices are a very secure platform, but it’s a concept people struggle to understand, especially executive decision makers. They are a bit behind and tend to go the well-known, safest route, even when that’s not ideal from a user interface or a cost perspective.”
“The flip side of Federico’s experience is Scandinavia,” Sagar added. “They are sometimes far ahead of the curve, and even the newer standards lag behind. Some of our existing customers in the healthcare sector, for example, are looking at technologies too advanced to have a standard yet available and end up with a bespoke solution.”
Aside from trends tied to cultural acceptance, our experts pointed to specific organizations leading the way in Europe to provide state-of-the-art digital experiences. Examples can be found in banking, where passwordless authentication for employees provide secure, convenient access to systems that manage nearly €200 billion in assets. Healthcare organizations are using passwordless authentication to give staff quick, secure access to healthcare records with data from tens of thousands of patients. Investment firms go passwordless to prevent unauthorized access to systems they use to manage €640 billion in assets.
Passwordless authentication is the future, and the world is making slow but steady progress toward widespread, mainstream use of the technology.
Personal Identity
Personal identity, decentralized identity or self-sovereign identity gives individuals the control to manage and share their own identity information.
It moves us away from the current model of identity management, where individual organizations store identity information for each user. Sagar explains, “One drawback to the current approach is privacy. You have to trust multiple businesses to manage and protect your identity. Then there’s the usability and maintenance of all these different identity providers (IdPs) that you connect to.”
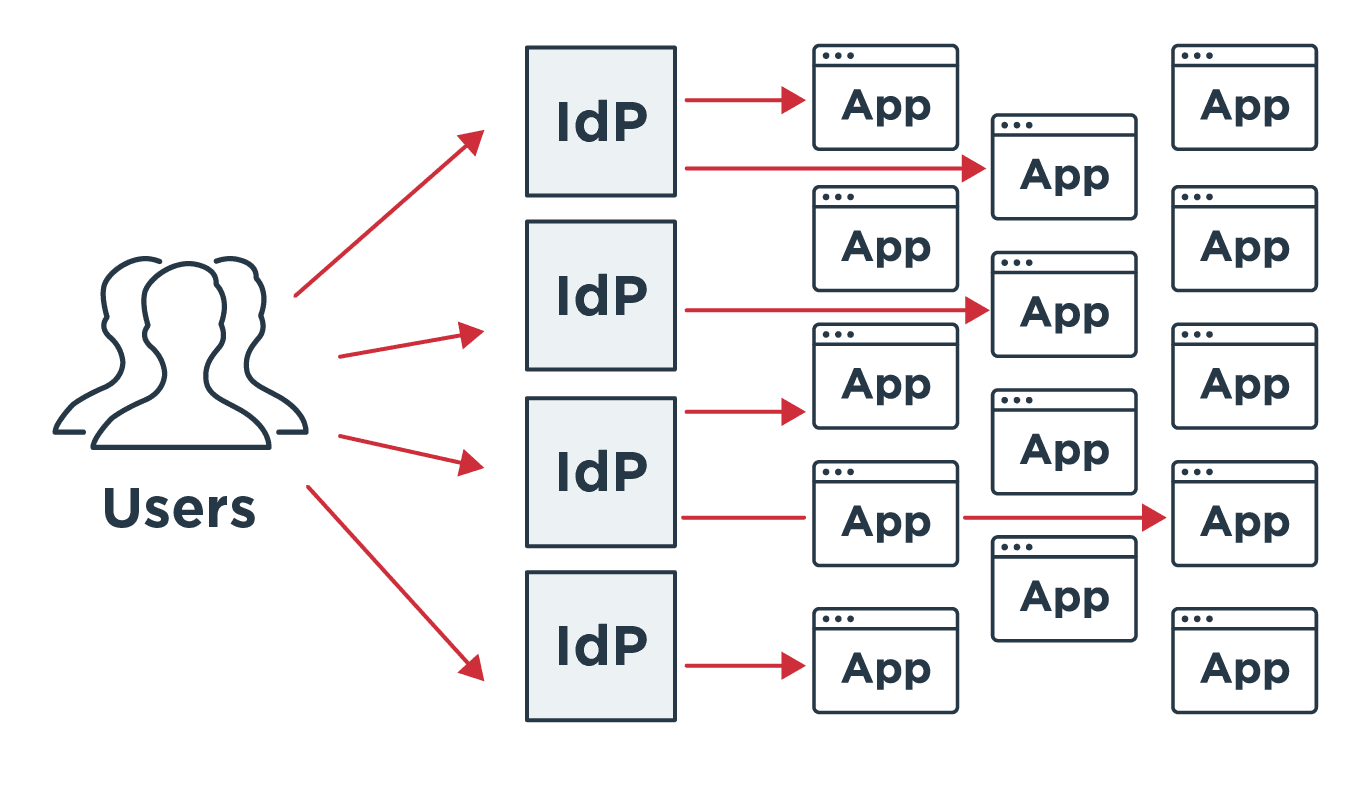
The current model puts the onus on users to remember what information they’ve shared with which organization to enter proper credentials. So as more happens online, users’ personal data is collected and stored in more places. Meanwhile, demands on organizations that collect data are growing, in the form of privacy regulations and necessary protections against data breaches and fraud.
Sagar is excited as a technologist about where personal identity is headed. “It’s a fundamental shift. We are used to organizations holding our identity data—Google, Facebook, etc.—and everyone needs your identity before they give you access. If you have 1,000 identity providers and 1,000 service providers, that’s 1000 x 1000 connections to maintain and manage. It’s not scalable. Making your phone an identity provider, essentially, is an exciting space as we move to where you are your own identity provider. You control your attributes and with who, when and where you share those.”

Sagar continued, “With your phone or something in your phone acting as a wallet storing a verifiable record of yourself it becomes much easier. The consumer is in control without having a backend connection to maintain. It doesn’t negate the problem where they lose control of how a third party uses their identity data once it’s out, even when they’ve consented. It doesn’t solve all the problems.”
A Sign of the Shift: The European Digital Identity framework
One of the biggest signs of a shift toward personal identity is the European Commission’s (EC’s) European Digital Identity (EDI) framework. It proposes an EU-wide framework enabling individuals and organizations to link national digital identities with drivers licenses or other forms of identification.
“If successful, we’ll see a push from the European community,” Carbone predicted. “Regulators are also exploring wallets and personal identity. We’ll likely see a push around personal identity and identity wallets across Europe.”
Europeans will then be able to identify themselves or provide confirmation of certain personal information to use offline or online services across the EU. An individual’s identity will reside in a digital wallet on a mobile device or laptop. It might integrate e-signatures, electronic timestamps and electronic registered delivery services. The EDI will eliminate revealing personal information not relevant to any specific task or transaction, such as opening a bank account, filing taxes, proving age, renting a car or checking into a hotel.
The biggest hurdle for adoption, said Sagar, is education. “I don’t think the average person knows how and where identity is stored. They have a login, they know their username and password. It will be a fundamental shift in thinking to see the benefits and embrace your phone or your e-wallet as your main ID source. The cultural shift will be the biggest hurdle. As Federico mentioned, there are countries where they tend to be skeptical of new tech. It will take longer in those places to adopt a new way of identifying yourself.”
Despite the challenges, individuals and organizations will reap significant benefits. The EC hopes to have agreed on a toolbox to implement the EDI framework by September 2022. The toolbox will be published in October 2022, then pilot projects will test the technical framework.
The next priority is how to monetize implementing and using this approach. It has support. Individuals have begun to embrace it. But businesses need to buy in, plan, design and implement the infrastructure and provide and promote it to users.
“Organizations need to be able to monetize this,” Carbone observed. “Organizations must always invest. Unless they can monetize this, we won’t see a big push. We see trends start and grow because there’s money to be made. If there’s no money to be made or saved, organizations won’t push for it.”
Sagar agreed. “Much of it will be covered by regulation. Some countries—Denmark, Sweden—already have some version of this. Driver's licenses are stored in your wallet. Much of the activity is in government services. It may become an EU regulation, but it must be driven by policy. It’s early and an exciting emerging trend and I hope it will catch on.”
Fraud Prevention
“Today fraud threats are prevalent and persistent, and our very notion of identity is now linked to our digital activity and behaviors. Digital identity empowers individuals to control and manage how the information associated with their own identity is used and shared while simultaneously enabling organizations to feel confident in a customer’s or client’s validated identity. When an organization can validate who a customer is from the initial point of contact, the risk of fraud is minimized without compromising customer experience.” — Ronald van Loon
Online fraud’s impact on individuals receives a lot of coverage, often because fraudulent transactions through account takeover, new account fraud and checkout fraud are fueled by hacks and data leaks from businesses with reams of customer data, including login credentials and information used for authentication. The fiscal value of any instance of fraud doesn’t need to be large to leave a user shaken, but defrauded customers are typically reimbursed.
“Fraud affects businesses more because they eat the costs, not individuals. The same with stolen credit card data. It’s usually not users that pay,” Carbone emphasized.
For businesses, the cumulative effect of fraudulent transactions can be profound. Fraud has an obvious and measurable impact, and those costs are typically passed along to consumers through higher prices on products and services procured through legitimate transactions.
Online payment fraud will cost eCommerce merchants $25 billion annually by 2024.
Online Payment Fraud: Emerging Threats, Segment Analysis & Market Forecasts 2020-2024, Juniper Research
Unethical attacks not legally classified as fraud are still detrimental to online businesses and customers. For example, checkout abuse uses automated scripts to rapidly buy out desirable inventory (collectible sneakers, concert tickets). The purchaser then resells those items for a substantial profit.
“Legally, it’s not fraud, but it costs merchants and their customers,” said Sagar. “For example, when shoe manufacturers launch a limited-edition shoe, or NVidia launches their latest graphics card, bots can create fake accounts and buy out every unit in seconds for resale. This damages companies’ brand reputation, and many struggle with it. It’s hard to detect bot accounts being created before they clear out inventory, but companies are trying to prevent it.”
The Fraud/Identity Arms Race
“The biggest challenge with fraud is that it’s constantly evolving,” said Carbone. “Attacks are becoming smarter and increasing in scale. Fraudsters are always pushing forward because there’s money to be made. It’s a constant battle, and we live in a catch-up scenario. That’s what makes it interesting from technology and business points of view. Organizations will need vendors to help prevent fraud more and more.”
As detection adapts to stop one method, fraudsters constantly modify their tools, targets and techniques. These rapid adaptations render classic fraud detection solutions ineffective.
Automated efforts—emulators and bots—allow them to accelerate and scale up hacking efforts. Bots or automated scripts rapidly perform simple, repetitive tasks. They are ideal for simple, inexpensive brute-force attacks, trying many username + password combinations in rapid succession to find which will grant access to an account.
The necessary response is for fraud detection and prevention solutions to become increasingly sophisticated. Biometric authentication can be difficult for fraudsters to circumvent. Using behavioral data to analyze activity patterns can reveal non-human users or specific actions characteristic of a human intent on committing fraud. No matter what environment or industry the solution is configured for, the key is to stop fraud without getting in the way of legitimate users executing real transactions.

Carbone said, “Fraud technology is evolving around the ability to analyze user behavior and user context using modern technology. The more you know about your customer, the more you understand their behavior, the more you can protect them in an efficient, smart way. Knowing exactly who someone is based on their behavior allows you to minimize if not nullify fraud attempts. It’s like going to the bar where the bartender knows you. There’s no way you can do anything bad and get away with it. It’s the same in this business. The risk engines, the fraud engines will need to mature to where they understand exactly what correct behavior looks like and what fraudulent behavior looks like.”
“AI for automating identity and fraud management is a trend that continues to grow.” —Neil Cattermull
Sagar added, “How users—or bots—interact with a service varies based on the type of business. Interactions with retail are very different from interactions with banking. We need to learn how normal users vs. bots react to a specific service type, and then distinguish between the two to stop fraud and not get in the customers’ way.”
Ideally, the inner workings of authentication happen out of sight and mind, improving the user experience and overall security for individuals and organizations. The intelligence of the solution correlates to the invisibility of authentication to the user. The more you know, the less you get in the way of legitimate customers. When increased risk related to identifying and authenticating a user arises, the process intrudes, requiring the user to take additional steps to prove their identity. Ideally, security measures are invisible, providing a friction-free user experience.
Digital identity can help organisations and individuals protect themselves against fraud by allowing them to authenticate themselves on various platforms without revealing too much personal information. Digital identity helps secure transactions between parties and reduces the risk of fraud.” —Cyril Coste
Conclusion
Technology and approaches to create and manage digital identity continue to evolve rapidly, driven by the need to reduce fraud, the desire to make the user experience more pleasant and the goal of reducing demand on employees to perform expensive, time-consuming authentication and support activities that can be automated and eliminated.
Organizations must educate themselves about where their platforms and digital identity meet; and their customers about how this will impact them and how they interact with online services.
"The adoption of digital identity will have three significant impacts on the market:
The first has to do with widespread access to a single and true identity. Once a person creates a digital identity and chooses a password or biometric data for security purposes, they can use it on any website without needing another account.
The second impact is the ability to make claims-based systems interoperable with one another. The adoption means that people can move their data from one system to the next without worrying about compatibility issues.
The third impact is a shift from the GAFA (or similar) being the reference to third parties, who do not have a commercial interest in exploiting customers' personal information.”
There is momentum building in the right direction to take on all the challenges we currently face in the industry, including increasing security, improving the digital experience, protecting personal identity and broadening its adoption in the marketplace to prevent fraud.
Want to explore more about these trends?