What is Federal ICAM, and How Can it Accelerate Your Digital Transformation Initiatives?
Everything you need to know about Federal ICAM
Just over a year ago, it would have been hard to imagine the transformation that the world’s workforce has gone through essentially overnight. Now, it’s clear that telework supported by the cloud is here to stay.
For organizations of all kinds, this requires the quick introduction of long-term digital transformation initiatives to properly secure your employees and sensitive assets, whether they’re located on premises or in the cloud. But these initiatives will only be successful if you reexamine the capabilities they’re built upon and enhance them wherever possible, as soon as possible.
For federal government agencies, this specifically means reviewing your Federal Identity, Credential, and Access Management (ICAM) architectures. You’ll need to identify areas where you can uplevel your existing ICAM capabilities in accordance with the latest standards and policies, including the May 12, 2021 Executive Order on Improving the Nation’s Cybersecurity which mandates the adoption of Zero Trust architecture.
So what exactly is Federal ICAM (FICAM), and how can it accelerate other critical digital transformation initiatives? Let’s find out.
What is FICAM/ICAM?
As defined by GSA and the Federal CIO Council, ICAM is “the set of tools, policies, and systems that an agency uses to enable the right individual to access the right resource, at the right time, for the right reason.” So FICAM is simply how federal government agencies implement ICAM, which are the actual technical components we will discuss.
The goal of FICAM is to enable the operations of government employees, contractors and authorized partners, who all require access to applications and assets maintained by government networks. This access must be secured so they can safely conduct mission-critical activities.
How Did Federal ICAM Originate?
The federal government has long been working to enhance, standardize and secure the identities of its employees and contractors. So not only does Federal ICAM have a lengthy history, but its underlying elements have actually been taking shape for decades.
One of these crucial elements is Homeland Security Presidential Directive 12 (HSPD-12). Issued in 2004, the directive “mandate[d] a federal standard for secure and reliable forms of identification.” Lessons learned from the tragic events of 9/11 and Hurricane Katrina
called attention to how the government’s lacking identity capabilities hampered agencies’ abilities to coordinate with each other and address incidents of terrorism.
HSPD-12 led the way for significant changes in the government’s approach to identity, including the now omnipresent PIV and CAC cards that agencies rely upon to strengthen user authentication.
A number of other policies, standards and memos guided the government’s evolution of identity in the years following HSPD-12. Eventually, they led to memorandum M-19-17: “Enabling Mission Delivery through Improved Identity, Credential, and Access Management.” Issued in 2019, the memo introduced an ICAM framework and required agencies to implement it according to the technical guidelines provided by NIST Special Publication (SP) 800-63. M-19-17 also emphasized “flexible and scalable solutions that can work across the agency and change as mission needs evolve.”
And mission needs have in fact evolved—significantly so. The shift to remote work, accelerated need for cloud transformation and urgency to implement Zero Trust security came about suddenly and unexpectedly due to the global pandemic. Agencies may have initially thought of these as short-term activities. But now, it’s clear that agencies will likely never go back to exactly how they operated pre-pandemic.
That has only become more certain as a result of President Biden's Executive Order on Improving the Nation's Cybersecurity. Not only does it mandate action related to cloud transformation and Zero Trust security, but it also signals the government's decreasing tolerance for legacy and non-compliant solutions.
These new technologies and challenges bring about new security needs. So ICAM architectures must be re-examined—now. By identifying opportunities to further modernize your infrastructure, you put yourself in the best position possible to adapt to today’s needs and set your other digital transformation initiatives up for success.
How Does ICAM Support Digital Transformation?
In addition to strengthening your overall identity security posture, refreshing existing ICAM architectures can help accelerate your modernization journey. It also lays the foundation for other digital transformation initiatives that require the use of identity and access management to enable better security, flexibility and agility. A few of these initiatives are discussed here.
Dynamic Authorization
Many organizations rely upon role-based access controls (RBACs) to authorize connections to applications. While understanding somebody’s role is certainly useful, there are a number of other variables that can affect access and permissions. This is where dynamic authorization powered by attribute-based access controls (ABACs) comes into play.
By making use of additional information (or attributes), policy decisions become much more flexible and adaptable. Users are granted access not just based on their roles, but also on the real-time context and ever-changing risk of any given situation.
Modern ABAC allows you to tap into the dynamic nature of attributes from multiple sources. To do this, it takes into consideration dynamic data like user and entity behavior analytics (UEBA), device data and other data that can and will change based upon how the user interacts with the system.
Shifting from a static authorization approach to a dynamic ABAC approach also supplements existing multi-factor authentication (MFA) capabilities. Even if an individual is authenticated, their attributes might warrant denying a specific transaction or requiring them to perform step-up authentication before the transaction can continue. For example, if a user’s location attribute changes in real time to a new location, the organization’s policy may require reassurance and proof of identity before allowing any subsequent transactions.
TIC 3.0
Trusted Internet Connections (TIC) 3.0 is a federal government initiative that focuses on shifting from a hard perimeter to either a flexible or multi-boundary perimeter. It uses policy enforcement points to enforce security actions, taking an approach of least privilege through the use of attributes.
This shift is enabled by trust zones: groups of elements that share the same level of security protections that have been deemed necessary to secure the activities associated with them based on risk categorizations.
If you don't have a single source of truth for your user data, it’s going to be very challenging to use attributes in a way that can support security decisions. By upleveling these capabilities as part of your ICAM architecture, you put yourself in a much better position to successfully implement dynamic authorization and TIC 3.0.
Central Authentication Authority
To improve federation, identity management and access management, you can harness the power of a central authentication authority. This helps break down identity silos and overcome hybrid IT challenges.
This is because a central authentication authority allows various types of credentials issued by various credential management systems into a central identity control plane. This gives you greater interoperability and greater visibility into sign-on activities, including what applications are being accessed, who is accessing them and how they are being accessed.
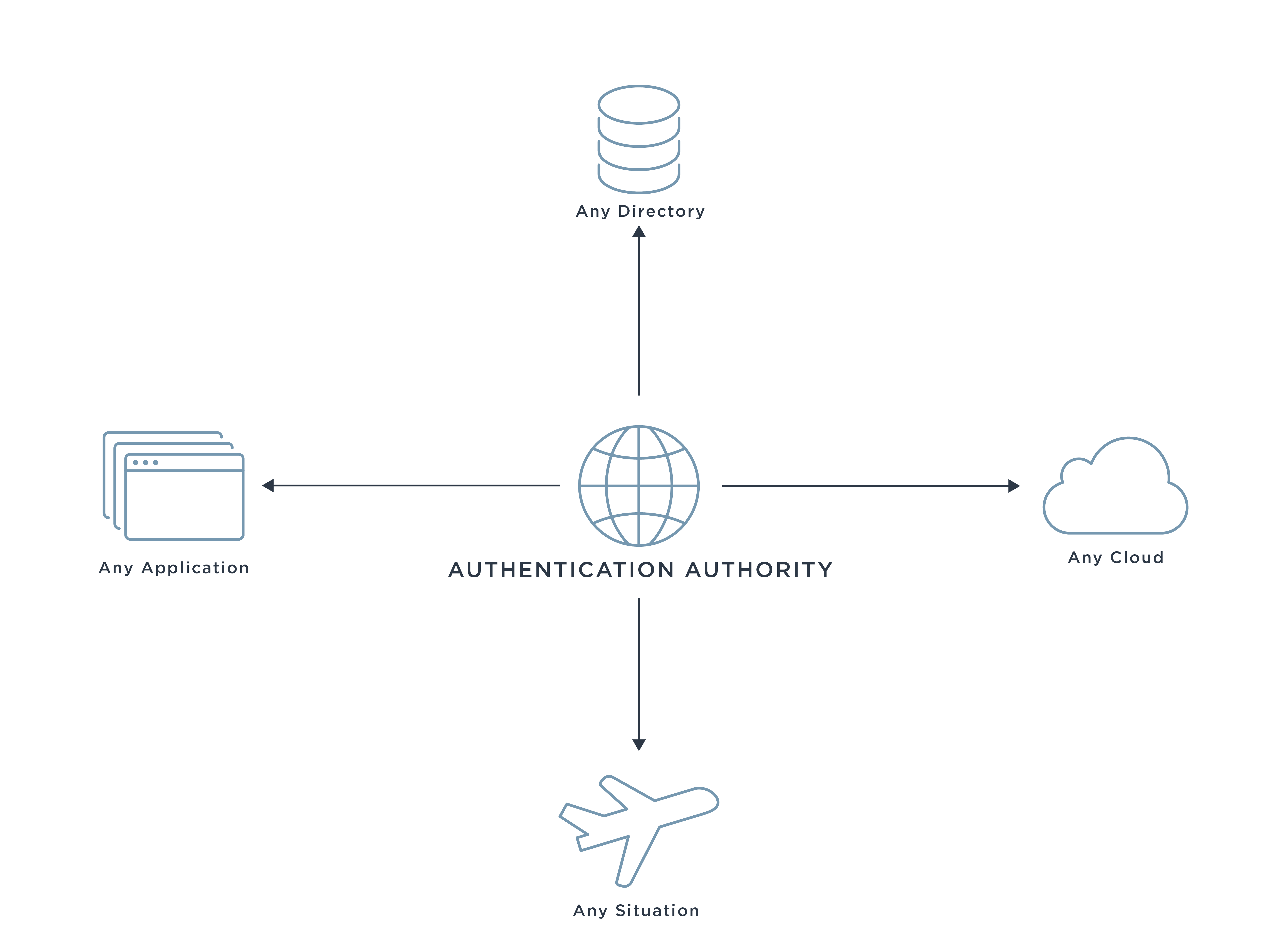
As a result, you can secure access for every user population, asset, environment and endpoint across your architecture, whether they reside on-prem or in the cloud. Furthermore, employing a central authentication authority supports Zero Trust initiatives. How so? It’s an easy way to enhance existing credentials to align with a Zero Trust architecture, since it removes the need to reissue or re-enroll existing MFA credentials.
Zero Trust
And while we’re on the topic, Zero Trust is perhaps one of the fastest-growing modernization initiatives today. It assumes the network is hostile, so instead of relying upon the network to secure an organization’s resources, it requires user identities to constantly be verified in order to grant and maintain access to resources. This approach employs multi-segmentation (which can be accomplished through TIC 3.0 architectures) and makes identity the center of your security strategy.
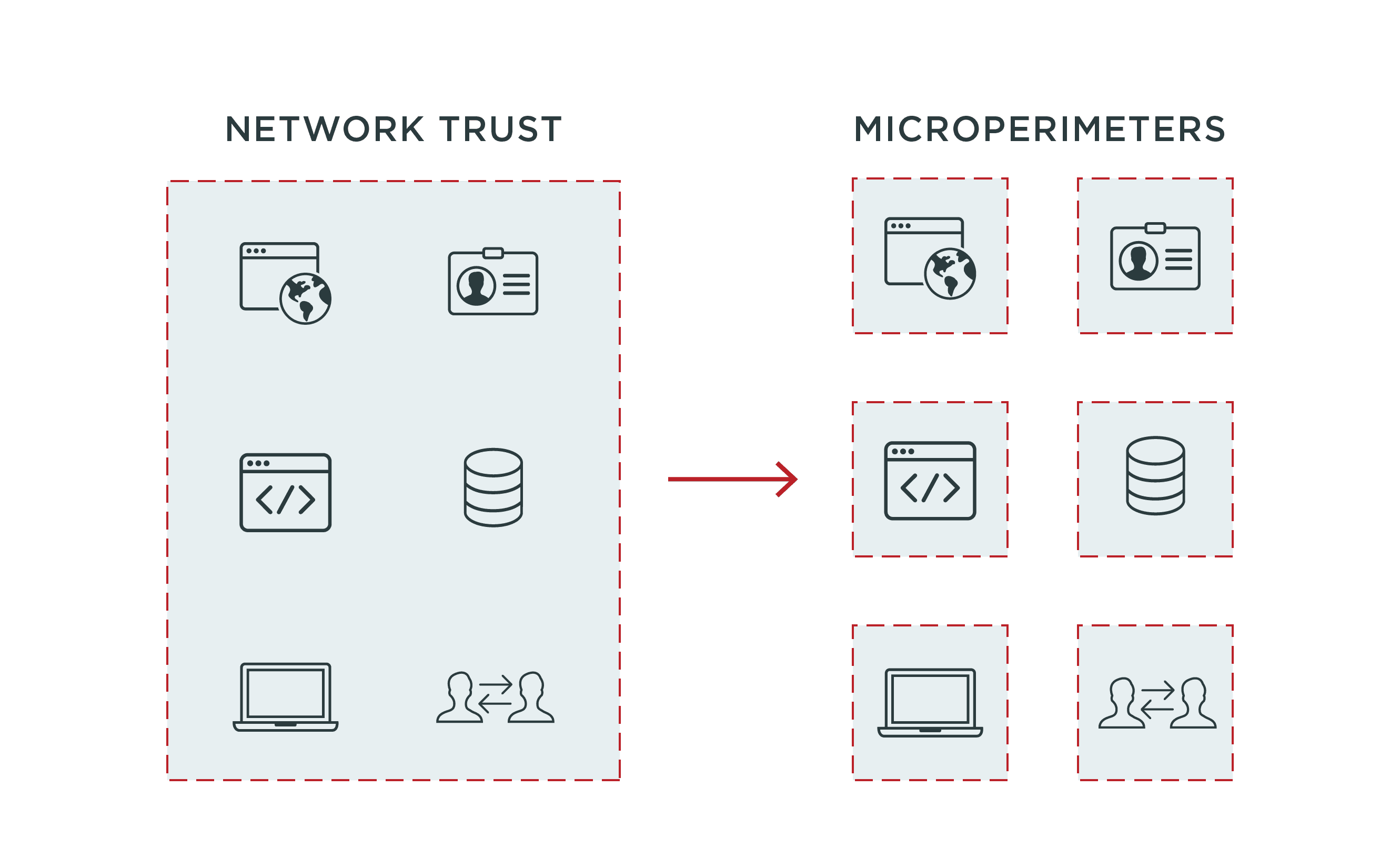
While there was already a sense of urgency around implementing a Zero Trust framework, President Biden’s Executive Order on Improving the Nation’s Cybersecurity now makes it a requirement for the federal government. With this, it’s imperative to keep identity infrastructure up-to-date.
So where does this all start? As stated by Chase Cunnigham, former Forrester analyst, it begins with “[fixing] your IAM and user side of the equation.” Without identity in place, you cannot begin to move forward with a Zero Trust architecture.
Agency Interoperability
While the federal government has made progress when it comes to agency interoperability, there are certainly still opportunities for improvement. This is especially true as the federal government works to harness its collective resources to address issues like cybersecurity, which requires different departments to proactively share critical information and report cybersecurity incidents and responses.
Rapid, agile collaboration like this requires standardization, which legacy solutions inhibit. Instead, you should look to standards-based technologies to serve as the foundation of your Zero Trust architecture. Open standard protocols for identity federation define how service providers (SPs) and identity providers (IdPs) exchange identity information, bringing speed and agility to the table for interagency operations. Furthermore, technologies built on these standards enable you to support various types of authenticators and multiple database sources, regardless of who issued them.
As a result, you can more effectively work on joint initiatives with other agencies or partners. For example, you can easily enable access to required resources in a controlled manner. This allows partner organizations to make use of your data and applications without compromising security.
What Are the Five ICAM Components?
Clearly, an elevated ICAM architecture poses a number of benefits. With identity paving the way for multiple modernization initiatives, it’s now time to dive deeper into ICAM itself.
ICAM consists of five components: federation, identity management, credential access management and governance. Within each area, Ping Identity and our partners provide key capabilities that can help enhance your existing architecture without needing to rip and replace your entire infrastructure. Let’s review each ICAM area and explore how you can address them with standards-based offerings.
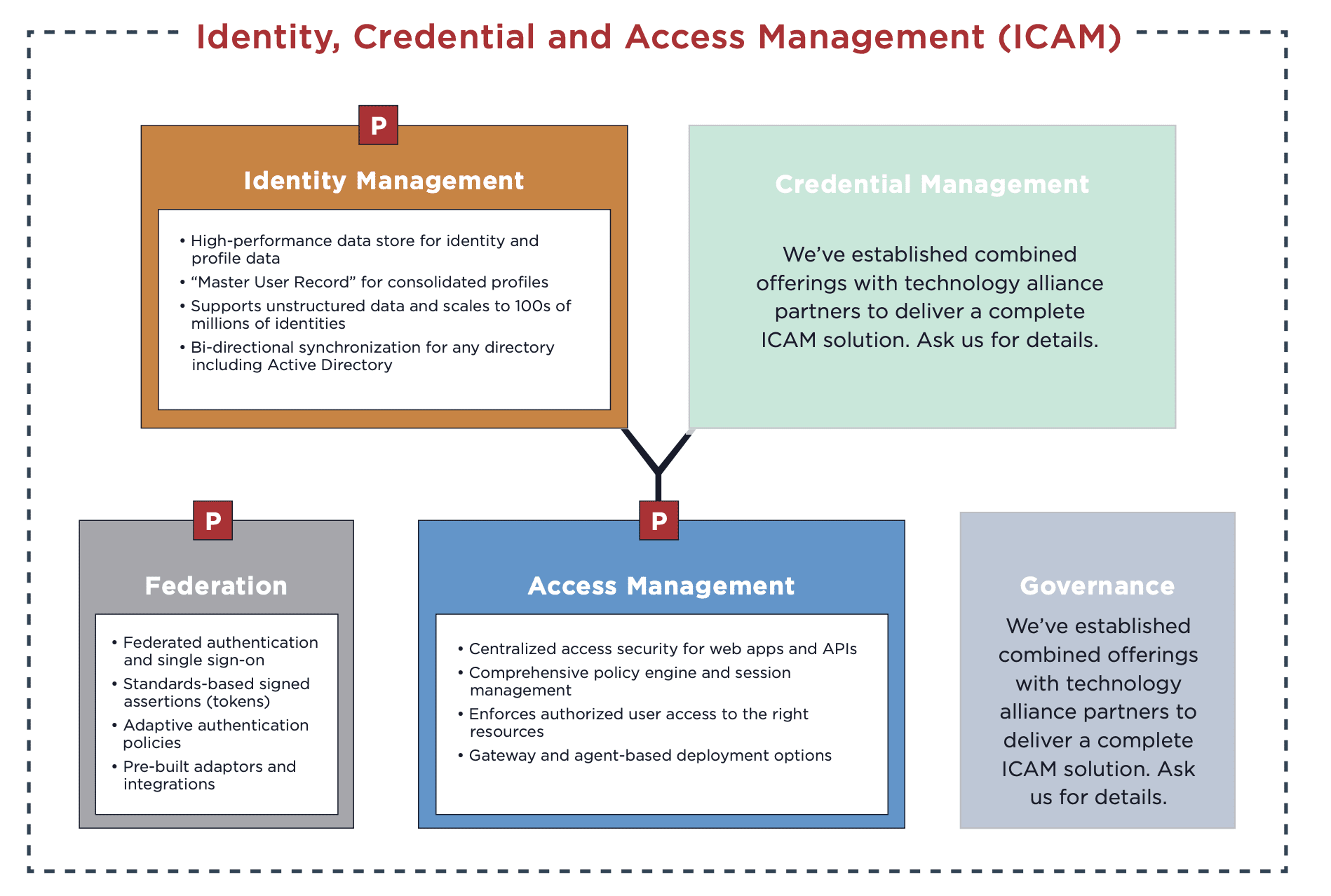
Federation
Federation consists of the “technology, policies, standards, and processes that allow an agency to accept digital identities, attributes, and credentials managed by other agencies.” To enable federated identity activities like user authentication and single sign-on (SSO), organizations need a federation server.
Customers rely on PingFederate, an enterprise-proven federation server, to accomplish these activities through key capabilities like:
Standards-based signed assertions
Adaptive authentication policies
Pre-built adaptors and integrations
PingFederate also supports existing ICAM authenticators without requiring re-enrollment.
Considerations When Choosing a Federation System Component
While every ICAM component is important, it’s especially critical to do your due diligence when it comes to federation. As stated within NIST SP 800-63: “federation is a keystone in the ability to enhance the privacy of the federal government’s constituents as they access valuable government digital services.”
This is because federation is essentially the working arm that brings everything in the digital identity guidelines together. To put it simply:
800-63A, the enrollment and identity proofing requirements, makes attributes available for use.
800-63B, the authentication and lifecycle management guidance, makes credentials available for use to validate an identity against.
800-63C, the federation and assertions guidance, is where the actual process occurs to issue the credentials from 63B to access the attributes from 63A.
So federation is what provides the results of an authentication. This step is so important that NIST is working on additional guidance, 800-63D, to ensure that agencies can align their federation with international specifications, like SAML profiles, to enhance interoperability.
And again, this isn’t about ripping and replacing your entire infrastructure. A robust federation hub will be able to bridge older authentication sources, multiple standards and modern applications to provide secure access for all users in a quick, cost-effective manner. So long as you employ modern federation capabilities, you can still leverage your existing investments.
Identity Management
Identity management is how “an agency collects, verifies, and manages attributes to establish and maintain enterprise identities for employees and contractors.” By providing a high-performance data store for identity and profile data, our identity management component is able to:
Support unstructured data and scale to hundreds of millions of identities
Perform bi-directional data synchronization for any directory, including Active Directory and Azure AD
Create and maintain a master user record for consolidated profiles
This means that all identities can be consolidated to provide a single source of truth across the enterprise for authentication to current and future corporate resources, whether on premises or in the cloud. This is enabled by our unlimited directory integrations and bi-directional syncing capabilities, which let you build a unified profile from multiple sources, so your existing investments don’t go to waste.
Considerations When Choosing an Identity Management Component
Whether you already have an identity management component in place or need to acquire a new one, it’s important to understand how it will enable the flexibility, security and performance you need for identity management.
Many multi-purpose and legacy LDAP databases are unfortunately unable to satisfy these requirements, increasing the risk of breaches, performance lags and outages. Not only can modern options decrease these risks, but they can also do so in a more cost-efficient manner, so you can focus your financial resources on other mission-critical activities.
For example, by leveraging out-of-the-box integrations with legacy and modern applications, you can spend less time customizing and onboarding new applications. Additionally, you can reduce your directory hardware footprint while simultaneously upgrading your infrastructure for better performance and scale.
Credential Management
Credential management is how “an agency issues, manages, and revokes credentials bound to enterprise identities.” With our integrations, customers can uplevel their credential management components to:
Easily integrate with PIV credential service provider solutions
Delineate between PIV and derived PIV
Support cloud authentications (e.g. Google and Microsoft) as well as currently deployed OTP solutions
Considerations When Choosing a Credential Management Component
A quality identity management provider will be able to recommend complementary technologies that are standards-based and can plug into your existing infrastructure. If you need a recommendation, drop us a line, and we’ll be happy to connect you with one of our trusted partners.
Access Management
Access management is how “an agency authenticates enterprise identities and authorizes appropriate access to protected services.” Our access security component, which supports both gateway and agent-based deployment options, elevates this ICAM capability by:
Enabling centralized access security for web apps and APIs
Offering a comprehensive policy engine and session management
Enforcing authorized user access to the right resources
Considerations When Choosing an Access Management Component
Some organizations have legacy WAM systems built to protect on-premises applications but not those hosted in the cloud. Without a solution to protect those cloud assets, agencies could experience disconnected, uncoordinated policies and sessions—an unnecessary risk.
Upleveling access management capabilities is even more critical following the President’s May 12th Executive Order (EO), which instructs the federal government to “accelerate movement to secure cloud services, including Software as a Service (SaaS), Infrastructure as a Service (IaaS), and Platform as a Service (PaaS).”
Within 60 days of the EO’s publication date, every agency needs to update their plans for how they’re going to increase their adoption of cloud technologies. When thinking this through, be sure to consider if your existing access management components provide the capabilities necessary to protect these new technologies you’ll soon onboard.
Governance
And last but not least, we have governance, which is the “set of practices and systems that guides ICAM functions, activities, and outcomes.” This includes rules to help manage access and risk, continuous analytics to determine if inappropriate access has been attempted and mitigation capabilities to resolve any confirmed issues.
We partner with a number of governance providers, as well as providers whose tools consume governance data for further security uses, such as security information and event management (SIEM) platforms. Let us know what you need, and we can make a recommendation.
Considerations When Choosing a Governance Component
Similar to other technologies mentioned above, the recent EO is accelerating the need to enhance governance capabilities. Specifically, the President has given the Secretary of Homeland Security 60 days from the date of the order’s publication to create a cloud-service governance framework. As this framework is developed and shared with the public, it will be vital to ensure your governance component provides the capabilities necessary to meet these new requirements.
Elevate ICAM with Standards-based Solutions
By elevating existing ICAM architectures, you can ensure you’re employing best practices when it comes to ensuring the right people have access to the right resources at the right time.
And while there are several components you need to address as part of your architecture, there are standards-based solutions available that can make upleveling a ICAM architecture much easier. Instead of ripping and replacing your entire environment, you can plug in only what you need to elevate your existing identity tools and capabilities.
Not only can our components support this, but they can also help you attain Federal Assurance Levels 1-3 as detailed by NIST SP 800-63, in addition to putting you on the right path to enable other modernization efforts.
To learn more about our solutions for the public sector, visit www.pingidentity.com/fedgov
