Everything You Need to Know about User and Account Provisioning
In any enterprise, employees access multiple applications and resources daily. When you also have a large number of employees working in various departments, managing user accounts and permissions across multiple systems can be a daunting task. Automated user and account provisioning ensures that your workforce can access the applications, files and other resources they need, while minimizing friction for system administrators.
What are automated provisioning and deprovisioning?
Provisioning governs rights and permissions to individual enterprise resources. Automated provisioning is the process of creating or updating user accounts across multiple applications and systems at the same time.
Automated provisioning is useful when information is added or modified in the identity source of truth (like an HR employee database) and then that change needs to be reflected throughout several other applications. For example, employees being hired, promoted or transferred are all user lifecycle events that involve automated account provisioning. Automated provisioning ensures that a user’s access rights are up to date across all systems, with minimal human effort involved.
While provisioning refers to creating user accounts, automated deprovisioning typically refers to deleting an account and revoking access to multiple applications and networks simultaneously, such as when an employee leaves or changes roles in a company. It can also refer to removing specific permissions or temporarily disabling an account, such as in the case of a trial license.
Automated deprovisioning disables, deletes or otherwise changes accounts across servers, such as Active Directory, freeing up an organization’s disk space, licenses and physical hardware for new employees. Deprovisioning prevents people from accessing corporate resources after they are no longer affiliated with the company, helping to maintain a secure and confidential environment.
What are the benefits of automated user and account provisioning?
User provisioning becomes increasingly important as an enterprise grows, bestowing the following benefits:
More efficient security administration that reduces work for administrators
Automated provisioning allows server changes to be automatically synchronized to applications within seconds, without any human involvement, streamlining the workflow between HR and IT departments.
Improved user experience
Users seamlessly gain access to everything they need without having to ask administrators or wait for approval.
Efficient utilization of resources
If just-in-time provisioning is used, an account isn’t created until the first time the user accesses it.
Automated deprovisioning ensures that appropriate accounts are deleted, disabled or changed in multiple systems and applications immediately upon a change in a user’s status, such as termination or role change.
Improved security within an organization
Provisioning allows organizations to ensure that users can only access resources that they are authorized to use, protecting your systems and applications from unauthorized use and ensuring that accounts are deactivated immediately.
Automated lifecycle management prevents permissions creep by re-evaluating user permissions when their status changes, as well as ensuring that a new user isn't just copied from an existing user, which could result in over-granted permissions.
How do automated provisioning and deprovisioning work?
Administrators can automate lifecycle management activities by taking advantage of Ping Identity's support of the System for Cross-domain Identity Management (SCIM) protocol, or by using the just-in-time (JIT) capabilities that some applications implement.
SCIM is a protocol for automating transactions of user identity data between IT systems. It is used to communicate a user change from an identity source of truth to downstream applications and systems, which triggers account create, read, update and delete (CRUD) actions to occur in those networks.
SCIM 2.0 is the current version and leverages standards such as REST and JSON to provide a regulated approach to user management. It facilitates consistent and automated communication between identity sources of truth and end-user applications and systems. For more information, see SCIM: How It Works.
In a typical configuration, a SCIM client communicates with the identity source of truth and pushes updates to downstream systems and applications.
To apply provisioning to large numbers of employees at once, users are placed into broader groups based on factors such as employee role or location. These groups apply the same permissions for all members, rather than applying permissions to a single employee at a time, which is known as delegated provisioning.
What is the difference between provisioning and authentication?
Authentication refers to a user proving that they are who they claim to be, while provisioning refers to the rights and permissions that the user possesses.
For example, in a hospital, each employee must authenticate to the systems and applications they use, often through a username and password combination. The employee has been authenticated, i.e., proven to be who they say they are.
But before that employee can access a particular system or application, they must have an account for that system or application, and this is where provisioning comes into play. While someone with the role of “nurse” in the HR database would likely have an account to access a patient management system, they would not be likely to have an account to access a payroll application.
What is SAML user provisioning?
Provisioning using SAML assertions is commonly referred to as JIT provisioning. While SAML is an authentication protocol, systems supporting JIT provisioning can use attributes provided in SAML assertions to create accounts.
With JIT provisioning, user accounts are created the first time users sign on to an application if they have necessary permissions.
To configure JIT provisioning, administrators configure single sign-on (SSO) between the identity provider (such as PingFederate or PingOne) and the service provider (the target application), and include any applicable attributes required by the service provider. These SAML attributes contain information about the user, such as their email address, role or department.
JIT provisioning allows only for the creation of users. To automate account modification and deletion, see SCIM provisioning in the following section.
What platforms are able to provision?
Automatic provisioning configurations vary, depending on an organization's architecture and the provisioning solution in place.
Ping’s user provisioning is based on the System for Cross-domain Identity Management (SCIM) standard.
With Ping, organizations have access to many out-of-the-box integrations that enable them to automatically provision and deprovision users across a wide range of platforms. In addition to SCIM support, Ping has also partnered with Aquera to integrate a number of customer relationship management and human capital management systems, such as UltiPro, Workday, Oracle HCM, ADP Workforce Now, ADP Vantage HCM and Ceridian Dayforce HCM.
What are the different types of user provisioning?
Role-based lifecycle management
Role-based lifecycle management is one of the most common forms of lifecycle management, and translates a user's group memberships from an identity source of truth into roles and permissions across multiple applications. For example, your organization stores users in a database with groups such as Corporate, Marketing and DevOps. Members of the Marketing group can access applications intended for them, but are barred from applications designated for the Corporate and DevOps groups.
Inbound provisioning for service providers
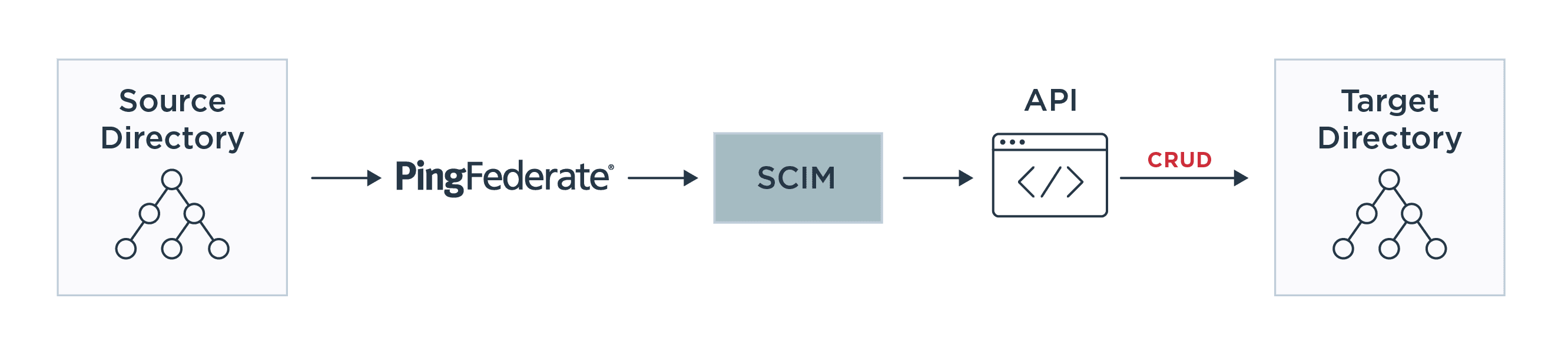
Inbound provisioning refers to when the source directory (or identity source of truth) is external to the SCIM client, such as when user accounts exist in partner systems. The source directory sends SCIM commands to the SCIM client, which in turn pushes CRUD operations to downstream systems and applications. In the following diagram, PingFederate functions as a SCIM client to receive requests for user management and then updates the target directory appropriately via CRUD operations.

Outbound provisioning for identity providers
Outbound provisioning refers to when the identity source of truth is directly linked to the SCIM server. In the following diagram, a SCIM client like PingFederate connects to the user directory and monitors it for changes. As users are added, modified or deleted, the changes are then pushed to the target directories or applications via their proprietary provisioning APIs.
What does a user provisioning process look like?
Provisioning can have many different processes, depending on the organization’s system architecture and the provisioning solution in place. The quickest and easiest way to implement user provisioning is to leverage PingOne, which streamlines provisioning across an entire enterprise. The following diagram depicts a typical outbound provisioning model using PingOne.
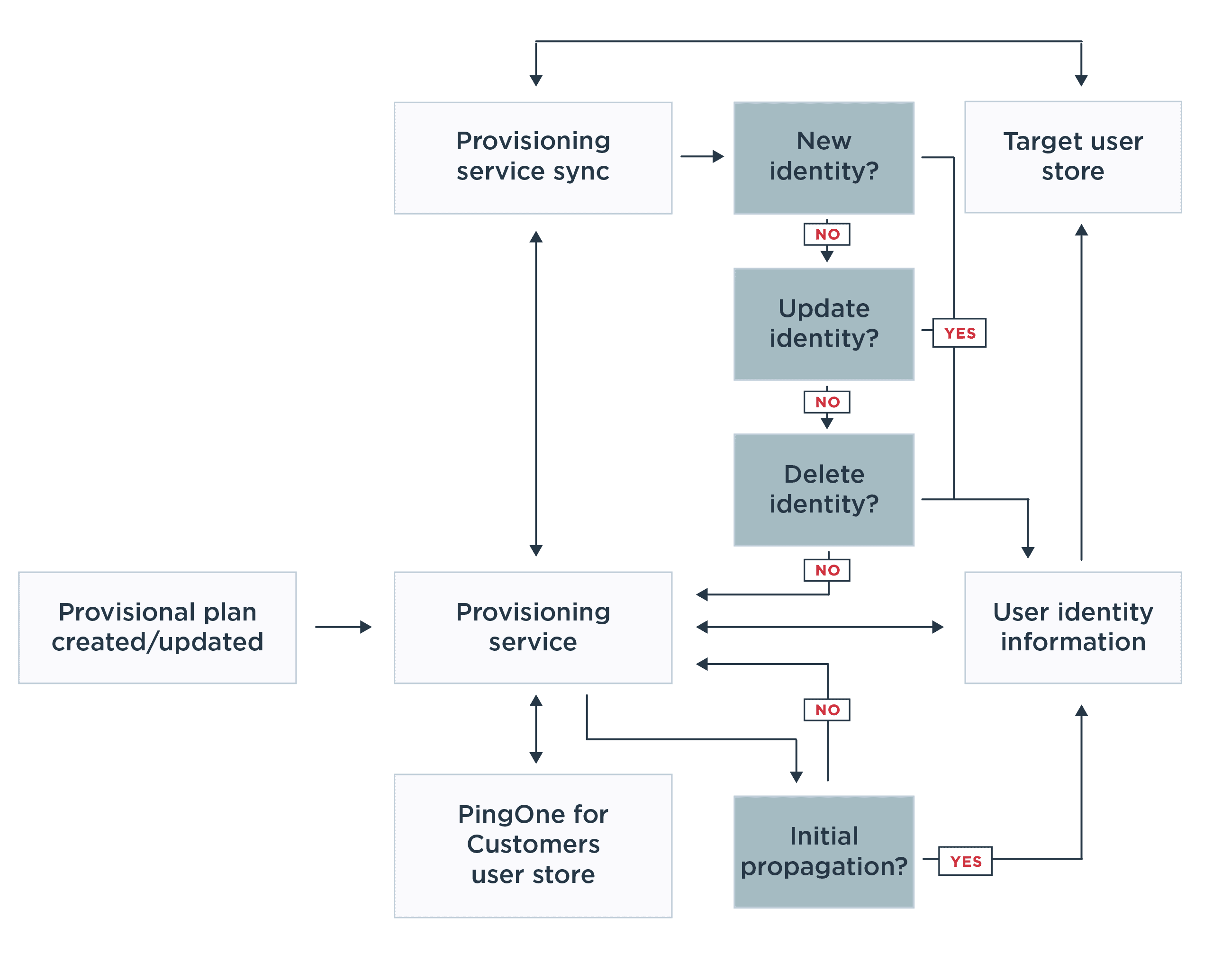
In this configuration, PingOne serves as the root user store. The PingOne provisioning service synchronizes identities from the root user directory to external user stores, such as Salesforce Communities and SCIM-based user stores.
The provisioning service continually keeps the target identity stores synchronized with the PingOne user store. Any addition, change or deletion of users or user information in the PingOne user store triggers an update to the target user stores.
To configure provisioning with PingOne, you'll first select a target identity store to which you want to provision users. Next, you'll step through the creation of a provisioning profile for the target identity store. The provisioning profile defines:
The configuration of authentication to enable a connection to the target identity store, as well as configuration settings that are specific to the target identity store
The user identity information in the PingOne identity store to select for provisioning to the target identity store
The PingOne population or populations from which to provision users to the target identity store
How long does implementation of user and account provisioning typically take?
With native SCIM provisioning, CRUD operations happen within seconds of a change in the user store. Setup typically takes less than an hour for each downstream system or application. Ping provides step-by-step documentation for customers to configure provisioning quickly and easily.
For systems that don’t natively support SCIM, Ping has a partnership with Aquera, who builds and maintains connectors that integrate seamlessly with the PingOne Cloud Platform. Aquera uses a system’s native APIs to build new connectors in one to five days on demand. This allows organizations to quickly configure provisioning for any legacy or custom application. For more information, see aquera.com.
How does user provisioning work in Active Directory?
Active Directory (AD) does not natively support federating identities to resources such as cloud applications, as it was conceived back in 1999. Regardless, many organizations continue to utilize AD as it has been the dominant identity directory since its inception. To achieve federation capabilities, many organizations add Active Directory Federation Services to their traditional AD implementation, or use Azure AD standalone or in conjunction with AD.
For organizations that currently have no federation capabilities from their on-premises AD, Ping offers solutions that can utilize on-premises AD as the identity source of truth and generate SCIM messaging based on AD changes.
The Ping Integration Directory
We are hard at work continuing to expand our user provisioning capabilities to convey enterprise benefits that include increased workforce efficiency, decreased security risks and better end user experiences. To view our complete provisioning catalog, please visit the Ping Integration Directory.
