Introduction
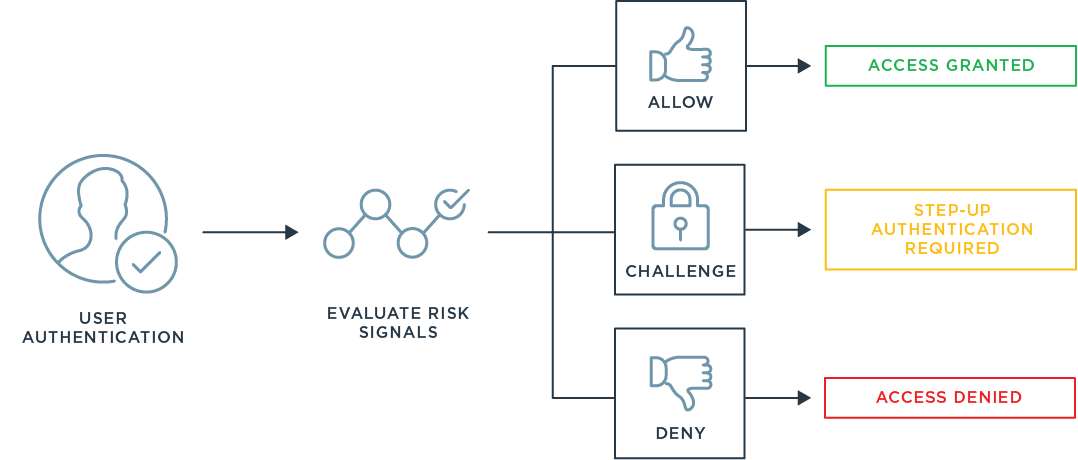
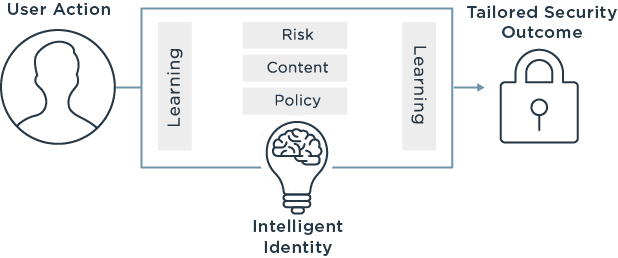
L’authentification basée sur le niveau de risque, également appelée RBA, a lieu lorsqu’un système d’authentification évalue le risque associé à chaque profil individuel essayant d’accéder au réseau (ou à une application). Il analyse la possibilité qu’un compte soit compromis ou qu’il y ait un autre type de faille de données à chaque tentative de connexion, en s’appuyant non seulement sur qui essaye de se connecter, mais aussi sur d’autres informations relatives aux circonstances de cette tentative de connexion (des précisions figurent ci-dessous).
En fin de compte, les entreprises font ceci chaque jour dans une certaine mesure, mais elles ne franchissent peut-être pas le pas supplémentaire pour se protéger. Pour les organisations qui veulent être certaines d’avoir de stricts contrôles de sécurité à chaque étape de la procédure d’accès, le moment est sans doute venu d’envisager l’adoption de l’authentification basée sur le niveau de risque, pour s’assurer que leurs clients sont bien ceux qu’ils prétendent être.
Mais, par où commencer ? Ce guide complet sur l’authentification basée sur le niveau de risque abordera :
L’authentification basée sur le niveau de risque, c’est quoi ?
La différence entre la RBA et l’authentification classique
Comment fonctionne l’authentification basée sur le niveau de risque ?
Avantages et inconvénients de l’authentification basée sur le niveau de risque
Est-ce le moment d’investir dans l’authentification basée sur le niveau de risque ?