Four Breaches Prevented by Implementing Zero Trust Principles
Another day, another data breach. If you pay attention to the news at all, you can’t help but notice the sudden splash of coronavirus-related spear phishing attacks. This could potentially launch a tidal wave of data breach headlines, considering it takes an average of 279 days to identify and contain a data breach.
But what’s the root cause of this increase? There are a number of potential reasons why we’re seeing more data breaches than ever before, and it’s not just the pandemic. The questions being raised in the media and during cybersecurity conference panels include:
Can cybersecurity tools keep up with the overnight shift to remote work at scale?
Is the adoption of advanced attack protection measures too slow?
Is it the lack of cybersecurity talent?
Are we simply outmatched by our attackers?
While each of these has legitimacy and may be adding to the challenges, I believe most modern data breaches are in fact the result of something much simpler: the available attack surface is growing exponentially, due to accelerated digital transformation.
Link Between Digital Transformation and Zero Trust
In the wake of COVID-19, you may have seen the following meme making its way around LinkedIn and Twitter. This tongue-in-cheek question highlights the degree to which the global health crisis is reshaping digital transformation agendas and changing the way we do business.

Source: Forbes.com
The rapid increase in remote workers, BYOD initiatives, partner access and cloud migration have collectively expanded the enterprise attack surface far beyond its traditional scope. Yet, while the cybersecurity principles and technologies exist to protect against this expanded surface, they aren’t being applied consistently.
Zero Trust is more than just the latest buzzword in security; it’s believed by many to be the best protection against data breaches in today’s widening threat landscape. It’s also grounded in the most basic cybersecurity practices, which define the need to ensure the protection of systems and data no matter where they are hosted, and no matter what users or devices are attempting to access them.
While the vulnerabilities related to ignoring these principles are outlined in the OWASP Top Ten, a well-regarded documentation of the most critical security risks to web applications and other enterprise resources, we still see examples of these basic principles being ignored all the time. To illustrate the point, here are four high-profile data breaches that could have been prevented if common security controls and monitoring like those provided by a Zero Trust architecture were in place.
Breach 1: Credential Stuffing Reveals Reused Passwords
Thanks to the rapid onset of 2020’s global pandemic, businesses around the world suddenly shifted to work from home. This increased the use of business collaboration tools, particularly Zoom, the popular video conferencing platform. The company reports it has surpassed 300 million daily Zoom meeting participants, up from 10 million in December 2019.
In April 2020, more than 500,000 Zoom account credentials were found for sale on the dark web, including credentials for business users at well-known organizations—even leading financial and educational institutions.
How do these credentials wind up on the dark web, you might ask?
Two things are happening:
Zoom is the victim of ongoing credential stuffing attacks. This doesn’t mean Zoom is being breached directly but that stolen credentials leaked from older data breaches are being used to systematically attack Zoom’s login. Each time a login is successful, the hackers add the valid Zoom credentials to a growing list they can sell on the dark web.
People reuse their login and password combinations. A 2018 research study of 28.8 million user accounts found 52% of users reuse passwords or repurpose them with minor modifications. Because hackers know that people often reuse the same credentials, they prey upon this well-known weakness.
How to Prevent this Vulnerability
Even if you haven’t experienced Zoom-like growth, your enterprise’s resources are still at risk of automated credential stuffing attacks. Strengthening password policies can help discourage reuse to some extent, but it’s not a completely airtight approach. The added friction forces users to find ways around security. Or even worse, it discourages them from using your service or application at all.
A better option is to address this vulnerability with Zero Trust principles. And the responsibility doesn’t rest solely on the application service provider either. Both the service provider (like a Zoom, for example) and/or enterprises using the service for their employees can implement multi-factor authentication (MFA) to achieve strong authentication of users, either as an option or a requirement. With MFA, even if there is password reuse, the exposed password is useless to a hacker. A more advanced, adaptive approach would be to establish an authentication authority and then deploy machine learning to analyze the access behavior and require secondary authentication or verification only when anomalous behavior is detected.
Breach 2: Look Ma, No Authentication!
How would you feel if your bank account information, mortgage statements, tax records, driver’s license information and wire transaction history were available to virtually anyone with a browser?
This is exactly what happened at First American Financial Corp in 2019. The title insurance and real estate closing services provider leaked upwards of 885 million customer records because of a flaw in its public cloud.
If you’ve ever bought a home, you know how much personal and sensitive financial information you’re required to provide. First American, like many similar organizations, stores all of this data in the cloud and makes it available to the parties involved in a particular real estate transaction by sharing a document link.
But First American didn’t have the appropriate security controls in place, so their customer data was literally available to the public. The document links they provided allowed unchallenged access to records—requiring no validation or verification of identity and providing no access control. Anyone with the document link could access the records using a web browser.
And it gets worse. Because each record or transaction was assigned a sequential number, all it took was modifying the number to obtain records and details about other real estate transactions.
How to Prevent this Vulnerability
The flaw in the First American example points to the core principle of a Zero Trust architecture: always identify and authenticate. This vulnerability could have easily been prevented by implementing an authentication authority.
An authentication authority provides a consistent and secure way for users to sign on to cloud and other resources. Providing fully customizable templates for registration, sign-on and self-service account management, it enables an adaptive approach to identification and authentication, which in turn can feed into an access control solution, like PingAccess, to provide centralized, dynamic and adaptive access control.
Breach 3: Authentication Doesn’t Equal Authorization
The United States Postal Service (USPS) introduced its informed visibility service in 2017. The service allowed for the retrieval of data regarding mail sent by USPS commercial customers. While this was a big step forward for digitization, the API that powered the service included a flaw that inadvertently allowed any logged-in user to view—and in some cases even modify—the account details of other users.
Since the API accepted wild card search parameters, there wasn’t even a need for hacking tools. Literally anyone could manipulate the search using a normal browser and with minimal effort as evidenced by the estimated 60 million people whose personal data was exposed.
According to the analysis done by KrebsOnSecurity, at least some data fields, like email addresses, required an extra validation step before they could be modified by an unauthorized person(s). This makes sense since large commercial customers need some assurance that their account information can’t be modified without an authorization check. But the security flaw was the omission of an access requirement to ensure the identity associated with the request had the appropriate access to read or modify the record.
The vulnerability is best described in the OWASP Top Ten Document as “A5: Broken Access Control.” It could have easily been prevented if the API in question would have done an access check to see if the person making the request had the proper authorization. This same access control check could have been used to filter wildcard search results, too.
This example also highlights another primary principle of Zero Trust: always verify the permissions and level of risk associated with an individual user at the time of the access request. We call this matching the trust established during authentication against the risk of access.
Since the USPS did require authentication to access the API in the first place, they did one better than First American. Unfortunately, equating authentication and authorization is a common mistake which often results in data breaches like these, where the impact can be outsized.
How to Prevent this Vulnerability
One way to prevent this vulnerability is to have each developer implement authorization checks on a per API basis. But many enterprises prefer to manage and implement authorization centrally.
Using the Adaptive Access Security solution from Ping, these enterprises are implementing a combination of medium- and fine-grained authorization to protect against unauthorized and/or unintentional access and potential data exposure. The solution secures APIs by enforcing an authorization check and filtering the data returned in the request. It does this in accordance with externalized data access policies composed by business users (e.g., security and compliance professionals) in a graphical interface.
Breach 4: Data Breach by Association
The human element is often the weakest link in any organization’s security chain. A simple phishing email can compromise an entire organization’s systems without the right controls in place to prevent lateral movement. When this type of breach is successful, the access gained can then be used to extend the attack beyond the initial target to its customers, too. Our next example is the story of such a compromise.
In early 2019, a large IT outsourcing firm was hacked, but their systems may not have been the ultimate target. Because they are a trusted vendor to many other companies, the attackers used their ill-gained access to launch further attacks against the company’s customers.
The initial system breach was the result of a successful phishing campaign against the company’s employees, which gave the hackers access to administrative credentials used to manage client accounts. From there, it’s believed the cybercriminals launched attacks against the company’s customers with the motive to access their customer names and systems to steal victims’ money through retail and financial gift card fraud.
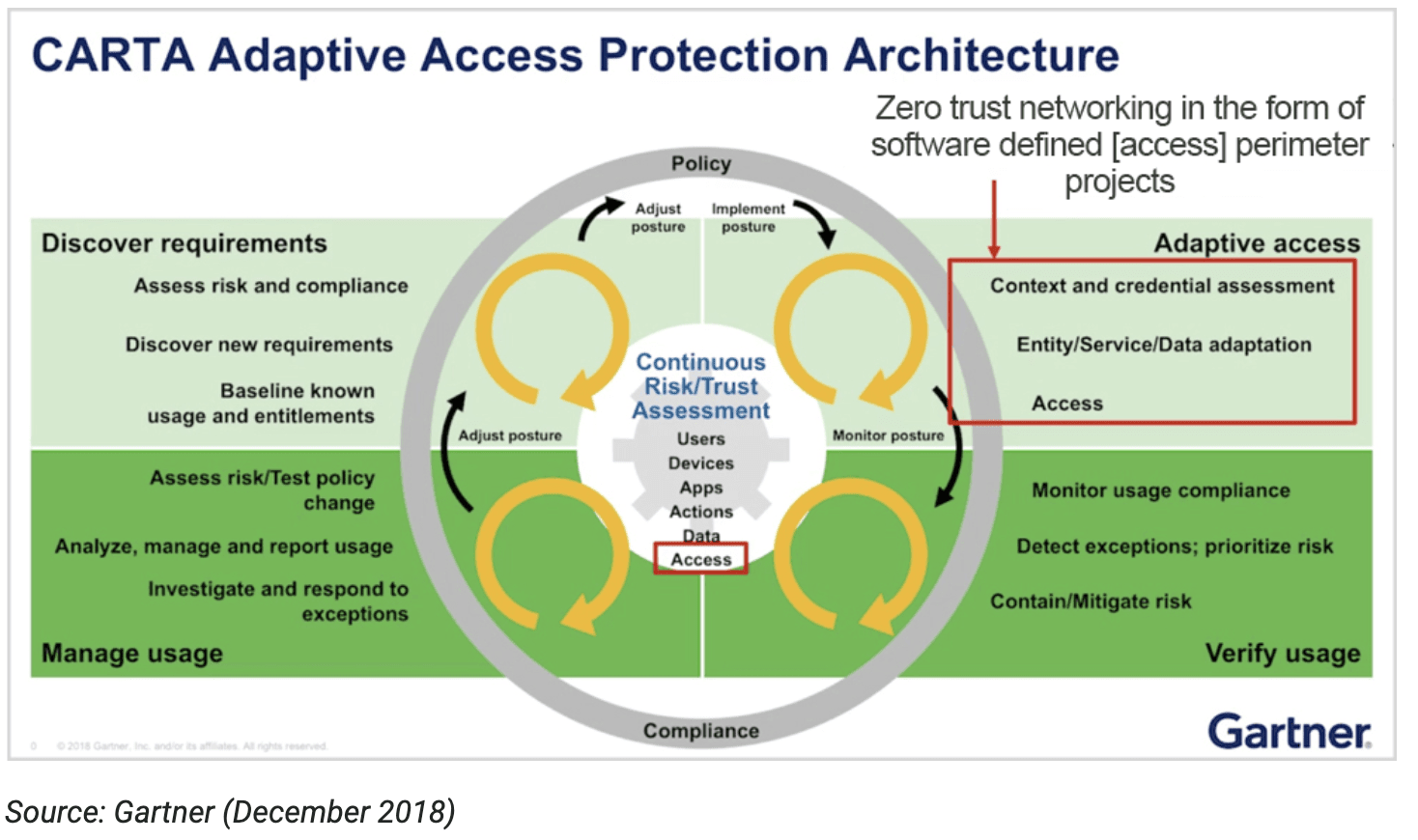
This example demonstrates the importance of yet another Zero Trust principle: assume all systems and devices are potentially compromised. This approach is advocated by Gartner’s Continuous Adaptive Risk and Trust Assessment (CARTA) framework and is a fundamental security practice crucial to any Zero Trust architecture.
How to Prevent this Vulnerability
When you assume that all systems are potentially compromised at any time, you need to take a different and increasingly intelligent approach to identity and access management (IAM).
By implementing an Adaptive Access Security solution at the web, API and data layers, you can use signals from internal and external systems to establish the circumstances for when access can be permitted, as well as to isolate abnormal behavior. With a centralized access security solution powered by a comprehensive policy engine and AI-powered API security, you’re able to identify and monitor atypical behavior.
You can then provide an additional layer of protection with adaptive MFA, which is a key capability of Workforce360, Ping’s proven workforce authentication authority solution for enterprises. This approach allows the overall system to be more resilient than an individual component as shared signals make for a more dynamic access approach.
Prevent Data Breaches with Zero Trust
Digital transformation is changing and evolving how we do business in lots of exciting ways. But it’s also expanding the attack surface for cybercriminals. The principles of Zero Trust center around the reality that organizations can no longer trust anything or anyone inside or outside of their perimeters, so they must verify everything and everyone before granting access. These concepts just make sense for today’s security challenges and can provide the protection you need against a never-ending barrage of threats.
