The Modlishka Phishing Tool and MFA: What You Need to Know
Enterprises look to Ping to help them provide secure and seamless access to the resources their customers, employees and partners require. Part of our commitment to our customers is not only to deliver intelligent identity solutions that tackle today’s identity challenges, but also to keep abreast of potential new threats in our fast-changing environment.
A year ago, the Ping CTO office predicted increased attacks on multi-factor authentication (MFA), and that prediction has come true—although we anticipate you’ll see fewer successful attacks against MFA in the coming year. But while companies have increased security to protect against such attacks, often by moving past SMS and on to one-time passcodes (OTPs) instead, attackers have also changed their approach by building tools to help them more easily phish OTP credentials.
Recently Modlishka, an even easier tool for hackers than the two-factor phishing tool ReelPhish, has gained notoriety. Modlishka, which automates the phishing of one-time passcodes, could potentially cause your users to unintentionally hand over their credentials to bad actors.
But the security industry is not standing still. Here’s what we’re seeing in the industry and what we at Ping are doing to help your organization guard against Modlishka-type phishing attacks.
How the Modlishka Tool Works
First, a quick look at how the Modlishka tool works.
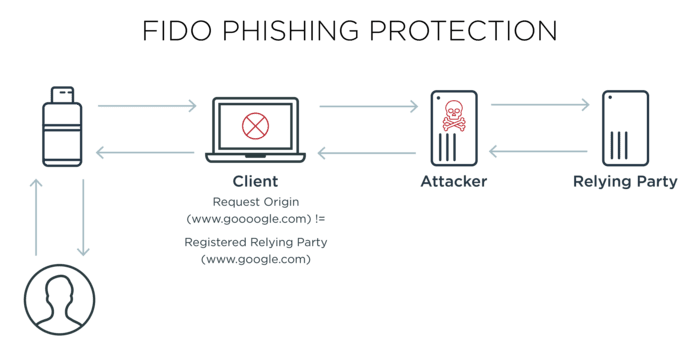
With tools such as Modlishka, the attacker sets up a phishing site at a domain that resembles a well-known domain. An example might be www.goooogle.com as a stand-in for www.google.com. A user is then convinced via email or other means to visit the site.
Then, all requests to the hacker site can be proxied in real time back to the legitimate site. All pages shown to the user can originate from the legitimate site. After the user enters both their primary and OTP credentials, the attacker can hijack the session since the legitimate site sees the hacker site as a browser.

Protecting against Modlishka
So you can see that preventing users from exposing their credentials to well-crafted phishing sites is challenging. This is why we recommend that all companies run anti-phishing training, as well as conduct phishing tests to measure employee’s awareness.
But even if your users take the bait in a phishing attack and perform insecure actions, the security industry has been doing its part to help keep them safe. FIDO can prevent the leaking of credentials even if a user is unaware they are being phished.
For a quick recap: FIDO2 is the combination of WebAuthn and CTAP1 (U2F) and CTAP2.
- WebAuthn is the protocol that browser-based applications can use to invoke authentication via a CTAP authenticator. It is supported by stable releases of Chrome, Firefox and Edge, and is available as an experimental feature in Safari technology preview release 71.
- CTAP is the protocol that WebAuthn uses to communicate with an authenticator. The authenticator can be a roaming device such as a YubiKey, or a built-in authenticator such as a fingerprint reader.
The reason that the FIDO combination is so resistant to phishing is that you must register the authenticator with each application that you want to have use it. For subsequent authentications, the domain that was registered with the authenticator is checked against the domain that the authentication request is coming from. If that domain does not match the registered domain then the authentication request will fail. This should alert users to the possibility they are being phished.
MFA, FIDO2 and PingID
Multi-factor authentication still provides dramatically enhanced security over password-only authentication, but the rise in attacks against MFA underscores the fact that we can’t stay still and that the security industry must continuously innovate.
We at Ping are constantly working to implement the latest standards to protect against ever-evolving attacks. If you’d like to try out our latest support for FIDO2 and U2F in PingID, our MFA solution, please contact your account rep to get your account enabled for FIDO2 authentication.


