The Case for MFA Everywhere for Financial Services
Money may not be the root of all evil, but it is the root cause of the majority of data breaches. Last year roughly 76% of data breaches were financially motivated, according to the Verizon 2018 Data Breach report, with bad actors trying to obtain valuable information like social security numbers, online banking credentials, financial account info and insurance details. Using these precious identity attributes, these individuals then follow a variety of paths—such as hacking into a bank account, defrauding an insurance claims/billing system, filing a false tax return, or opening a new credit line—to get to a pile of money.
To guard against unauthorized individuals acquiring sensitive information in the first place, most enterprises put multi-factor authentication (MFA) in place to secure their high-risk applications. But that may not be enough. Companies in the financial sector in particular can benefit from the use of MFA to protect access for every user to literally everything in your enterprise. By deploying MFA everywhere, you lower the risks of breach while also providing a seamless experience for your end users.
Financial Services Are Under Attack
Enterprises in the finance industry are prime targets for digital thievery:
- Banks (all types including commercial, retail, federal, central, online, mutual, investment, etc.)
- Credit unions, building societies, and savings and loans
- Wealth management and securities brokerages
- Retirement advice, planning and management firms
- Credit card and payment processors
- FinTech/InsurTech companies
- Non-bank lenders
- Foreign exchanges
- Accountants and tax preparation professionals
And the stakes are extremely high, especially in an era where groups like Lazarus focus on hacking banks. Certain industries have higher per capita data breach costs, according to the Ponemon Institute’s 2018 Cost of a Data Breach Report, and you can see that Financial Services are second only to the Health industry, at $206.
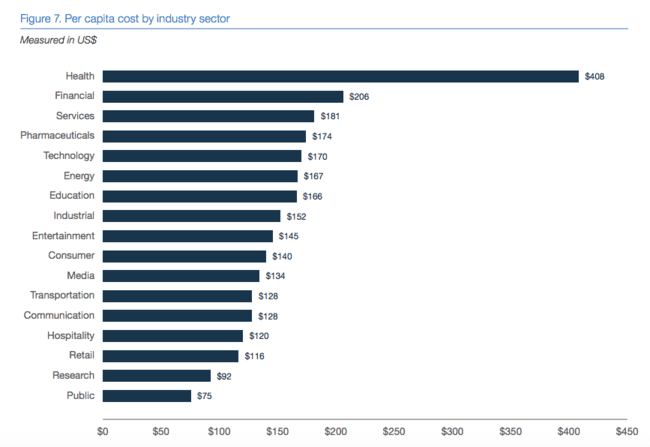
It’s even more concerning that customers have higher expectations of their data protection in highly regulated industries, as evidenced in that same study. This means the stakes also are higher for financial services companies in terms of churn resulting from a data breach.
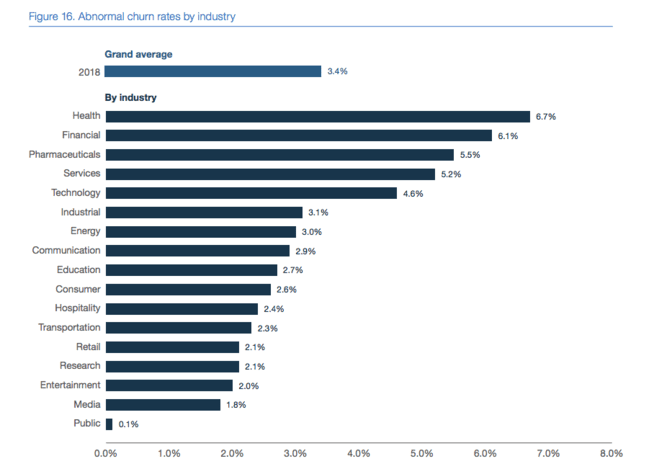
All this means that you need to be extra diligent, and your authentication ecosystem deserves close scrutiny.
Assume Your Users’ Credentials Have Already Been Compromised
When you’re securing access to financial assets or personal information, a username and password all by itself is risky. Credentials can become compromised in infinite ways and used to gain unauthorized access to a financial system. Here are just a few examples, big and small:
- A bad actor hacks their way into a regional database of bank employee credentials.
- An insurance claims adjuster poorly chooses to recycle or use a common password for their work systems and apps.
- A former brokerage employee at a partner company gets fired and still has valid credentials to some of the partner portals to your shared systems.
- A careless customer shares their online banking login with a sketchy family member.
Bottom line: It’s safer to assume that credentials have already been compromised. This is why many financial services enterprises already request additional security factors beyond a username/password. Methods for securing additional factors go by a handful of different names in the security space, including 2-step verification (2SV), two-factor authentication (2FA), out-of-band authentication (OOBA) and multi-factor authentication (MFA), but all are designed to help mitigate the risk of bad actors accessing financial systems using valid credentials.
The Solution? Aim for MFA Everywhere
I promise you this is NOT another security article debating the subtle differences and advantages among flavors of additional security factors. You likely know that at Ping Identity, we do MFA, where you use more than one channel/network (something out-of-band is ideal) and more than one factor type among:
- Things you know (e.g., credentials, PINs, knowledge-based answers, etc.). This type of factor is on the decline because it is likely that any information you know about yourself is probably something that can be found online or in an insecure database somewhere (like your passwords, prom date and what types of cars you’ve owned).
- Things you have (e.g., devices, hard tokens, etc.)
- Things you are (e.g., biometrics like fingerprints, voice and face recognition)
Instead, this article is a look at where you have MFA and why you might need to expand your protection. Today most financial services organizations are using MFA in some form; however, it’s often only deployed to a limited set of high-risk use cases. The MFA tools that do exist are disconnected for different user populations due to decentralized application ownership. Also, some legacy MFA authentication solutions are less secure because bad actors have discovered and are exploiting their weaknesses, such as intercepting SMS text messages. And any users still unlucky enough to be carrying around ancient, bulky hard tokens are probably secretly cursing you and the security team daily.
Your financial service enterprise can benefit from the use of MFA to protect access for everyone to everything. We mean all digital resources: applications, systems and networks, even low-risk ones. And we mean any and all users and their digital identities: employees, customers, members, partners, brokers, regulators, examiners, consultants and vendors.
Obstacles to Centralizing MFA Enterprise-Wide
So if MFA everywhere is so beneficial, why isn’t everyone attempting this feat?
One key reason is that the organizational complexity of global financial enterprises has been a major hurdle to MFA everywhere. Authentication flows and architecture are different for each identity type, and these variations have led to many financial services organizations having distinct teams managing internal and external identities separately. Historically, you may have had no choice other than to use identity and access management (IAM) vendors that specialize in each of the major identity types: employee, customer (or member) and external/partner (such as a broker, agent, regulatory examiner or consultant).
MFA technology needed to evolve and mature over time to be able to get to the point where a single technology solution could be proven at scale for widespread enterprise deployment.
MFA Everywhere Needs One Powerful Solution
Assuming your organization already has an assortment of MFA solutions in place for different uses, it’s important to note that putting MFA everywhere isn’t as simple as scaling each of those tools until everything is covered by MFA. If you were to do that, you would probably achieve better security—but your users would hate you for forcing them to keep track of a variety of completely separate authentication methods or tokens for different uses, and your help desk resolution complexity would rise with each additional MFA solution users could potentially be calling about.
To be fair, in this scenario you might achieve better security just by the simple fact that people can’t get access. When various MFA methods are failing, users would likely struggle to get support in a timely manner when they don’t know which application owner in your organization to turn to or your helpdesk gets backed up with requests.
Instead, begin by assessing user populations, application/resource groups and existing MFA solutions, and then determine how they can be better orchestrated so that the same user experiences a seamless MFA experience. Using a tool like PingID that is capable of integrating with both on-premises and cloud-based applications makes creating a global authentication authority that can centrally manage MFA everywhere much more feasible.
PingID puts an end to organizational silos because it is powerful and flexible enough to handle the different flows, complexity and scale for all identity types, business units and user populations that a large enterprise needs to satisfy. Many of our enterprise customers minimize business disruption by tackling a few major use cases at first with PingID, with the confidence of knowing that it is flexible enough to scale and add licenses as they go. Over time, our customers can deploy PingID to cover more and more use cases until all users are fully onboarded and the enterprise has established a global authentication authority for centrally orchestrating MFA literally everywhere.
Here at Ping we’ve also found that when it comes to MFA, financial institutions have different motivations and degrees of adoption for different user types. Let’s look at the three major user types that most financial services companies are dealing with:
MFA For Employee Use Cases
Bank employees are subject to rigorous background checks and security procedures to ensure the internal security of systems from insider threats. Enterprises also need to protect against external threats that wrongly hijack employee access to critical resources. Despite knowing that their companies are targets, even bank, fintech or insurance company employees are only human—and can sometimes find themselves the victims of phishing or other targeted attacks.
Chances are you have some form of MFA in place for employee systems, at least for the most critical resources like core banking systems and transaction/application databases. In many financial services enterprises, employees were the first use case for MFA (before customers and partners) because employees are accessing critical resources and are more “captive.” For example, a bank employees is unlikely to quit their job just because they are required to use an unreliable hard token, but customers and partners can just find another company that is easier to do business with literally a few clicks away.
MFA Isn’t Just for High-Risk Employee Resources
A common approach to MFA traditionally has been to risk categorize resources by impact and probability and then put MFA only in front of the highest risk ones. We think it’s time to now put MFA everywhere, even in front of low-risk applications, because they sometimes contain high reward data for clever crooks. It’s these small bits of harmless information that can add up and aid in a phishing attack, such as an email referencing a new rewards program, satisfaction survey or employee raffle.
Here’s one scenario: Imagine that a bad actor was able to use stolen credentials to get into the event calendar for one of your branch locations. Harmless, right? But then they saw that you had an employee blood drive coming up and captured the emails of the attendees who had signed up. They could then send an extremely specific, socially engineered email to those individual employees regarding the blood drive and somehow convince the employee to give up a 2nd factor (like a one-time passcode) to successfully complete an MFA login to a higher-risk application.
I’m not saying that this specific scenario is a problem—just trying to explain that now that modern MFA makes it easier and more cost effective to deploy MFA for any use case, it’s worth it to protect low-risk applications as a good practice. And even with MFA in place everywhere, it’s not always necessary to trigger it in every scenario, so it is helpful to implement a solution that is capable of leveraging contextual and adaptive policies to intelligently determine whether to ask a user for an additional factor.
BYOD (Bring Your Own Device) for Financial Services
One of the main reasons why it is much more feasible to put MFA in more places is that many employees have their own devices that are now smart enough to be used as an additional authentication factor. MFA solutions that have out-of-the-box integrations with mobile device management (MDM) solutions like MobileIron, AirWatch and Microsoft Intune are helping IT and security professionals ensure that employees’ personal and work device postures remain secure enough too (for example, phone isn’t jailbroken, it requires a passcode to unlock, sufficient operating system, etc.). For anyone who has had to manage bulky two-factor hardware tokens, this should be music to your ears. BYOD makes it much less likely to lose or accidentally wash/dry your only security token.
MFA for Windows Login with Offline Mode
Most financial services professionals agree that locally storing sensitive data on an employee device is a risk and should be avoided and monitored carefully, but sometimes it is necessary to temporarily store sensitive data on employee devices such as desktops and laptops. Since many of these employee devices are running on Microsoft operating systems, it’s important to use a modern MFA solution like PingID that seamlessly integrates with Windows login and has an offline MFA option to prevent productivity issues for your workforce—a critical requirement that prevents unnecessary downtime.
MFA for VPN and Privileged Applications
While many MFA solutions have integrations with major VPN solutions, another requirement to consider is the ability to integrate with any RADIUS client, as you never know when your infrastructure team will switch vendors or require more flexibility. Compared to other industries, financial services have some of the highest-risk use cases and need to implement MFA into the flow of privileged applications. The availability of a pluggable authentication module or an SSH integration through force commands to protect local and remote login to Linux and Unix systems is a key requirement for many financial services enterprises.
MFA For Customer Use Cases
When a customer or member wants to transact with your institution, whether it be a remote deposit, a loan payment, an insurance claim or anything else, the first step is authenticating who that person is and whether or not they are an authorized user for that account. The act of physically flashing a driver’s license to a teller/agent has been digitally reduced down to entering a username and password, but we’ve fast become aware that credentials alone are not strong enough to authenticate a customer.
Customer MFA is becoming table stakes across the financial sector, and even helps satisfy regulatory requirements in some parts of the world. For example, PSD2 in the EU and Open Banking in the UK both explicitly require that banks conduct strong customer authentication (SCA) before allowing a customer to use their account through a third party.
Whether motivated by regulation or just good business sense, rather than looking for a point solution, many financial institutions are evaluating MFA in the context of their overall IAM strategy. The vision for the future in an enterprise is to establish a sole digital authentication platform for all customer journeys, including those that require additional security factors. To accomplish that, you need a powerful, flexible standards-based authentication authority architecture that has the capability to enforce MFA only when required and support a broad variety of context and authentication factors.
But what if your organization has already put MFA in place for customers?
MFA probably isn’t news to you. Large enterprises in the financial services industry in particular are among the early enterprise adopters of customer MFA. As a consumer yourself, it’s likely that accessing your own online banking account was one of the first times you were asked for additional security factors during a login experience. Multiple security factors during login are becoming conventional and generally understood by consumers; they expect you as their financial institution to protect access to their money, and having an additional factor is a visible sign that you’re focused on keeping their accounts secure.
SMS and Email Are Not Secure Enough
Many financial institutions that are proactively requesting additional security factors from customers are using a one-time passcode (OTP) sent through SMS or email. And while SMS and email one-time passcodes do a good job of stopping most attacks, they aren’t foolproof—and bad actors have caught up. Codes sent through SMS or email can be intercepted; a recent data breach of 26 million text messages highlights the dangers of relying on SMS, and the fact that email passwords are often reused means this isn’t ideal either.
Secure Mobile Push Notifications
Ping Identity’s answer to the known weaknesses of OTP is the mobile push notification option of PingID. A push notification is sent directly to an app on a customer’s device, and can include custom details for transaction approvals so customers know exactly what they are approving and asks them to perform an intuitive action like a swipe or thumbprint to authorize. The app that the notification is sent to can either be:
- Your own mobile app, with MFA directly embedded using the PingID SDK
- Our PingID app, which can be configured with your branding colors and logo
Both options enable you to uphold your own look and feel and deliver a seamless, branded experience to customers.
Customer Experience with MFA Everywhere
Another way that PingID helps achieve a better customer experience is self-service mechanisms that allow a customer to manage their own profile and devices so that they can select a backup authentication method when they forget their primary one. This reduces friction for your users and prevents them from angrily tying up your customer care lines when they are struggling to place an online order, make a claim, or access their benefits. PingID also exposes APIs to be able to further develop your own self-service capabilities for users, giving your own internal developers the ability to differentiate the MFA experience.
In addition, PingID enables you to configure contextual and adaptive authentication policies to be able to intelligently step-up authentication when it is needed for higher-risk transactions and bypass it when it is not. This enables your financial institution to strike the right balance of both security and convenience, which helps build customer trust and loyalty.
MFA For Partners (or Any Third-Party Use Case)
When you want to give external users access to your financial systems, an additional security factor makes sense. According to the 2018 Global Cost of a Data Breach Report by Ponemon Institute, third-party involvement in a breach increases the cost; if a third party caused the data breach, the cost is increased by more than $13 per compromised record, for an adjusted average cost of $161, up from $148 per record.
Smart Devices Reduce Friction
Smart devices make it cheap and seamless by providing contextual and behavioral info that can be incorporated into your policies, often in a way that is invisible to users. They don’t know that you just verified that they are sitting at their desk, that they’re connected to the office wifi, that their device isn’t jailbroken, and that this is a normal time of day for them to be logging in. But thanks to the ubiquity of smart devices, you now have the ability to capture more information in the background. And if you’re using a modern MFA solution that knows what to do with all that information, you can come up with a combination of policies that adds assurance to securing access without adding friction for the user.
Enterprise-proven MFA for the Financial Sector
In conclusion, MFA is a surefire way to practically eliminate the risks of weak passwords, and financial services companies in particular can benefit from putting MFA everywhere.
