Delivering Great Digital Customer Experiences with MFA
As we’ve undergone a huge global shift to work from home (WFH), what was at first an organizational mandate has fast become the desired experience for other types of interactions. “Shop from home,” “bank from home,” “eat out from home,” “visit my doctor from home,” etc. not only significantly reduce the number of daily physical interactions, but embody convenience that appeals to an ever-growing population. These days, it seems like everyone wants a remote customer experience.
Enabling these types of digital experiences isn’t new, and many enterprises have already embraced this paradigm shift. The drive to deliver extraordinary digital experiences, though, has been accelerated with this influx of digital-only customers. The companies that can quickly adapt are the ones most likely to survive post-2020.
And although the words “transformation” and “fast” probably seldom appear in the same sentence when it comes to enterprise architecture, fortunately most enterprises already have some type of digital presence. So the key question is: What can you adjust right now that will make a meaningful near-term impact?
While you probably can’t create or even overhaul your existing digital experience, you can help ensure that customer access is both convenient and secure.
Making an Impact Quickly with Multi-factor Authentication
As digital or call center interactions increase, the opportunities for bad actors will also increase. Fraudsters have become accomplished at leveraging mechanisms such as credential stuffing, password spraying or social engineering to take over customer accounts, and they are coming after your customers. You’ll need to protect them, while at the same time balancing security with convenience.
One of the quickest, most impactful actions you can take is to implement multi-factor authentication (MFA) for your customer digital properties. With tools like push notifications from your custom mobile app, you can add additional layers of protection while requiring just the right level of authentication required for an experience that’s as smooth as possible.
Providing a secure authentication experience is critical in curtailing a bad actor’s success, because it offers assurance that your customers are who they say they are. When introducing MFA for your customers, you also have to be sure it doesn’t add too much friction.
Your organization may already be successfully leveraging MFA for the workforce, but keep in mind that there are significant differences between workforce users and your customer base. Customers can be more particular about their MFA processes, and unlike with employees, you can’t force them to adopt it. Your employees may be willing to carry around hard tokens, but very few customers (if any!) customers will. Striking a balance between convenience and security means carefully evaluating MFA implementations to best meet your enterprise needs.
Three Common MFA Scenarios
To ensure the highest level of convenience, organizations typically focus on three MFA options for supplementing a user’s password:
- One-time passcodes via SMS. The ubiquitousness of mobile phones means that most customers will be able to receive single-use passcodes via text messaging.
- Email verifications. Also nearly everywhere, email accounts are convenient delivery mechanisms for wide swaths of customers.
- Push notifications from your custom mobile app. This method allows you to turn customer devices with your app installed into trusted devices and use push notifications from your custom app for MFA.
Each option has their advantages and disadvantages. Your priority when implementing MFA, should be to give customers the most secure, convenient options for MFA.
SMS
First, let’s talk SMS. Offering your customers an additional way to authenticate is clearly better than nothing, and presenting them with a second factor that allows them to verify their identity is good defense against bad actors and can drastically reduce fraud. But we’ve been writing in this space for several years about the risks of using SMS, and if someone is really motivated, they can bypass this security check.
For instance, SIM swapping, whereby someone uses social engineering to fraudulently convince a wireless carrier to assign the phone number to a new SIM card, or SIM cloning, which duplicates the SIM card so that it can be used in a different phone, are two ways that MFA can be compromised. Motivated scammers have shown how easily MFA can be compromised through vulnerable SMS messages.
Also, while SMS is a medium nearly all customers are used to, it has inconveniences as well as insecurities. Your customers have to wait for the text to arrive, which may be affected by telenetworks and other variables out of your control. And then it often involves memorizing, or using smartphone copy and paste (which isn’t always the easiest to use!) to paste in a code. Your customer may have to close their web browser, open the SMS app, copy the text, and then reopen the web browser—an approach to MFA that’s far from convenient.

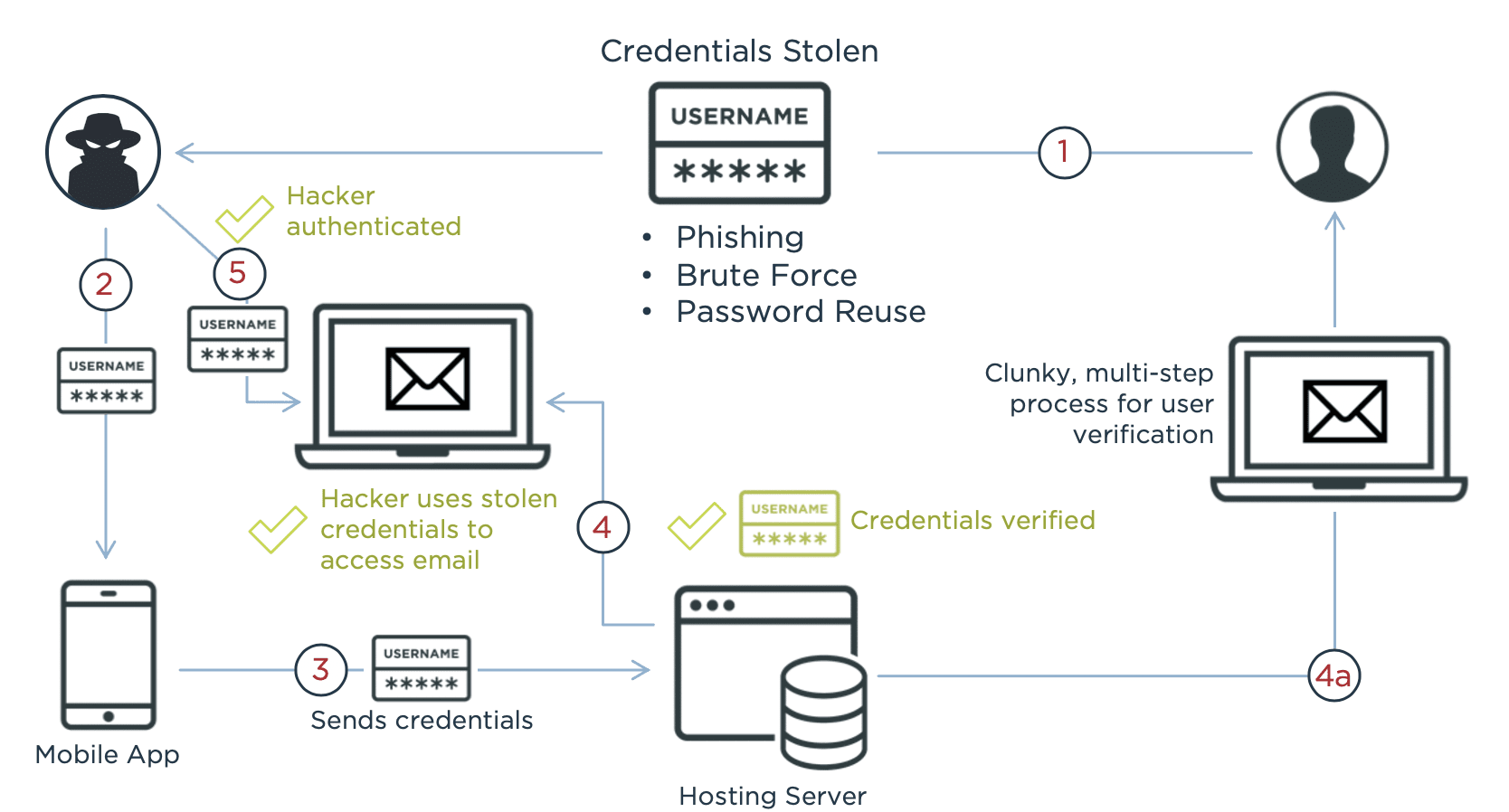
Like SMS, email is something most customers are familiar with, but it has some of the same inconveniences as SMS. Customers have to wait to receive an email, and they must open their email and then copy a code or click a link, which may force them to open a second browser tab. It’s not the end of the world, but it also isn’t the most convenient set of actions.
And that doesn’t address what’s arguably an even bigger problem: security. A recent Ping survey found a whopping 47% have let others use their password for an entertainment or e-commerce service, and nearly one quarter of that group is likely to reuse those passwords for a service that can unlock more personal information, such as email and banking.
Since so many customers share and reuse passwords, the odds are too high for comfort that a hacker who is attempting to log in to a site using a compromised or shared password will also be able to log into that customer’s email account, thereby bypassing the MFA capability.
Push Notifications to Trusted Devices
A third—and better—option is to create a “trusted device” by installing your mobile app on a customer’s phone. In this case, your app has access to unique device secrets that will only ever be tied to a single device, and these unique device identifiers are much more difficult to compromise than phone numbers or email addresses (which regularly change devices).
At its core, it’s much more secure, and it’s also more convenient. Your customers don’t have to open browser tabs or copy random numbers with a smartphone UI. Instead, a push notification is sent to their smartphone from an app they already have—your app, then they can face scan or fingerprint to verify their identity, and they’re in. That’s it.
Going Beyond MFA
Which MFA factors you choose to offer is up to you. Typically, you’ll want the most convenient and secure factor—push notifications from your own app—to be adopted by the most people. Then, for customers who don’t have your app, you can supplement their options by offering SMS or email. You can even incentivize mobile app downloads by promoting additional security for customer accounts as an added benefit.
And once you have a trusted device or MFA method, your enterprise can use it for more than just multi-factor authentication. Imagine being able to send alerts for high-value transactions, enabling CSRs to send push notifications so customers can use biometrics to verify their identities, or allowing customers to face scan and type in a new password to drastically simplify account recovery. You can even use these methods to forgo passwords entirely and enable passwordless authentication with PingZero.
The best part is that implementing MFA now is really an addition rather than a fundamental re-architecture of your existing systems. As such, it’s something you can add in the near-term to enhance both the security and convenience of digital customer experiences. Learn more about how MFA and customer IAM can deliver extraordinary digital customer experiences.

