Is Workforce Identity Holding Back Your Organization?
IT professionals in charge of workforce identity face an uphill battle. Your main goals are to support the needs of the business—mainly onboarding new applications and resources—but you must spend significant time on critical tasks like maintaining and fixing backend systems just to keep the business running. Meanwhile, as your enterprise has grown and accelerated digital transformation initiatives, you’re also tasked to match business growth.
This can be a struggle for a number of reasons, including:
Volume: The sheer number of applications and APIs can be in the thousands for the standard enterprise.
Time: Identity teams can get overwhelmed by priorities in maintaining existing systems and responding to new app requests.
Technology: You lack the right tools and capabilities to address this new world.
The technology piece is particularly concerning because relying on legacy technology that is unequipped to handle the needs of your business can lead to serious long-term negative consequences. It can delay digital transformation initiatives from taking flight or prevent other strategic projects like Zero Trust from happening. Read on to learn about the top ways that legacy systems hold back your business, and how a workforce authentication authority can help.
Legacy IAM System Issues & How to Address Them
Issue: Limited Application Scope
Applications are constantly changing. Enterprises have to deal with a wider variety of apps more than ever before, including web apps, mobile apps, single-page apps and APIs. Identity and access management (IAM) teams must have the ability to onboard any app or resource that the enterprise needs. This is typically done via open standards like OAuth, OIDC, SCIM, SAML, etc. Legacy IAM that does not support open standards is severely impacting your ability to meet the requirements of new and future resources.
Solution: Support for Open Standards & Legacy Apps
Identity teams need IAM to support their entire ecosystem of applications. You need a system with developer-friendly support for open standards so you can easily onboard newer resources like SaaS apps and APIs. At the same time, IAM should provide server and language coverage for legacy systems that typically live on-premises and/or are homegrown.
Issue: Shadow IT & Unplanned Silos
When identity teams can’t meet the requirements or the speed of the business, lines of business resort to creating or buying their own identity systems. These forms of shadow identity, or authentication silos, often start off as exceptions to a centralized IAM but grow over time. It’s a shortsighted strategy for immediate gains that can have crippling long-term effects. These silos not only become an operational headache and another facet within the environment to maintain, but also increase the organization’s security risk and the potential for breach.
Solution: Centralized Authentication Services Built for Speed & Scale
Modern enterprises need IAM that allows admins to centrally manage thousands of applications and respond quickly to new onboarding requests. Given the small nature of IAM teams, systems should come with automation and APIs that enable self-service and delegated admin capabilities. In addition, IAM teams should look for robust management consoles and policy templates, which enable them to plan ahead of time for when the business needs to scale.
Learn How Gates Corporation Removed Silos with an Authentication Authority
Issue: Disjointed Employee Experience
When IAM fails to support a broad application portfolio and/or creates silos, it diminishes the employee experience. Numerous logins are a burden to the workforce, introducing password risk and increased calls to the help desk that hamper productivity. It also limits the effectiveness of investments, as employees won’t have access to all of their resources in one place and therefore adopt new technologies more slowly. Last but not least, it will create an inconsistent experience as employees move between apps.
Solution: Simple, Single-click Access to All Apps
When IAM is centrally managed and simplifies the needs of workforce identity admins, it also leads to positive changes for all employees. By centralizing authentication, employees no longer have to use multiple login credentials to access different systems. Instead, they can log in to a single portal or dock where they have single-click access to all their apps. The result is better productivity, and, with fewer passwords in circulation, improved security.
The Migration Dilemma
If the solution seems so clear, then why don’t enterprises simply switch over? For one, workforce identity systems are mission-critical, and any downtime can impact the ability of employees to do work and lead to lost revenue. Many IAM systems are homegrown or custom-built, and the people behind their creation are long gone or no longer maintaining them.
If you’re using a vendor solution, keep in mind it was built for a different era, by vendors such as Oracle, CA Technologies and IBM, as complementary pieces to support a limited, homogenous environment. As a result, upgrading these systems must be done in lock-step with other facets of your environment, which can take years. These complicated upgrade paths are simply not worth the money nor the time, especially when even the latest releases are missing key features.
However, there is a path for enterprises to adopt leading IAM capabilities without disrupting their workforce. Migration tools and services provide a proven method to adopt new features and co-exist with legacy IAM. Using those tools and engaging with a vendor’s professional services or third-party consultants allows you to migrate according to the pace that is right for your organization.
Paving the Way with a Workforce Authentication Authority
In addition to the right migration tools and services, today’s enterprises need robust workforce IAM that can manage their entire environment and application portfolio to deliver a consistent employee experience. This means having a vendor-agnostic system that supports open standards, with platform extensibility to integrate anything and everything. This is commonly referred to as an “authentication authority,” which centralizes identity and authentication within the enterprise.
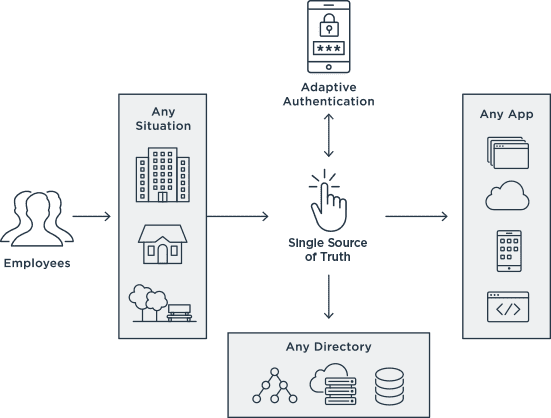
Identity professionals who adopt an authentication authority can manage the workforce at scale, delegate onboarding of new resources to the business, and safeguard smooth integrations. The system leaves no app behind and can work with both on-premises and cloud environments. By eliminating silos, you deliver a frictionless employee experience while increasing productivity and strengthening your organization’s security.
To learn more about how an authentication authority can ensure that digital interactions are secure and seamless across the enterprise, please read our workforce authentication authority whitepaper.

