Announcing Ping Identity Support for Attribute-based Access Control in AWS
In today’s digital world, the number of applications an enterprise manages continues to increase. Managing all of those applications and which employee has access to which app can be complex. That complexity only gets compounded as your enterprise grows, people switch roles within your company, or employees go elsewhere.
Today, we’re excited to announce that Ping Identity supports a new feature in AWS Identity and Access Management (IAM) that gives your administrator some relief when it comes to managing access to AWS resources.
With AWS’s IAM recent launch of session tags, now enterprises can use Ping Identity for attribute-based access control (ABAC) in AWS. ABAC helps today’s enterprise simplify fine-grained access to AWS resources by using attributes from their own corporate directories in permissions rules.
Read on to discover the value of AWS session tags, explore a real-world example, and learn how to configure PingFederate and PingOne for Enterprise to take advantage of this new AWS IAM feature.
The Value of AWS Session Tags
Enterprise customers frequently manage their workforce identities (the “who”) using an identity provider (IdP) such as PingFederate or PingOne for Enterprise by Ping Identity. They federate from Ping’s single sign-on (SSO) solutions into AWS using industry standards such as SAML and OIDC.
Now, with AWS session tags you can configure PingFederate or PingOne for Enterprise to send attributes in the AWS sessions when your users federate into AWS and use these attributes in IAM policies for controlling access to AWS resources.
Benefits of AWS Session Tags
- Rely on attributes from your own corporate directory
- Reduce the number of AWS roles and permissions policies you have to manage
- Save time by automating updates when an employee's responsibilities change
A Real-world Use Case
When an employee federates into AWS using IAM roles from a standards-compliant IdP such as PingFederate or PingOne for Enterprise, the administrator can include attributes like employee cost center, job title and email address in the AWS session. These attributes work as tags in the session and can be matched to tags on AWS resources so that the employee only has access to the resources with matching tags.
For example, when an employee with job title "systems engineer" and cost center "1234" federates into AWS, the administrator can configure PingFederate to include these attributes in the session and author policies in IAM such that the employee is granted access to all EC2 instances with matching tags. If the employee’s cost center changes, PingFederate includes the new cost center in the session and the employee automatically gets access to EC2 instances in the new cost center, without requiring any permission updates in AWS.
How to Implement Session Tags
Getting Started: 2 Things You Need To Know
- Ping supports multiple configuration options (SAML and OIDC). PingFederate and PingOne for Enterprise each support SAML and OIDC configurations. For brevity of this blog, we will highlight PingFederate using OIDC and PingOne for Enterprise using SAML. For more details and additional configuration options, we recommend you view our detailed documentation.
- PingFederate SAML
- PingFederate OIDC
- PingOne for Enterprise SAML
- PingOne for Enterprise OIDC
- AWS Session Tag Key Definitions
- PrincipalTag: Used in SAML configurations and is a prefix to an attribute in an assertion. Examples include team, project, cost center, etc.
- TransitiveTagKey: An optional attribute that customers can specify only for the attributes they want to persist from session to session, e.g., in a role chaining scenario when moving across AWS accounts. Additionally, only tags included as PrincipalTags in the assertion can be set as transitive.
Configuring PingFederate Using OIDC to Support AWS Session Tags
For OIDC connections, the PingFederate OpenID Connect Policy merely has to be expanded to include the Session Tag attribute.
Assumptions
- A PingFederate OAuth client configured for AWS Console Authentication
- A PingFederate Open ID Connect Policy
- OGLN Expressions have been enabled in PingFederate
Steps
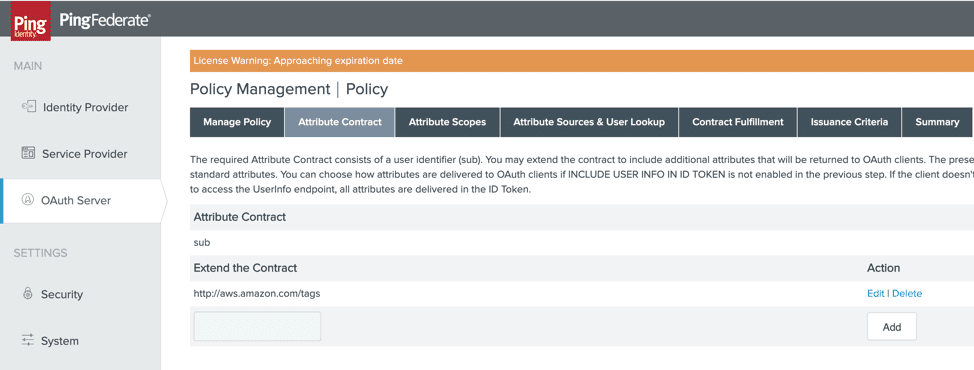
1. Under the OpenID Connect Policy, click the Attribute Contract. Create a new attribute with the name https://aws.amazon.com/tags and click Add.
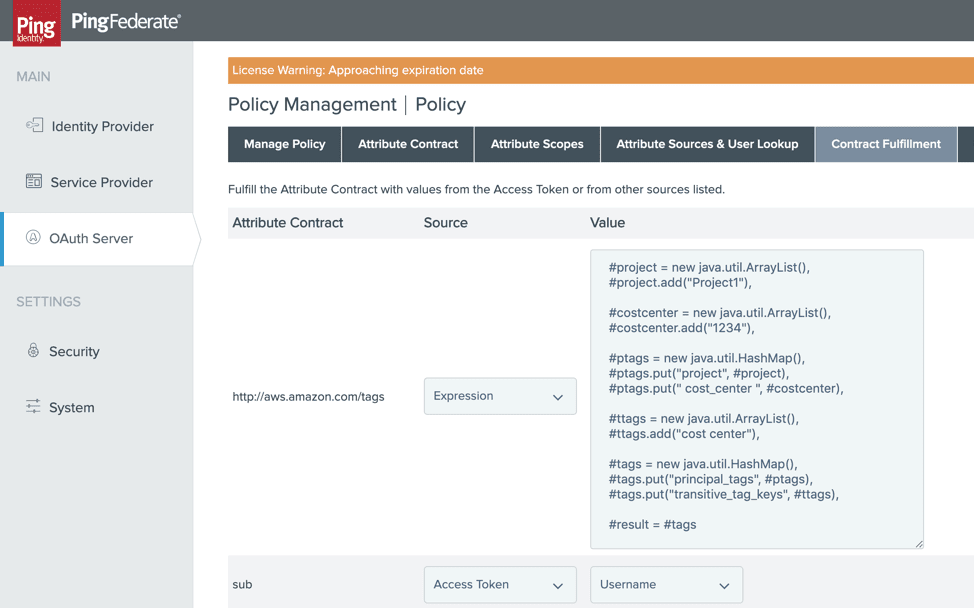
2. Navigate to Contract Fulfillment and enter the required OGNL expression for the Session Tag. Note, the OGNL expression will have to be constructed for the specific source data structure being used. The example below provides a guideline to follow:
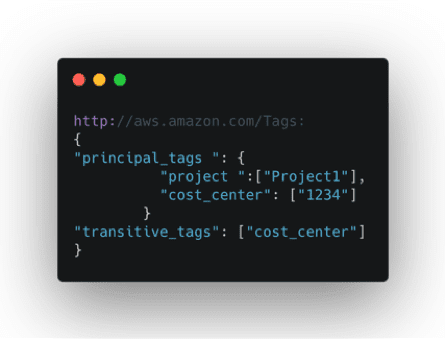
3. Click Save and ensure the AWS OAuth Client is configured to use the particular OpenID Connect Policy. The ID Token generated by PingFederate will now include the following AWS Tags value:
Configuring PingOne for Enterprise Using SAML to Support AWS Session Tags
Assumptions
- User has PingOne for Enterprise Account
- User has External Identity Provider to source AWS attributes
- Custom SAML application for AWS has been created within PingOne for Enterprise. Note: The PingOne for Enterprise AWS application template in the PingOne for Enterprise App catalog is defined for static AWS SAML attributes. Thus, a custom SAML application must be created if AWS Session Tags are to be used.
Steps
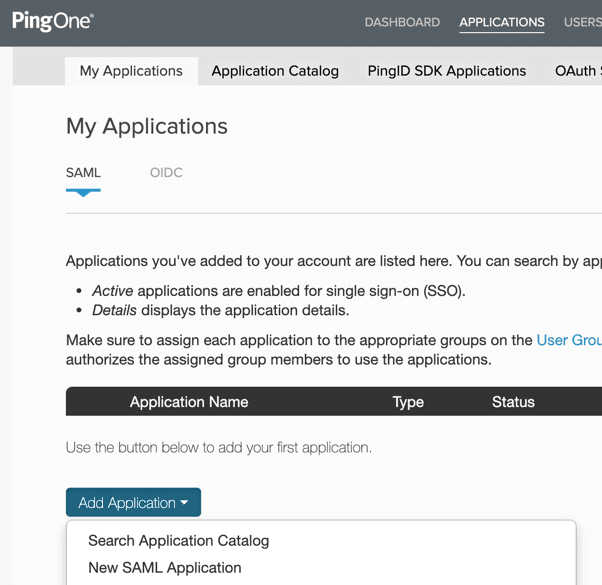
1. To create a custom SAML application, click Add Application -> New SAML Application under My Applications in PingOne.
2. Enter an application name such as AWS with Session Tags.
3. Fill in the application description, category and application icon, followed by clicking Continue to Next Step.
4. Under Application Configuration, enter the following:
ACS URL: https://signin.aws.amazon.com/saml
Entity ID: urn:amazon:webservices
5. Click Continue to Next Step.
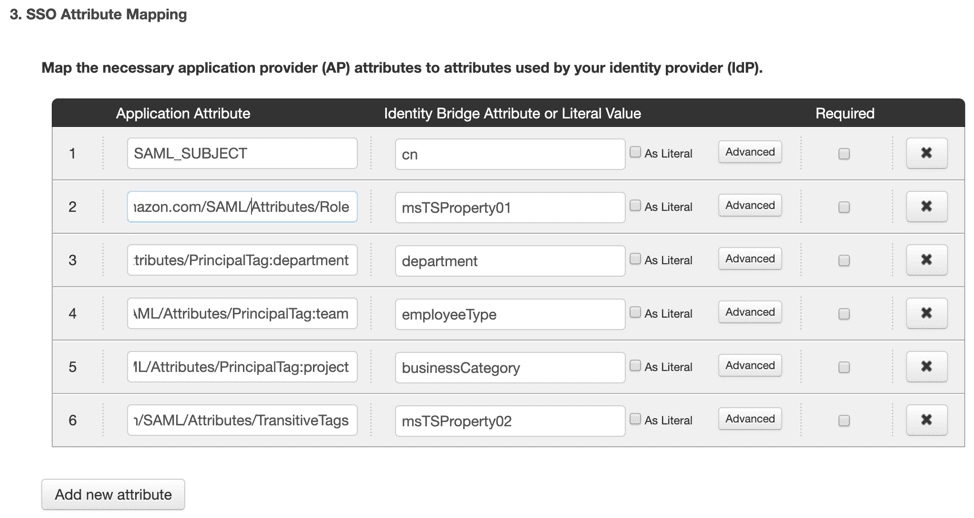
6. Under SSO Attribute Mapping, click Add New Attribute and enter the necessary attribute mapping from the External Identity Provider to PingOne that will be used in the SAML assertion creation.
Below is an example of potential PrincipalTags and TransitiveTagKeys that were sourced from a Directory:
7. Click Continue to Next Step twice and finally Finish to create the AWS Session Tag SAML application. PingOne will now create the SAML Assertion to AWS with the configured Session Tags.
Get More Information
Managing access to your AWS resources just got easier with Ping Identity. For detailed guidance on how to take advantage of AWS Session Tags in your environment and implement attribute-based access control, please see our detailed Solution Documentation.
Are You Using AWS and New to Ping?
- Check out our PingOne for Enterprise Trial today and start using AWS Session Tags
- Learn more about PingFederate and PingOne for Enterprise


