IAM Security: What It Is and What You Need to Know
The FBI's latest report on Internet crime reveals an alarming increase in phishing, ransomware and malware attacks on U.S. companies. The FBI's Internet Crime Complaint Center (IC3) received nearly 20,000 reports last year of business email compromise/email account compromise (BEC/EAC) events—hackers compromising organization email accounts using intrusion and/or social engineering techniques—that caused companies to suffer almost $2 billion in losses. And the number of total complaints the IC3 receives has skyrocketed, up from roughly 300,000 complaints in 2016 to 790,000 in 2020.
Preventing hackers from infiltrating a company and jeopardizing its integrity is a full-time job for today's IT departments. Cybercriminals have access to a limitless amount of knowledge, tools and technology via the Dark Web. The sophistication and speed with which they use to compromise organizations continues to grow rapidly, with no end in sight.
One of the most important tools for fighting cyberattacks is identity and access management, which ensures only the right people are accessing company resources. By providing authorized users with secure, seamless access to all their applications and resources from anywhere, companies unlock value while delivering better security.
What is identity and access management (IAM)?
Identity and access management is the set of solutions that help your organization attain the right level of assurance for a specific situation through the collection, analysis and management of identity attributes and information. IAM evaluates context, device and risk signals for smarter authentication and authorization decisions, optimizing security and convenience so you can simultaneously protect your organization and make interactions easy for your workforce and customers.
Although IAM typically refers to authentication and authorization, the identity and access management field as a whole may encompass a full range of identity security capabilities, such as:
Self-service for users and developers
What are some features of IAM security?
Precisely managing the digital identities of employees, partners and customers while safely controlling access to corporate resources is the core definition of IAM security. Methods for ensuring these protocols include:
Authenticating and verifying users in real time, based on factors that include the user’s device, behavior and other contexts (time of day, geographical location, etc.)
Using dynamic authorization to grant or restrict access to resources, share specific pieces of data or authorize sensitive actions
Seamlessly managing access privileges (assigning, removing and/or suspending user privileges)
Increasingly the first choice among enterprises, cloud IAM, or identity as a service (IDaaS), is a group of IAM solutions deployed in hosted environments. In addition to providing powerful security against hackers, IAM in the cloud frees up IT teams from the operational nuts and bolts of hosting and managing a solution themselves. Consequently, employees can devote more time to developing IT enhancements intended to contribute to the success of the company.
Best practices for IAM security: What makes IAM so effective?
In today’s hyper-connected world, remote access is essential. Customers and employees are mobile, and business applications are in the cloud. But the traditional, network-based security perimeter leaves sensitive digital assets vulnerable and hampers employee productivity due to lack of access. As digital enterprises open up unprecedented access to resources, it is imperative that they move to dynamic and continuous authentication and authorization to protect their apps and data.
An identity-centric approach allows security teams to focus on the secure processes and technologies that can be applied directly to corporate resources, irrespective of where they’re located. A popular strategy for modern enterprises is the Zero Trust security model, which is built on authentication and authorization controls rather than network perimeters.
IAM delivers identity-driven security through tools such as contextual multi-factor authentication (MFA), federated single sign-on (SSO), standards-based access control that dynamically adapts to users and devices, an encrypted data store of consolidated user data, and data governance with a single set of policies for streamlined compliance. Identity at the core of enterprise security gives organizations centralized, policy-driven control that enables strong protection of enterprise apps, services and APIs.
Common IAM Security Tools
The following tools are crucial to upholding IAM security. They include but are not limited to:
Single Sign-on (SSO)
Single sign-on is a type of IAM control that enables users to authenticate their identity across numerous resources via one set of credentials. The first time a user signs on, the username and password are directed to the identity provider for verification. The authentication server checks the credentials against the directory where user data is stored and initiates an SSO session on the user’s browser. When the user requests access to an application within the trusted group, instead of requesting a password, the service provider requests that the identity provider authenticates the user’s identity.
Advantages of SSO include:
Attack surface reduced from many credentials down to one
A streamlined user experience and minimized password fatigue
Lowered security risks involving partners, customers and other entities associated with the organization
Multi-factor Authentication (MFA)
When a hacker finds an account supported by only one password and one username, they know they've hit pay dirt. Cybercriminals have access to software purchased on the Dark Web that can send hundreds of thousands of passwords and usernames to this account in less than a minute. Once the account recognizes the right combination of letters, numbers and symbols, the hacker can access the account and potentially get ahold of sensitive company information.
Multi-factor authentication ensures that digital users are who they say they are by requiring that they provide at least two pieces of evidence to prove their identity. Each piece of evidence must come from a different category: something they know, something they have or something they are. If one of the factors has been compromised, the chances of another factor also being compromised are low, so requiring multiple authentication factors thereby provides a higher level of assurance about the user’s identity. These additional factors might take the form of numerical codes sent to a mobile phone, key fobs, smart cards, location checks, biometric information or other factors.
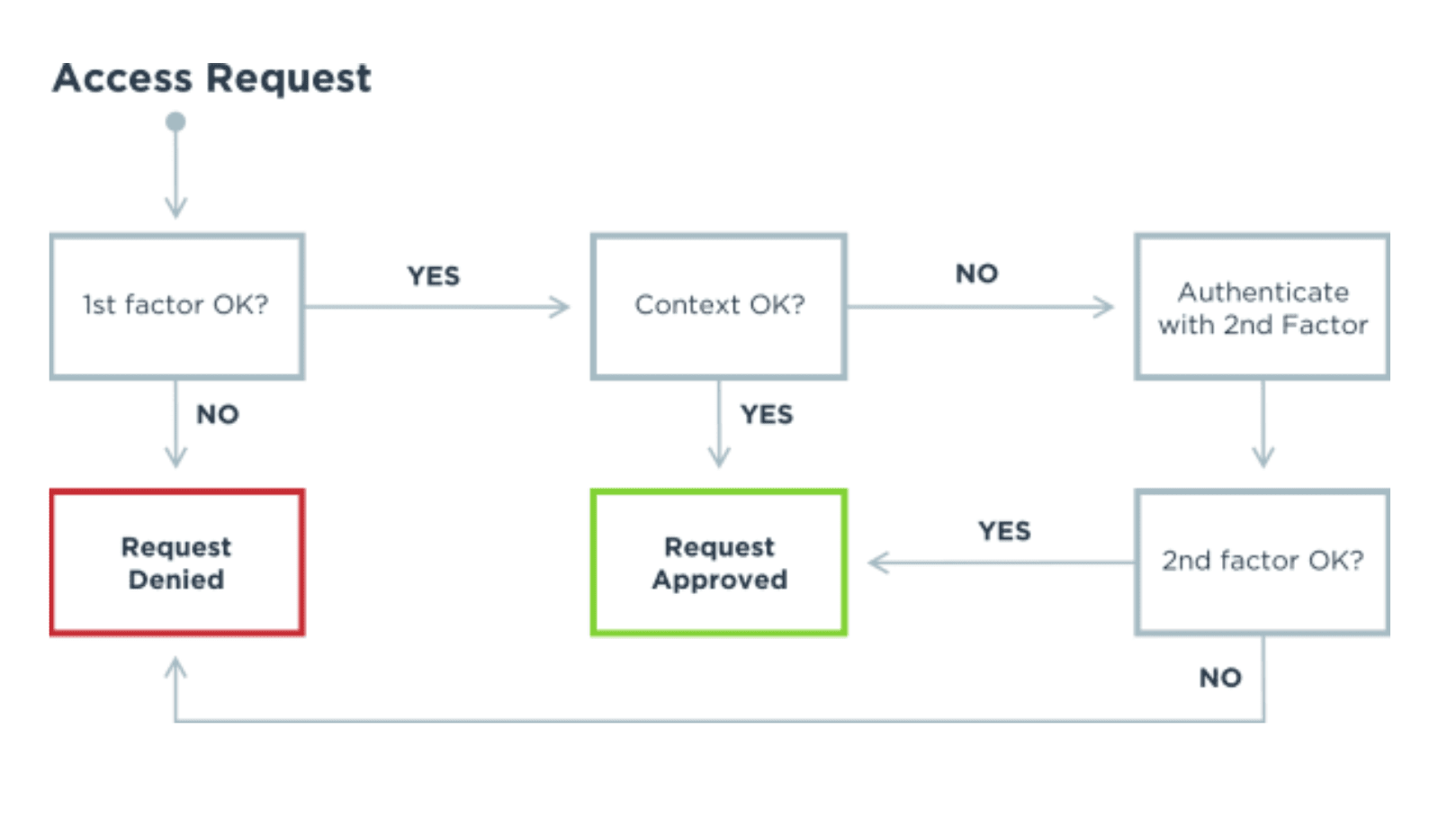
See how an access request works with MFA:
Directory
User identity data is a prime target for attackers, especially when it’s housed across decentralized data stores with inconsistent security policies. IAM security can help keep employee, partner and customer data safe via a directory that centralizes and encrypts identity data, protecting it from attacks. A solid directory solution can also help protect against insider attacks by allowing enterprises to limit admin access and by sending active and passive alerts when suspicious activity occurs.
Self-service Password Resets
One important but often overlooked feature of an IAM security solution is the ability to implement self-service password resets instead of requiring users to send requests to IT department help desks. By enabling employees to use MFA to authenticate their identity and reset passwords, not only do you reduce the number of costly password resets, but the security risk of password hijacking by hackers monitoring system "chatter" is significantly reduced.
Protecting Your Organization with
IAM Security
Here at Ping, we believe that modern identity is the thread that ties the digital world together, and is critical to achieving digital transformation. Customer demand for privacy and protection has never been greater, and the global health crisis shone a spotlight on the need to secure remote access so work can get done anywhere. This means getting IAM security right is your number one digital transformation priority today.
To learn more about why the world's largest enterprises choose IAM solutions from Ping Identity to protect their most critical assets and enable secure access for employees, customers and partners, we invite you to watch this video.
