Ultimate Guide to Multi-factor Authentication
5 - How Adaptive MFA Works
For the Administrator
Adaptive MFA works in the background to develop an active assessment of the user. This might include contextual, behavioral or correlative factors, including the geolocation, computing environment and nature of the transaction being attempted. If policy surrounding any of these factors dictates greater security, the system can step up authentication requirements to apply the correct level of security based on the associated risk.
As an administrator, you set access control policies to dictate the need for strong multi-factor authentication. Since these policies are based on risk, you’ll typically start with a data classification exercise that identifies your audit risks, as well as the data that’s most at risk should your organization be compromised (PII, PHI, credit card numbers, social security numbers, intellectual property, etc).
You will then map the users, devices, applications and APIs able to access your sensitive data and determine the level of acceptable risk in certain scenarios, identifying those that:
Don't require MFA
Require some form of MFA
Require high assurance and a specific form of MFA
Warrant a denial of user access, because MFA isn't enough to overcome the risk
Armed with this information and understanding of your risk profile, you’re able to set security policies in line with the risks associated with specific resources, behaviors and contextual factors.
Is There an Easier Way to Implement MFA?
If data classification exercises and user maps sound more complicated than you need or want to take on, not to worry. Modern MFA solutions are:
Fast to implement
Simple and convenient for users to adopt
Fit within your IT budget
- Can easily grow with your company’s changing security needs
learn more about mfa made easy
For the End User
Adaptive MFA enables users to securely and conveniently authenticate to all of their applications. They simply install an app on their phone and self-register that device. The app may be a standalone MFA app for authentication purposes only. Or you can embed MFA capabilities in your own app, which is often more convenient for customer end users. Regardless of how you implement, adaptive MFA is easy to set up and use, while providing strong authentication to all of the apps your users need to access.
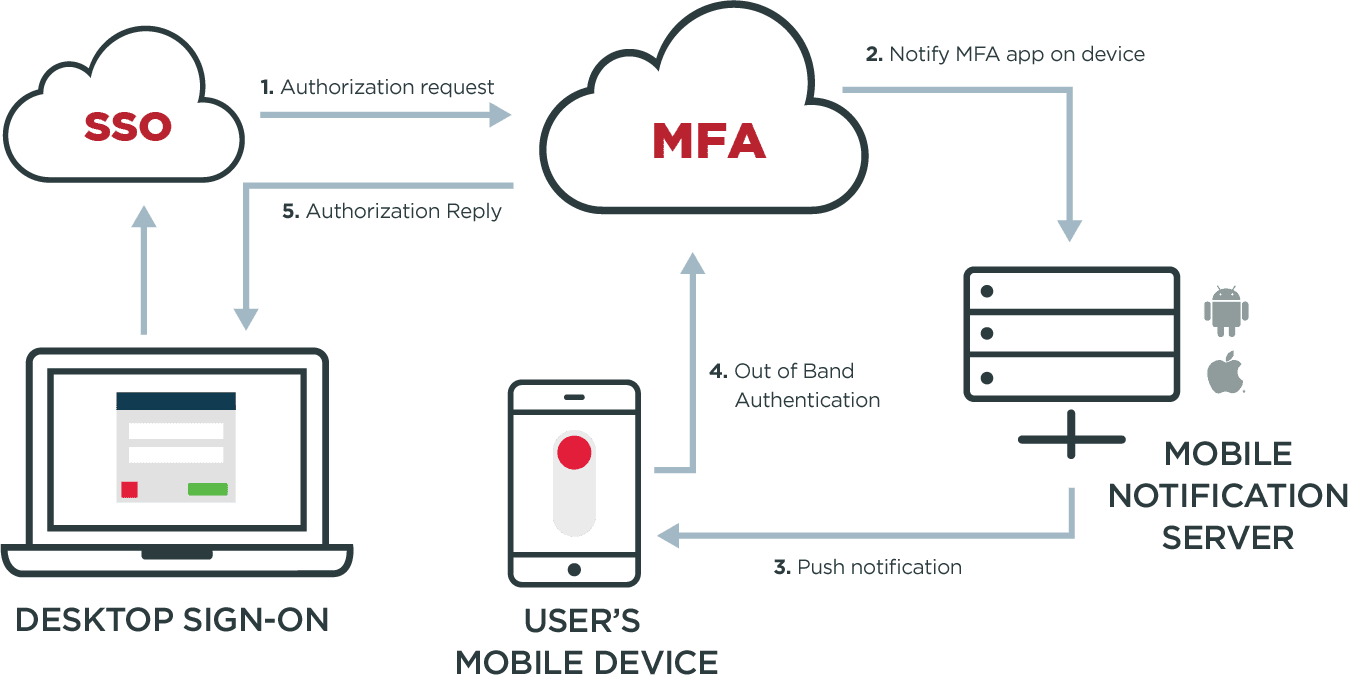
When your governance policies dictate the need for strong authentication, the MFA service sends a notification to the user’s smartphone. If the user employs iOS or Android devices, the Apple or Android notification service sends this notification. This eliminates the cost of a voice call or SMS message. Upon receiving the notification, the user swipes his or her device to sign-on and is authenticated.
Watch the video to see MFA in action.
If a user can’t get online but needs access to their device, offline modes can generate a one-time passcode (OTP). Alternatively, SMS, voice, email or a desktop application can deliver the OTP. YubiKey and other hard tokens can also be employed for sensitive environments or for users without mobile device or phone access.
Start Today
See how Ping can help you deliver secure employee and customer experiences in a rapidly evolving digital world.
Request a free demo
Thank you! Keep an eye on your inbox. We’ll be in touch soon.