Getting Started with Zero Trust? Begin with Identity
The Zero Trust party is in full swing. The security concept had been around long before COVID-19 as the way forward in managing the increasing number of resources outside of the corporate network like mobile devices, IoT, cloud computing and small instances of remote work. But while many organizations had been experimenting with Zero Trust, they still relied on the perimeter-based approach—until the global pandemic changed everything.
Almost overnight, Zero Trust went from a nice-to-have to a necessity as companies shifted entire workforces to a remote work environment. In our recent survey of 1,300 executives worldwide:
82% have already adopted some type of Zero Trust element
71% say their Zero Trust investments will increase in the next 12 months
85% believe identity security technologies are critical to mobile and/or user experience
Clearly, executives see the value, but each organization will deploy Zero Trust in different ways. Prior infrastructure investments, varying levels of cybersecurity knowledge and executive buy-in can influence how (and how quickly) a company adopts a Zero Trust architecture. So how do you determine the best approach for your enterprise to get started with Zero Trust?
Zero Trust Is a Journey, Not an End State
In security, it’s often said that anything and everything can be hacked. In other words, there is no such thing as ‘perfect’ security. Bad actors will continue to come up with creative ways to get in, and in turn, cyber defenses will also evolve.
Prior to Zero Trust, enterprises depended on network security vendors and technologies to secure the perimeter. However, Zero Trust is much more than that; it’s a concept that relies less on the safety of a network perimeter and more on identity security. The network is a key component, but so are devices, users, APIs, data, etc. And since there’s no definitive guide to Zero Trust—for example, Forrester has its Zero Trust Security Playbook and Gartner has the CARTA model, while U.S. government agencies NIST and the NSA have also provided direction—every organization must constantly evaluate their Zero Trust posture in terms of people, processes and infrastructure to meet their unique requirements.
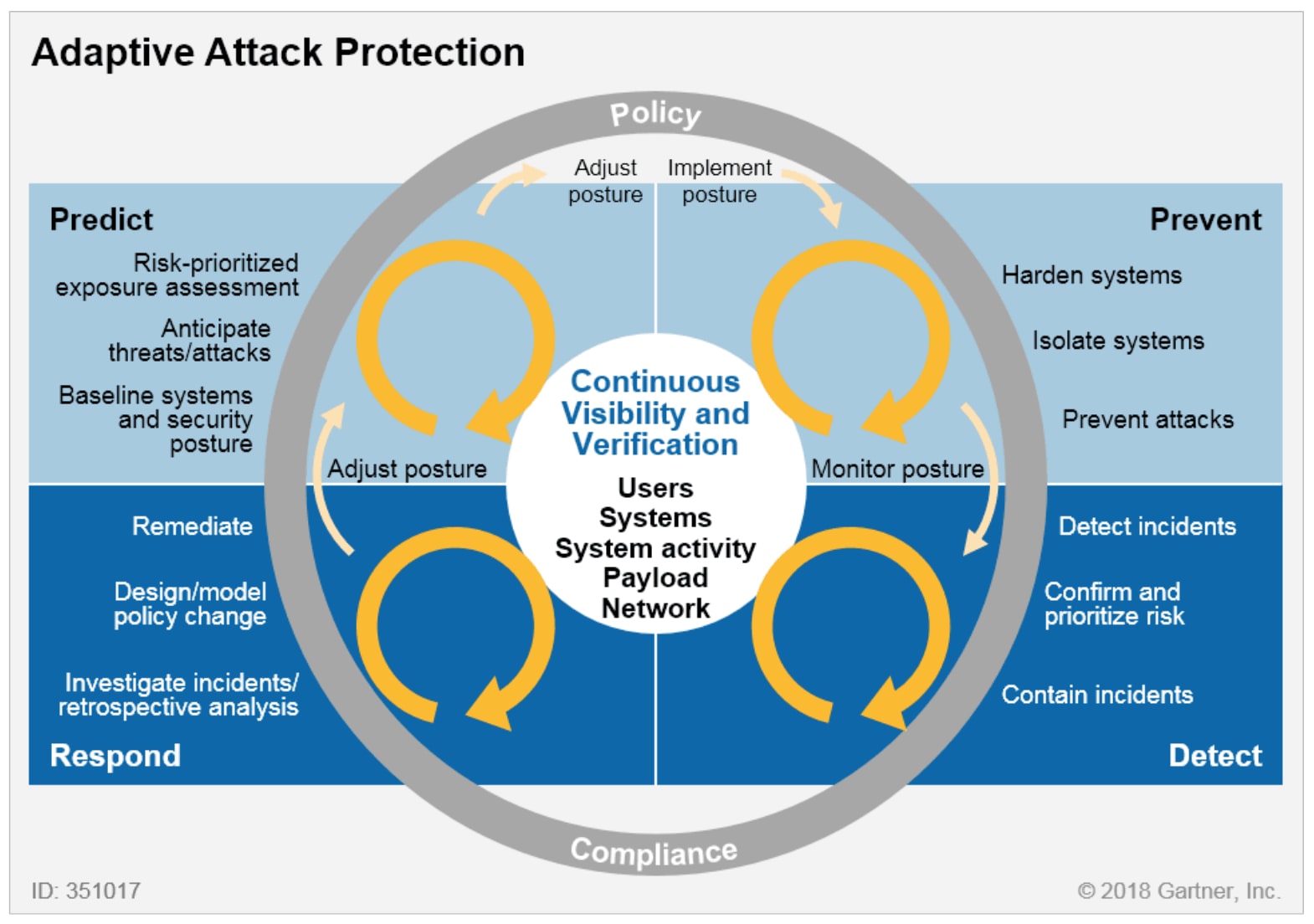
The Gartner CARTA Model
Identity: The Foundation for Zero Trust Success
The key principle of Zero Trust is “never trust, always verify,” meaning all users and devices must first be authenticated before they can gain access to sensitive resources or data. This may seem obvious in the current era but it is a departure in thinking from the security of the past, where users were trusted once they were on the corporate network. These days, where it’s critical to enforce trust beyond the network at a more granular level, such as on users, devices and other resources, identity plays an essential role.
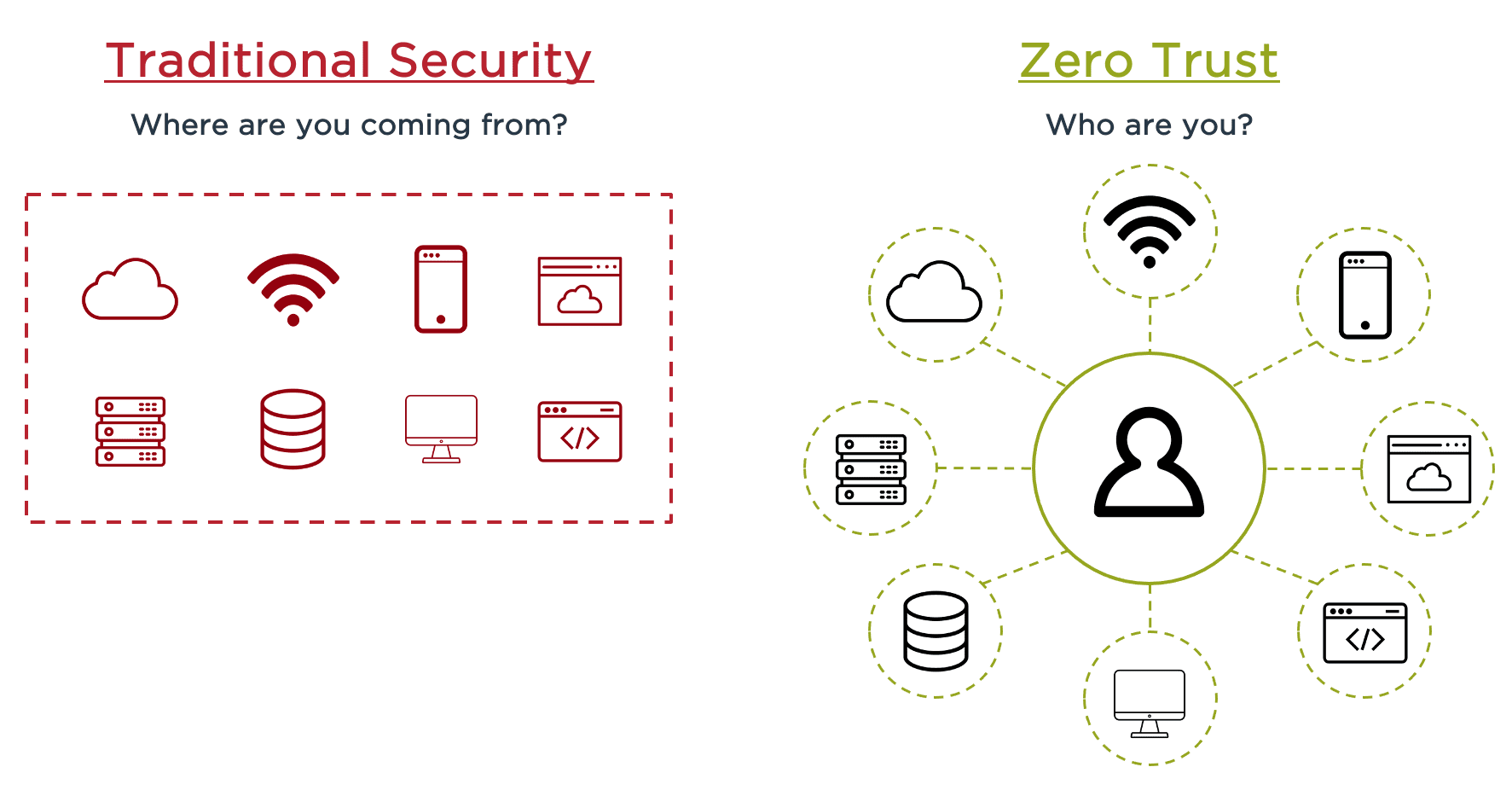
Identity should be the first step of your Zero Trust journey because it encompasses and addresses:
Centralized Management. Most enterprises have a variety of applications, including homegrown, legacy software, SaaS, mobile and more. These apps have caused silos to form over time, which can be difficult for IT to maintain. A strong identity management solution can tie it all together and enable your organization to authenticate consistently across the board.
Passwordless. Passwords continue to be the top security threat to enterprises and the main point of entry for bad actors. A strong identity platform allows you to reduce the number of passwords via capabilities like single sign-on (SSO) and multi-factor authentication (MFA). And ultimately, you can even remove passwords from the equation with advancements in passwordless login and device biometrics.
User Experience. This theme is a byproduct of the first two points but deserves its own mention because the user experience is critical to Zero Trust success, especially with the acceleration of remote work. Enterprises are wary of locking things down too much at the expense of employee productivity. Identity security done right ensures seamless access so your workforce can stay efficient.
Dynamic Risk. One of the key benefits of adopting Zero Trust is the ability to continuously monitor and assess risk versus being constrained by the static nature of perimeter-based security. Being able to identify everything and anything is the first step and the foundation for integrating risk management solutions that can leverage tools like machine learning and analytics that detect and respond to potentially harmful activity.
Silver Bullets for Zero Trust Don’t Exist
As you start on your Zero Trust journey, be wary of any vendor or solution touting itself as the single answer to your needs. A Zero Trust ecosystem has many components. It is not just about the technology, as your people and internal process matter too.
You need executive buy-in and adherence to Zero Trust principles from your IT and security teams to see a successful rollout. This is easier said than done since many security practitioners have built their careers on implementing network security tools focused on securing the perimeter. Also, processes like onboarding apps or users may cause change, leading to internal resistance.
That’s why focusing on identity security is a great place to begin your Zero Trust journey. Identity helps you manage everything at scale. Adopting an identity-centric approach also lessens business disruption by minimizing friction for employees and administrators.
Zero Trust Is a Team Sport
In your Zero Trust journey, working with a number of different vendors and solutions is inevitable. Enterprises require coverage for all their applications, including homegrown and legacy ones. They also need integration into the other aspects of the security stack, especially device management and security analytics and monitoring.
That’s why integration and orchestration capabilities should be key factors in your decision-making when considering Zero Trust investments. If your team cannot manage everything efficiently, your money will be wasted. Getting identity right will make your Zero Trust execution much more successful because identity is the fabric that ties it all together.
How Executives Are Approaching Zero Trust
Want to understand how other organizations and leaders are thinking about Zero Trust implementation? Check out our survey “Growth in Remote Work Fuels Zero Trust Investment.” And to discover how you can achieve your digital transformation goals with Zero Trust, download our white paper “Zero Trust: Thinking Outside the Perimeter.”
