Gartner Magic Quadrant and Critical Capabilities for 2020 Provide Essential Insight into Access Management
See why Ping Identity is positioned as a Leader in the 2020 Magic Quadrant for Access Management for the fourth year in a row and scored the highest for workforce and customer access management use cases in the 2020 Critical Capabilities for Access Management Report.
Right now, businesses around the world find themselves in the midst of transformative change, brought on by the pandemic-initiated explosion of work from home and digital-first customer interactions. Many are turning to identity and access management (IAM) solutions to serve as the foundation of security and user convenience for customers, employees and partners during this time of significant change.
In these times, when you are evaluating IAM providers to lean on, how can you be sure of what matters most?
You need a partner with the ability to execute on your behalf. And that’s why we are pleased to be positioned highest in Ability to Execute in the 2020 Gartner Magic Quadrant for Access Management. This means that Ping Identity has demonstrated strong market responsiveness, that our products are feature rich and mature and can adapt to changing requirements, and that we have a large, satisfied customer base.
The biggest takeaway from Gartner’s 2020 reports: the need to deploy or modernize access management has never been more critical.
But the proof is in the pudding, right? Well, in this case the pudding is the complementary report called the The Gartner 2020 Critical Capabilities for Access Management. In addition to the Magic Quadrant for Access Management, Gartner provides guidance and scoring for the specific “critical capabilities” an access management solution must provide. The report is often overlooked by the more heavily marketed Magic Quadrant, but it serves an equally important role for identity buyers and evaluators.
According to Gartner, “a Critical Capabilities document is a comparative analysis that scores competing products or services against a set of critical differentiators identified by Gartner. It shows you which products or services are a best fit in various use cases to provide you actionable advice on which products/services you should add to your vendor shortlists for further evaluation.” In other words, the Magic Quadrant report provides an overall view of how vendors stack up in terms of their “completeness of vision” and “ability to execute,” while the Critical Capabilities report zooms into vendors’ scoring with regards to specific use cases.
Let’s jump in.
2020 Gartner Magic Quadrant for Access Management
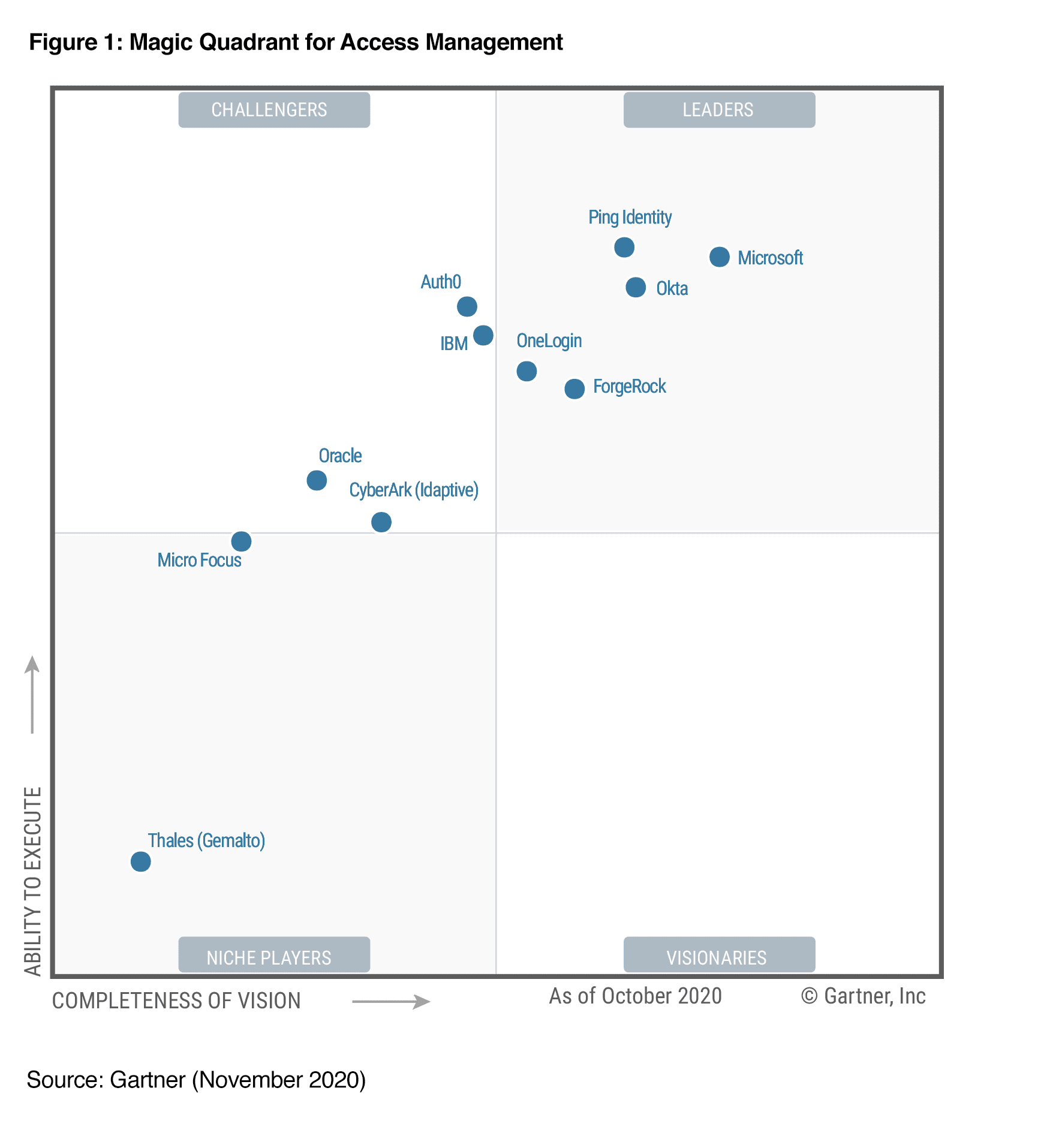
2020 marks Ping Identity’s fourth consecutive year as a Leader. We believe this year’s Magic Quadrant and Critical Capabilities reports acknowledge that Ping Identity is pushing the industry forward in several ways. We were recognized for:
- Product Capabilities. Ping was recognized for nonstandard application integration, API access controls and user self-service capabilities. Scoring “very high for product capabilities,” we built our entire solution on open standards for maximum interoperability and extensibility. We provide extensive APIs for integration and customization, and we invest in turnkey integration kits that rapidly connect to all your SaaS, web, mobile and legacy apps.
- Customer Experience. Ping was recognized for integration flexibility, ease of deployment and administration. Scoring “very high for customer experience,” we offer numerous self-service features to give administrators, developers and users more seamless and intuitive experiences. Administrators can control product and environment configurations from a top-level IAM admin or a delegated business application admin view in PingCentral. Developers can quickly embed identity services into their apps with PingOne for Customers, allowing them to get back to developing features which deliver strategic business value. And we make it easy for users to create new accounts, manage profiles and control their data.
- SaaS-delivered IAM. Recognized for solid adoption of new SaaS products PingOne for Customers and PingOne for Enterprise as well as offering more than 1,000 OOTB SSO connectors for SaaS apps along with supporting standards, our solutions really are fast and easy to set up.
2020 Gartner Critical Capabilities for Access Management
The 2020 Critical Capabilities for Access Management research defines three use cases or scenarios: internal identities, external identities and a combination of internal and external identities.
- Internal Users Access Management. This B2E use case for workforce (internal) identities includes employees, temporary workers, outsourcers and contractors. The capabilities’ weightings placed highest emphasis on standard application enablement, with the next highest weightings across authorization and adaptive access, nonstandard application enablement and user authentication methods.
- External Users Access Management. This use case for B2C, B2B, G2C (government to citizen) and gig economy (external) identities includes customers, partners, citizens and contingent freelance talent. The highest weighting by far resides in user self-service capabilities. All other capabilities held similar weightings.
- Multi-constituency Access Management. This use case includes a vendor’s ability to support both the internal and external identity use cases, an important consideration for large enterprises seeking to standardize on a single identity platform. The highest weighting was emphasized under the administer identities capability. Directory and identity sync, authorization and adaptive access, and user self-service features were the next highest weighted capabilities.
All three use cases are weighted on the following capabilities: administer identities, API access controls, authorization and adaptive access, BYOI integration, directory and identity sync, event logging and reporting, nonstandard application enablement, standard application enablement, user authentication methods, and user self-service features.
Ping Scored Highest in All Three Use Cases
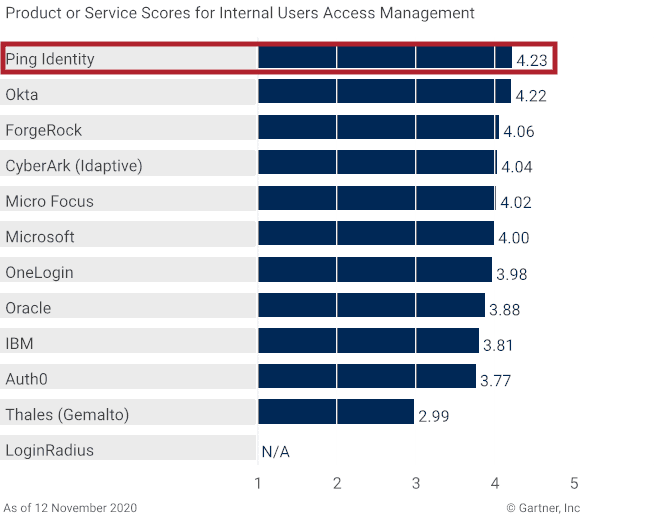
Figure 1: Vendors’ Product Scores for Internal Users Access Management Use Case
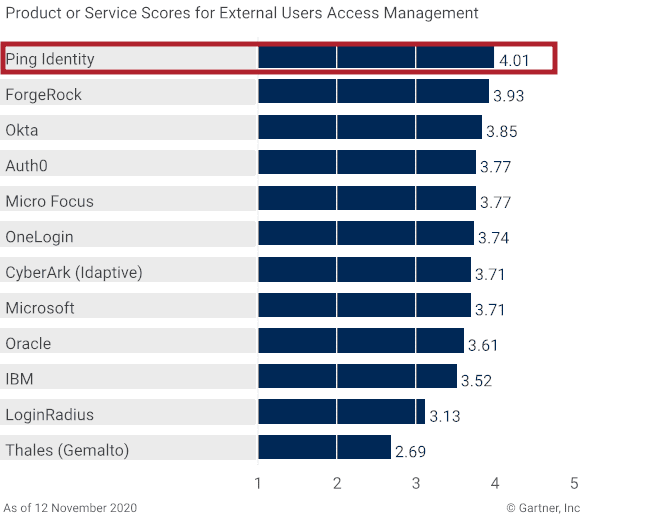
Figure 2: Vendors’ Product Scores for External Users Access Management Use Case
Figure 3: Vendors’ Product Scores for Multiconstituency Access Management Use Case
What Makes Ping Identity Stand Out?
We are taking this opportunity to proudly reflect on the incredible year we’ve had.
Our Customers
We believe this recognition wouldn’t be possible without the amazing passion, feedback and support that our customers have provided. We’re lucky to partner with brilliant security and business leaders who push us every day to innovate faster to solve real-world problems.
Ping customers are transforming their organizations through the power of identity—building digital business models with identity at the center and deploying IAM solutions more broadly than ever. HP delivers a simplified, engaging experience to 150+ million customers and partners via a unified identity ecosystem. We’re proud to be trusted by over half of the Fortune 100 and be recognized with a class-leading Net Promoter Score of 65.
Nothing is more fulfilling than to see our customers succeed with identity at scale. It’s only through our customer’s successes that Ping can obtain such high recognition, and ensuring their success is ingrained in our culture.
New Acquisitions in Dynamic Authorization and Personal Identity
Ping continues to push innovation in our industry through both organic product development and strategic acquisitions. With the addition of ShoCard and Symphonic to Ping this year, we have the opportunity to bring the power of dynamic authorization and personal identity to market with the most comprehensive identity security platform available.
Standalone Identity Services Available for Rapid Adoption
This year we also expanded our platform with PingOne services, a suite of stand-alone cloud services that provide advanced identity and access management capabilities with flexible integration options and rapid implementation. The first two cloud services we announced, PingOne MFA and PingOne Risk, will be followed by additional services, all of which address enterprises’ needs to balance security and convenience for their workforce and customers. Alongside these services, we launched a unified cloud administration experience that provides a single location for administrators to view and manage their identity solutions deployed on-premises and in the cloud.
Going Passwordless with PingZero
This year, we raised the bar on advanced passwordless features by unveiling PingZero, a suite of passwordless authentication features organizations can implement to deliver seamless digital experiences to employees and customers. By eliminating login friction, including removing the need for usernames and passwords, PingZero boosts employee productivity, improves customer retention and acquisition rates, and strengthens cybersecurity defenses—all with zero passwords and zero friction. PingZero uniquely leverages the Ping Intelligent Identity platform and technologies like the FIDO2 standard to enable passwordless experiences across a variety of resources and applications.
The Immediate Need for Modern Access Management
The biggest takeaway from Gartner’s Magic Quadrant and Critical Capabilities reports: modern, highly capable access management tools have never been more critical for organizations' digital transformation initiatives. Gartner attributes this critical need to a few factors.
The Sudden Shift to Remote Work
The trend toward a mobile, distributed workforce, including working from home, has been underway for many years. Unfortunately, sudden events like COVID-19 can shine a harsh spotlight on the need to provide a more comprehensive workforce access and productivity solution than many companies have in place currently.
Gartner is seeing the market increasingly embracing this long term. According to their Forecast Analysis, “through 2024, approximately 30% of all employees working remotely will permanently work from home. By the end of 2024, the change in the nature of work will increase the total available remote worker market to 60% of all employees...By 2024, in-person meetings will drop from 60% of enterprise meetings to 25%, driven by remote work and changing workforce demographics.”
Working from home is no longer just a perk to offer employees, but an essential alternative to keep your business running. Ping is prepared to help IT organizations ensure employees can be secure and productive anywhere in the world.
Read our step-by-step guide to secure work from home with digital identity.
Acceleration of Digital Customer Experience Initiatives
The world events also accelerated the move to digital business and caused an immediate demand for online access. This surfaced weaknesses for many companies who needed to provide a fully digital experience and placed a premium on those that were providing one.
Customers want two simple things as they interact with brands. First, they want brands to delight them by providing great user experiences. Second, they want brands to protect them from fraud, breaches and privacy violations. CIAM helps you do both.
Delighting your customers means ensuring their journey—from their initial introduction to your brand to the time they become your loyal advocates—is as smooth as possible. If you fall short of providing an exceptional experience, your customers may go elsewhere. Given what’s at stake, a great customer experience is no longer just nice to have; it's a critical differentiator.
You can’t stop at experience either. Customers also care deeply about security. A 2019 Ping Identity report revealed that 81% of customers would stop engaging with a brand online following a breach (a 3% increase over 2018), and one in four would stop all interaction whatsoever. The most recent Cost of a Data Breach study found that of the $3.92 million average cost of a data breach, 36% of the total, or $1.42 million, was the direct result of lost business.
Adoption of Zero Trust Security Models
Enterprises are accelerating digital transformation initiatives in response to the rapidly evolving business landscape. Successfully implementing business-critical digital transformation efforts requires an efficient, effective workforce that has access to every application and tool they need to get their job done.
However, security leaders are faced with the difficult challenge of balancing the security of their organizations with keeping employees productive by providing access to resources from anywhere, at any time. Maintaining this balance requires an organization to have full confidence in the identity of the employee requesting access to ensure only the right users gain access to the resources they’re authorized to use.
In response, organizations are adopting Zero Trust. Zero Trust is a strategic concept that encourages security teams to rely less on the safety of a network perimeter and more on the identity of the user and the secure processes and technologies that can be applied directly to corporate resources, irrespective of where they’re located. Gartner takes this a step further by applying seven imperatives of a continuous adaptive risk and trust assessment, or CARTA. According to Gartner research, “While zero trust is the initial security posture, CARTA envisions enterprise security infrastructure as continuously adaptive based on real-time assessments of risk/trust throughout the life cycle of a user’s access.”2
Ping further addressed the need for Zero Trust and CARTA approaches this year with PingOne Risk, a cloud service that uses machine learning to evaluate risk signals and detect threats in real time. It evaluates multiple signals to understand the level of risk posed by a user attempting to access a particular resource, including UEBA, anonymous network detection, impossible travel detection and the reputation of a user’s IP address
Make the Best IAM Decisions for Your Needs
There are many trends and capabilities to consider, but you don’t need to go it alone. We’re pleased to provide access to the 2020 Gartner Magic Quadrant for Access Management to help you evaluate solutions against your unique objectives and requirements. Download your complimentary copy of the report.
SOURCES:
