How to Evaluate Identity Integrations to Reduce Security Risks
At Ping, we offer several products and services, ranging from standard practices—including single sign-on (SSO) and multi-factor authentication (MFA)—to unique offerings like API intelligence and data governance. But what differentiates us time after time is our integrations. Our extensive integrations are why so many of the world’s largest enterprises—including over 60% of the Fortune 100—choose us for their identity needs.
Enterprise organizations partner with us not because of a single capability but because of our vision of an identity ecosystem to power everyone and everything. We refer to this as an “authentication authority,” which acts as a single hub powerful enough to manage all of your identity transactions. When architected correctly, this authentication authority provides the integration points to connect any user on any device to any app on any cloud.
Because of the unique requirements of large enterprises, getting this architecture right is imperative. These requirements often include:
- Technology deployed both in the cloud and on-premises
- Diverse user types, such as partners and contractors
- An application portfolio comprised of locally deployed software, homegrown apps, APIs and SaaS
These nuances make it critical that enterprises thoroughly understand the integration capabilities of potential vendors to ensure their needs are met.
Not All Vendor Integrations are Created Equally
Above all else, you need a vendor’s integrations to be secure. To ensure they are, you need to understand how they address password security.
Insecure password practices are still to blame for many security events. In fact, stolen credentials and brute force attacks account for 80% of successful hacking attempts, according to the 2020 Verizon Data Breach Report. This makes sense when you think about user behavior. Despite all of the education and warnings, we know that users continue to engage in risky practices like reusing passwords and writing them down.
You might be surprised, though, to learn that some security vendors are doing the same thing. They’re doing the equivalent of writing down passwords and replaying them by using password vaulting, also called password replay or a password manager. Password vaulting relies on storing passwords in a directory, often in the cloud, and replaying them to the application during every authentication event.
Password vaulting poses significant security risks as passwords can easily be compromised, leading standards bodies and industry experts to caution against it. Yet, some identity vendors are still using this practice, while masking it with misleading terms like “secure web authentication.”
“Gartner strongly recommends against using password vaulting and forwarding due to the associated risks of potential password compromise; instead, use standards-based federation when possible.”
—Gartner Identity and Access Management MQ 2019
To avoid this risk, you want to ensure your vendor is using federation to securely authenticate users. By replacing passwords with token exchange, federation minimizes the risk of an attack.
Federation is the foundation of the authentication authority, providing unparalleled control over access to resources. When your vendor provides an authentication authority that acts as a federated identity hub, you can feel confident that all of your applications and user devices will authenticate consistently and securely.
Authentication Authority: How You Ensure Integrations are Secure
An authentication authority allows your employees and other workforce users to securely access all the applications they need from any device. It enables easy integration with applications across the enterprise, third-party authentication sources, diverse user directories and existing IAM systems, all while supporting current and past versions of identity standards like OAuth, OpenID Connect, SAML and WS-Federation.
To realize the authentication authority vision, you must integrate three core facets of your enterprise: applications, strong authentication and identity stores. Doing so allows you to deliver a consistent experience, while also keeping employees secure and productive. This integration also ensures IT is agile enough to respond to changing business needs, like the sudden shift to remote work that occurred earlier this year.
Applications
Single sign-on is a core capability that allows you to give users seamless single-click access to their applications without the hassle of multiple sign-ons and passwords. For SSO to deliver on its potential to increase productivity and convenience, it must be applied to all applications. But many identity systems fall short when it comes to integrating the many different application types found in large enterprises. These systems require a heavy burden on IT to be able to support SSO to SaaS, mobile, legacy and homegrown apps, as well as APIs.
Instead, you need a vendor that can easily integrate with applications across your enterprise. At Ping, we ensure you can provide SSO to all applications via:
- An app catalog with pre-configured connections
- Open standards that are developer-friendly
- Extensive integration kits
- Token meditation and translation
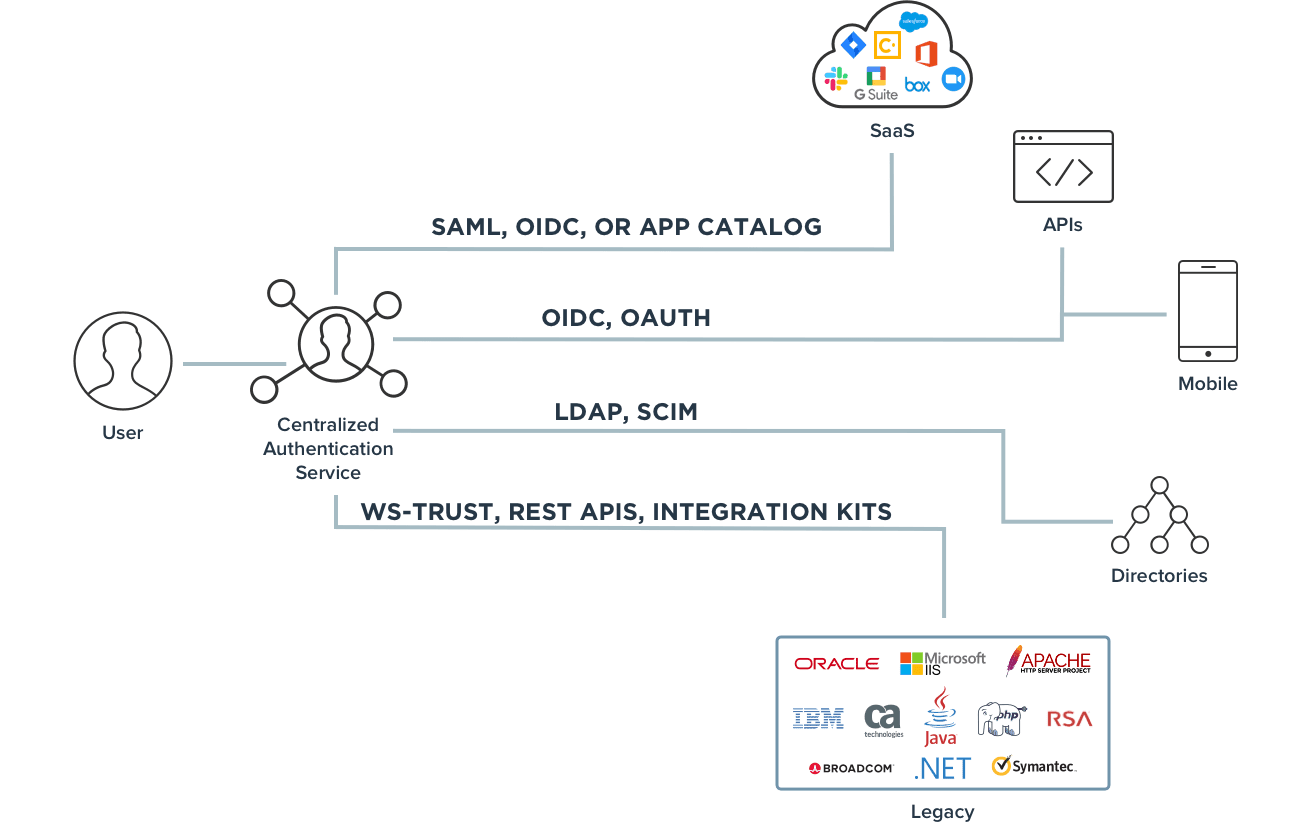
Strong Authentication
Identity must account for all of your security investments to deliver a seamless experience to your users and support greater productivity and agility. You’re able to experience these benefits while also protecting your workforce and valuable enterprise assets with adaptive multi-factor authentication. Adaptive MFA lets you leverage risk signals and data from multiple sources to apply adaptive authentication policies that evaluate a user’s devices, behavior and other context beyond passwords to dynamically assess risk and respond appropriately.
Ping’s workforce authentication authority gives you the ability to deliver strong, centralized authentication services to any application, any cloud, any directory and in any situation. You’re able to:
- Apply MFA everywhere
- Strengthen VPN security
- Enforce policies on devices via MDM providers
- Create adaptive and contextual policies based on third-party risk scoring
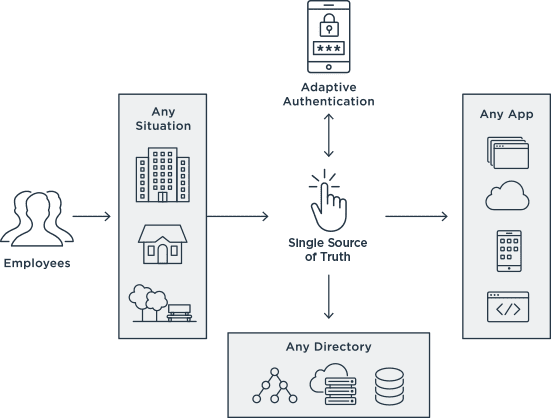
Identity Stores
When it comes to directory capabilities, most large enterprises value independence and choice. This is evident in the popularity of Active Directory, which is the preferred enterprise data store of many of our customers. Yet, some vendors try to force enterprises to replace AD in favor of their own directory capabilities.
While Ping also provides directory capabilities, our workforce authentication authority lets us be flexible to meet our customers’ needs, not the other way around. Our authentication authority can integrate and pull user attributes from multiple directories to maximize your existing investments. Our identity store integrations cover common typical enterprise needs including:
- Legacy data stores (Microsoft, Oracle, IBM)
- Cloud (AWS, Microsoft, Google)
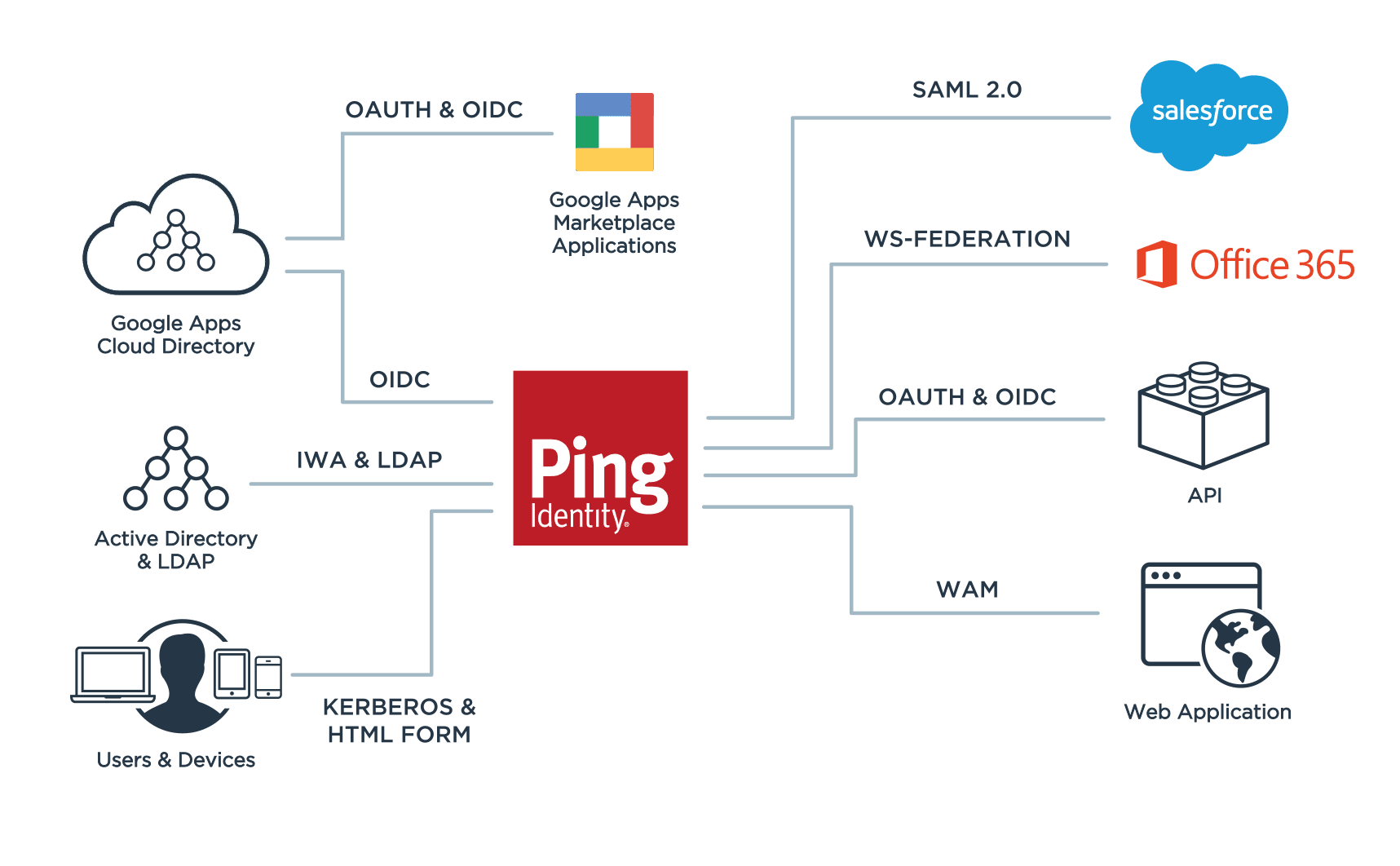
Passwordless Authentication: The Next Generation of Identity Security
When evaluating identity integrations, you’ll find that those vendors who offer the most advanced, secure integrations are also the ones pushing the envelope to remove passwords altogether—and the risks that come along with them.
Passwordless authentication lets you strike the ultimate balance between security and user experience by minimizing your reliance on passwords. But because it doesn’t fit in the usual box of a product or technology, like MFA or SSO, it can feel elusive.
Passwordless is best thought of as a goal or desired outcome. To achieve it, you need the right technologies to support use cases that reduce and potentially even eliminate the use of passwords.
An authentication authority makes passwordless a reality for even the largest and most complex enterprises. By allowing you to leverage adaptive MFA, an authentication authority lets you minimize the requirement for passwords based on user behavior.
Ping provides our customers with flexible passwordless options as well as integrations with several third-party passwordless providers. PingZero
Secure Your Integrations & Enterprise with a Workforce Authentication Authority
It’s imperative that enterprises thoroughly understand how potential vendors support integrations to ensure security isn’t compromised. Questionable practices and insufficient capabilities can introduce unnecessary risks.
An authentication authority gives you peace of mind that your integrations and users are secure. At the same time, it gives you the freedom to launch new products quickly and the flexibility to scale identity without being locked into a particular vendor or ecosystem. With an authentication authority, you can:
- Improve security posture
- Boost employee productivity
- Increase business agility.
To learn how Workforce360, Ping’s workforce authentication authority, can help you secure your enterprise, read the whitepaper.

