8 Benefits of Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) reduces the risk of security breaches from occurring and keeps data safe. In the past, requiring a static username and password to access an account seemed sufficient for security. However, weak or stolen passwords can be used to execute fraud attacks and data breaches when they are the only form of authentication required. Using MFA to bolster password security with another form of authentication is proven to keep hackers out of your systems. According to Microsoft, MFA can “prevent 99.9 percent of attacks on your accounts.”
What is MFA and How does it Work?
At a basic level, authentication requires proof that users are who they say they are. Multi-factor authentication takes it step further by requiring users to provide proof from two or more authentication factors (categories) before access is granted. A hacker or unauthorized user may be able to steal a password or buy it on the dark web, but for them to gain access to a second authentication factor is slim and requires much more effort. Consequently, MFA stops most bad actors before they can enter your systems and gain access to your data.
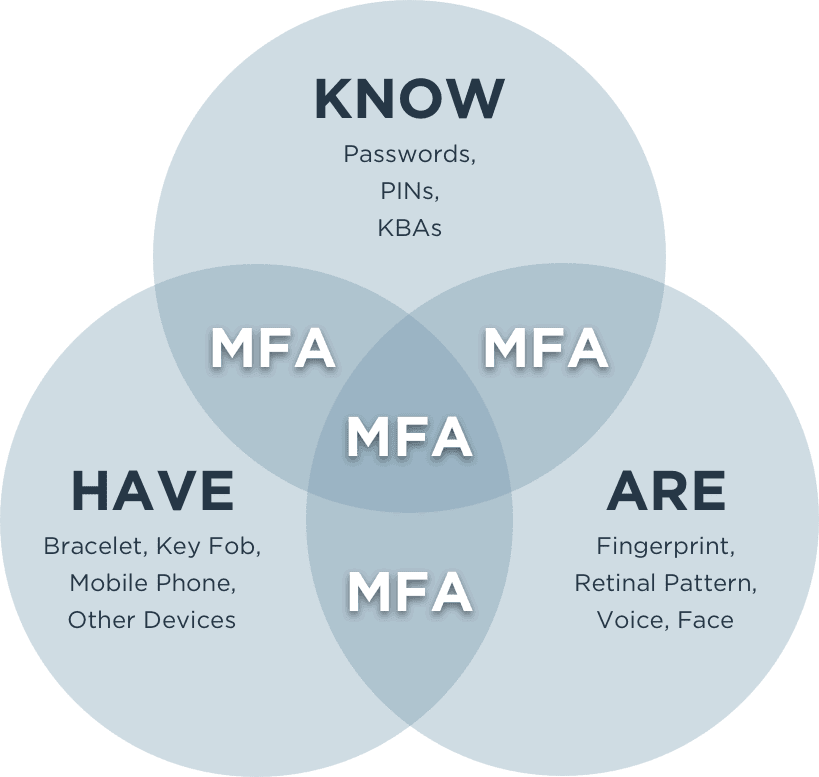
Authentication Factors:
Something you know (knowledge)
The most common knowledge factor is a password. Other knowledge factors include PINs, passphrases and security questions (e.g., What was the name of your high school?). These have become less secure as users fall victim to phishing attacks, hackers steal or buy passwords on the dark web, and people openly share personal information (answers to security questions) on social media sites.
Something you have (possession)
Possession factors include smartphones, hard tokens, soft tokens, key fobs and smartcards. To verify a user’s identity, they may receive a one-time passcode (OTP) sent to a smartphone, receive a unique code generated by a physical token, or need to insert a smartcard into a device.
Something you are (inheritance)
Inheritance factors, also referred to as biometrics, are the unique physical traits we all possess. Biometrics are verified through fingerprint scans, voice or facial recognition, retinal scans and other methods such as your heartbeat. Because biometrics require some sort of hardware for scanning, enterprises need to make sure users have access to the necessary equipment before implementation.
What is the Purpose of MFA?
Habits are hard to break. Most organizations don’t have the time or the resources to fully eliminate usernames and passwords to authenticate users, so additional ways to verify a user’s identity are necessary. Multi-factor authentication keeps data and systems secure by adding roadblocks that stop bad actors in their tracks. Even if a password or other authentication method is compromised, it’s extremely rare that a hacker also has a second or third authentication factor. MFA prevents users without the requisite number of authentication factors from accessing your resources.
Why is it Important to Use Multiple Factors of Authentication?
A single compromised password allowed hackers to disrupt the Colonial Pipeline because other forms of authentication were not required to access their VPN. Ransomware and other cyberattacks have become a top priority on the U.S. cybersecurity agenda. While cybersecurity training may be provided by organizations, employees still fall for phishing tactics or share passwords out of convenience. Customers can also fall victim to scams or have their data stolen. MFA prevents bad actors from using compromised credentials to enter your systems because they cannot provide the second and/or third authentication factor.
What are 8 Benefits of MFA?
Increases Security
By requiring users to provide multiple credentials prior to accessing accounts, hackers are prevented from using stolen passwords, devices, or other individual pieces of information to enter your network. A recent Ping Identity survey revealed that security and IT professionals consider multi-factor authentication to be the most effective security control to have in place for protecting on-premises and public cloud data.
Reduces Risk from Compromised Passwords
While passwords are the most common form of authentication, they are the least secure. People may reuse or share passwords, which can also be stolen or guessed, leading to exposure for account holders and system administrators. A 2021 Verizon Data Breach Investigations Report found that 61 percent of breaches in 2020 were executed using unauthorized credentials.
61% of data breaches involve the use of unauthorized credentials.
2021 Data Breach Investigations Report, Verizon
Customizable Security Solution
Each authentication factor offers multiple options, providing enterprises with the ability to customize the user experience to meet their needs. For example, users might have access to fingerprint scanners on their smartphones, but not retinal or voice recognition scanners. Two factors may be sufficient for some use cases, while others may require all three authentication factors.
Compatible with Single Sign-On (SSO)
MFA can be embedded into applications and integrated with single sign-on. Users no longer have to create multiple unique passwords or make the risky choice of reusing the same password for different applications when logging in. Together with SSO, MFA reduces friction while verifying the user’s identity, which saves time and improves productivity.
Scalable for Changing User Bases
Multi-factor authentication easily adapts to your business needs. MFA can be set up for all users, including employees, customers and partners. Single sign-on combined with MFA eliminates the need for multiple passwords, streamlines the login process, improves the user experience, and reduces the number of calls to IT departments for password assistance.
Regulatory Compliance
There may be industry or geographical regulations requiring MFA. For example, Payment Card Industry Data Security Standard (PCI-DSS) requires that MFA be implemented in some situations to prevent unauthorized users from accessing payment processing systems. It also helps meet strong customer authentication requirements dictated by Payments Service Directive 2 (PSD2) in the EU. In addition, MFA helps healthcare providers comply with the Health Insurance Portability and Accountability Act (HIPAA).
Enables Enterprise Mobility
The pandemic made remote work options necessary for many organizations and sped up the digital transformation. Allowing employees to use mobile devices to easily and securely access the resources they need increases productivity. Using MFA to log into business applications, especially when integrated with SSO, provides the flexibility and 24/7 access employees need, while keeping networks and data protected.
Adaptable for Different Use Cases
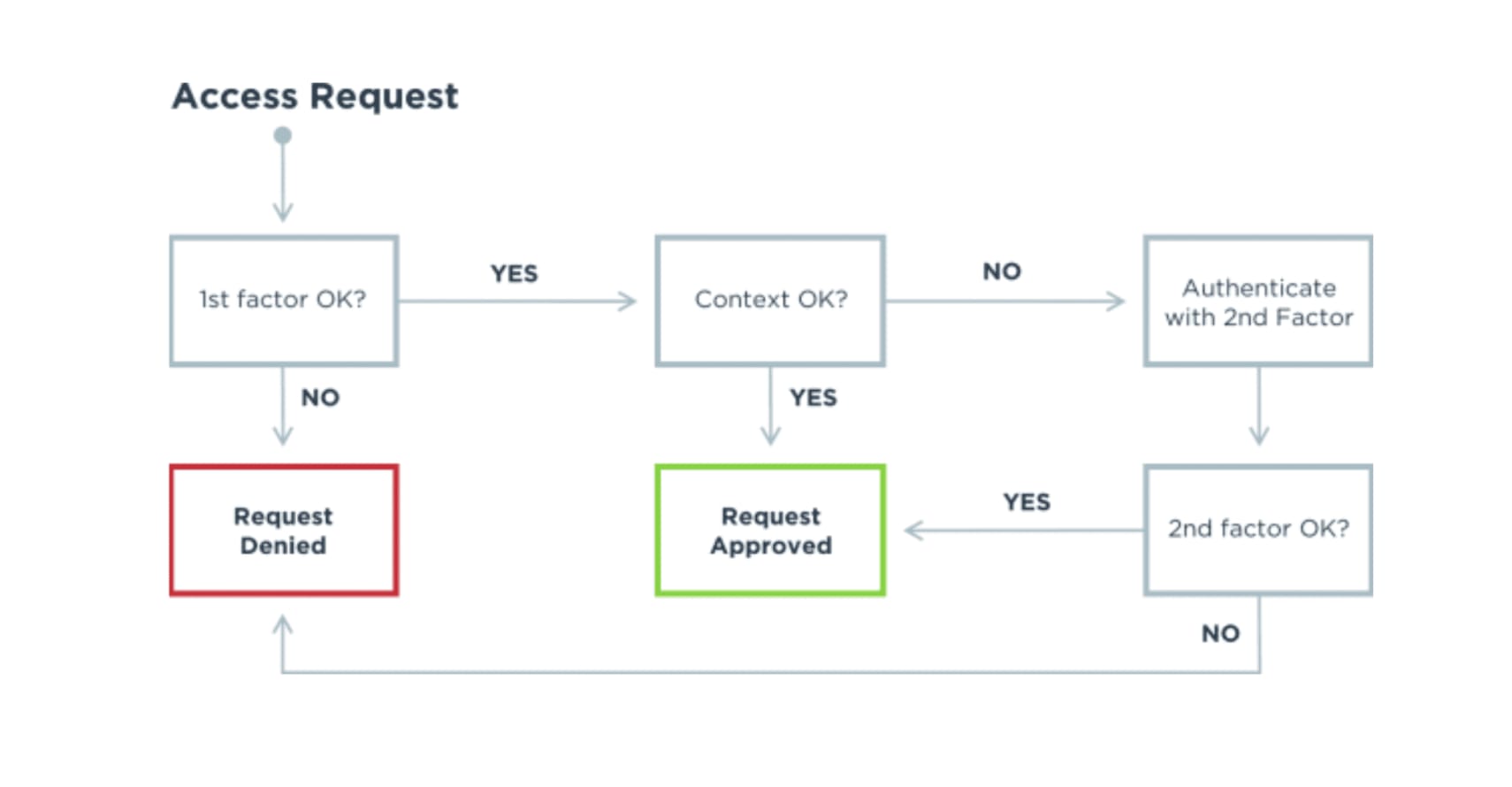
Some situations call for greater security, like conducting high-value transactions and accessing sensitive data from unknown networks and devices. Adaptive MFA uses contextual and behavioral data such as geolocation, IP address and time since last authentication to assess risk. If the IP address is considered risky (e.g., coffee shop or anonymous network) or other red flags are noted, authentication factors can be added as needed to gain a higher level of assurance about a user’s identity.
What is the Risk of Not Using Multi-factor Authentication?
As noted above, the Colonial Pipeline ransomware attack was caused by a compromised password and could have been prevented if MFA was in place. MFA protects against phishing, social engineering and password brute-force attacks and prevents logins from attackers exploiting weak or stolen credentials. A 2020 study by the Digital Shadows Photon Research Team found 15 billion stolen credentials available on the dark web, including username and password pairs for online banking, social media accounts and music streaming services. Simply put, if a username-password combination is all that is required to access your systems, that is negligent as you are allowing cybercriminals to steal data and/or install ransomware.
Conclusion
Adding multi-factor authentication is the #1 action most enterprises can do to prevent cybersecurity incidents from occurring. Even in industries that do not currently require MFA for regulatory compliance, governments are taking cybersecurity more seriously as agencies and infrastructure are increasingly being targeted. Investing in an MFA solution is an effective way to secure your data from unauthorized access and protect your resources.
To learn more about Ping’s MFA solutions, please watch this video.
FAQs for MFA
What is an Example of MFA?Let’s use PingOne MFA. Customers can choose to authenticate by tapping, swiping or using fingerprint or facial recognition via a secure push notification from their mobile device or using Fast Identity Online’s FIDO2 bound biometrics on their laptop or security keys. Other options include a one-time password (OTP) sent to their email or SMS, or use of third-party, time-based one-time passwords (TOTP) authenticator apps (such as Google Authenticator). | ||
How does MFA Improve Security?MFA adds layers of security by requiring users to provide multiple forms of identification. Think of MFA like a bank requiring you to provide ID, account information and a physical key in order to open a safety deposit box. If any of the required forms of identification are missing, access is denied. | ||
What is the Difference between MFA and 2FA?Multi-factor authentication (MFA) requires proof of a user’s identity from two or more authentication categories. Two-factor authentication (2FA) is a subset of MFA and requires proof of a user’s identity from two categories. | ||
How is Cloud MFA Different than On-prem MFA?Cloud-delivered MFA removes the limitations of on-prem MFA. With ever changing cybersecurity threats, it is difficult for in-house employees to stay current on risks and the investment in software and equipment adds up. Cloud MFA lets organizations outsource their MFA solutions to experts. | ||
How does MFA Increase Security for Enterprises Working with Third Parties?Organizations often work with partners, vendors and other third parties who access their systems. Not only does the organization have to worry about the credentials of its employees and customers, it also has to be concerned about the data security of third parties. By requiring multiple forms of authentication from all users, MFA increases security and limits the risk of data breaches. |
