To Better Understand Digital Identity, Look to Physics
To the uninitiated, the whole concept of digital identity can be difficult to understand. We all get what user accounts are and a bit about how they can be leveraged—thanks to the internet and social media—but for many of us, they’re just basic tools that we use, and we put little thought into what makes them run. We may have an idea of what goes into maintaining an identity (things like names and passwords), but no real knowledge of the inner workings.
But digital identity is all around us in daily life, and understanding how it works can help us think about identity in a new way and gain insight into how digital identity concepts can relate to one another. So, as someone who thinks about identity (a lot), I was struck by how identity concepts bear a striking resemblance to models and concepts found in physics.
Theoretical Physics Models
First, let’s get it straight that I’m an identity management architect by training, not a theoretical physicist. So as I was putting my thoughts down on paper, I had to discard a few ideas that didn’t fully pan out. For instance, my initial approach was to try and come up with some “Grand Unified Theory” of identity that would explain the relationships between concepts like identity management, access management and identity governance.
It sounded good at first, but I soon got stuck. What seemed to work better as an analogy is how identity maps to the atomic model, which most of us are familiar with from school science and/or physics classes. So here goes.
Identity attributes = atoms
In this analogy, atoms are attributes that we might see from authoritative sources such as PingDirectory, Active Directory or a database. We can combine these “atoms” to create different types of identity elements (particles) that relate to objects, such as identities, entitlements, roles and single sign-on. We can further combine the compounds of these elements to be the entities in our productive identity solution, such as compounds of groups made up of elemental identities or roles made up of elemental entitlements.
Actions such as authentication, authorization, provisioning, attestation, API access controls and data synchronization become the forces that move these objects—and make them become more than just the sum of their parts.
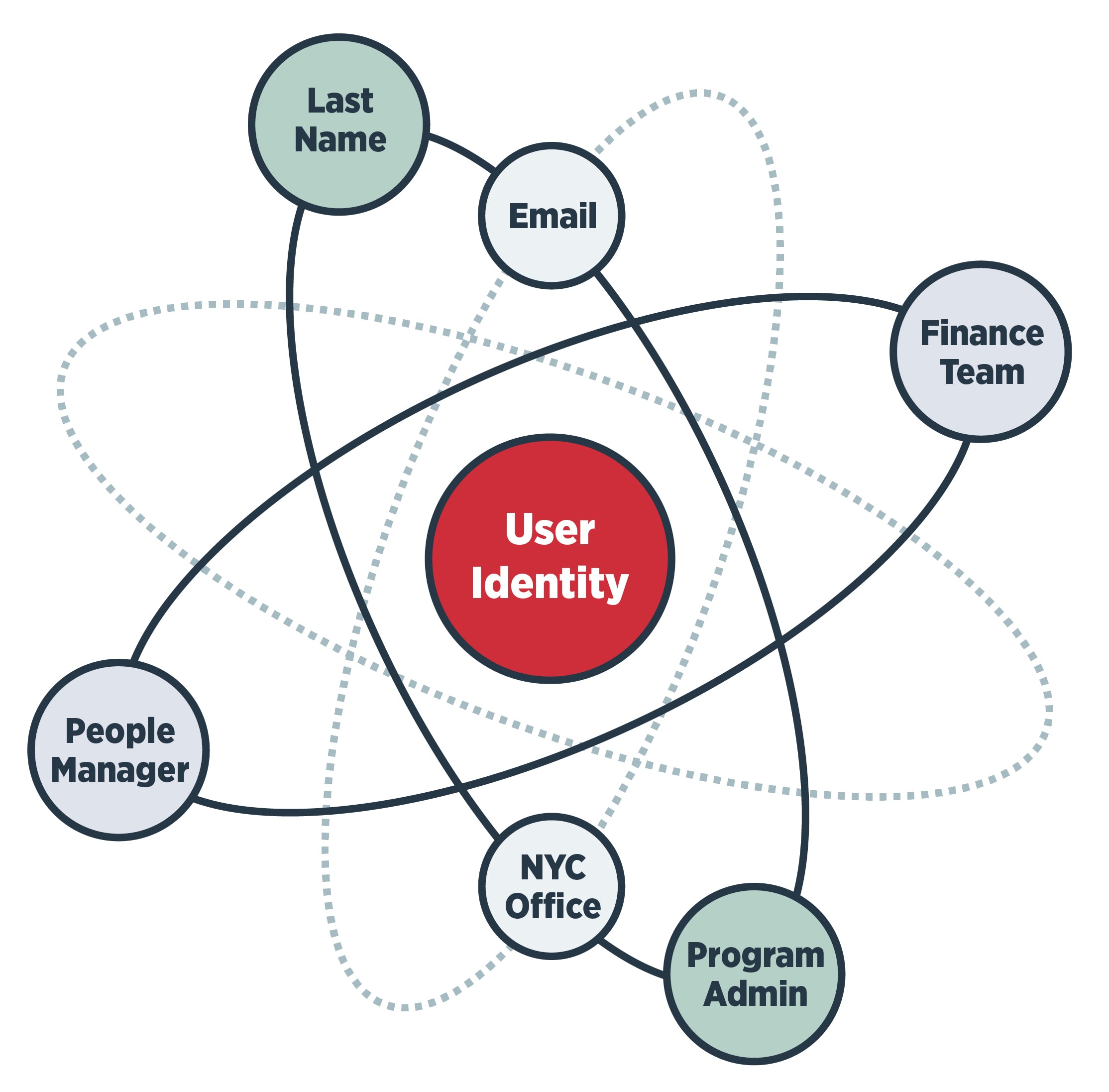
One of the things that I like the most about this view of identity is that it brings us back to the idea that all of these objects, whether they be elements or compounds, can be broken down into their parts and put back together. Interestingly enough, we can potentially bring identity management tools into this model when we consider that we can create “isotopes” of identity elements by passing them through an “atom smasher” using the forces listed above.
Other actions and forces can cause our atoms to change over time, growing smaller or larger as attributes are added, modified and removed. Sometimes this happens via self-service operations, when we change our address or other personal information. Other times it happens when application administrators or help desk staff perform actions on our identities as they make entitlements, groups and other changes.
Because when you think about it, changing identity access entitlements in the most compliant way involves removing all entitlements, down to the most basic ones that apply to all organizational identities, and then building them back up to the new access. And identity “half-lives” are even more evident when we consider that some entitlements might have specific life spans due to specific validity spans built into them.
Even more interestingly, we can also use the concept of alchemy to “create” new types of objects using tools like DataSync as we move information from one repository to another. It is easy enough to create new elements in such a manner, which would be “custom” entries.
Properties of Identity Physics
The other area where the physics model seems appropriate to identity is when we consider ideas such as inertia, entropy, uncertainty and relativity.
Inertia
Inertia is an interesting concept as it relates to identity. Think about concepts such as “friction” or “stickiness” when looking at overall operations in provisioning or single sign-on. In some operations, things “seem” to move slower or faster, which might have real-world reasons such as waiting on approvals or just network latency. (One of our primary objectives here at Ping is to reduce this friction wherever desirable to provide better user experiences.)
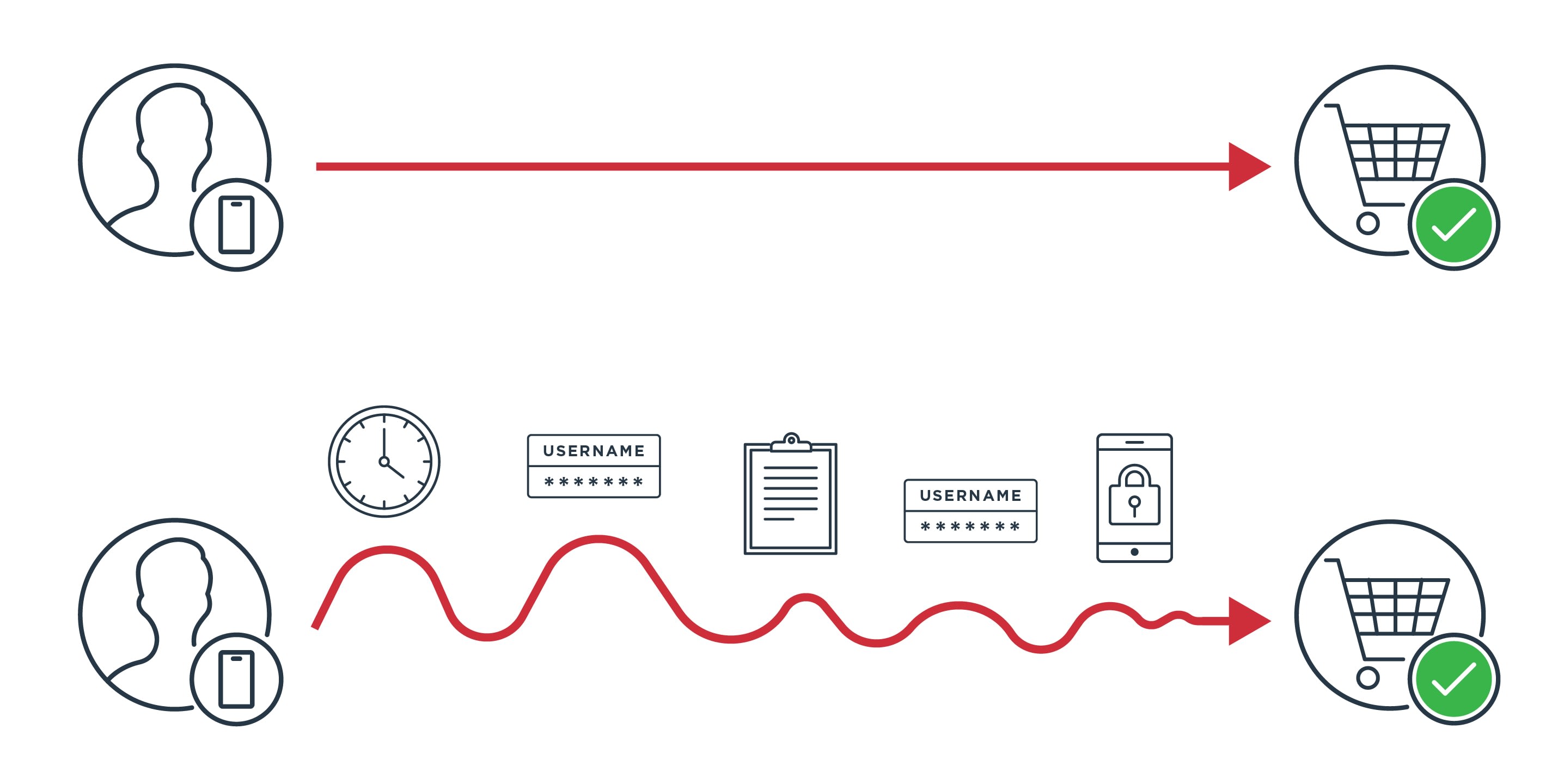
This raises the issue of whether identity friction is a good thing or bad thing. Certainly for customer-related experiences such as ordering a product or service, we want minimal friction to establish identity: just what we need to get the transaction completed. Based on the graphic above, I think we can all agree that when making purchases, the top model is preferable.
However, if we are talking about accessing sensitive processes or information such as financial data, employee information or other closely held corporate secrets, we might want more steps introduced into the process. It really comes down to if the process should be smoothly flowing to easy completion or a bit slower—with intentionally introduced friction—to make sure that the process is not flying off the rails, ensuring it is more secure and better audited. Of course, too much of that friction could result in the delay of related processes or desired results, so this is something that needs to be reevaluated regularly.
Regardless, simplification in identity operations has a huge impact on reducing the forces of inertia. Implementing single sign-on, or better yet passwordless technologies, can remove much of the friction that comes with the user experience.
Improved orchestration of the back end of the process to manage changes in user load and needs also assists in the reduction of friction. As we continuously automate how our application servers are spun up and maintained, we directly influence the experience as well.
Entropy
Much like we see in physics, identity elements are subject to entropy. The more we work with identity elements and make changes, the greater the chance that these changes will cause issues. Sometimes it is in the form of modifying an attribute in an objectClass in a directory service just to find out it can’t be done, or that it has an effect on a data sync operation later on in the flow of events. As we add more and more to our identity elements and operations, the risk of errors and breakdowns escalates. Each change needs to be evaluated with care.
Uncertainty
Evaluating operations regarding our “identity physics” is a big part of what we do as identity management scientists. Sometimes referred to as the uncertainty principle or the observer effect, we need to carefully evaluate what and how we are monitoring. This is significant in our discipline, as the creation and monitoring of logs is a large part of what we consider to be the result of our work. Even the introduction of logging operations has an impact on performance and can lead to an entropic effect, as additional monitoring adds complexity that affects the speed of operations. Also, significant effects can occur if logs get too large.
Additional uncertainty, perhaps more in the traditional form, is always managed by good requirements and testing plans. While it is difficult to obtain 100% certainty when it comes to operations despite all our hard work in requirements, testing and operational logging, all efforts in that direction help in the pursuit of our overall goal.
Those of us who are applied identity scientists have all experienced the ultimate application (and resulting facepalm) of the observer effect when we can’t find the source of an error—but a colleague spots it in seconds when we ask them for help.
Relativity
Relativity refers to the differences between observers and objects. Much like my discussion of uncertainty in the previous section, this concept involves how things on the outside affect identity operations. As opposed to physics, in identity we can handle many “relativistic” concerns by carefully managing project requirements regarding how the identity system works with the observers.
Good Identity Organization
In chaotic systems such as those that the discipline of physics seeks to describe, there is also the concept of the “self-organizing principle,” which dictates a tendency for chaotic systems to organize themselves. While this might be a tendency in physics, organization usually needs a nudge in the right direction in the identity world. Proper attention to requirements and a good change control process are a crucial part of the equation.
To learn more about some of the basic concepts of identity security, check out our Identity Fundamentals collection.
