4 Ways Self-service IAM is a Game Changer
Welcome to PingCentral
PingCentral is a new product from Ping Identity. It’s a self-service IAM application integration tool and converged operating portal for business users that provides workflows, templates, orchestration automation, lifecycle management and central monitoring. It allows resource-constrained IAM teams to do more with less, serving the business faster and delighting application teams by enabling the self-service onboarding of applications and consumption of centralized identity services.
The Roadmap for PingCentral Leads to a Converged Operating Portal Vision
In v1.0, PingCentral provides an administration layer for authentication and single sign-on (SSO) tasks across all instances of PingFederate in each of your environment tiers (e.g., dev, QA, staging, prod, etc.). The Ping Intelligent Identity platform has additional capabilities that are on the roadmap to be added to PingCentral in a similar centralized, self-service fashion.
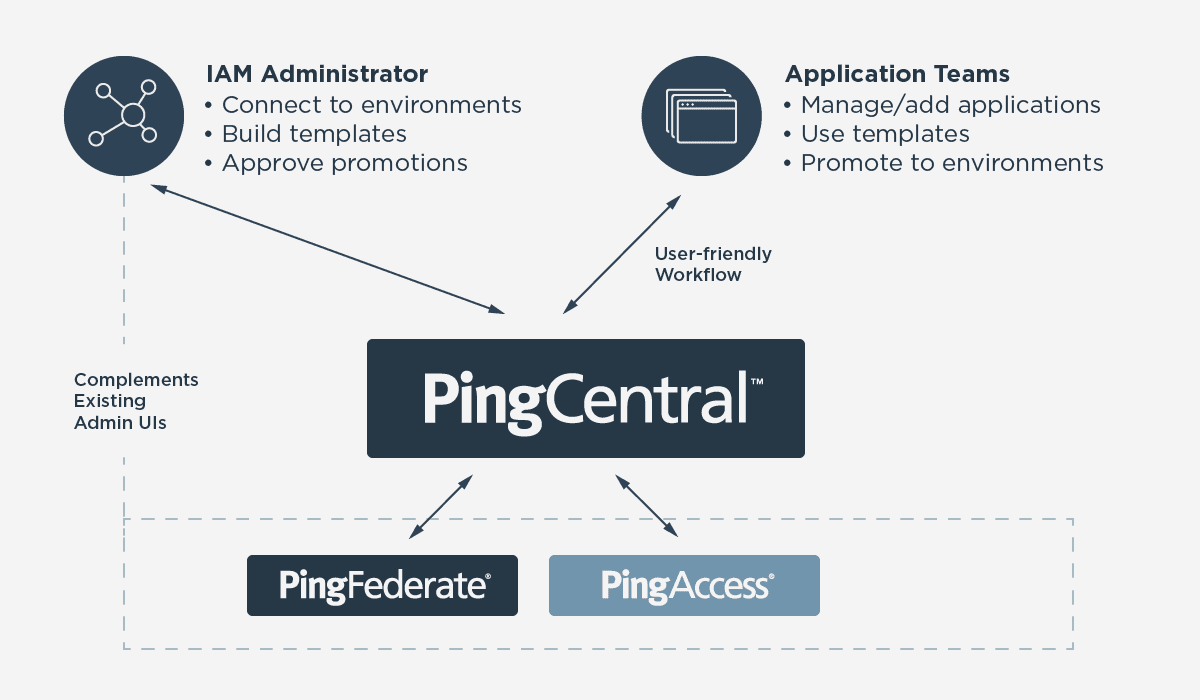
The next capability to be added in the first half of 2020 is authorization with PingAccess. The ability for business application teams to select and implement authorization policy templates will be another valuable step toward accelerating the rollout of centralized IAM services. On the roadmap for the second half of 2020 is PingDirectory. You’ll see services such as users, groups and password reset.
From the beginning, PingCentral provides self-service authentication and single sign-on, and in the future, it will be the single portal that provides self-service identity and access management.
Today, PingCentral is a game changer for your enterprise.
4 Ways Self-service Single Sign-on is a Game Changer
1. PingCentral Accelerates Digital Transformation with Rapid App Onboarding
Rolling out a new app can be a grueling process for enterprises, and authentication is one of the critical final steps to get an app launched. Many development teams are accustomed to waiting until an application or API is in a later development phase to get the identity security team involved. In other words, although they could have incorporated and tested the login and single sign-on functionality when the app was in the dev or QA environments, some app teams are waiting until the app is in the staging environment, just before it’s pushed to production. The main reason they are waiting so long is because their primary focus is on getting their app functionality right, and they’re putting off worrying about security until it’s critical.
PingCentral accelerates the rate at which new apps and APIs can get to market. Since it orchestrates and automates promotions among all instances of PingFederate in each environment tier in your DevOps pipeline, development teams will be encouraged to build and test authentication in their applications sooner in the development process, ultimately leading to a smoother launch from staging to production.
PingCentral also accelerates the rate of adoption and coverage of all existing applications and APIs. No matter where you are in your journey with PingFederate, PingCentral is the locomotive that powers and spreads central, modern authentication to cover all existing resources, especially those that are still relying on legacy SSO systems like Oracle Access Manager or CA Layer7 SiteMinder (formerly CA Single Sign-On).
2. PingCentral Bridges the IAM Knowledge Gap among Developers
Ping already has comprehensive developer admin APIs for the entire Ping Intelligent Identity platform. IAM-savvy developers often do just want access to these all-powerful administrative APIs to onboard and manage identity services for their own applications without having to go through an interface. But at Ping, we understand that not all app developers are equally confident about identity security and some don’t like dealing with OAuth, OIDC and SAML if they can help it.
That’s why we built PingCentral. It distills the full capabilities of our PingFederate admin APIs down to the lowest common denominator of information that needs to be exchanged to protect a resource with SSO. This way, app developers can help themselves according to your best practices without having to know the nitty-gritty details.
We believe that given the choice, most of your developers will gladly choose PingCentral. PingCentral also provides a “goldilocks option,” where developers can leverage PingCentral’s APIs instead of directly leveraging PingFederate’s APIs or using the PingCentral interface.
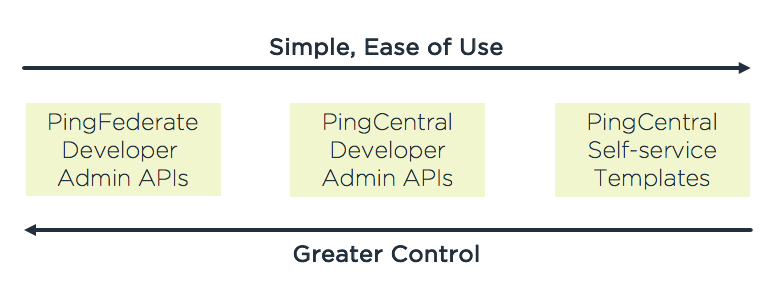
Legacy identity and access management companies don’t give developers a choice. CA Technologies’ Layer7 Siteminder (formerly CA Single Sign-On) has APIs for developers, and Oracle Access Manager also provides REST APIs for admin and end-user functions. The problem with the labyrinth of APIs provided with these legacy tools is that they require developers to have IAM expertise to make the right API calls.
PingCentral is our modern differentiator. It lets you meet your developers wherever they are on the spectrum of identity security knowledge, consuming central identity services in the most efficient way for each use case.
3. PingCentral Prevents Shadow IT and Technical Debt in Identity Security
Today, your enterprise may be dealing with a patchwork of different vendors or homegrown solutions for identity security, which isn’t ideal. In that situation, all systems outside of IT’s control pose a challenge and need to be replaced with modern identity and access management.
If your enterprise has attempted to centralize identity security by stretching a legacy IAM system, oftentimes IAM administrators aren’t able to keep up with requests for onboarding new apps or rotating client secrets. During delays, some app teams use outside vendors not approved by IT (shadow IT) or they roll their own security and go DIY with authentication, generating another login in either case.
With PingCentral’s simple-to-use interface and instant registration to receive client ID and secrets, there’s no delay and no need to look for solutions outside of central IAM. Some of our largest enterprise customers who built their own custom self-service portals* before PingCentral have seen a 10-fold increase in the number of resources protected by their central IAM infrastructure. This is a huge business impact—speeding the deployment of more revenue-generating applications and ensuring consistent SSO protection according to standard business policies.
*Sidenote: A common theme among the organizations who have built their own self-service tools is that they are freezing development of their own tools in favor of using PingCentral!
4. PingCentral Workflows Build a Bridge between Central IAM and App Teams
Want to see for yourself how easy PingCentral is to use? In this post, we’ll walk through three different workflows for 1) using a template, 2) promoting an app to an environment, and 3) creating a template.
Workflow #1: Application Admin: Using a Template to Add a Client
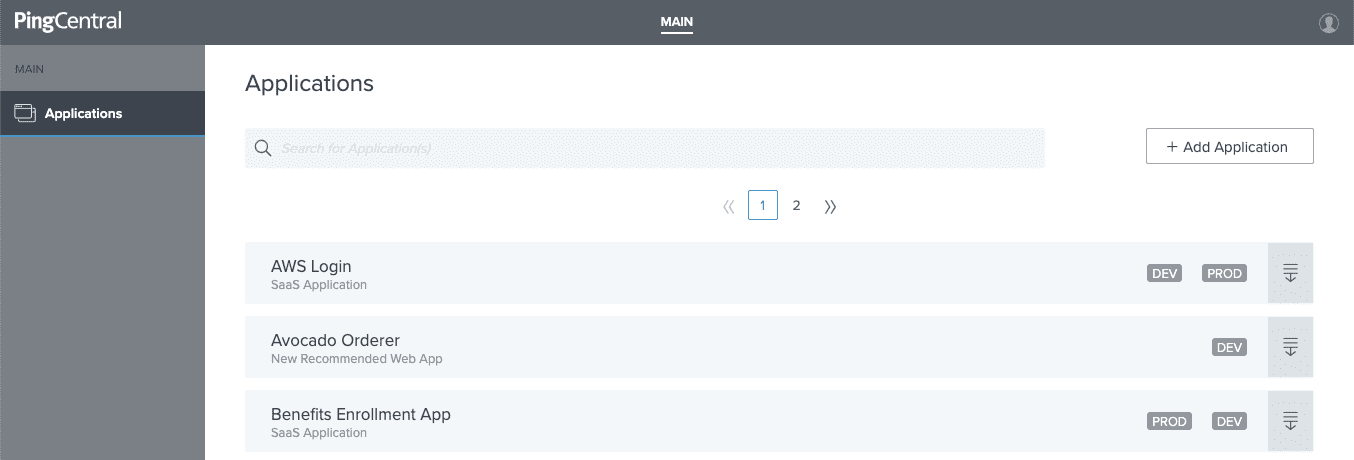
1. As an application owner, when you log into PingCentral, you see only the apps you have created or that have been assigned to you. To add an application, select “Add Application.”
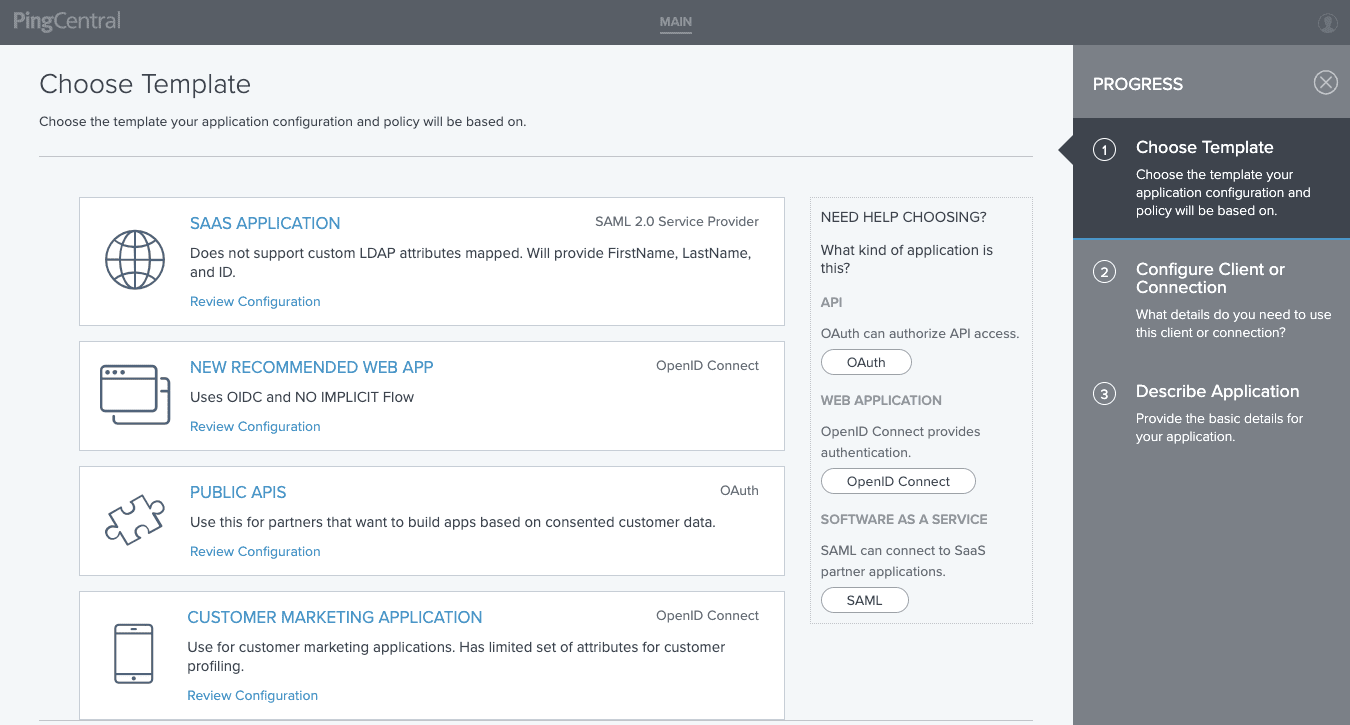
2. Choose a template based on the connection type (OAuth, OIDC, SAML). The IAM admin has made this really easy for you by adding titles, descriptions and icons for each template, so it’s easy to see which one makes the most sense.
For this example, let’s choose to add a SaaS Application with a SAML connection.
3. For a SAML app, conduct attribute mapping that is based on the associated/templated Policy Contract.
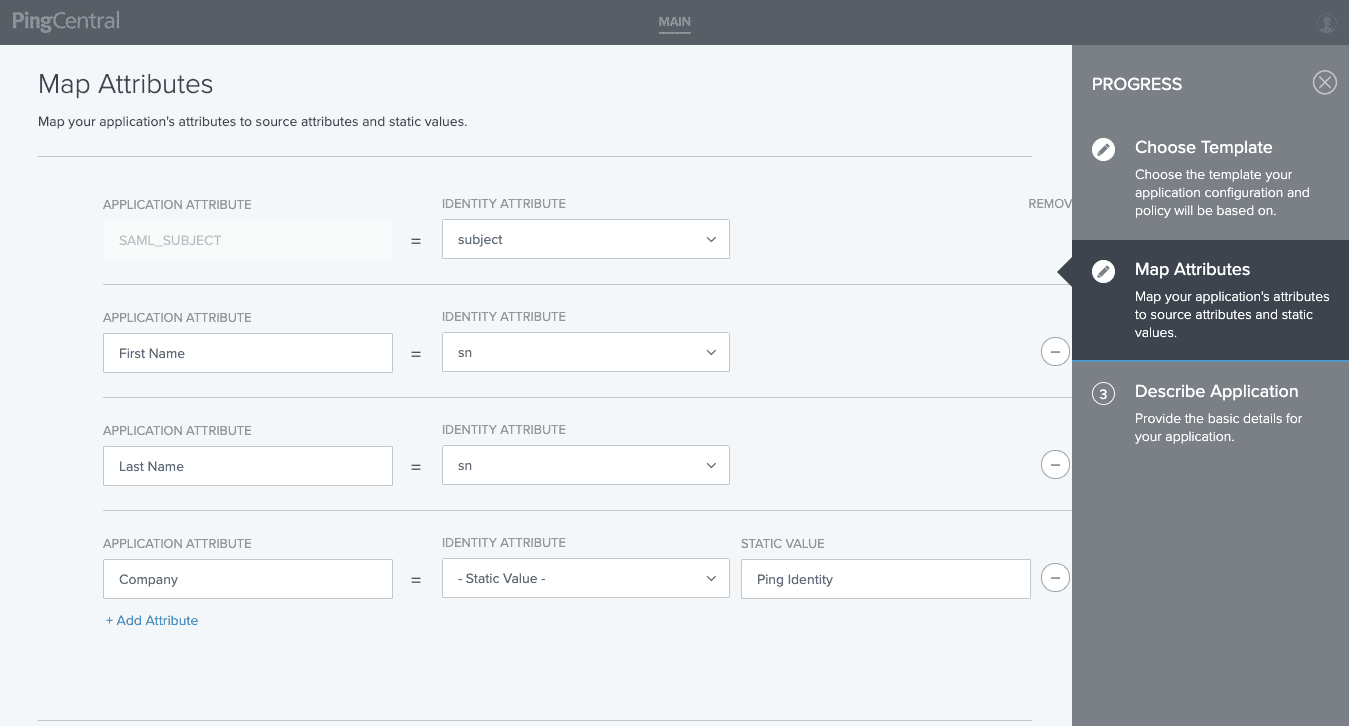
4. Add application name and description. Add the application owner’s names. Hit Save.
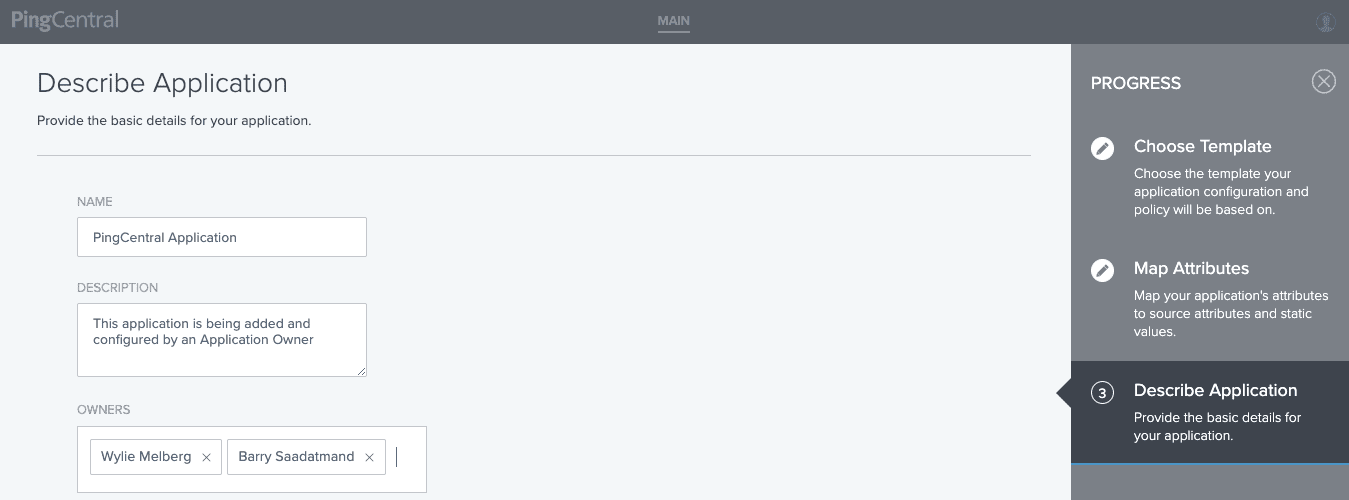
The application has been added within in PingCentral.
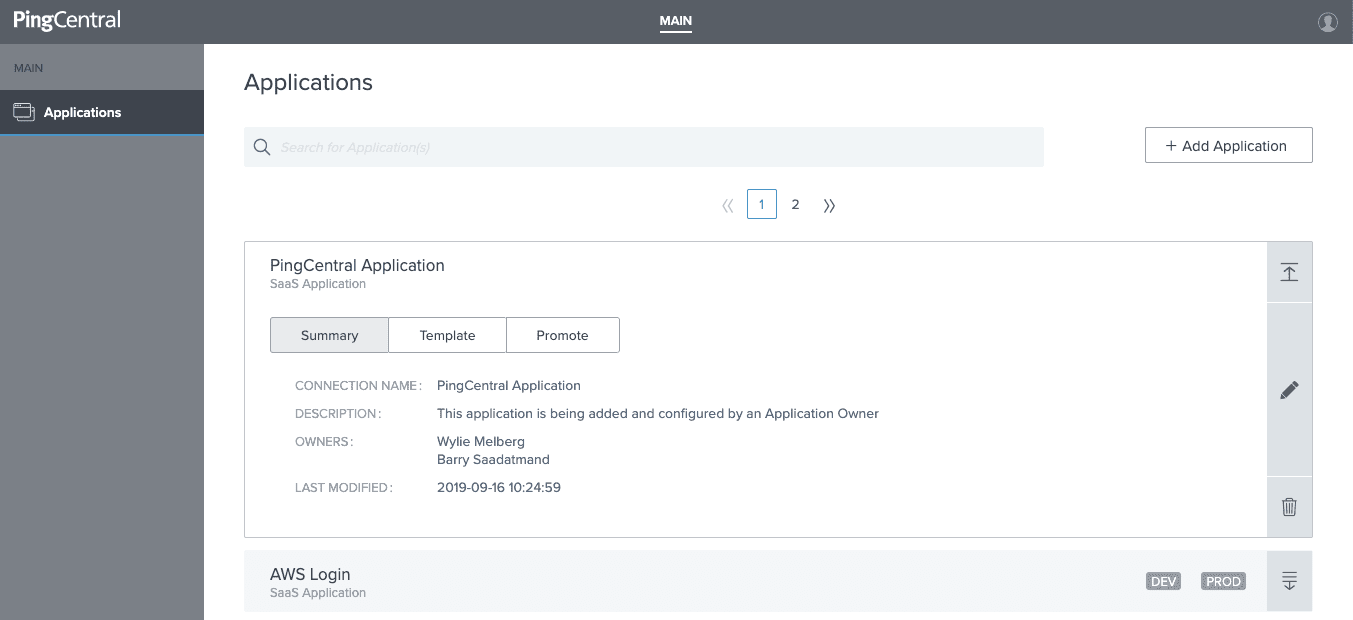
Workflow #2: Application Admin: Promoting Your Application to an Environment
1. Continuing with the SAML connection example we just walked through, after you create a new client or connection, the new application will automatically be at the top of the screen in edit mode.
You just choose the environment/s you would like to promote to.
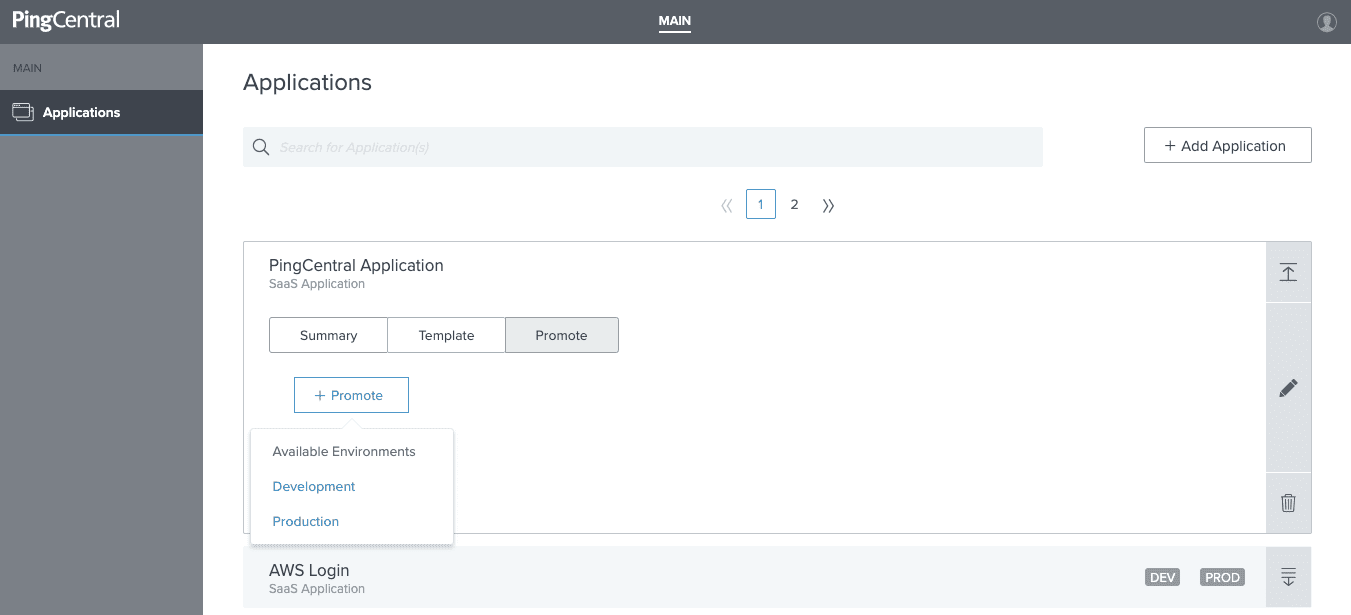
2. Provide the entity ID, ACS URL and SP cert (if applicable). Then you hit “promote” and it has been promoted to PingFederate.
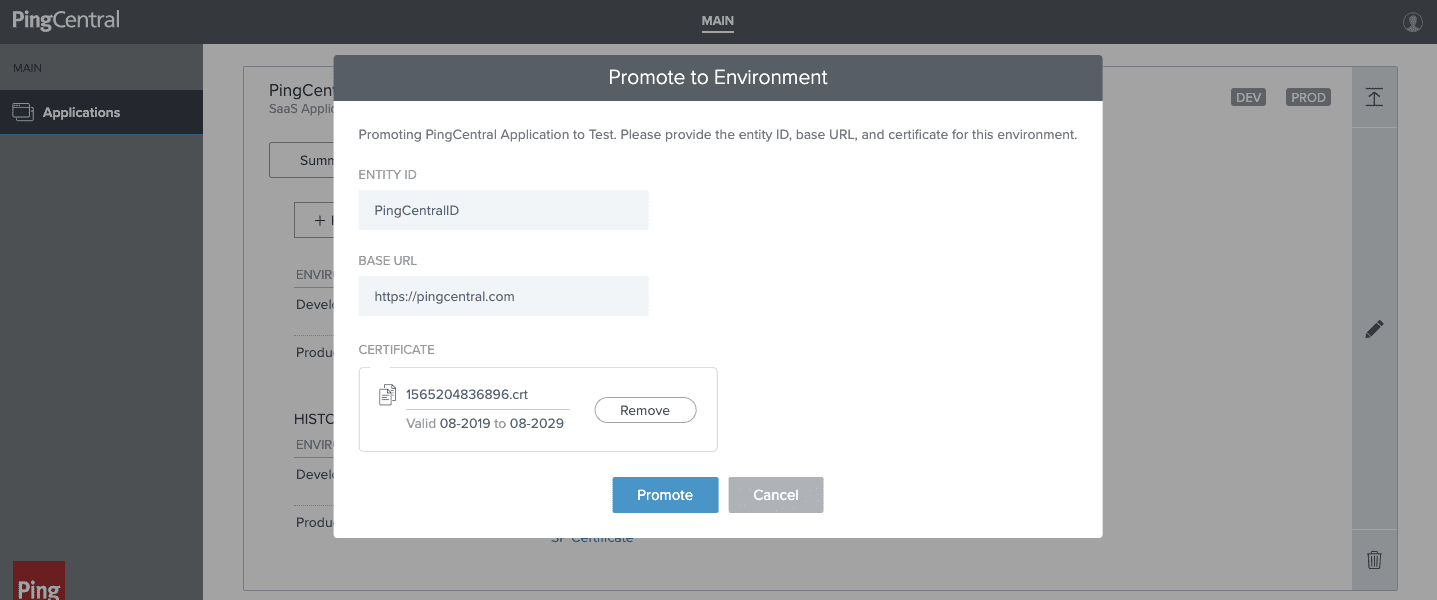
Boom. Game changed.
But how did that template get there for the application owner to use in the first place?
Workflow #3: IAM Admin: Creating a Template
Let’s take a look at how the IAM administrator uses an easy template builder interface in PingCentral to create a set of standard templates that make the delegated admin’s job super easy, while also limiting risk.
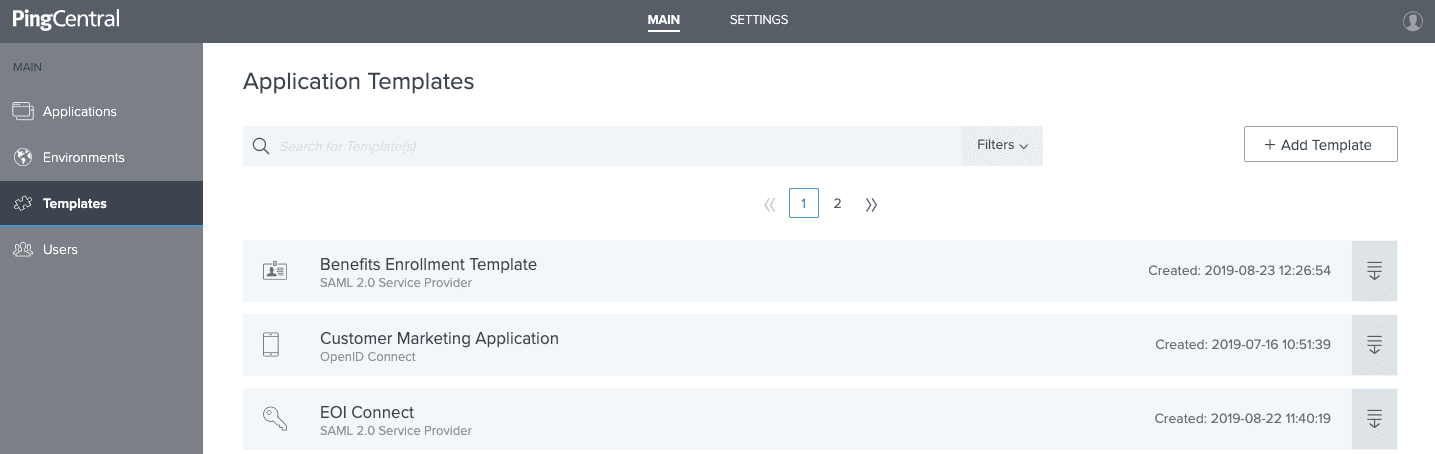
1. First off, you can see that the IAM admin has additional main menu options that the application admin doesn’t have, including environments, templates and users.
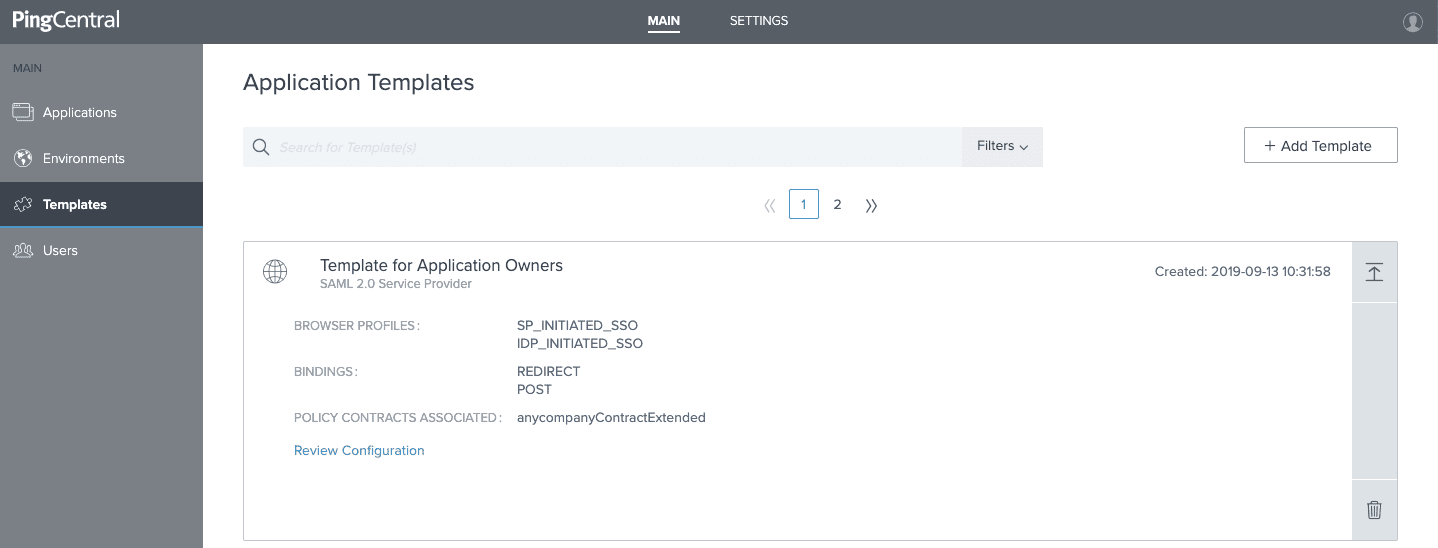
Add a new template from the Templates Screen.
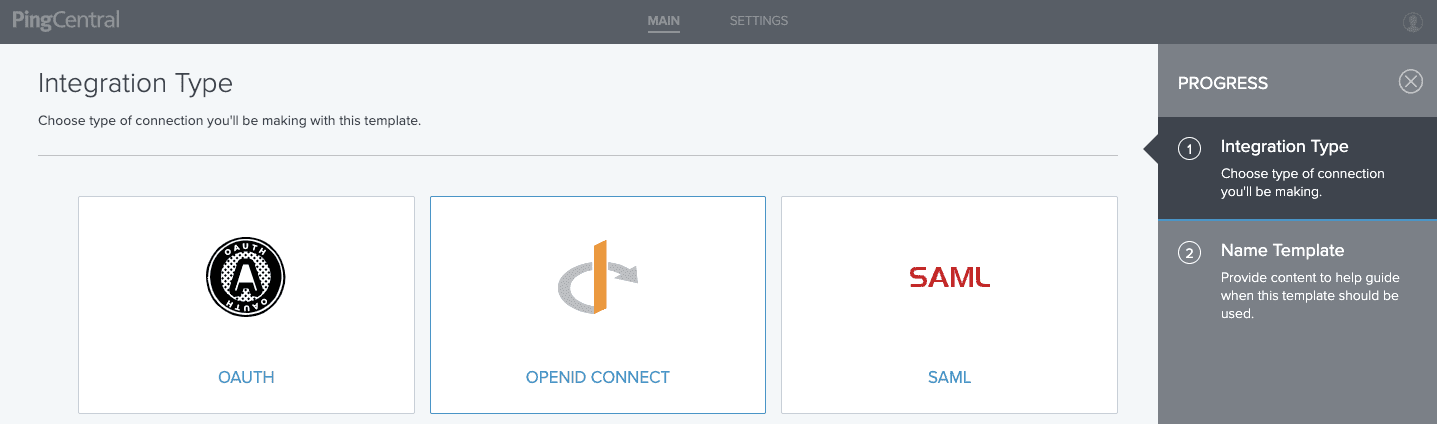
2. Select the Integration Type. For this post, let’s create a SAML template.
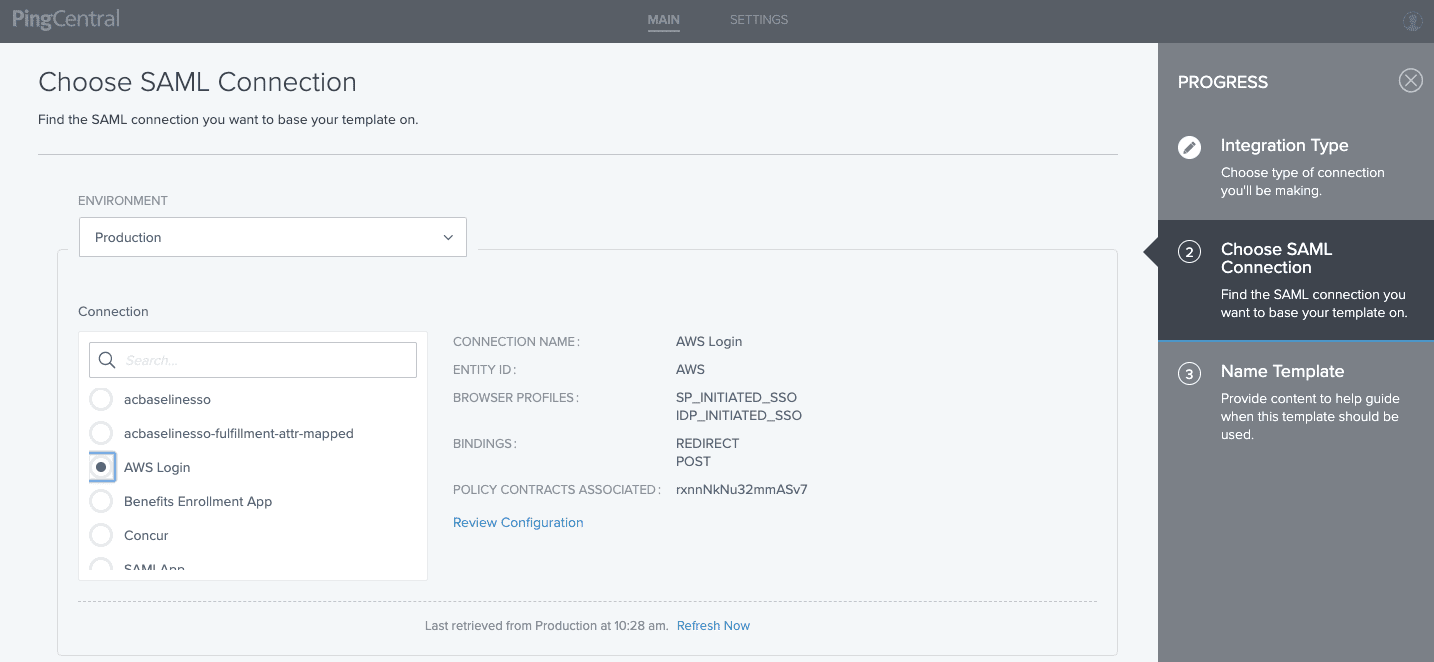
3. Select the Environment to indicate where you would like the configuration pulled from.

4. Choose the SAML Connection from PingFederate that you would like to use as the basis for a template.
5. Input the Template Name and Description, and select an icon that makes it visually easy for application owners to choose from among the templates available to them.
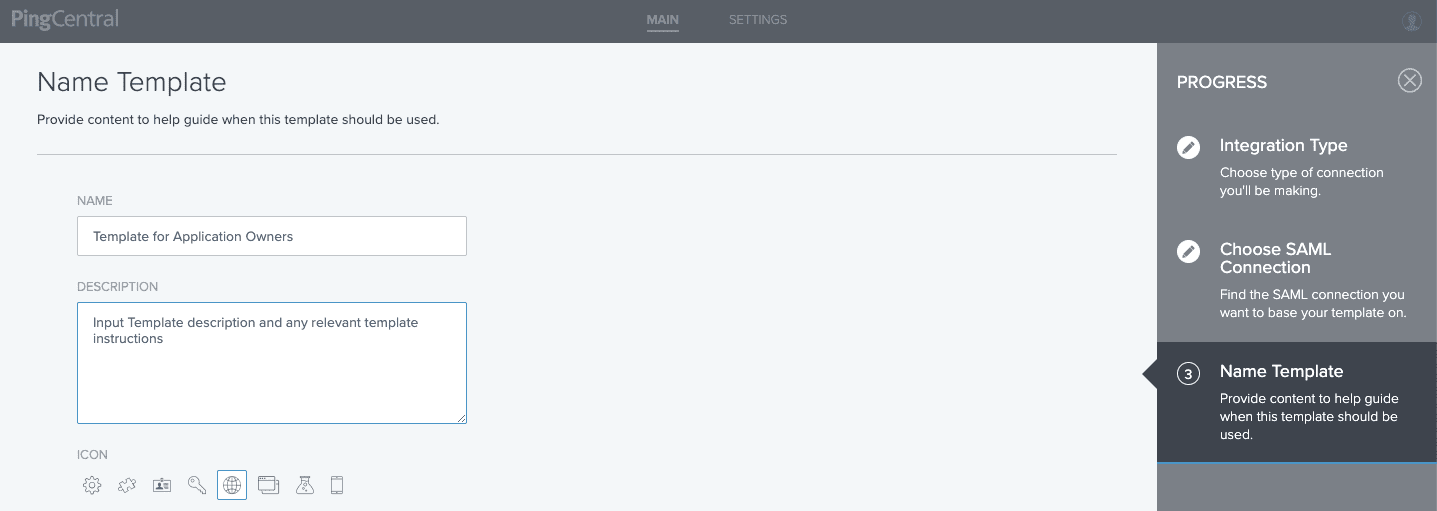
6. Save and Close. The template is now available for use by application owners and other administrators.
Learn More About PingCentral
You already know that modern identity and access management (IAM) is a valuable business driver for your enterprise. Now enabling self-service application integration for your business application teams allows IAM teams to do even more with less:
- Accelerate digital transformation with rapid app onboarding
- Bridge the IAM knowledge gap among developers
- Prevent shadow IT and technical debt in identity security
- Build a bridge between central IAM and app teams
Visit the PingCentral product webpage to learn more about how self-service IAM is a game changer for your business.


