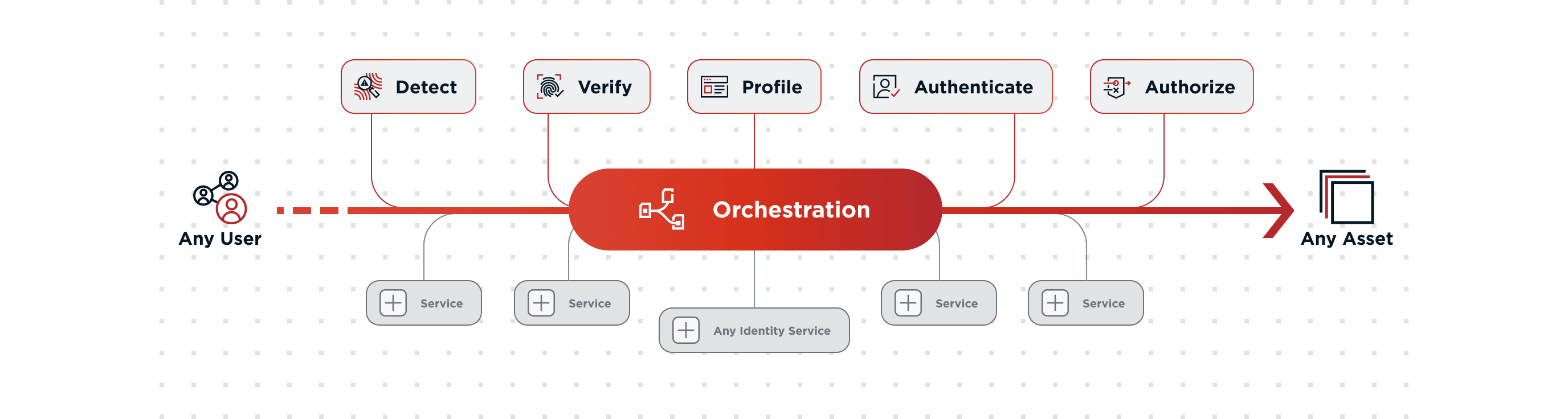
Identity orchestration has vast potential. It has the capability to stretch beyond identity and tackle any type of workflow across different applications and services. However, there are four significant business challenges where orchestration is already gaining traction:
These business challenges have a couple of attributes in common:
- They require a seamless user experience.
- No single solution exists, but rather a combination of multiple technologies and vendors must be tightly integrated.
- Nothing is set in stone—constant change and optimization are required.
Technology is a competitive advantage in the marketplace and as a result, it must be flexible to change. Orchestration enables businesses to adapt their technology to meet their user experience needs.
Passwordless
Perhaps the most effective way to deliver better security and a better experience to your users is via passwordless authentication. Users generally dislike entering passwords as it adds significant friction and frustration to the digital experience. Similarly, passwords come with weak security and remain a popular target for hackers.
Passwordless technology has evolved and is ready for mainstream adoption. However, organizations remain hesitant because of concerns about user rollout and ensuring coverage for all the different user scenarios and devices. But, orchestration provides a framework to deploy passwordless at scale with efficiency.
With an orchestration solution, organizations can easily test and optimize their passwordless rollout. Orchestration provides visibility into the actual user experience. You can also create rules and policies that support your unique user scenarios; for instance, rules for devices or backup authentication methods. Finally, you can integrate risk signaling to create a smarter, stronger, and more seamless authentication experience across the enterprise.
Registration
In the digital world, acquiring or converting a user often involves a registration flow or form. But, this ends up being a delicate double-edged sword. Why? When a customer shows interest in your brand, you want to be able to capture as much information as you can from them.
However, if you make that process too long or arduous, there’s a good chance they will abandon you for a competitor that offers a better user experience. As a result, organizations are constantly seeking to improve their registration experience as efficiently as possible. Orchestration provides the tool to optimize registration experiences in a few ways. For instance, you can live A/B test different registration processes. You can collect conversion data to see where users are dropping off. And, you can integrate services that make registration easier like social login.
To do this, you don’t have to collect all the user information at once, either. Instead, you can initiate ‘progressive profiling’ to collect information gradually. For instance, granting users access with limited information and asking for more information as they seek higher value services. The result is a more seamless user experience with more conversions and less friction.
24% of clients refuse to fill out checkout forms if there is a requirement for creating a user account. (Baymard Institute)
Fraud Prevention
Fraud is on the rise and comes in many forms: malicious bots, identity theft, payments, etc. The negative impact on revenue for companies is significant. Fraud prevention is thus a crowded space with many vendors solving different pain points.
Typically, organizations are deploying multiple fraud vendors. But integrating them can be difficult. Organizations also lack visibility of where and when the fraud checks occur in the user journey. Most importantly, they want to deploy a fraud solution but do not want to introduce friction to the user experience.
With orchestration, organizations can integrate and adapt fraud prevention capabilities to the user experience. Orchestration offers visibility into where and when fraud checks occur in the user journey. In doing so, organizations can fight fraud while providing consistency in an online experience, wherein security is weaved in thoughtfully.
Zero Trust
The Zero Trust movement has gained traction to the point where many security leaders view it more as marketing jargon versus a reality that can be delivered. That’s because like the initiatives we’ve already covered, Zero Trust requires an orchestrated ecosystem of numerous vendors and solutions. Identity is a foundational aspect of Zero Trust as it’s essential first to authenticate the user and the device they’re using.
Identity orchestration can enable Zero Trust initiatives to finally reach their potential by allowing for closer coupling of various security technologies. This is because orchestration lets you see how the various tools—i.e., multi-factor authentication, mobile device management, network segmentation, authorization, etc.—are incorporated across the user journey. This enables organizations to identify what security gaps may exist, but also where there is too much security tooling in place.
User experience is one of the most overlooked aspects of Zero Trust. Organizations are investing in Zero Trust to combat modern threats and enable their business and increase productivity. By placing a greater emphasis on the user experience through identity orchestration, perhaps Zero Trust projects can finally reach their full potential.
Other User Experiences
Interactive Voice Response (IVR) & Helpdesk
Customers don’t enjoy calling helpdesks due to long wait times and the numerous steps required to verify their identity. Interactive Voice Response (IRV) offers a quick, automated way to authenticate a user and solve their inquiry. Identity orchestration ensures the right security checks are performed and can integrate numerous applications and services.
“Lazy” Migration
A common identity use case is organizations seeking to migrate users from a legacy, on-premise directory to a cloud directory. However, they don’t want to make a “big bang” migration that could cause downtime or potential errors at scale. With identity orchestration, enterprises can perform “just in time” (JIT) migration when a user logs in with zero downtime.
A/B Testing
We’ve discussed A/B testing related to other initiatives already, but it deserves to stand on its own—especially in a customer identity environment. Brands constantly seek to optimize their user experiences and need a quick way to test the user experience. With orchestration, organizations now have opportunities to test customer security experiences thoroughly.