Overview
PingIntelligence for APIs is an award-winning software solution that provides deep visibility into API traffic, discovers APIs automatically, provides AI-powered automated API attack detection and blocking, and uses decoy/honeypot environments to identify hacking in real time.
Attacks on API services can come from outsiders, such as hackers and bots, or from insiders. Sometimes the hacker looks like an insider, and attacks may be malicious or not. For example, a system malfunction may affect another system via its API through what is known as friendly fire.
There are many different types of attacks to defend against, and PingIntelligence for APIs can detect them regardless of origin or intent. PingIntelligence works by inspecting API traffic between every device and the applications and data services accessed via the API to deliver deep knowledge on how each API is accessed and used.
Combine strong API behavior analytics with security expertise and data science
- Identify good and bad API traffic with advanced mathematical modeling.
- Utilize self-learning to save security analysts from having to write or update rules.
- Adapt automatically to changing environments.
Gain rich API traffic visibility, forensics and compliance reporting
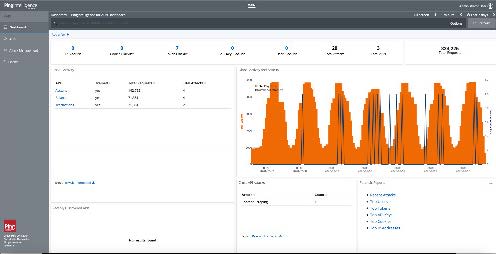
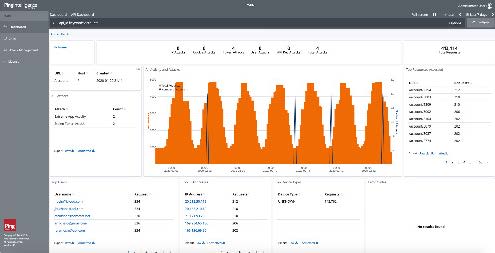
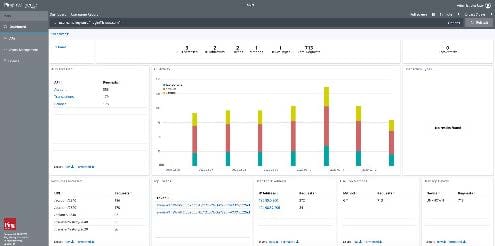
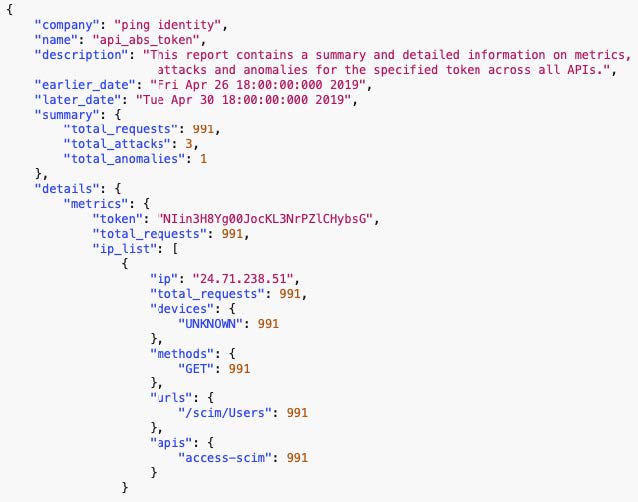
- Obtain unique insight into API activity with dashboards and in-depth reporting for each API.
- Automatically identify the APIs in your infrastructure.
- Accelerate gathering of evidence after an attack to expose all activity.
- Simplify investigations and track compliance with optimized reports.
Stop API cyberattacks with threat detection and automated blocking
- Detect hackers instantly with API-based deception.
- Automatically discover malicious activity by bots, external hackers and insiders.
- Terminate identified attacks automatically across all nodes and API gateways.
Preserve investments in API infrastructures
- Deploy within existing API infrastructures, including APIs on application servers or in API gateways.
- Integrate with all popular API gateways for “drop-in” deployments.
- Deliver security and visibility unification across all API gateways and APIs.
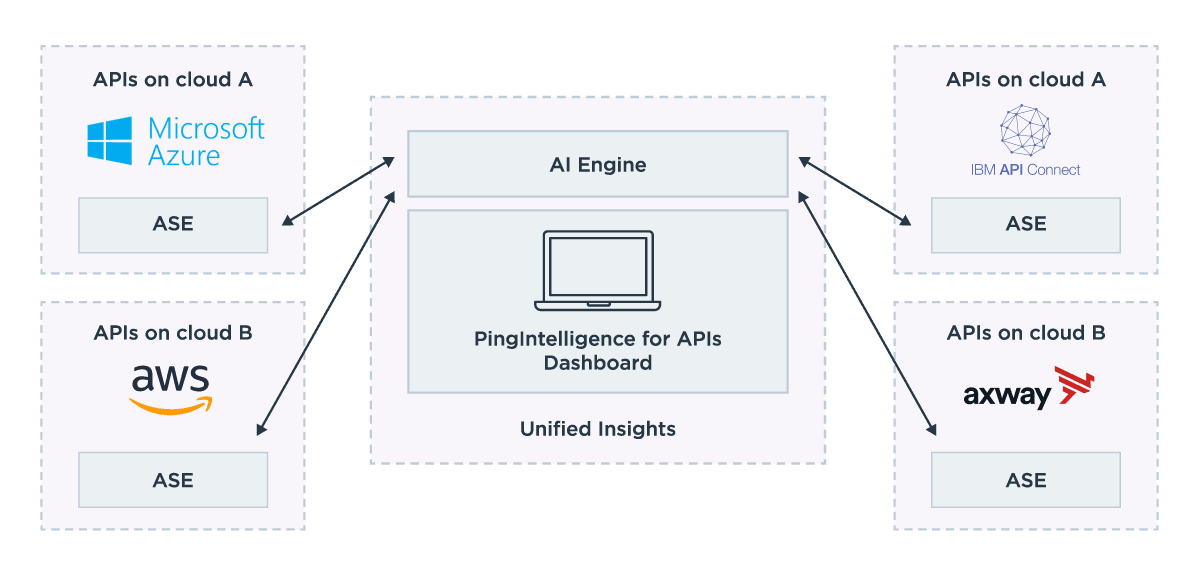
PingIntelligence for APIs combines real-time security and AI analytics to detect, report and block cyberattacks on data and applications exposed via APIs. Its artificial intelligence engine brings cyberattack protection and deep insight into API activity to existing API gateways and API management platforms, as well as APIs implemented directly on App Servers, such as Node.JS, WebLogic, Tomcat or WebSphere.
PingIntelligence provides automated AI-powered cybersecurity, including these specific capabilities:
- API auto-discovery of all active APIs.
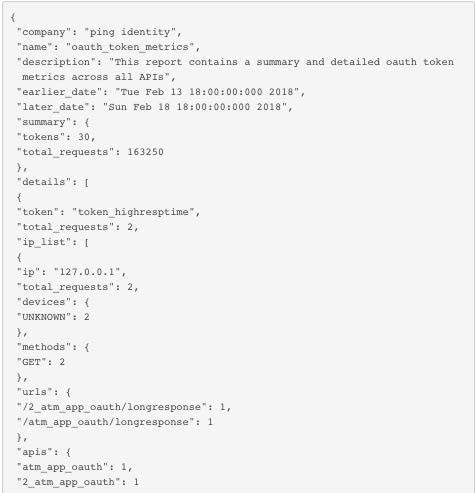
- API activity audit trails for deep insight, compliance and forensic reports.
- Identification of cyberattacks on APIs and data/systems.
- API deception to instantly detect hacking.
- Automatic blocking of API threats.
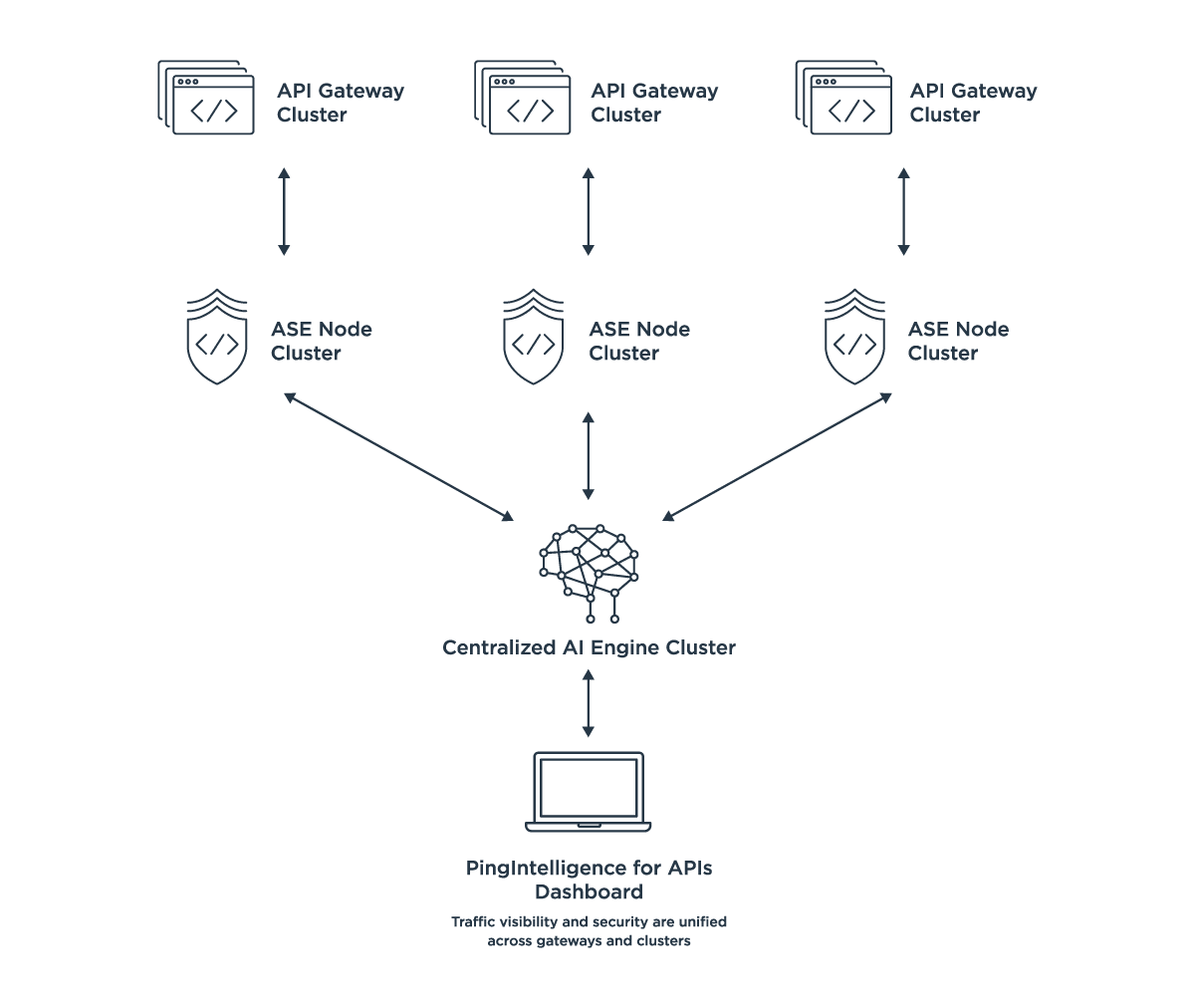
PingIntelligence can be deployed in hybrid clouds, public clouds and on premises. This self-learning solution requires no signatures, security rules or policies to write and is optimized for REST and WebSocket APIs. Because it does not depend on rules or knowledge of attack patterns, it can catch attacks that are new or changing. PingIntelligence for APIs consists of two core components:
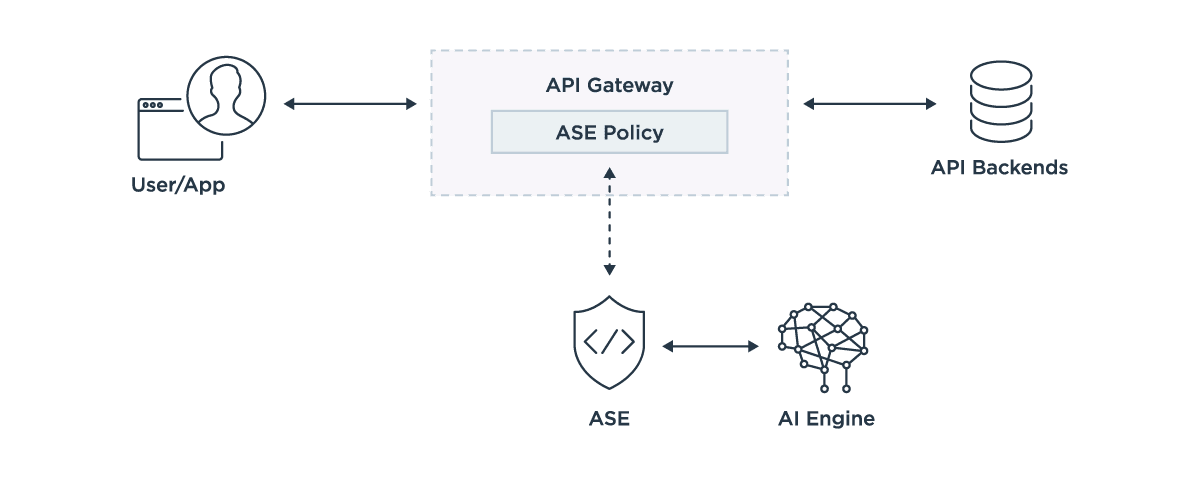
API Security Enforcer (ASE)
With both inline and sideband deployment options, ASE deployments support the best fit for an organization’s API architecture. An inline configuration offers a high-performance reverse proxy to protect APIs deployed on API gateways or directly on application servers. A sideband configuration works with API gateways and/or PingAccess to provide the same AI-powered attack detection and comprehensive insight, without requiring network or infrastructure modifications. Both options can be deployed in clusters and launched on demand when auto-scaling.
AI Engine
The execution of AI algorithms detects in near real-time any cyberattacks targeting data, applications and systems via APIs. Attack information is automatically provided to all ASEs (or other systems) to block ongoing breaches directly or via the API gateway, as well as prevent reconnection. AI Engine can be deployed in clusters and added on demand to address capacity needs.
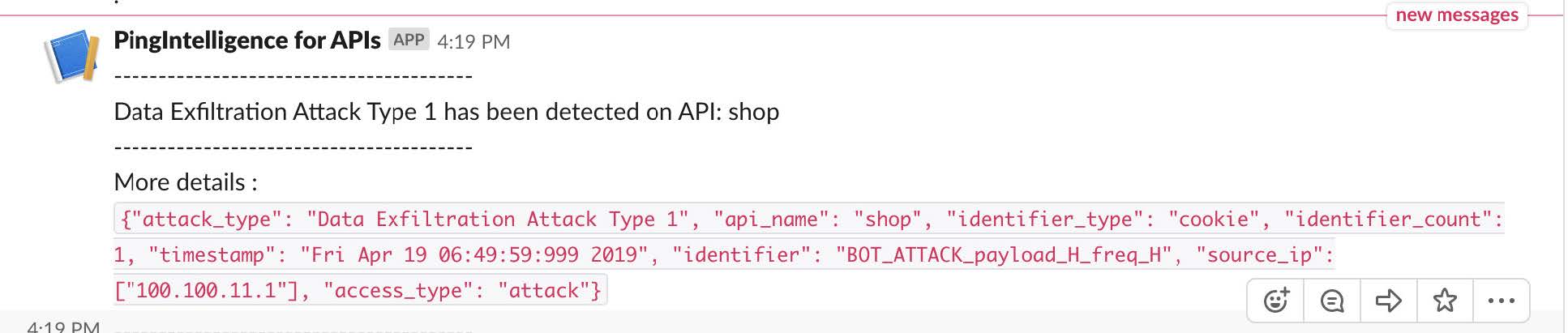
PingIntelligence for APIs’ AI engine uses specialized algorithms to inspect and track all API sessions’ metadata, including client information, API information and request/response flows. The AI engine continuously looks for abnormal behavior and can identify stolen tokens/cookies, data exfiltration and other types of advanced API attacks missed by traditional API security tools.
PingIntelligence identifies attacks that go undetected by traditional security solutions, including WAFs, such as zeroday attacks and attacks from users with valid credentials. These attacks—which represent over 90% of attacks on API infrastructures—may include account takeover attacks, data theft attacks, data manipulation attacks, attacks with stolen tokens, DoS/DDoS attacks on APIs that stay below gateway rate limits, attacks that reverse engineer the API to identify vulnerabilities and get to data, fuzzing attacks and others.
Unlike traditional security platforms, the AI engine automatically learns expected traffic behavior across API environments and does so on a per-API basis. When an attack is detected, it instructs all API gateways and/or PingAccess to start blocking the requester. PingIntelligence works across your APIs, regardless of which tool is used for issuing tokens and managing identities, effectively providing an additional security layer on top of your foundational API security infrastructure.
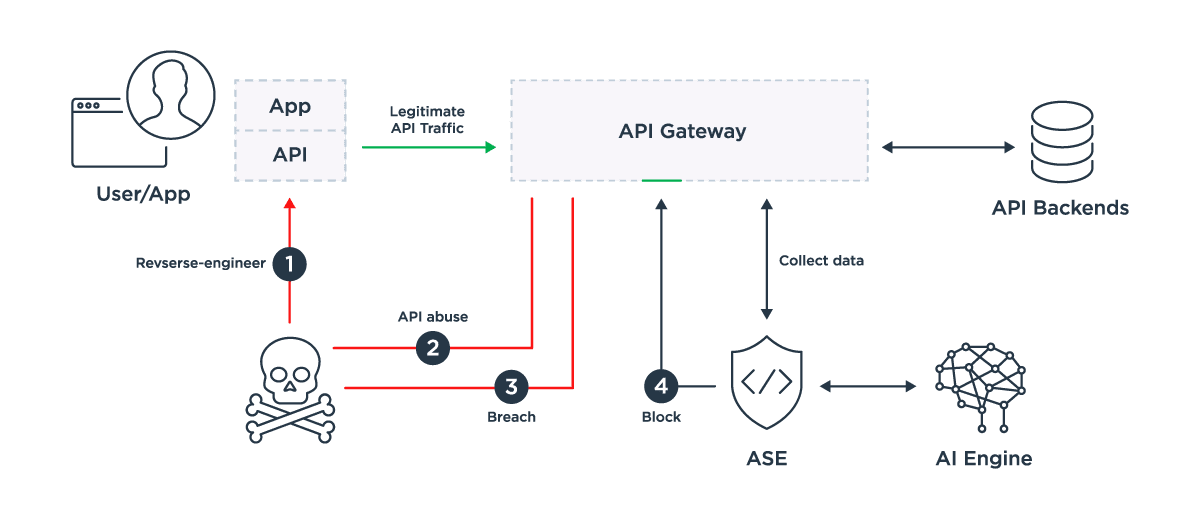
The ASE forwards API traffic metadata from the Gateway into the AI Engine and blocks information from the AI engine to the API gateway.
1. Hacker reverse-engineers API to use it outside the app.
2. Hacker uses the API in unintended ways to find vulnerabilities.
3. Private data breaches through the API gateway.
4. AI Engine detects anomaly and instructs API Security Enforcer (ASE) to block source of traffic. ASE passes this blocking information on the API gateway thus stopping the attack.