Introduction
"Trust no one, Suspect Everyone"
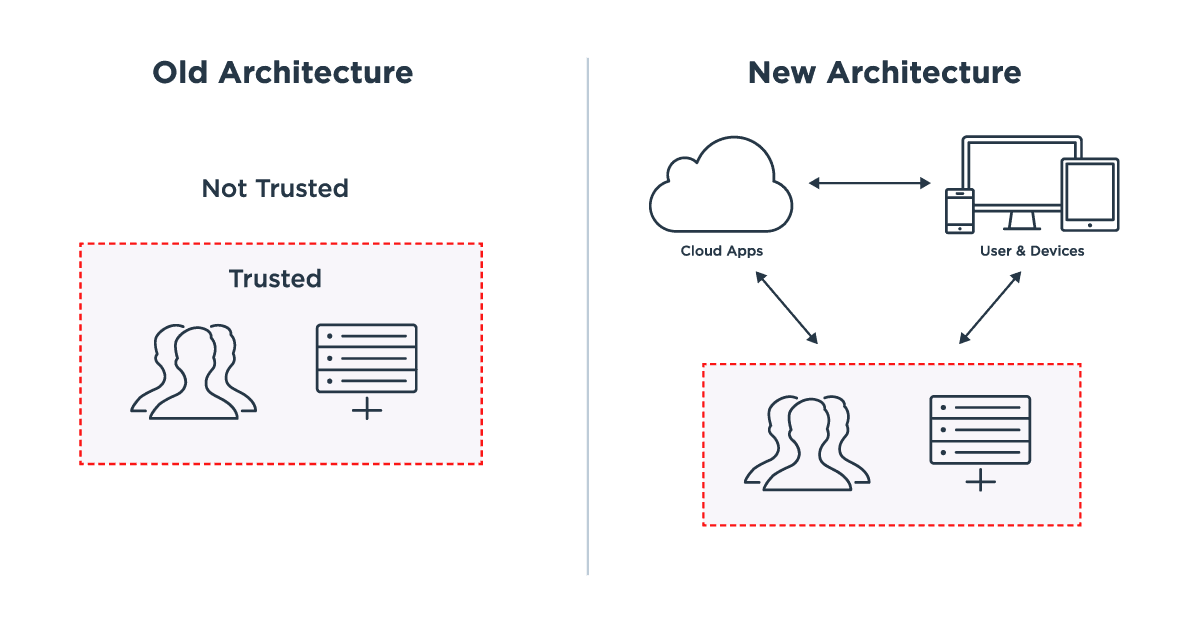
More than just a Cold War cinematic catchphrase,1 this mantra is a way of life for the security leaders of today. Security pros increasingly are adhering to the zero trust model,2 which is based on the philosophy that there should be no implicit trust in a corporate network. As users and devices go mobile and apps move to the cloud, leading enterprises now build networks on the assumption that anyone could be on the network at any time, and they deny open access to corporate resources residing inside those networks.
The old paradigm of a perimeter-based security approach is being replaced by a new one based on zero trust—and it’s a zero trust model with identity at its core.
“Where today’s security approaches fail to protect data, Zero Trust is the best, most modern way to keep your network secure.”3
- John Kindervag, VP and Principal Analyst at Forrester
Google is one such organization that has moved in this direction. Its BeyondCorp program, which Google began developing more than six years ago, demonstrates a security model that:
- Puts user identity at its center.
- Does not rely on the traditional firewall perimeter with VPN.
- Allows convenient and secure access to resources.
- Provides the highest possible level of security assurance.
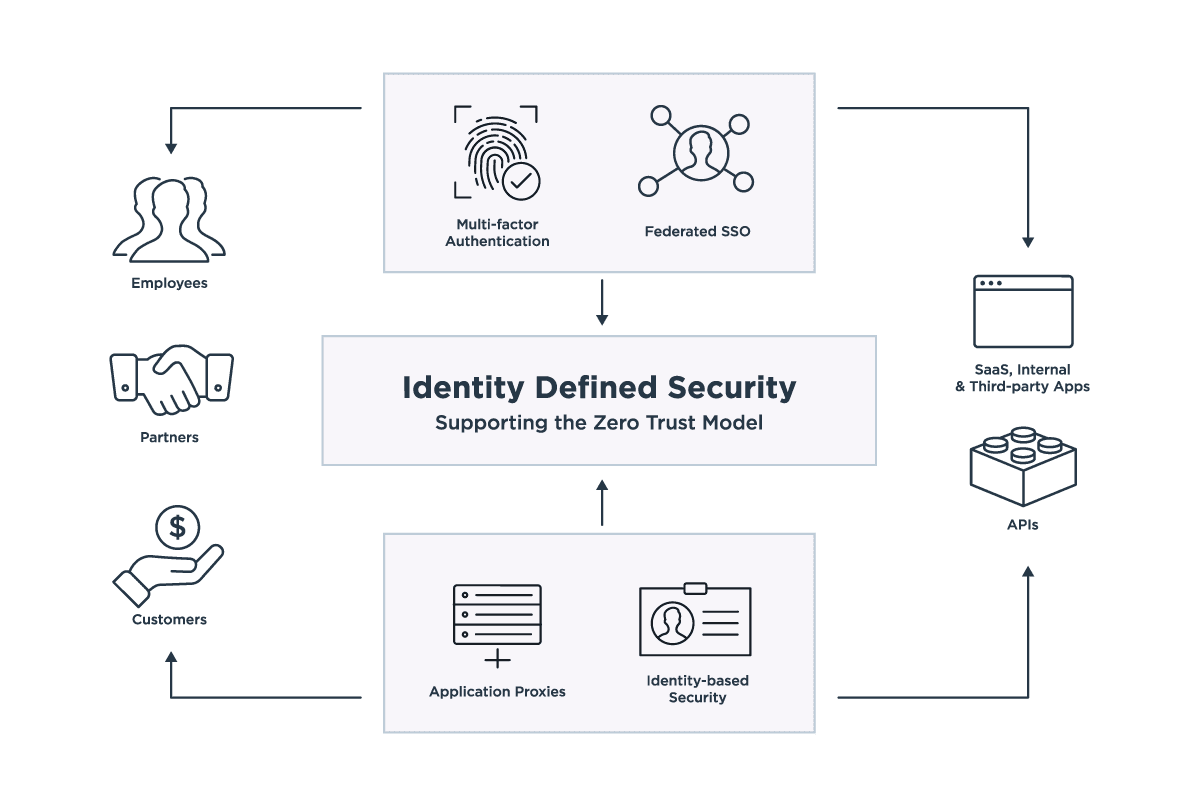
As the zero trust model becomes more widely adopted, security leaders are implementing identity and access management (IAM) controls that grant users access to the network from anywhere while still maintaining tight, centralized security. This is what is known as Identity Defined Security: a security architecture based on identity.
So how do you go about creating a zero trust model built upon an Identity Defined Security architecture? By keeping four principles in mind.