- EBOOK -
CIO's Guide to Modern Identity
As the enterprise continues to open and perimeters disappear, the CIO has an opportunity to play an increasingly strategic role in enterprise growth. The ability to deliver secure, frictionless and fluid access to services across the cloud, mobile and social will open new revenue opportunities.
Modern identity holds the key to delivering the convenient access users demand, and the security necessary to protect critical data and infrastructure. Here, we explore five key trends facing CIOs today, and how your ability to respond with the right identity infrastructure will make or break your business.
Identity is the New Perimeter
5 Trends Facing CIOs Today
Cloud
Mobile
Omnichannel
Internet
of Everything
Expanded
Access
Long gone are the days of all on-premises software, where proprietary applications were accessed from within the confines of the corporate firewall over computers issued by the organization, or by consumers from a single web access point. Yet, many enterprises continue employing a traditional security model; assuming a firewall is enough to shield their important assets from outside threats.
However, because cloud and mobile are now everywhere in today’s enterprises, the concepts of ‘inside’ and ‘outside’ have become considerably blurred. With employees, partners and customers accessing sensitive data from insecure networks and mobile devices, the new security paradigm must protect users and data regardless of their location or device.
The intersection of mobile, social and cloud offers unprecedented visibility and opportunities for the enterprise, but has also created an environment with multiple (and increasing), disparate user identities across touch points—placing additional barriers between your users and the applications they need to access. Security that specifically targets endpoints, cloud, networks and email is not equipped to cope with the array of devices, systems and workflows that even the most progressive enterprises wouldn’t have dreamed of a few years ago. Identity is emerging as a silver bullet for CIOs looking to keep their corporate data safe, drive business agility and improve end users’ experiences across their ecosystem.

Cloud
Warning: Your Business Has Left the Building
The adoption of cloud-based applications has been explosive within enterprises over the past few years. This move to the cloud forces enterprises to rethink their identity and access management (IAM) strategy as security perimeters move beyond the firewall.
The growth in cloud-based apps and SaaS architectures is driven both by organizations seeking more efficient and effective ways to run their business while improving workforce productivity, as well as by well-meaning employees looking for better task proficiency via SaaS apps. But the trend cuts even deeper. According to the Forrester Research® 2014 predictions, “A great digital experience is no longer a nice-to-have; it’s a make-or-break point for your business as we more fully enter the digital age”.1
This fundamental shift of business to the cloud has many repercussions for security and compliance, such as:
- Traditional IAM systems weren't designed to secure applications outside of the corporate firewall.
- Password proliferation creates huge security risks as employees use either the same password for many systems, or use many passwords and have to write them down on things like sticky notes.
- The growth of unique sign-ons can also be a significant productivity drain as employees spend time dealing with finding, updating and reinstating passwords instead of on more industrious work.
The bottom line? In a borderless enterprise, identity is the strategic enabler ensuring the access users want with the security you need.
Identity Insider Tip:
By focusing on authenticating user identity versus protecting the endpoint, companies can enable secure access to any application from any device, anywhere. CIOs can use modern identity tools to add the word ‘anywhere’ to their authentication vocabulary. Look into extending your existing IAM stack with cloud-based services that can take users from any repository, attach them to any authentication/security infrastructure, and connect them to any application, regardless of where the systems and applications reside.
Mobile
Serve Your Employees and Customers — Wherever They May Go
Get ready for diversity because there won’t be a dominant mobile platform or vendor, but there will be a flood of new devices and applications. By 2016, each user will have three to five devices covering all shapes, sizes and abilities, with interfaces that range from touch/voice to keyboard/mouse to gestures. The enterprise mobile platform will be cloud-delivered, social-enabled, multi-channel, device-aware and device-agnostic. Distinct markets for mobile device management, security containers, file sync/share and other tools may fade into suites.
 Many enterprises have invested heavily in a security regime that works for web applications (typically a web access management [WAM] solution). While WAM solutions make internal web applications more secure, they don’t extend easily to secure APIs needed for native mobile applications and other web applications. Why does this matter? APIs represent a huge market opportunity for many companies and can drive significant revenue. But in a world where many sensitive and critical functions are increasingly deployed as services, and are exposed through web APIs, security posture around those APIs becomes mission critical. The best solution for managing access to APIs should have several key characteristics. They should:
Many enterprises have invested heavily in a security regime that works for web applications (typically a web access management [WAM] solution). While WAM solutions make internal web applications more secure, they don’t extend easily to secure APIs needed for native mobile applications and other web applications. Why does this matter? APIs represent a huge market opportunity for many companies and can drive significant revenue. But in a world where many sensitive and critical functions are increasingly deployed as services, and are exposed through web APIs, security posture around those APIs becomes mission critical. The best solution for managing access to APIs should have several key characteristics. They should:
- Replace or extend existing IAM infrastructure to secure web and APIs.
- Employ a standards-based approach that eliminates the need for local password storage on mobile devices.
- Use a proxy-based approach with a central policy server for both web and API access.
“Salesforce.com, for example, generates nearly 50 percent of its annual $3 billion in revenue through APIs; for Expedia, that figure is closer to 90 percent of $2 billion”. – Forbes2
Identity Insider Tip:
As you’re building out your strategy, industry standards will add tremendous value by ensuring a well-documented, proven and interoperable framework. Guard your enterprise against vendor lock-in and proprietary mechanisms by aligning with standards that will continue to evolve as requirements expand and new technologies become available.
Omnichannel
PSSST! Your Customers Hate Passwords Too
Many still argue about the difference between multichannel and omnichannel. So what’s in a name? At it’s simplest, multichannel has us embracing many different channels (such as mobile, web, etc.) to engage with customers. But if you’re just focused on the individual channel, you’re missing an opportunity. Enterprises initially got to multichannel by ‘bolting on' each new channel as the need arose, but omnichannel isn’t about which individual channel you engage your customer through. It’s about delivering a single, unified experience for your customer across every channel. An activity that begins in one channel should fluidly move to another, and another, until the customer’s business transaction is complete.
Of consumers change their passwords only once a year.3
Of consumers use five or fewer passwords.3
Of consumers felt that a single multi-purpose identity credential would be more convenient than the current password/username system.4
Of consumers are dissatisfied with current authentication methods.5
Where does identity fit in? What began as simple single sign-on (SSO) technology (easy access to all your internal and third-party applications through your web portal) has grown rapidly over the past decade. And it continues to accelerate with mass consumer adoption of mobile and the API economy. We used to just be concerned with how a customer moved through the web experience, but we now have to deliver to a fluid experience across all existing and future channels and consider how the authentication experience impacts the larger experience. The goal? Customers will be able to maintain states as they shift across different channels.
Internet of Everything
Everything's Connected. Is Your Business Ready?
If you’re still struggling to address the identities in your organization for cloud, mobile or social, you better brace yourself as another 30 billion ‘things’ come online in the next five to ten years. The Internet of Things (IoT) is basking in its nirvana stage. Thanks to the mobile Internet, adoption rates of IoT will soon accelerate. Industry pundits are predicting a multi-billion dollar industry fueled by billions of connected devices that will support better business and make life more efficient and pleasurable for individuals.
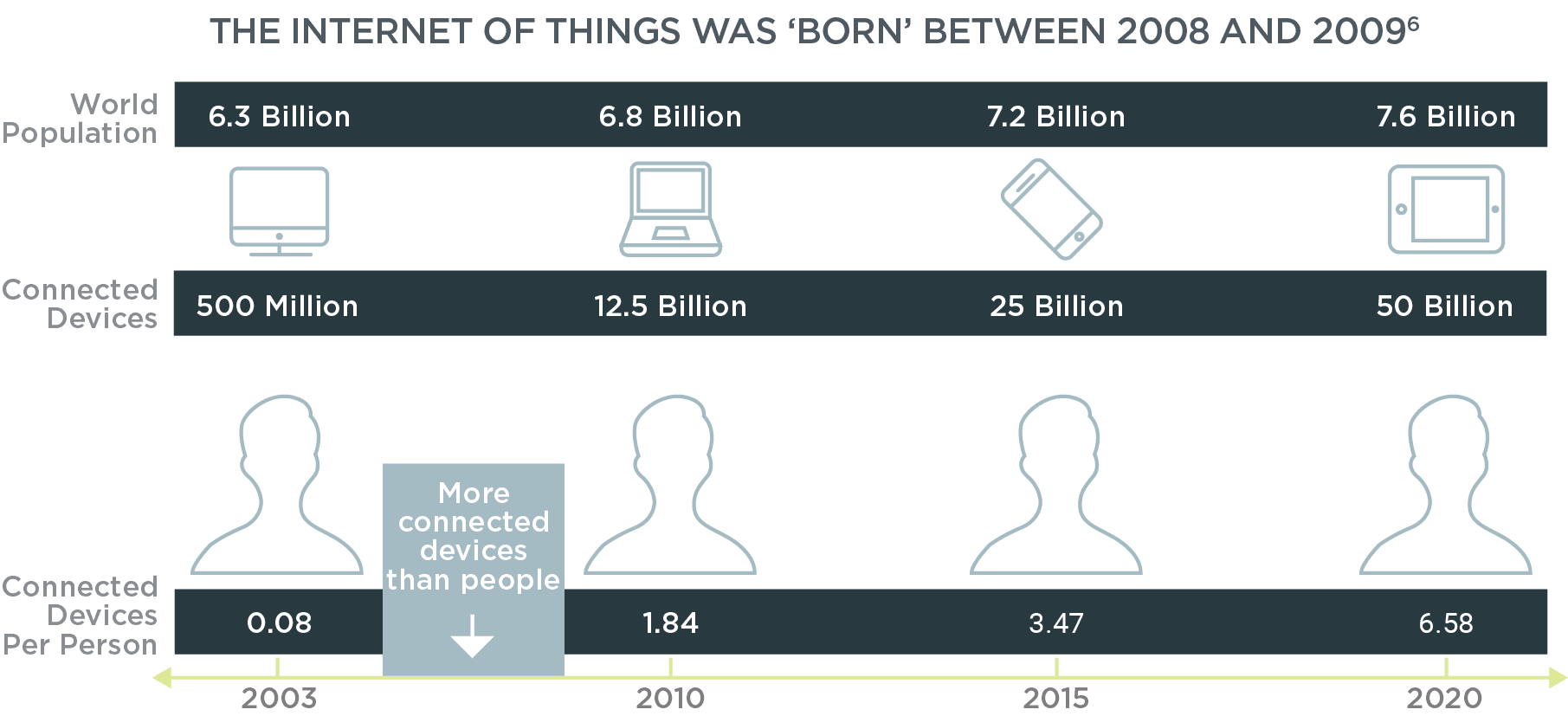
The possibilities for positive business impact are monumental, as are the challenges associated with building such an interconnected world, including security architectures, bandwidth, IP addressing, standardized communication protocols, management consoles, certificate management, power consumption, privacy and identity. Why identity? In order to query or connect to any ‘thing,’ that thing will have to possess an identity of some sort. A smartphone has relevance as a device, but its value skyrockets when it's identified as a particular user, and gets even better when it can be associated with their other things. An HVAC provides an even indoor temperature, but it needs to identify itself to participate in an ecosystem of things. Identity forms the bedrock for the relationships between things, such as pieces of equipment on a shop floor, a sensor or a device.
Identity Insider Tip:
Focus on these three key identity concepts, which can be applied across any organization, to help achieve the promise of delivering a single, unified experience.
People, things, information and places. There’s value in all that connectivity, and architecture will matter. ‘Manage’, ‘monetize’, ‘operate’ and ‘extend’ will frame CIOs thinking. Application logic, data and analytics will be put anywhere–the network edge, gateways, clouds and in the enterprise. CIOs will need to evaluate business processes to discover where the opportunities lie.
Expanded Access in a Federated World
In Today's World, You Don't Win by Working Alone
Today’s connected enterprises rely upon partners across their supply chain to integrate services for customer-level interaction, or to take advantage of an extended workforce that's not exclusively composed of full-time employees. The economy is global and partners are on the critical path to sustainable and profitable growth.
Partners expect seamless, anytime-anywhere access to critical, internal applications and data. This leaves the enterprise with an exorbitant number of users (external identities for every partner or customer) that must be provisioned (and de-provisioned) with the right access, despite the enterprise’s lack of ownership or influence over those partner identities. Managing external identities and partner access not only places a significant burden on IT, it often opens the enterprise up to security breaches.
A federated approach to IAM ensures that you can provide the access partners need without assuming the complexity, cost and risk associated with managing those identities locally.
Your security is only as strong as your weakest link. Focus on these four elements for securing partner access:
-
Unified management in a central identity authority
-
Self-service with user driven onboarding experience
-
Control and visibility through zero-day provisioning
-
Strong access policies that employ strong MFA
"The Target breach was initiated through the compromise of one of the retailer’s service providers, a small HVAC company in PA... the notion of a network perimeter is ancient history." – Network World7
Key Takeaways
These days, IAM is a moving target being moved by the forces of cloud, mobile and increasingly connected consumers. By keeping these five trends in mind, and understanding the security and access control needs of your enterprise, you can make decisions that'll benefit you today, while providing a good foundation for future evolution. As you look toward what a modern identity management solution looks like for you, there are three key actions to focus on that will help guide your move to Identity Defined Security:
- Consolidate authentication as a separate service.
- SSO-enable your apps to take advantage of consolidated authentication.
- Replace passwords with a strong authentication service.
Why Choose Ping?
- We don’t force you to compromise security. Your IT team retains control over access to apps/data without replicating identities in the cloud.
- The Ping Identity Platform spans the cloud and data centers. Choose cloud SSO, on-premises SSO or both; whatever is best for your business.
- Our solutions easily integrate with your existing infrastructure. Working with your existing systems saves you time, frustration and money.
Sources:
1 Forrester Research®: Predictions 2014: Mobility And Computing Technologies In The Age Of The Customer, January 15, 2014 By J.P. Gownder with Christopher Voce, Katherine Williamson
2 Forbes, CIO Network, Ready for APIs? Three Steps to unlock the fata economy’s most promising channel, by contributor McKinsey & Company, January 2014
3 CSIDTM , Consumer Survey: Password Habits, September 2012
4 Ponemon Institute, Moving Beyond Passwords: Consumer Attitudes on Online Authentication, April 2013
5 Nuance, Surveys Show: Consumers Ready to Say Goodbye to PINs, Passwords, and Probing, May 2013
6 Stratecast, Frost and Sullivan, The Hidden Truth Behind Shadow IT: Six trends impacting your security posture, an executive brief sponsored by McAfee, November 2013
7 NetworkWorld, Lessons Learned from the Target Breach, by Jon Oltsik, March 2014
Start Today
See how Ping can help you deliver secure employee and customer experiences in a rapidly evolving digital world.
Request a free demo
Thank you! Keep an eye on your inbox. We’ll be in touch soon.