3 Ways Securing Your APIs Just Got Easier
Keeping up with hackers is a time-consuming business. Those with malicious intent always seem to be a step ahead—or at least close behind—the latest vulnerabilities.
Because of the access to data and application functionality they provide, APIs hold the potential to be the chink in your security armor. And API security best practices are increasingly under review as a result.
Vulnerabilities made public by internal security teams, third-party analysts, white hats and malicious actors alike often kick off a reevaluation of certain security approaches. Organizations have spent hours, days and even months setting and adjusting rate limits, reconfiguring permissions and scopes, rotating keys, and more in response to the recent barrage of high-profile API related breaches. And with more APIs introduced into enterprise networks each day, the level of effort involved in keeping them secure will only continue to rise.
How to Secure Your APIs
Ensuring you’ve got the right policies in place to keep each of your APIs secure requires knowledge of application security risks, such as the OWASP Top 10, as well as what the expected behavior on each API is supposed to resemble. For example, rate limiting is typically implemented to prevent automated denial of service (DoS) attacks, and implementing the right policies requires knowledge of typical inbound requests to each API. Unfortunately, hackers with knowledge of how the API is intended to be used can design attacks to keep requests just below rate limits and the detection capabilities of existing security infrastructure.
You may find it difficult to obtain the detailed operational knowledge of each API, and you’re not alone. Because of the sheer number of APIs on enterprise networks alone—often over 400 according to our recent API security survey—and the various ways they’re implemented, gathering and maintaining API knowledge is a challenge. Plus, relationships between API producers and consumers are constantly in flux, making it difficult to establish “normal” consumption patterns.
Enter artificial intelligence (AI). By using AI algorithms to establish an evolving baseline of expected API behavior, you can detect and block attacks on your APIs. And fill the security gaps that your existing solutions aren’t identifying or defending against today.
PingIntelligence for APIs helps you move away from static, policy-driven security models to continuous, proactive API threat monitoring and detection. By applying AI models to continuously inspect and report on your API activity, it’s able to automatically discover anomalous API traffic behavior. It can even recognize and respond to attacks which fly under the radar of foundational API security measures.
Securing Your APIs Is as Easy as 1-2-3
If you’re like many enterprises, you’re leveraging APIs to advance your digital transformation initiatives and seize new opportunities. But all of those APIs are also new entry points into your organization's most sensitive data, making it easier for hackers and botnets to steal and manipulate critical information.
While API gateway products can provide foundational security capabilities, they can’t detect many cyberattacks on APIs. But PingIntelligence for APIs can. It helps you protect your enterprise against attacks like:
- Credential stuffing on login systems
- Botnets scraping data and launching DDoS attacks
- Hackers using stolen cookies, tokens or API keys
- Insiders exfiltrating data over time
When it comes to API security, it’s safe to say that PingIntelligence makes your job easier. And its most recent updates make experiencing PingIntelligence for yourself even easier, too.
Easier to Protect Your APIs
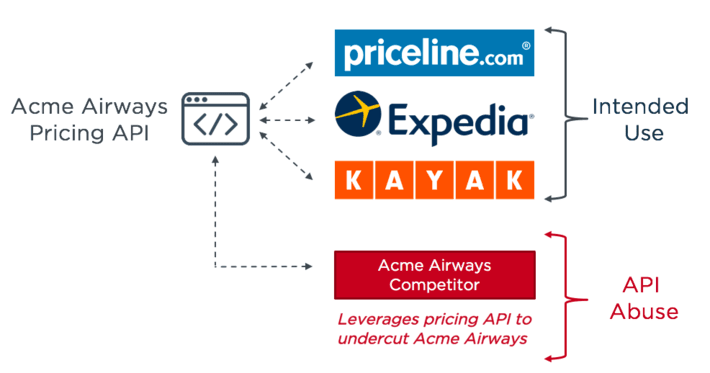
Identifying attacks on APIs isn’t easy for two primary reasons. Firstly, APIs provide more granular and direct access to data and services than web applications. This makes API-based integrations highly efficient, but it also exposes organizations to a new category of API attacks which they aren’t prepared to defend against today. Bad actors, but also competition can leverage exposed functionality and data for unintended purposes. In this example, Acme Airways publicly exposes a pricing API so that price comparison sites can use this information. Unfortunately for Acme, their main competitor has deployed a bot to “scrape” this data with the intention of using it to undercut Acme’s prices whenever a change is made.
Second, hackers often fly under the radar of attack detection systems when using APIs in their attacks. Rather than using tradition credential stuffing methods like attempting to log in hundreds of times until a successful login event takes place, hackers will instead use bots to programatically attempt API access in ways that wouldn’t be caught by volume based detection systems. An example of this is detailed below:
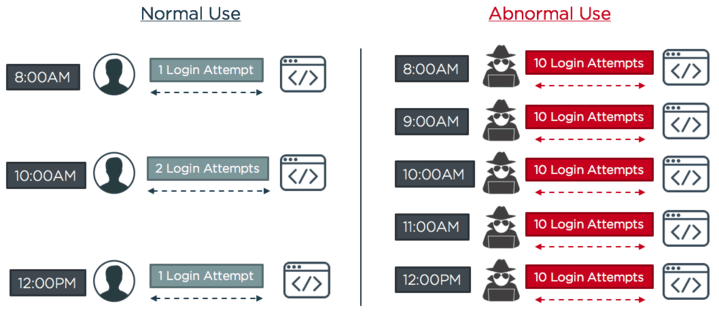
Hackers execute low volume, programmatic login attacks to avoid detection.
In addition to many other vulnerabilities passing as anomalous behavior, PingIntelligence for APIs now protects against both of these attack vectors, enabling you to identify and block bad actors using these tactics. Today, attacks like these expose gaps in API security which existing tools—like content delivery networks (CDN), web application firewalls (WAF) and API gateways—are unable to detect.
Easier to Deploy with Apigee Integration
Recently announced, PingIntelligence for APIs is now available via sideband integration with the Apigee Edge full lifecycle API management platform. Apigee customers can now rely on the combined solutions to provide comprehensive API protection. PingIntelligence augments Apigee’s client authentication and threat protection policies with automated API threat detection and blocking on a per API basis. For example, the Apigee platform generates and validates scoped OAuth tokens for a range of clients and purposes, while PingIntelligence for APIs ensures the token presented hasn’t been stolen since its initial issuance.
PingIntelligence provides a shared flow to integrate Apigee Edge with PingIntelligence for APIs’ platform. The two mechanisms of calling shared flows are flow callout and flow hook policies. A Flow Hook in Apigee Edge applies the PingIntelligence shared flow globally to all APIs in an environment under an organization. The Flow Call Out policy in Apigee Edge applies the PingIntelligence shared flow on a per API basis in an environment under an organization.
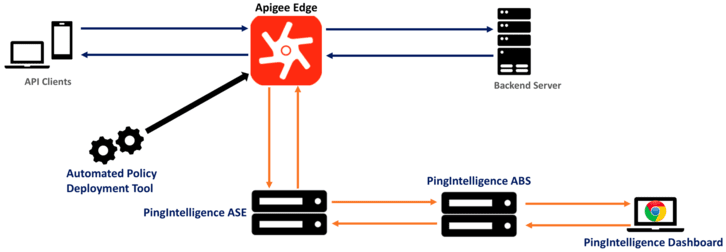
A logical set-up of PingIntelligence ASE and Apigee Edge
Easier to Try for Yourself
Evaluation of the PingIntelligence for APIs solution is now available through a self-service trial delivered as a cloud-based service. Simply download the lightweight API Security Enforcer (ASE) to connect your API environment with the cloud-based service, then deploy it inline in front of APIs or sideband next to PingAccess or an API Gateway.
You can see for yourself how PingIntelligence for APIs can help protect you against targeted API attacks and improve your overall API security posture by enabling:
- Automated API discovery
- AI-based API threat detection and blocking
- Deep traffic visibility with metrics and forensics reports
- Threat dashboard
- Configurable API deception
Secure Your APIs the Easy Way
Attacks against APIs are predicted to increase and eventually become the dominant attack type against enterprises. There’s no better time than now to shore up your API security.
Take the first step to securing your APIs by signing up for a cloud-based trial today.
And join us for a panel discussion with four organizations stewarding the API-first movement on February 27th.


